Guarding the Gates: Exploring Supported Scenarios for Azure DDoS Protection and Public IP Prefixes
Introduction
In the face of an ever-evolving digital landscape, businesses are constantly under the threat of Distributed Denial of Service (DDoS) attacks. These relentless assaults have the potential to overwhelm network resources, disrupt services, compromise sensitive data, and lead to significant financial losses. As these threats become increasingly common, the need for a robust defense mechanism has never been more critical.
In this blog post we are showing you the scenarios where Azure DDoS Protection can help protect Public IP Prefixes from these attacks.
What is Azure DDoS Protection?
Azure DDoS Protection is a cloud-based service provided by Microsoft Azure that provides automatic detection and mitigation of DDoS attacks for Azure resources. Key features and benefits of Azure DDoS Protection include:
- Adaptive tuning of the DDoS mitigation policy thresholds based on the traffic patterns and characteristics of each application.
- Automatic detection and mitigation of DDoS attacks without requiring any user intervention or configuration changes.
- Detailed monitoring and reporting of DDoS attack incidents and mitigation actions.
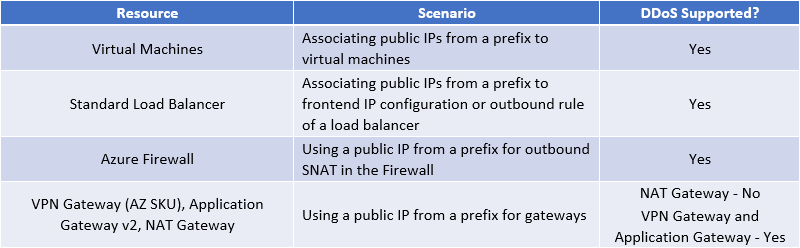
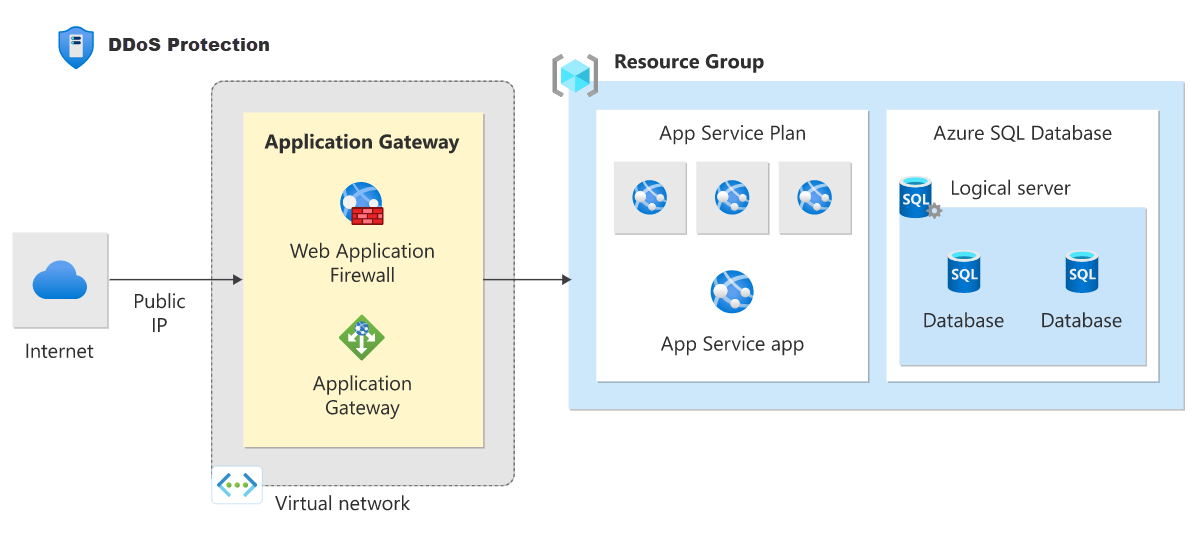
Azure DDoS Protection protects resources using Public IPs and Public IP Prefixes in ARM based VNETs, such as:
- IaaS Virtual Machines
- Load Balancers
- Application Gateway (including WAF)
- Azure Firewall
- Bastion
- VPN Gateway
- IaaS based Network Virtual Appliance (NVA)
- Others as described here
What is Public IP Prefix?
A public IP address prefix is a reserved range of public IP addresses in Azure. Public IP prefixes are assigned from a pool of addresses in each Azure region. You create a public IP address prefix in an Azure region and subscription by specifying a name and prefix size. The prefix size is the number of addresses available for use. Public IP address prefixes consist of IPv4 or IPv6 addresses. In regions with Availability Zones, Public IP address prefixes can be created as zone-redundant or associated with a specific availability zone. After the public IP prefix is created, you can create public IP addresses. A Public IP Prefix can be used in different scenarios as described here.
Protecting Public IP Prefixes from DDoS attacks
Upon the creation and assignment of a Public IP Prefix to a resource, it becomes exposed and potentially susceptible to DDoS attacks. To prevent these attacks from disrupting services or rendering applications unresponsive, the use of Azure DDoS Protection is highly recommended. However, it is important to know what to expect when you are protecting a Public IP Prefix. Below you will find the supported scenarios using a PIP from a Prefix and a Public IP Prefix.
PIP from a Public IP Prefix:
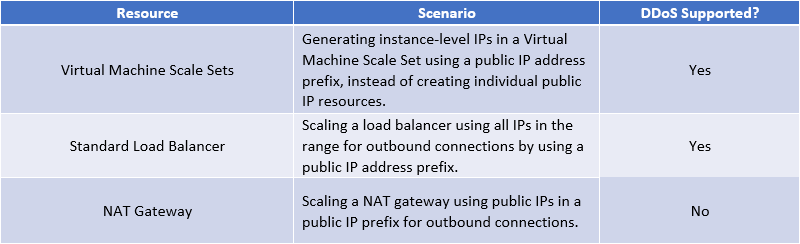
Public IP Prefix:
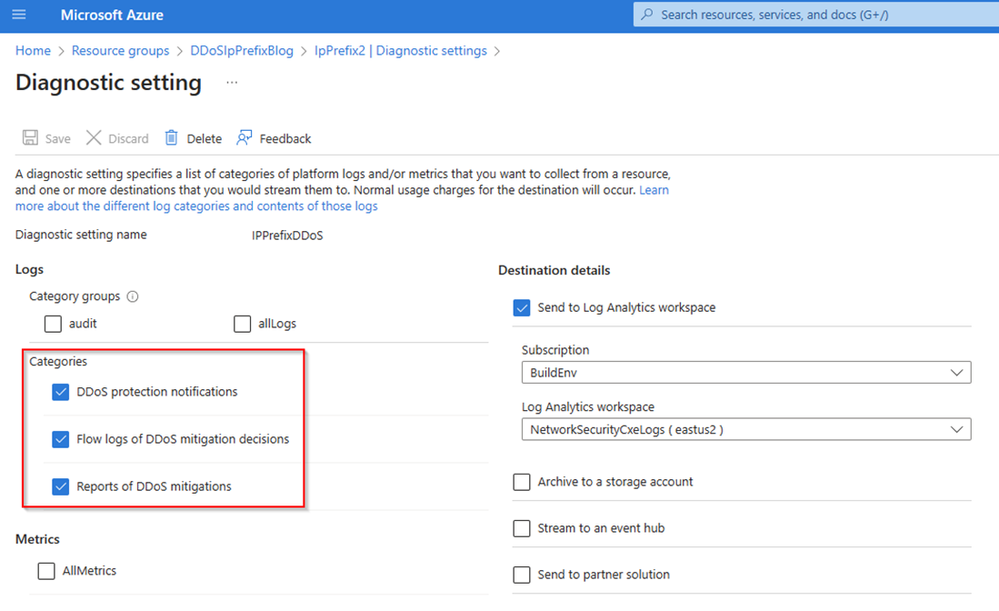
The only SKU available to protect an IP Prefix is DDoS Network Protection. Once the DDoS protection plan is enabled at VNET level the IP Prefix attached to a resource in the same VNET is protected. Next, we need to create a Diagnostic Setting, enabling all 3 DDoS log categories, so we can get visibility of attacks when they occur.
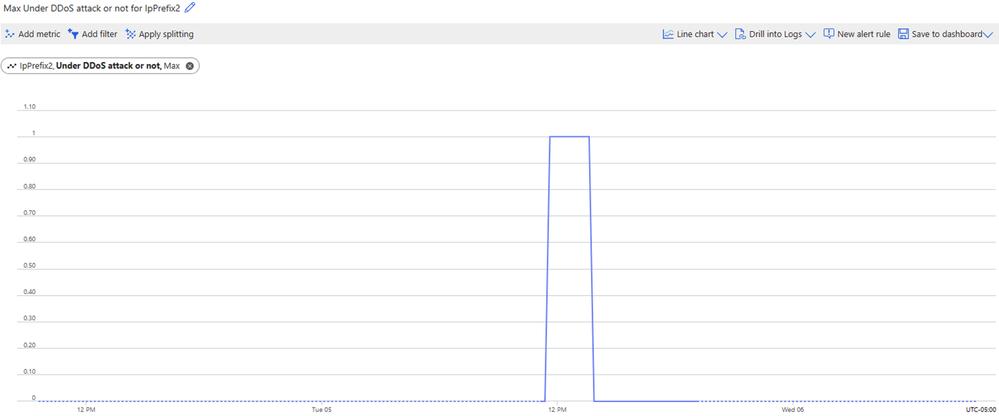
Through the IP Prefix Metrics blade, we can also gain visibility of all the DDoS metrics such as “Inbound TCP packets to trigger DDoS mitigation”, “Under DDoS attack or not”, and others.
Conclusion
The digital landscape is fraught with threats, and DDoS attacks are among the most disruptive. The exposure of Azure resources using Public IPs and Public IP Prefixes can make them vulnerable to such attacks. However, with Azure DDoS Protection, organizations can fortify their defenses, ensuring the continuity of services and the responsiveness of applications keeping in mind each scenario discussed in this blog.
Resources
Published on:
Learn moreRelated posts
Azure Developer CLI (azd): One command to swap Azure App Service slots
The new azd appservice swap command makes deployment slot swaps fast and intuitive. The post Azure Developer CLI (azd): One command to swap Az...