Validate SpringShell Vulnerabilities with Azure Network Security
Author: Eliran Azulai, Principal Program Manager, Azure Networking
Co-author: Gunjan Jain, Principal PM Manager, Azure Networking
If you were wondering how to protect your resources from the latest Spring Framework exploits, this blog will guide you step-by-step on how to detect and protect against SpringShell vulnerabilities using our native network security services, Azure Firewall Premium and Azure Web Application. You can utilize one of these services or all of them for a Multi-layered security approach.
For more in-depth information on the SpringShell vulnerability and guidance for protection and detection, please check out the blog published by the Microsoft Threat Intelligence Team.
Prerequisites for each service
- Enable IDPS and TLS inspection on Azure Firewall Premium
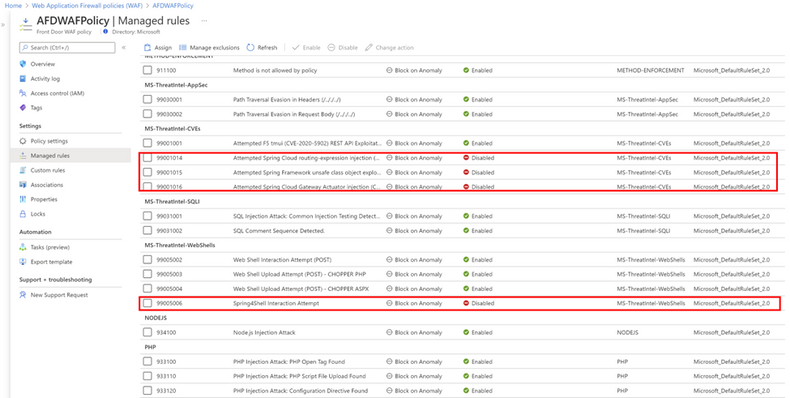
- Enable SpringShell WAF rules on your Azure Front Door WAF (they are disabled by default):
- Rule group: MS-ThreatIntel-WebShells, Rule Id: 99005006 – Spring4Shell Interaction Attempt
- Rule group: MS-ThreatIntel-CVEs, Rule Id: 99001014 – Attempted Spring Cloud routing-expression injection (CVE-2022-22963)
- Rule group: MS-ThreatIntel-CVEs, Rule Id: 99001015 – Attempted Spring Framework unsafe class object exploitation (CVE-2022-22965)
- Rule group: MS-ThreatIntel-CVEs, Rule Id: 99001016 – Attempted Spring Cloud Gateway Actuator injection (CVE-2022-22947)
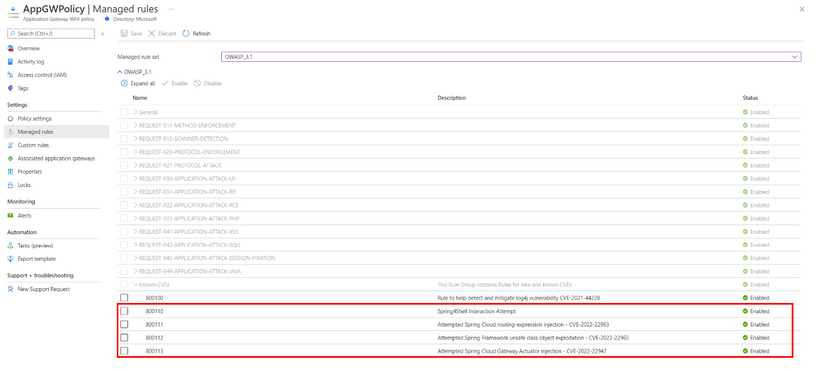
3. No need to enable SpringShell WAF rules on Azure Application Gateway WAF V2 as they are enabled by default:
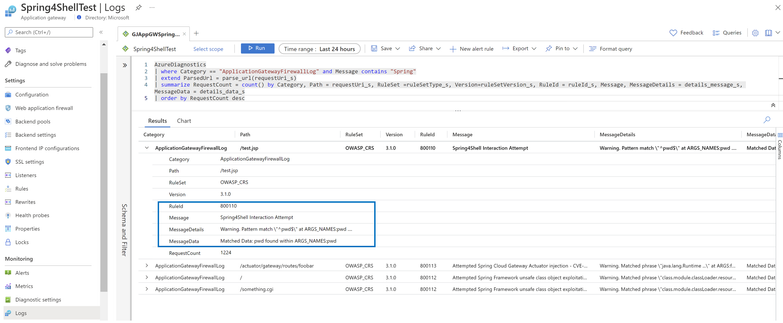
- Rule Id: 800110 – Spring4Shell Interaction Attempt
- Rule Id: 800111 – Attempted Spring Cloud routing-expression injection – CVE-2022-22963
- Rule Id: 800112 – Attempted Spring Framework unsafe class object exploitation – CVE-2022-22965
- Rule Id: 800113 – Attempted Spring Cloud Gateway Actuator injection – CVE-2022-22947
Testing the exploit in Azure Firewall Premium lab
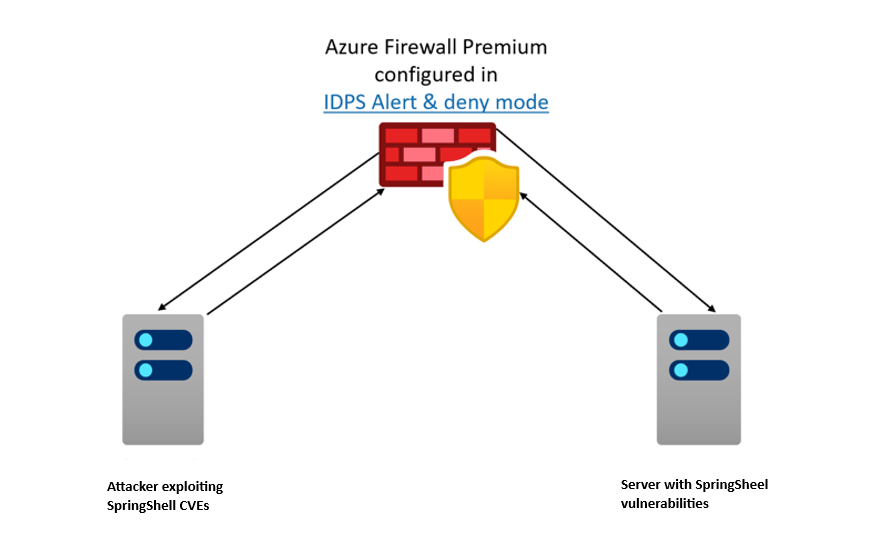
To provide customers with a safe environment to simulate the exploits, we developed a lab setup built with an application that is vulnerable to the Spring4Shell exploit (CVE-2022-22965). You can follow the instructions provided in this GitHub repository to build your own setup.
- Setup requires deploying VNETs in hub-and-spoke model. Firewall, in the hub and spokes, is configured to forward traffic to the hub Firewall for inspection.
- Configure two Linux machines in the spokes as shown in the diagram above.
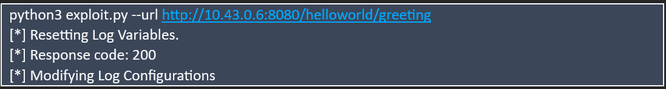
- Make sure the Spring application is available at http://localhost:8080/helloworld/greeting
- Run the exploit.py script locally to view the exploit impact on the server, as shown below:
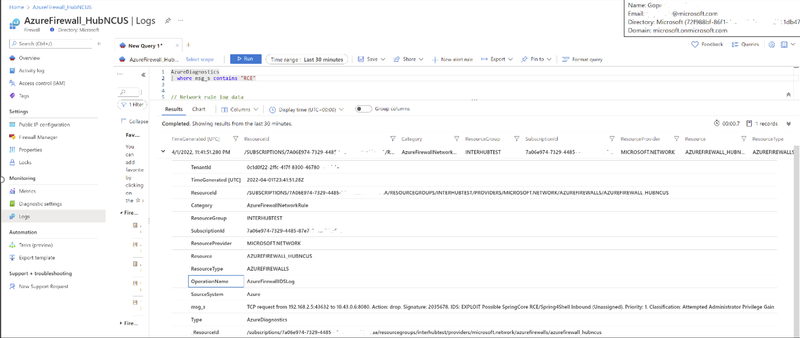
- Run the exploit.py script across the network and verify Azure Firewall blocks the exploit.
- Check out Premium Firewall logs to verify the exploit was blocked.
Testing the exploit with Azure WAF on Azure Front Door
- Setup Azure Front Door with an attached WAF policy. You can use your existing Azure Front Door deployment or set up a new Azure Front Door with an attached WAF policy.
- Ensure WAF SpringShell rules are enabled to get protection from SpringShell threats.
- Replace domain name with your domain name in the following command and run the command in a browser to simulate the exploit:
- Check Azure Front Door WAF logs to verify the exploit is blocked.
Testing the exploit with Azure WAF on Azure Application Gateway
- Setup Azure Application Gateway WAF v2 with an attached WAF policy. You can use your existing Azure Application Gateway setup or create a new Azure Application Gateway with a WAF policy.
- Replace domain name with your domain name in the following command and run the command in a browser to simulate the exploit:
- Check Azure Application Gateway WAF logs to verify the exploit is blocked.
Learn More
Azure Firewall Premium and Azure WAF provide advanced threat protection capabilities to help detect and protect against SpringShell and other exploits. For more information on everything we covered above, please see the following documentation:
- Azure Firewall Premium features | Microsoft Docs
- Deploy and configure Azure Firewall Premium | Microsoft Docs
- Azure WAF DRS rules documentation for Azure Front Door
- Azure WAF CRS rules documentation for Azure Application Gateway
Published on:
Learn moreRelated posts
Microsoft Purview compliance portal: Information Protection – Sensitivity labels protection policy support for Azure SQL, Azure Storage, and Amazon S3
Microsoft Purview Information Protection now supports label-based protection for Azure SQL, Azure Data Lake Storage, and Amazon S3 buckets. Wi...
Centralized private resolver architecture implementation using Azure private DNS resolver
This article walks you through the steps to setup a centralized architecture to resolve DNS names, including private DNS zones across your Azu...
Azure VMware Solution - Using Log Analytics With NSX-T Firewall Logs
Azure VMware Solution How To Series: Monitoring Azure VMware Solution Overview Requirements Lab Environment Tagging & Groups Kusto ...
Troubleshoot your apps faster with App Service using Microsoft Copilot for Azure | Azure Friday
This video provides you with a comprehensive overview of how to troubleshoot your apps faster with App Service utilizing Microsoft Copilot for...
Looking to optimize and manage your cloud resources? Join our Azure optimization skills challenge!
If you're looking for an effective way to optimize and manage your cloud resources, then join the Azure Optimization Cloud Skills Challenge or...
Have a safe coffee chat with your documentation using Azure AI Services | JavaScript Day 2024
In the Azure Developers JavaScript Day 2024, Maya Shavin a Senior Software Engineer at Microsoft, presented a session c...
Azure Cosmos DB Keyboard Shortcuts for Faster Workflows | Data Explorer
Azure Cosmos DB Data Explorer just got a whole lot easier to work with thanks to its new keyboard shortcuts. This update was designed to make ...
How to Use Azure Virtual Network Manager's UDR Management Feature
What will you learn in this blog? What is Azure Virtual Network Manager’s UDR management feature? How UDR management simplifies route setting...
Secure & Reliable Canonical Workloads on Azure | GA Availability
With Azure's partnership with Canonical, the industry standard for patching Linux distributions on the cloud is elevated. The collaboration hi...
Azure VMware Solution now available in Italy North, Switzerland North and UAE North
Azure VMware Solution continues to expand its reach, as it is now accessible in Italy North, Switzerland North, and UAE North. With this expan...