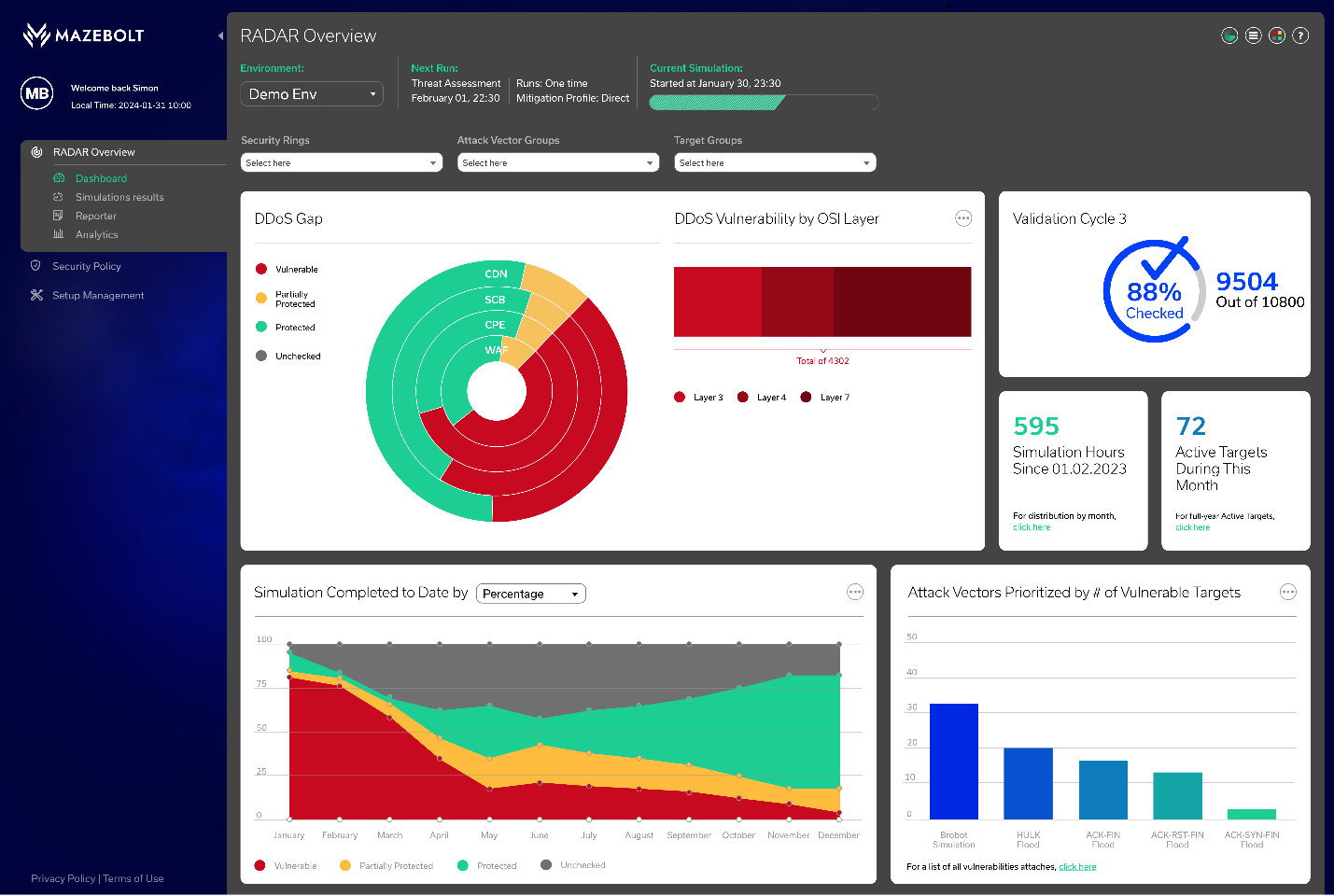
GeoLocation Filtering with Azure Firewall
Published Friday, March 11, 2022
Microsoft is committed to helping defend organizations and governments from cyberattacks. This guide provides steps Azure Firewall customers can take to secure their cloud infrastructure.
Overview of Azure Firewall
- Azure Firewall is a cloud-native stateful Firewall as a service with built-in auto-scale (30 Gbps) and High availability.
- Standard SKU provides DNAT, Network, and Application rule filtering. It also supports advanced filtering with threat intelligence and web categories. You can read more about standard Firewall features.
- Premium SKU includes all functionalities of Standard SKU. In addition, it provides URL filtering, IDPS, and outbound TLS inspection. You can read more about Azure Firewall Premium features.
Azure Firewall Best Practices
- Azure Firewall operates in a default-deny mode. This means that you will need to add an explicit rule to allow traffic. It’s best practice to review your rules regularly to ensure the IP addresses and FQDNs are relevant.
- Avoid wild cards in rules and use URLs instead of FQDNs! Provide explicit ports and protocols. This will reduce the attack surface drastically. Note: URL filtering is only supported on Premium SKU!
- Enable Threat Intelligence in alert and Deny mode! The feed is provided by the Microsoft cyber-security team and is updated continuously based on changing threat landscape.
- Customer deployments who want to route VNET traffic through Azure Firewall to another 3rd Party or On-Prem Firewall for internet egress can deploy Azure Firewall in Forced Tunnelling mode without a Public IP. Please follow the instructions in this blog for more information.
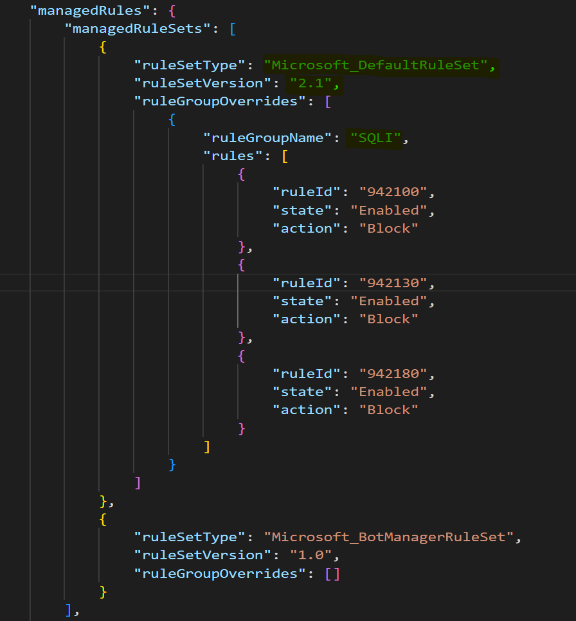
- Azure Firewall provides support for IP Group which provides a facility to block large IP ranges. Azure Firewall supports 100 IP Groups with each containing 5000 IP addresses! You can follow the guidance provided here to automate company-wide IP blocking via Azure Firewall. Alternatively, you can use the community-provided script to create IP Group reading IP addresses from any input file (containing list of IP addresses that you would like to block e.g. here). This approach can be used to block traffic to or from specific regions or geographies. Post-creating IP Group, customers can create DENY rules to block traffic to the IP addresses in the IP Group. It’s sufficient to mention the IP Address in Src or Dest. The azure firewall will automatically create rules in both directions.
|
Rule Action |
Rule |
|
DENY |
{Src:IPGroup1, Dest:*, Port:*, Protocol:*} |
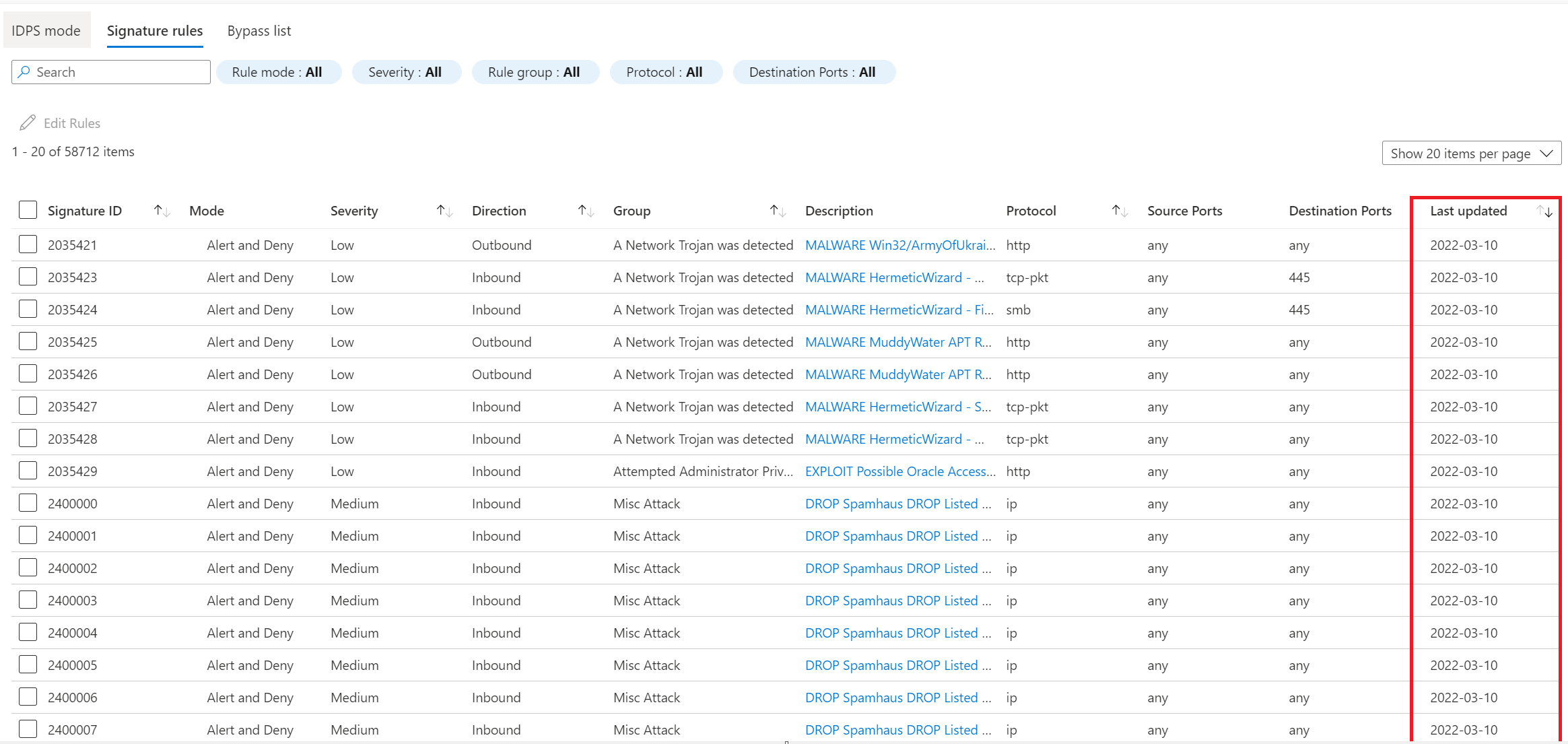
- Premium SKU customers can additionally configure IDPS in DENY mode. We support more than 57000+ CVEs that are updated continuously and provide protection against the latest ransomware/malware attacks. For inbound HTTPS security, you can additionally deploy Application Gateway in front of Premium Firewall.
Recent CVEs
Customers using Azure Firewall Premium have enhanced protection from the latest exploits including Nobelium, Log4j, WhisperGate, PurpleFox, Cobalt Strike, Gamaredon. Azure Firewall premium IDPS (Intrusion Detection and Prevention System) provides IDPS inspection for all east-west traffic and outbound traffic to the internet. The vulnerability rulesets are continuously updated. Below screenshot shows all the scenarios which are actively mitigated by Azure Firewall Premium.
Customers are recommended to configure Azure Firewall Premium with both IDPS Alert & Deny mode and TLS inspection enabled for proactive protection against Log4j (CVE-2021-44228) exploit.
Sentinel Threat Hunting and workbook
Azure Firewall Solution for Azure Sentinel provides Azure Firewall specific net new detections and hunting queries. The solution also contains a new firewall workbook and automation components, which can now be deployed in a single, streamlined method. You can read more about this from the link below.
- New Detections, Hunting Queries and Response Automation in Azure Firewall Solution for Azure Sentinel (microsoft.com)
- New Detections for Azure Firewall in Azure Sentinel
- Automated Detection and Response for Azure Firewall with the New Logic App Connector and Playbook
Related Links
Destructive malware targeting Ukrainian organizations - Microsoft Security Blog
Digital technology and the war in Ukraine - Microsoft On the Issues
Continue to website...