Azure Firewall's Auto Learn SNAT Routes: A Guide to Dynamic Routing and SNAT Configuration

Introduction
Azure Firewall is a cloud-native network security service that protects your Azure virtual network resources. It is a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability. However, some Azure Firewall customers may face challenges when they need to configure non-RFC-1918 address spaces to not SNAT through the Azure Firewall. This can cause issues with routing, connectivity, and performance. To address this problem, Azure Firewall has introduced a new feature that allows customers to specify which address spaces should not be SNATed by the firewall. This feature can help customers reduce the overhead of managing custom routes and NAT rules and improve the efficiency and reliability of their network traffic. In this blog, we will explain how the feature works, what Azure Route Server is, and how to enable it. We will also provide a QuickStart guide and some examples to help you get started with this feature.
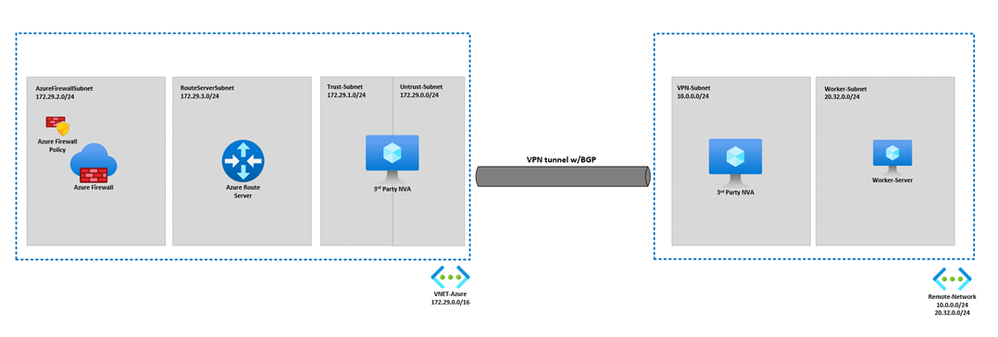
What is Azure Route Server?
The Azure Route Server (ARS) is a fully managed service that enables dynamic routing between your network virtual appliance (NVA) and your Azure virtual network, without requiring any manual configuration or intervention. The ARS is configured with high availability, meaning that it can automatically fail over to another instance in case of failure or disruption. The ARS uses the Border Gateway Protocol (BGP) routing protocol to exchange routing information directly with any NVA that supports BGP, such as firewalls, load balancers, or VPN gateways. This way, the ARS can learn the network address spaces that are advertised by the NVA and propagate them to the entire Azure virtual network. This eliminates the need for customers to manually configure route tables across all the subnets of an Azure virtual network, which can be tedious and error prone. Moreover, the ARS can dynamically update the route tables whenever a new address space is added or an old address space is removed by the NVA, ensuring that the routing is always consistent and up to date. The ARS simplifies the integration of NVAs with the Azure Software Defined Network (SDN), which provides a flexible and scalable network infrastructure for cloud applications. By using the ARS, customers can leverage the benefits of both NVAs and Azure SDN, such as security, performance, reliability, and cost-efficiency.
How does Auto-learn work?
Auto-learn SNAT routes is a public preview feature that can help reduce time and complexity spent manually defining SNAT private ranges. The Azure Firewall will pull an updated list of learned address ranges from the Azure Route Server every 30 minutes. These learned address ranges are considered to be internal to the network, so traffic to destinations in the learned ranges aren't SNATed. This is especially useful when enterprises must use non-RFC-1918 address spaces in their environments.
Auto-learn SNAT routes is simple to configure either through the Azure Portal or using a variety of Infrastructure as Code (IaC) flavors.
To enable the feature, you’ll first have to create an Azure Route Server and BGP peer it to your network virtual appliance. The Azure Route Server must be in the same virtual network as the Azure Firewall. Use this QuickStart guide to learn how to deploy the ARS and configure it to peer with your appliance. Once the ARS has been successfully peered with the appliance, we can start associating the Azure Firewall with the Azure Route Server to auto-learn out of network address spaces. To enable the feature in the Azure Portal, follow the steps below:
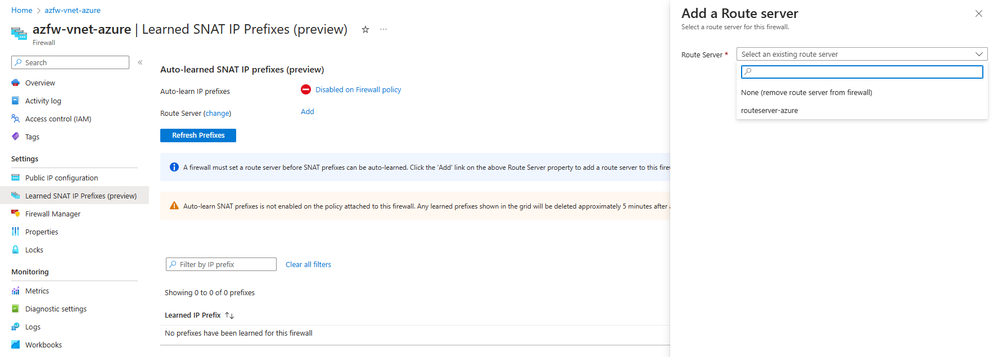
1. Navigate to the Azure Firewall’s Overview blade and select Learned SNAT IP Prefixes. From this view, select Add to choose which Azure Route Server will teach this particular firewall its learned routes. Remember that the Azure Firewall and the ARS must be in the same Azure virtual network.
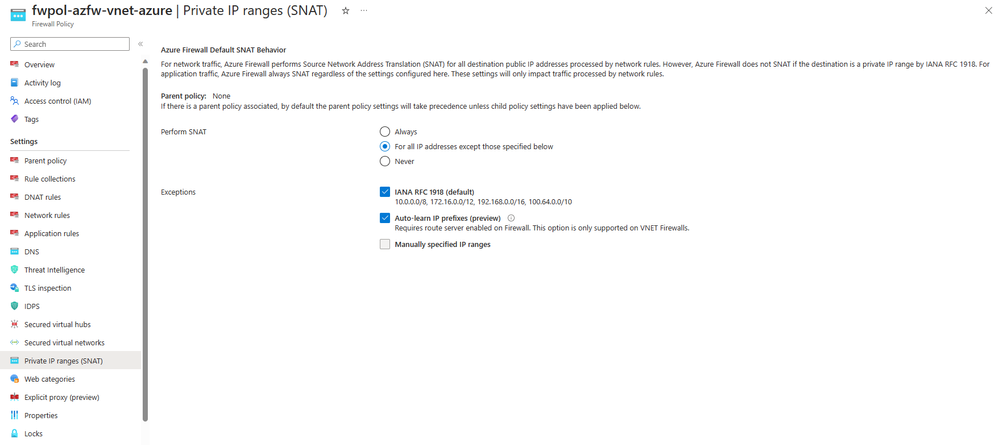
2. Once an ARS has been selected, the feature needs to be enabled on the associated Azure Firewall Policy. From the previous screenshot, simply select Disabled on Firewall policy to be redirected to the Private IP ranges (SNAT) blade in the associated Azure Firewall Policy. On this blade, select Auto-learn IP prefixes under Exceptions to finish configuring the Auto-learn SNAT feature.
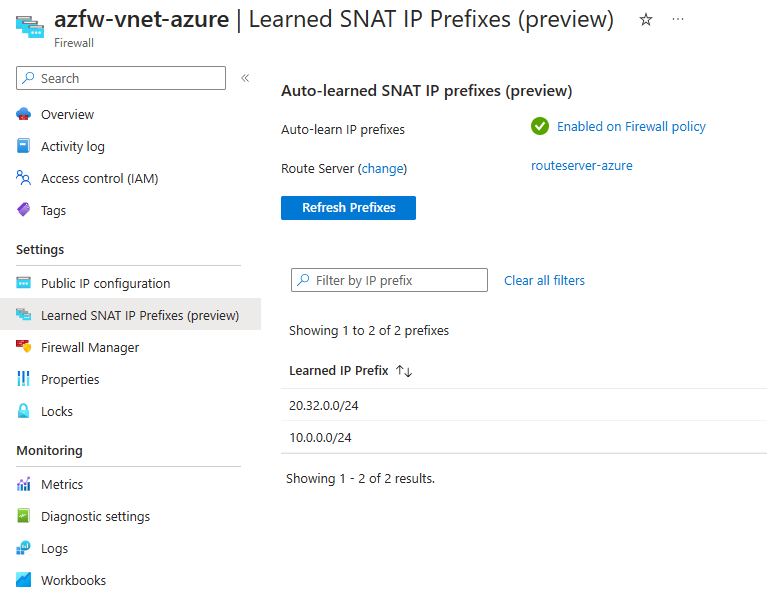
3. After you finish the steps on the Azure Firewall, and after the ARS and the NVA can talk to each other using BGP, you can see the new routes that the ARS told the Azure Firewall on the Learned SNAT IP Prefixes blade. In the picture below, you can see that we learned one private address range and one public address range, 20.32.0.0/24. The Azure Firewall will now know that 20.32.0.0/24 is not for public internet but for local networks in Azure and other remote networks. This prevents the Azure Firewall from changing the source IP of the public address range when it checks the traffic. But any traffic that goes through Application Rules on the Azure Firewall will still have its source IP changed to either the private IP or the public IP of the Azure Firewall, depending on where it goes next.
Conclusion
Azure Firewall’s Auto-learn SNAT routes feature can help you simplify and optimize your network configuration in Azure. This feature allows the Azure Firewall to automatically learn the out-of-network address spaces from the Azure Route Server and avoid SNATing the traffic to those destinations. This can save you time and effort in manually defining the SNAT private ranges, and also improve the performance and security of your network traffic. Auto-learn SNAT routes is easy to enable either through the Azure Portal or using your preferred IaC tool. You just need to create an Azure Route Server, peer it with your network virtual appliance, and associate it with your Azure Firewall policy. If you want to try this feature, you can follow the QuickStart guide and the steps we have provided in this blog. Auto-learn SNAT routes is a public preview feature that can enhance your network experience in Azure, so don't miss this opportunity and give it a try today!
Resources
What is Azure Firewall? | Microsoft Learn
Azure Firewall FAQ | Microsoft Learn
Azure Firewall preview features | Microsoft Learn
Azure Firewall SNAT private IP address ranges | Microsoft Learn
What is Azure Route Server? | Microsoft Learn
Azure Route Server frequently asked questions (FAQ) | Microsoft Learn
Lab/RS-AA-OPNsense-ForceTunnel-ER at master · dmauser/Lab (github.com)
Published on:
Learn moreRelated posts
Azure Migrate Execute
From Manual Testing to AI-Generated Automation: Our Azure DevOps MCP + Playwright Success Story
In today’s fast-paced software development cycles, manual testing often becomes a significant bottleneck. Our team was facing a growing backlo...
Cognitive services and Azure ML for Dataflows will be fully retired by September 15th, 2025
This blog is outlining the depreciation announcement for Azure ML and Cognitive services using dataflows.
Azure Developer CLI: From Dev to Prod with One Click
This post walks through how to implement a “build once, deploy everywhere” pattern using Azure Developer CLI (azd) that provisions...
Azure Migrate assessments
AI Builder – Invoice processing and Invoices document type to begin using Azure
Starting on July 21, 2025, the prebuilt model invoice processing and invoices document type (built on Azure Document Intelligence 4.0) will be...
Dataverse: Learn How to Implement Azure Durable Functions – Payment Scenario
Azure Durable Functions is an extension of Azure Functions that offers specialized capabilities, including statefulness, orchestration, handli...
Build reliable Go applications: Configuring Azure Cosmos DB Go SDK for real-world scenarios
When building applications that interact with databases, developers frequently encounter scenarios where default SDK configurations don’...