Monthly news - September 2022
Published Monday, October 3, 2022

|
Microsoft 365 Defender |
 |
||||||||||||||||||||||||
|
This is our monthly "What's new" blog post, summarizing product updates and various assets we have across our Defender products. |
|||||||||||||||||||||||||
|
|||||||||||||||||||||||||
| Microsoft 365 Defender | ||
|
| Microsoft Defender for Cloud Apps | ||||||||||
|
| Microsoft Defender for Endpoint | ||||||||||||||||||
|
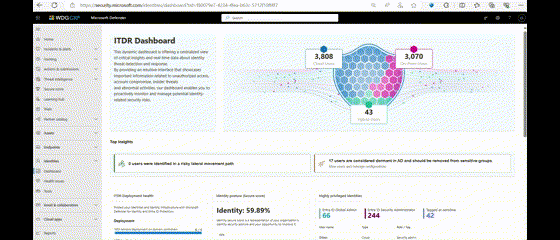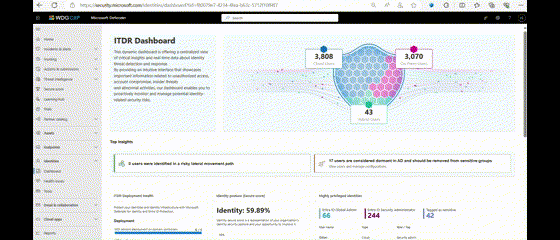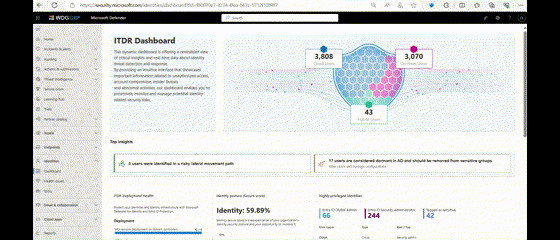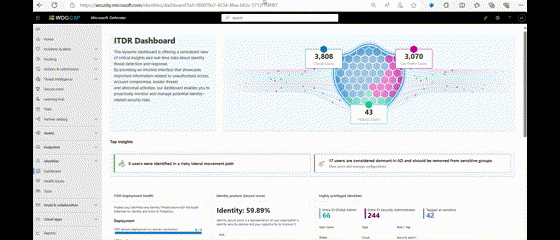
| Microsoft Defender for Identity | ||||||||
|
| Microsoft Defender for IoT | ||
|
| Microsoft Defender for Office 365 | ||||||||||
|
| Microsoft Defender Vulnerability Management | ||
|