Malware Detection in Sentinel for Azure Firewall

Malware refers to any software that is designed to cause damage, disruption, or compromise the security and functionality of computer systems, networks, or devices. It includes diverse types of threats, such as viruses, worms, trojans, ransomware, spyware, adware, rootkits, and more. Malware can have various negative impacts, such as stealing sensitive data, encrypting, or deleting files, displaying unwanted ads, slowing down performance, or even taking control of the device.
Azure Firewall IDPS feature automatically detects and denies Malware by default and can prevent the cloud workloads from being infected. We can further enhance this capability by employing automated detection and response using prebuilt detection queries and Sentinel. In this blog, we will explore how to detect some common malware found in Azure Firewall logs like Coin-miner, Cl0p and Sunburst using predefined KQL detection queries for Azure Firewall.
These detections enable security teams to receive Sentinel alerts when machines on the internal network request connections to domain names or IP addresses on the internet that are linked to known Indicators of Compromise (IOCs), as defined in the detection rule query. True positive detections should be regarded as Indicators of Compromise (IOCs). Subsequently, security incident response teams can initiate a response and implement appropriate custom remediation actions based on these detection signals.
Instructions for implementing the analytic rules using the queries below may be found in the blog.
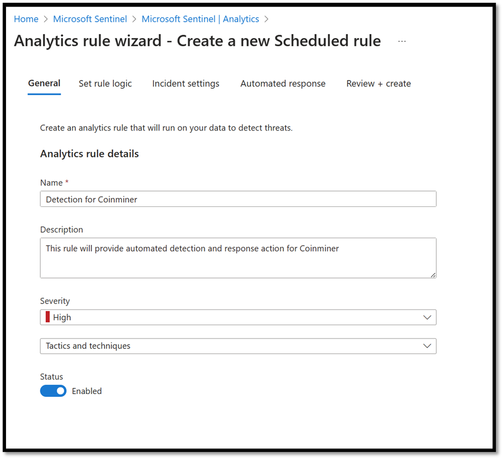
1. Coinminer
Due to the recent surge in cryptocurrency mining, there is an increasing need for high-performance network processing units. This has given rise to the expansion of distributed computing and the widespread availability of mining software, both in legal and illegal contexts. Coinminer represents a type of malware that utilizes the hardware resources of an unwitting victim's computer for cryptocurrency mining. The graphics processing unit (GPU) of the unsuspecting user's PC is utilized to execute various scripts aimed at mining cryptocurrencies and calculating transaction block hashes. To mitigate the risk of these threats, proactive measures should be implemented at the typical entry points. This includes ensuring that Jupyter software is deployed with proper authentication, configuring, and updating web applications to minimize vulnerabilities, controlling external access to Docker, and following extra Zero Trust principle.
The following detection query can be used to create an analytical rule in Sentinel to automatically detect and respond to this malware using Azure Firewall logs.
2. Cl0p
Cl0p is a ransomware that operates by applying distinctive encryption keys to the victim's files and subsequently requesting a ransom for the files' decryption. It leverages a vulnerability in the data transfer software MOVEit and sends spear phishing emails to numerous employees in the hope to deliver cl0p. Then it uses tools like truebot and dewmode to move laterally within the network and exfiltrate data. The ransomware encrypts files using the AES-256 encryption algorithm.
Cl0p vulnerabilities include CVE-2023-35036, CVE-2023-34362 and CVE-2023-35708. In June 2023, FBI and CISA published a press release of the effect of this exploitation. The effects of cl0p ransomware have recently been registered across several universities in the Midwest and government organizations. Airlines, TV Networks and UK based retail stores are the latest victims of the cl0p ransomware gang.
Here’s the detection query that can be used to create an analytical rule in Sentinel to automatically detect and respond to this malware using Azure Firewall logs.
Detection Query for Cl0p: Firewall Malware Detections for Sentinel/Detection - Analytic rule query for Cl0p.json
3. Sunburst
This malware targets victims by using domain generation algorithm (DGA) strings to evade detection and establish a command-and-control backdoor attack. The DGA strings are often difficult for security tools to identify the domains used by the malware due to the pattern used in the syntax and their constant changing of the domain information.
Here is the detection query that can be used to create an analytical rule in Sentinel to automatically detect and respond to this malware using Azure Firewall logs.
Detection Query for Sunburst Malware: Firewall Malware Detections for Sentinel/Detection - Analytic rule query for Sunburst.json
Conclusion: Azure Firewall is a powerful tool that can help secure your network and prevent malicious attacks. By using the detection queries provided here, you can further enhance your security posture and monitor your firewall activity more effectively.
It is important to identify and eliminate malware from a system or network which can be achieved by employing various detection techniques, such as signature-based, behavior-based, heuristic-based, or machine learning-based techniques. Malware detection is vital for protecting the security and privacy of users, as well as the integrity and availability of systems and networks.
Additional references: