Azure NetApp Files SMB volumes for Azure Kubernetes Services with Astra Trident on Windows
Published Thursday, June 1, 2023
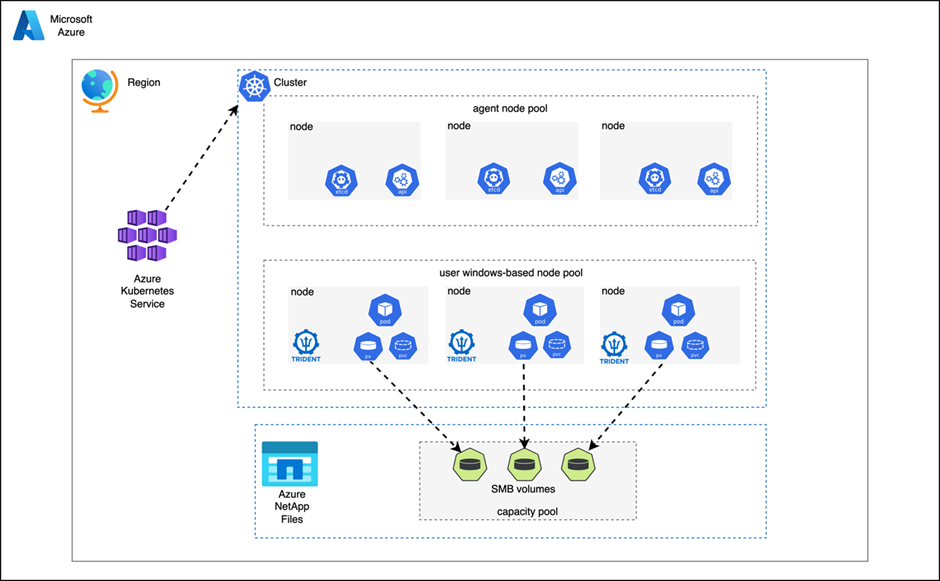
Table of Contents
Initial Azure NetApp Files and AKS prerequisites and configurations
Azure NetApp Files initial configuration
Sign in and register the resource provider
Review Azure NetApp Files networking guidelines
Provision a subnet to Azure NetApp Files
Create and manage Active Directory connections for Azure NetApp Files
Installing and configuring the Astra Trident CSI driver for Kubernetes
Using the Astra Trident CSI driver for Kubernetes
Create a secret with the domain credentials
Create a persistent volume claim
Add data to the volume and check access
Abstract
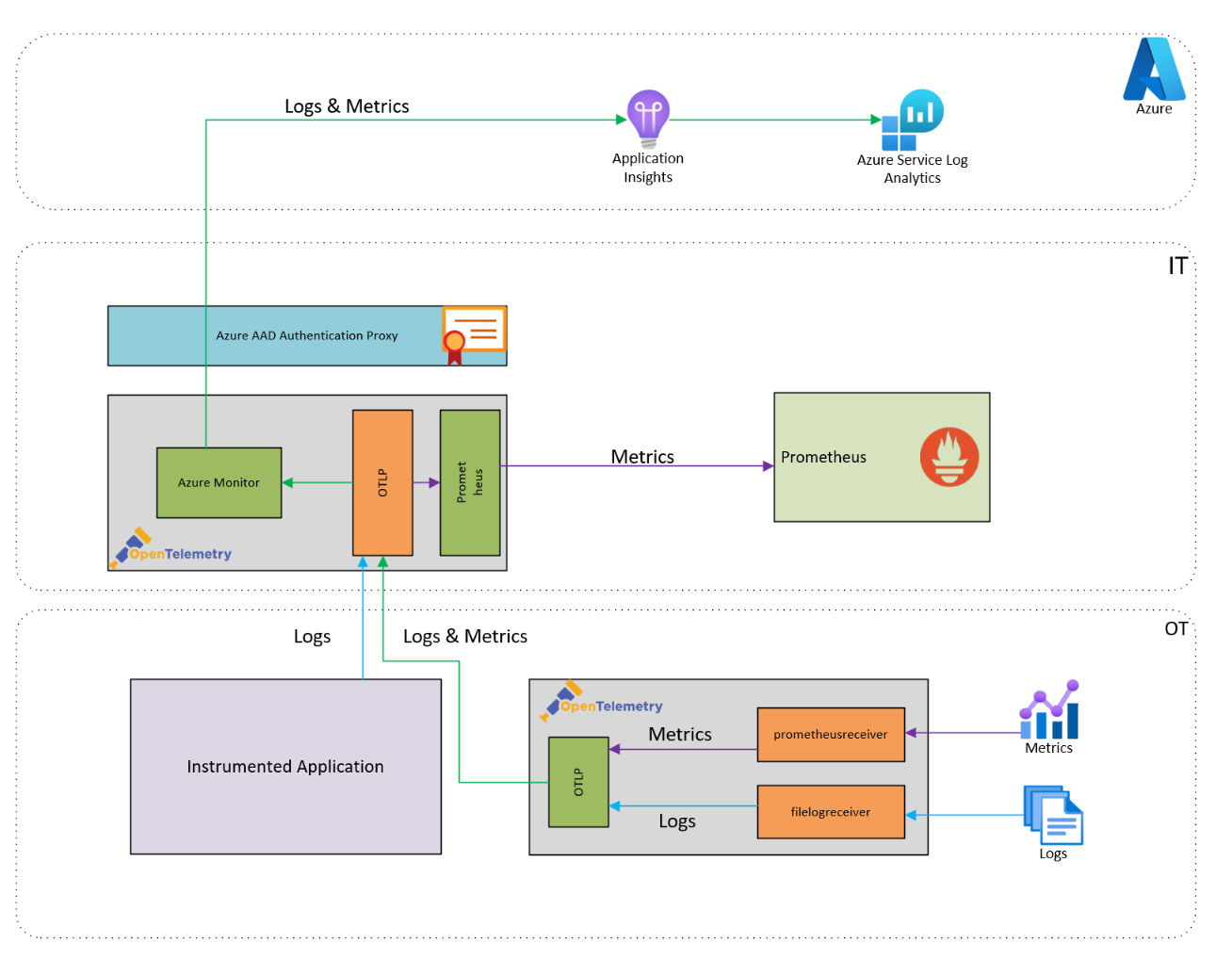
This article describes how to use Astra Trident to set up dynamic SMB volume provisioning on an Azure Kubernetes Service (AKS) cluster with Windows worker nodes and Azure NetApp Files. We show how to set up the pre-requisites for using Azure NetApp Files shares and how to install, configure, and use the Astra Trident provisioner.
Co-Authors: Diane Patton, Technical Marketing Engineer
Introduction
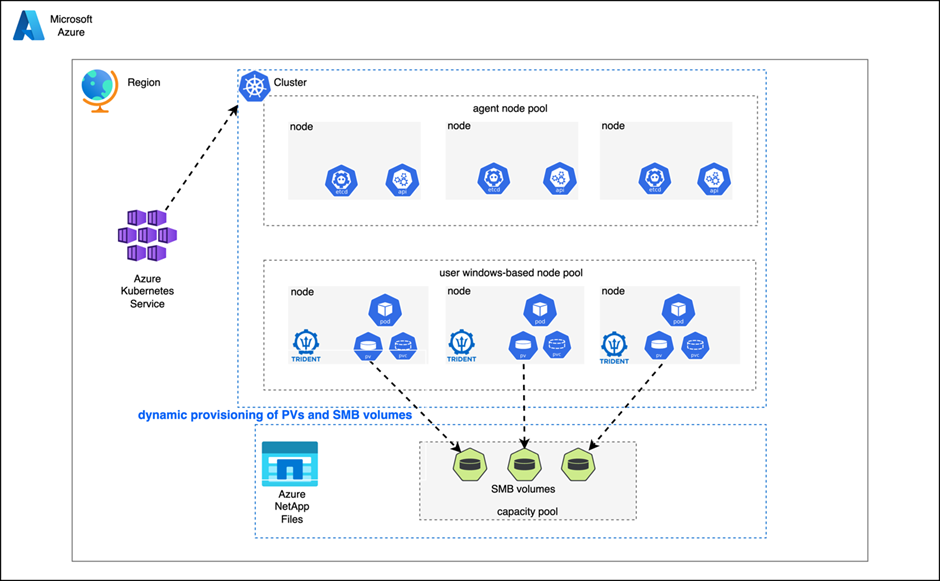
As more stateful windows-based applications are containerized and deployed on Azure Kubernetes Service (AKS), it becomes imperative to have dynamic Secure Message Block (SMB) access to Azure NetApp Files. Azure NetApp Files is an Azure native, first-party, enterprise-class, high-performance file storage service. It provides NAS volumes as a service for which you can create NetApp accounts, capacity pools, select service and performance levels, create volumes, and manage data protection. It allows you to create and manage high-performance, highly available, and scalable file shares, using the same protocols and tools that you're familiar with and enterprise applications rely on on-premises. Azure NetApp Files supports SMB and NFS protocols and can be used for various use cases such as file sharing, home directories, databases, high-performance computing and more. Additionally, it also provides built-in availability, data protection and disaster recovery capabilities.
Astra Trident is a fully supported open-source project maintained by NetApp as part of the Astra product family. Astra Trident v22.10 and later provides reliable dynamic volume provisioning, mounting and protection via snapshots of windows-based containerized application data using the Secure Message Block (SMB) volumes for Azure NetApp Files. This gives developers and operators alike the freedom to validate and deploy applications along with required volumes and class of service, while also allowing for data protection with the use of dynamic snapshots.
This document contains the prerequisites and guidelines for using Azure NetApp Files SMB shares for AKS worker nodes running windows. It then covers the Astra Trident installation and provides examples of using Astra Trident, along with Azure NetApp Files, as an AKS dynamic CSI provisioner for all your stateful windows application's data needs.
To see these steps performed in action, please view the video below:
Initial Azure NetApp Files and AKS prerequisites and configurations
This section describes the process to initially set up Azure NetApp Files for use by AKS.
AKS cluster configuration
The AKS cluster must be set up with at least one Windows node pool. The AKS cluster must have connectivity to an Active Directory. Verify that the AKS host can resolve DNS to the AKS cluster.
Azure NetApp Files initial configuration
Sign in and register the resource provider
Sign into https://portal.azure.com/. Register for the resource provider as outlined at Register for NetApp Resource Provider.
Review Azure NetApp Files networking guidelines
Review the networking architecture for Azure NetApp Files using Guidelines for Azure NetApp Files network planning. Be sure your network is configured to support your individual requirements.
Create a NetApp account
Generate an account on Azure NetApp Files if you do not already have one. See Create a NetApp account for detailed steps. For best performance, the AKS cluster and the Azure NetApp Files account should be placed in the same region.
Provision a subnet to Azure NetApp Files
Delegate a new subnet for Azure NetApp Files. The subnet must be inside a virtual network that has connectivity to Active Directory. For more detailed information and considerations, please see Delegate a subnet for Azure NetApp Files.
Create and manage Active Directory connections for Azure NetApp Files
Connect Active Directory with Azure NetApp Files; SMB volumes require an Active Directory connection. Both the AKS cluster and the Azure NetApp Files delegated subnet need to have network connectivity to the same Active Directory. Also, verify that the AKS host can resolve DNS to Azure NetApp Files endpoints. See Create and manage Active Directory connections for Azure NetApp Files for more information.
Create a capacity pool
Create a capacity pool inside the Azure NetApp Files account. The dynamic Azure NetApp Files SMB volumes for your Windows application will be provisioned inside this capacity pool. For instructions, please see Create a capacity pool for Azure NetApp Files.
Installing and configuring the Astra Trident CSI driver for Kubernetes
Astra Trident requires v22.10 or later to enable dynamic provisioning with AKS and Windows worker nodes using the SMB protocol with Azure NetApp Files. This section describes the steps needed to install and configure Astra Trident with Azure NetApp Files.
Verify prerequisites
All the steps outlined in Initial Configurations and Prerequisites must be completed prior to continuing in this section.
Make sure to review the requirements and ensure any Astra Trident pre-requisites are met. See Before you begin for details. AKS installs any required drivers on the worker nodes by default.
Install Astra Trident
One of several methods may be used to install Astra Trident. Be sure to set the windows flag during any installation method to allow Astra Trident installation on Windows nodes. The various installation methods are described in Choose your installation method.
One method using Helm is shown below. Helm must be installed on your local workstation prior to using this method. More information is found at Deploy Trident operator and install Astra Trident using Helm.
$ helm repo add netapp-trident https://netapp.github.io/trident-helm-chart
$ helm install trident netapp-trident/trident-operator --version 23.04.0 --create-namespace --namespace trident --set windows=true
After any installation method, verify the Astra Trident pods are running.
$ kubectl get pods -n trident
NAME READY STATUS RESTARTS AGE
trident-controller-cdb6ccbc5-cwqrv 6/6 Running 0 28s
trident-node-linux-dkv82 2/2 Running 0 28s
trident-node-windows-bn8hq 3/3 Running 0 28s
trident-node-windows-lrbjb 3/3 Running 0 28s
trident-node-windows-v5tgs 3/3 Running 0 28s
trident-operator-74977bc66d-5c4gj 1/1 Running 0 50s
Configure Astra Trident
Create an Astra Trident backend json file for the Azure NetApp Files capacity pool. An example is shown below. Update the subscriptionID, tenantID, clientID, clientSecret and location, and you may also change the backendName. The tenantID, clientID, and clientSecret must be from an App Registration in Azure Active Directory with sufficient permissions to the Azure NetApp Files service.
backend.json:
{
"version": 1,
"storageDriverName": "azure-netapp-files",
"backendName": "anf-smb",
"subscriptionID": "<subscription_ID>",
"tenantID": "<tenant_ID>",
"clientID": "<client_ID>",
"clientSecret": "client_secret",
"location": "location",
"nasType": "smb"
}
Apply the backend.
$ ./tridentctl create backend -f backend.json -n trident
You can also create a backend using kubectl. More information is found at Create backends with kubectl.
Ensure the new backend state is online.
$ ./tridentctl get backend -n trident
+---------+--------------------+--------------------------------------+--------+---------+
| NAME | STORAGE DRIVER | UUID | STATE | VOLUMES |
+---------+--------------------+--------------------------------------+--------+---------+
| anf-smb | azure-netapp-files | 1b64d075-3c73-4340-90da-8fda0d757c74 | online | 0 |
+---------+--------------------+--------------------------------------+--------+---------+
More information on creating an Astra Trident backend for Azure NetApp Files, including using virtual pools to allow access to different Azure NetApp Files service levels located at Configure an Azure NetApp Files backend.
Using the Astra Trident CSI driver for Kubernetes
Upon recognizing a new persistent volume claim (PVC), Astra Trident will create a Kubernetes persistent volume (PV) and a SMB volume in your Azure NetApp Files capacity pool and automatically mount to the windows pod associated with the PV. This section describes how to dynamically provision volumes and provide protection using Astra Trident.
Create a secret with the domain credentials
Create a secret with the domain credentials to authenticate to your Active Directory server. Include your domain as part of your username in the secret as shown below. Here, we create a secret called smbcreds. Update the domain, username and password with your information.
$ kubectl create secret generic smbcreds --from-literal= username='<domain>\<user>' --from-literal=password='<password>'
Verify the secret is created.
$ kubectl get secret smbcreds
NAME TYPE DATA AGE
smbcreds Opaque 2 47h
Create a storage class
Create a manifest file for the storage class. We use the following example. Update the name of the secret and the namespace where the secret is located. You may also change the name of the storage class if desired. Multiple storage classes may be created if desired to associate with different QoS values and more information may be found in Storage Class Definitions.
Storageclass.yaml
---
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: anf-sc-smb
provisioner: csi.trident.netapp.io
parameters:
backendType: "azure-netapp-files"
trident.netapp.io/nasType: "smb"
csi.storage.k8s.io/node-state-secret-name: "smbcreds"
csi.storage.k8s.io/node-stage-secret-namespace: "default"
Apply the storage class to your cluster:
$ kubectl create -f storageclass.yaml
Create a persistent volume claim
Create a PVC manifest file. We use the following configuration as an example and use the storage class configured above.
pvc-smb-anf.yaml
---
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: smb-content
spec:
accessModes:
- ReadWriteMany
resources:
requests:
storage: 100Gi
storageClassName: anf-sc-smb
Run the following commands to apply the PVC to your desired namespace. The first command creates a new namespace. You can change the name of the namespace to an appropriate name for your environment. The second command deploys the PVC in the namespace.
$ kubectl create ns webserver
$ kubectl create -f pvc-smb-anf.yaml -n webserver
Astra Trident will create the Kubernetes PV from the PVC and the backend SMB volume on Azure NetApp Files.
Check that the PV and PVC are created, and that the status is Bound.
$ kubectl get pv,pvc -n webserver
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE
persistentvolume/pvc-8848b516-3636-4f3b-b0c6-68c3f2118af4 100Gi RWX Delete Bound webserver/smb-content anf-sc-smb 4m34s
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
persistentvolumeclaim/smb-content Bound pvc-8848b516-3636-4f3b-b0c6-68c3f2118af4 100Gi RWX anf-sc-smb 9m39s
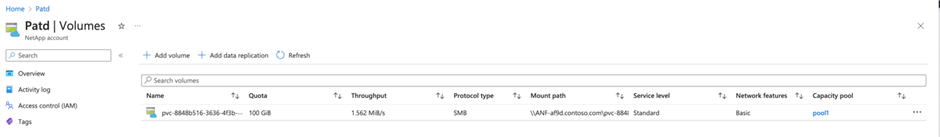
Check the volume on Azure NetApp Files. It should have the same name as the new PV.
You can check the volume name on Azure NetApp Files matches the Kubernetes PV.
Create a deployment
This section deploys an application to mount, populate and use the new volume. It tests that the Azure NetApp Files SMB share is mounted to the pod.
Create a manifest file to deploy your application. As an example, the below yaml file contains both the deployment and a service of type loadbalancer to deploy and access an IIS webserver application from outside the cluster. It also provides the mount path from the volume to the inetpub/wwwroot directory within the container, and places it on a windows worker node.
deploymentsvciis.yaml:
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: webserver
labels:
app: web
spec:
replicas: 1
template:
metadata:
name: webserver
labels:
app: web
spec:
nodeSelector:
"kubernetes.io/os": windows
volumes:
- name: smb
persistentVolumeClaim:
claimName: smb-content
containers:
- name: web
image: mcr.microsoft.com/windows/servercore/iis:latest
resources:
limits:
cpu: 1
memory: 800M
ports:
- containerPort: 80
volumeMounts:
- name: smb
mountPath: "/inetpub/wwwroot"
readOnly: false
selector:
matchLabels:
app: web
---
apiVersion: v1
kind: Service
metadata:
name: web
spec:
type: LoadBalancer
ports:
- protocol: TCP
port: 80
selector:
app: web
Run the following command to enable the deployment and service:
$ kubectl create -f deploymentsvciis.yaml -n webserver
Check that a pod was created, and that its state is Running. The LoadBalancer service should be given an external IP address.
$ kubectl get pods -n webserver
NAME READY STATUS RESTARTS AGE
webserver-b74875c86-hs4lp 1/1 Running 0 3m18s
$ kubectl get svc -n webserver
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
web LoadBalancer 10.0.64.251 20.81.106.100 80:30049/TCP 5m1s
Check the external volume is mounted to the correct directory via smb.
$ kubectl describe pod webserver-b74875c86-hs4lp -n webserver | grep -A 1 Mounts:
Mounts:
/inetpub/wwwroot from smb (rw)
Add data to the volume and check access
Create an index.html file with some sample content to populate the persistent volume to test access. (Alternatively, a new container image could be created and deployed that populates the volume during container creation time). Change the pod name to your pods name and run the following command to copy the index.html file into the containers /inetpub/wwwroot directory, which is mounted to the SMB volume:
$ kubectl cp index.html webserver-b74875c86-hs4lp:/inetpub/wwwroot/index.html -n webserver
Check access to your web page. Use the LoadBalancers External IP address obtained above. Our example shows 20.81.106.100.
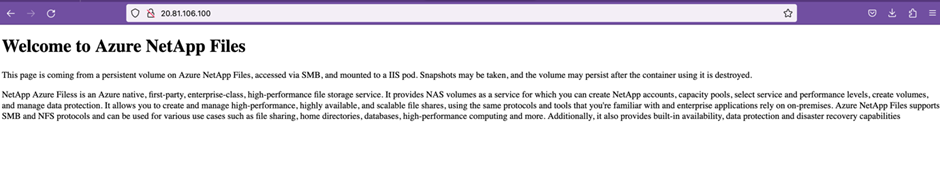
Check the file from within the container.
$ kubectl exec -it webserver-b74875c86-hs4lp -n webserver -- powershell.exe
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\> cd /inetpub\wwwroot
PS C:\inetpub\wwwroot> ls
Directory: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/12/2023 6:04 PM 1161 index.html
Create a volume snapshot
To provide extra protection, we can create a snapshot of the persistent volume using Astra Trident.
Ensure the volumesnapshot controller is installed on your cluster. AKS installs the Custom Resource Definitions (CRDs) for you. Please see Deploying a Volume Snapshot Controller for more information. Create a volumesnapshotclass.
Generate a volumesnapshot manifest file. An example is shown below.
snapshot.yaml:
apiVersion: snapshot.storage.k8s.io/v1
kind: VolumeSnapshot
metadata:
name: pvc1-snap
spec:
volumeSnapshotClassName: csi-snapclass
source:
persistentVolumeClaimName: smb-content
Apply the file to take a snapshot of the PV bound with the smb-content PVC and check the snapshot.
$ kubectl create -f snapshot.yaml -n webserver
volumesnapshot.snapshot.storage.k8s.io/pvc1-snap created
$ kubectl get volumesnapshot -n webserver
NAME READYTOUSE SOURCEPVC SOURCESNAPSHOTCONTENT RESTORESIZE SNAPSHOTCLASS SNAPSHOTCONTENT CREATIONTIME AGE
pvc1-snap true smb-content 100Gi csi-snapclass snapcontent-8acd4953-0393-4c1d-9c70-bffd3c9df3fe 16s 21s
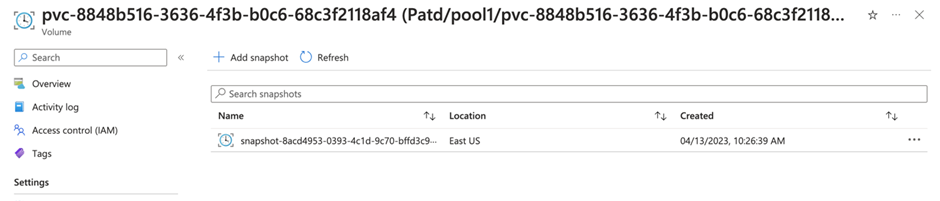
Check the snapshot on Azure NetApp Files.
You can also create a new PVC using the snapshot data and mount it to a new container to make a clone or for recovery. See Create PVCs from VolumeSnapshots for further information.
Summary
Azure NetApp Files provides all the performance and robustness required by modern enterprise cloud-native applications with both NFS and SMB protocols. With the use of open-source CSI driver, Astra Trident, it is easy dynamically provision and protect cloud-native containerized applications data running on Azure Kubernetes Service Windows worker nodes using SMB volumes. Set it up and try it out! Then, you can get on with the more fun work of designing architectures and applications and not worry about your production applications data.
Additional Information
To learn more about the information that is described in this document, review the following documents and/or websites:
- https://azure.microsoft.com/services/netapp/
- https://www.netapp.com/support-and-training/documentation/
- https://learn.microsoft.com/cli/azure/netappfiles?view=azure-cli-latest
- https://docs.netapp.com/us-en/trident/trident-get-started/kubernetes-deploy.html
- https://docs.netapp.com/us-en/trident/trident-use/anf.html
- https://github.com/NetApp/trident
- https://learn.microsoft.com/azure/aks/azure-netapp-files#provision-azure-netapp-files-volumes-dynamically
- https://anfcommunity.com/