Best Practices for Upgrading Azure WAF Ruleset
This blog is written in collaboration with @davidfrazee.
Introduction:
In today’s digital landscape, web applications are the lifeblood of businesses. They enable seamless communication, transactions, and interactions with customers. However, this increased reliance on web apps also makes them prime targets for cyberattacks. To safeguard your applications and protect sensitive data, implementing a robust Web Application Firewall (WAF) is essential.
What is a Web Application Firewall (WAF)?
A WAF acts as a protective barrier between your web applications and potential threats. It analyses incoming HTTP/S traffic, detects malicious requests, and blocks them before they reach your application servers. By doing so, it prevents common vulnerabilities and attacks without requiring modifications to your application code.
Azure Web Application Firewall (Azure WAF):
Azure WAF, integrated with Azure Application Gateway or Azure Front Door, provides a powerful solution for securing your web apps. Let’s explore why you should consider using Azure WAF:
- Protection Against Common Exploits and Vulnerabilities:
- Azure WAF actively safeguards your applications against well-known attack vectors like SQL injection and cross-site scripting.
- It leverages the Core Rule Set (CRS) from the Open Web Application Security Project (OWASP) to stay ahead of emerging threats, it also uses MSTIC (Microsoft Threat Intelligence Collection) rules that are written in partnership with the Microsoft Intelligence team to provide increased coverage, patches for specific vulnerabilities, and better false positive reduction.
- Easy Configuration and Central Management:
- Create custom WAF policies tailored to different sites behind the same Application Gateway/Front Door instance.
- Manage and configure settings centrally using WAF policies.
- Monitoring and Real-Time Alerts:
- Monitor attacks with real-time WAF logs integrated into Azure Monitor.
- Easily track WAF alerts and analyse trends.
- IP Reputation Ruleset:
- Protect your applications from malicious bots utilizing the Azure WAF Bot Manager Ruleset
- Defend against Distributed Denial of Service (DDoS) attacks.
Upgrading WAF Rulesets
Keeping your WAF rulesets up to date is critical for several reasons:
- Expanded Coverage:
- New rulesets include additional protections for emerging vulnerabilities.
- Stay ahead of attackers by having the latest defenses in place.
- Reduced False Positives:
- Updated rulesets improve accuracy, minimizing false positives.
- Ensure legitimate traffic isn’t blocked unnecessarily.
- Staying Ahead of Threats:
- Regular updates ensure your WAF defends against the latest attack vectors.
- Cyber threats evolve rapidly, and your defenses must keep pace.
Best Practices for Upgrading Azure WAF Ruleset
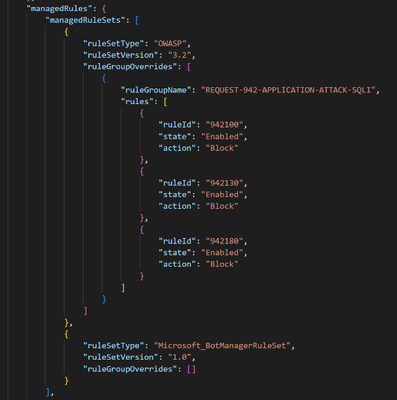
Consider a situation where you are currently using Core Rule Set (CRS) version 3.2 for your Azure Web Application Firewall (WAF). You have made several customizations to the WAF configuration, including disabling specific rule IDs, adjusting rule actions from Anomaly score/Log to Block, and applying exclusions.
Now, if you decide to upgrade to Default Rule Set (DRS) version 2.1, it’s important to be aware that all your previous customizations to the managed rulesets will be reset if you upgrade through the portal directly. However, rest assured that any Custom Rules, Global Exclusions and Policy settings you’ve defined will remain unaffected during this transition.
To make sure that you do not lose any custom configurations for your Managed rulesets, follow these best practices using Template-based approach:
1. Document Your Current WAF Configuration:
- Export the template capturing existing WAF settings, including disabled rules and exclusions. Save this template as CRS_3.2
2. Prepare a New Template:
- Clone the old Template and rename it to DRS_2.1 for the upgraded version.
3. Test in a Non-Production Environment:
- Switch to the new ruleset using Portal Assign method in a non-production environment.
- Temporarily disable Custom rules used in Tuning
- Verify if exclusions are still necessary by sending traffic through this non prod WAF setup.
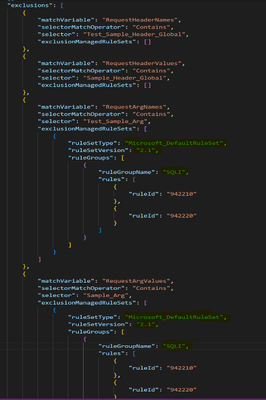
4. Reassign Exclusions and Customizations:
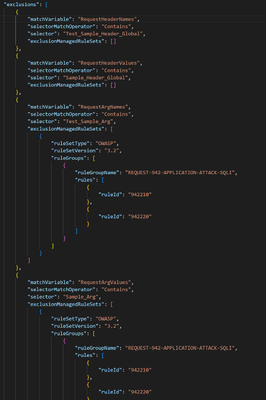
Apply exclusions and customizations using the below template modification method.
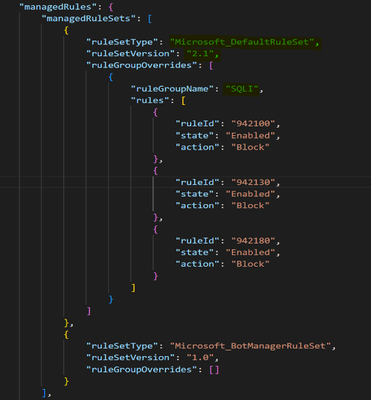
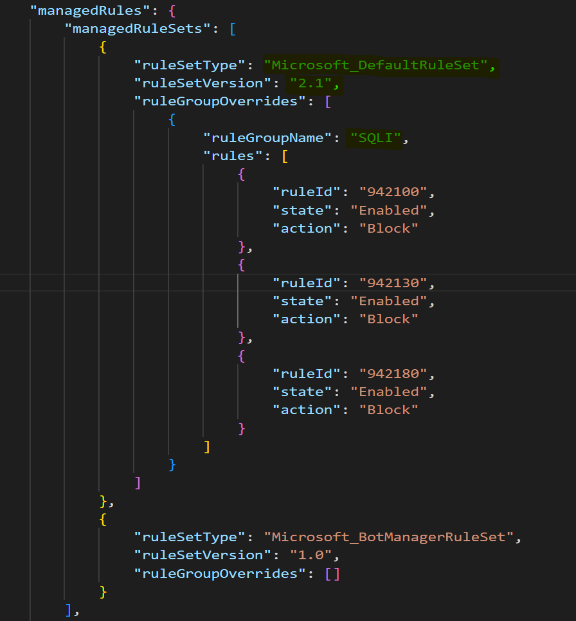
- Modify the following parameters in the template saved as DRS_2.1 as shown below:
i. Ruleset Type
ii. Ruleset Version
iii. Rule Group Name (Rule Group and Id information can be found here )
- Deploy this template in your environment and this will upgrade the policy from CRS_3.2 to DRS_2.1 with all the Rule Overrides and Exclusions intact.
5. Run Tests:
- Send traffic and validate that exclusions and customizations still apply as expected.
Note:
- If the exclusions are set to the Global level, those exclusions will not be affected after the upgrade. So, no changes are needed for Global exclusions.
- In any case, you want to revert to the old ruleset, you can simply redeploy the initially saved template CRS_3.2 and all the changes should be reverted to previous state.
- While following Template Based Upgrade process above, it is important to note that the Rule Id must be present in the new ruleset for which there has been a custom modification done in the existing ruleset. This needs to be checked before the upgrade using the information here.
Conclusion:
In summary, Azure WAF provides robust protection, easy management, and real-time monitoring for your web applications. Upgrade your rulesets regularly to stay secure in an ever-evolving threat landscape. Remember, a proactive defense is the key to keeping your applications safe and your users confident.
Published on:
Learn moreRelated posts
Azure Developer CLI (azd): One command to swap Azure App Service slots
The new azd appservice swap command makes deployment slot swaps fast and intuitive. The post Azure Developer CLI (azd): One command to swap Az...