Confidential VM node pool with AMD SEV-SNP protection available on AKS in public preview
Published Monday, August 1, 2022
Microsoft’s zero-trust policy aims at eliminating threats from malicious admins who have physical access to on-prem computing resources, as well as those within the cloud service provider. With the general availability of confidential virtual machines utilizing 3rd Gen AMD EPYC™ processors, organizations can deploy Azure virtual machines with higher level of protections from Hypervisor and Datacenter admins with encrypted memory and guest attestation capability rooted to the hardware.
We’re excited to announce that Microsoft’s latest offering in its industry leading confidential computing portfolio focuses on transitioning on-prem Kubernetes managed infrastructure to the cloud. Azure Kubernetes Service (AKS) provides enterprise security capabilities for organizations to deploy containers at scale. AKS is the first to market in enabling confidential VM with AMD SEV-SNP node pools in Kubernetes, adding defense-in-depth to Azure's hardened security profile.
Azure confidential VMs (DCav5/ECav5) are VM based Hardware Trusted Execution Environment (TEE) that leverage SEV-SNP security features to deny the hypervisor and other host management code access to VM memory and state, providing defense in depth protections against operator access. It enables easy migration of legacy workloads with no code changes and minimal performance impact. Having confidential VMs on AKS allows organizations to shift their highly sensitive, regulated resources from resource restrictive on-prem environments to Azure and benefit from the full feature support of AKS.
Lift and Shift with full AKS feature support
Confidential node pools on AKS enable a seamless lift-and-shift of Linux container workloads. Migrating to AKS means that organizations can now opt into a highly scalable, full AKS feature parity without the overhead of changing code or performance degradation. You can target sensitive workloads to confidential nodes using simple node pool affinity annotations through pod spec yaml/helm changes.
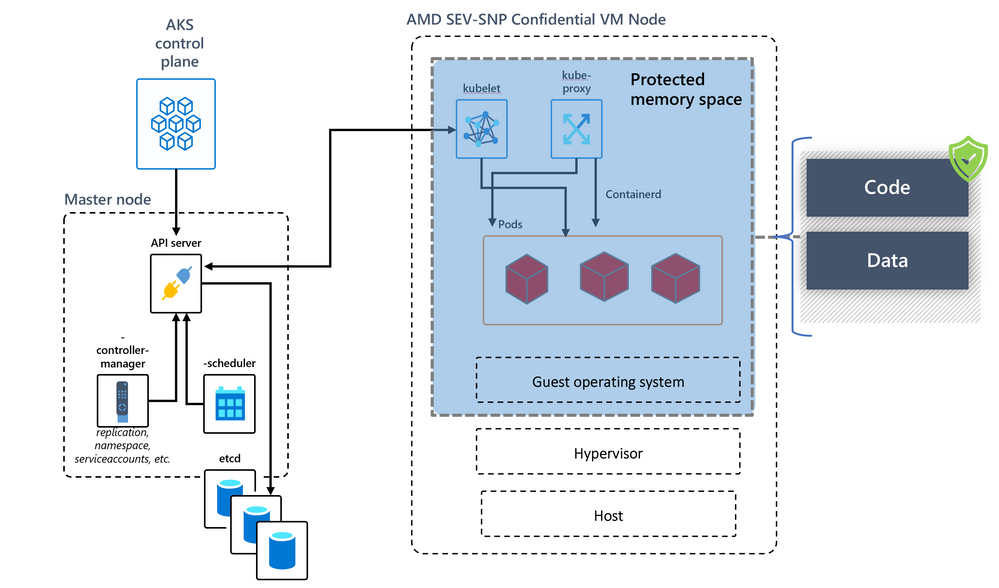
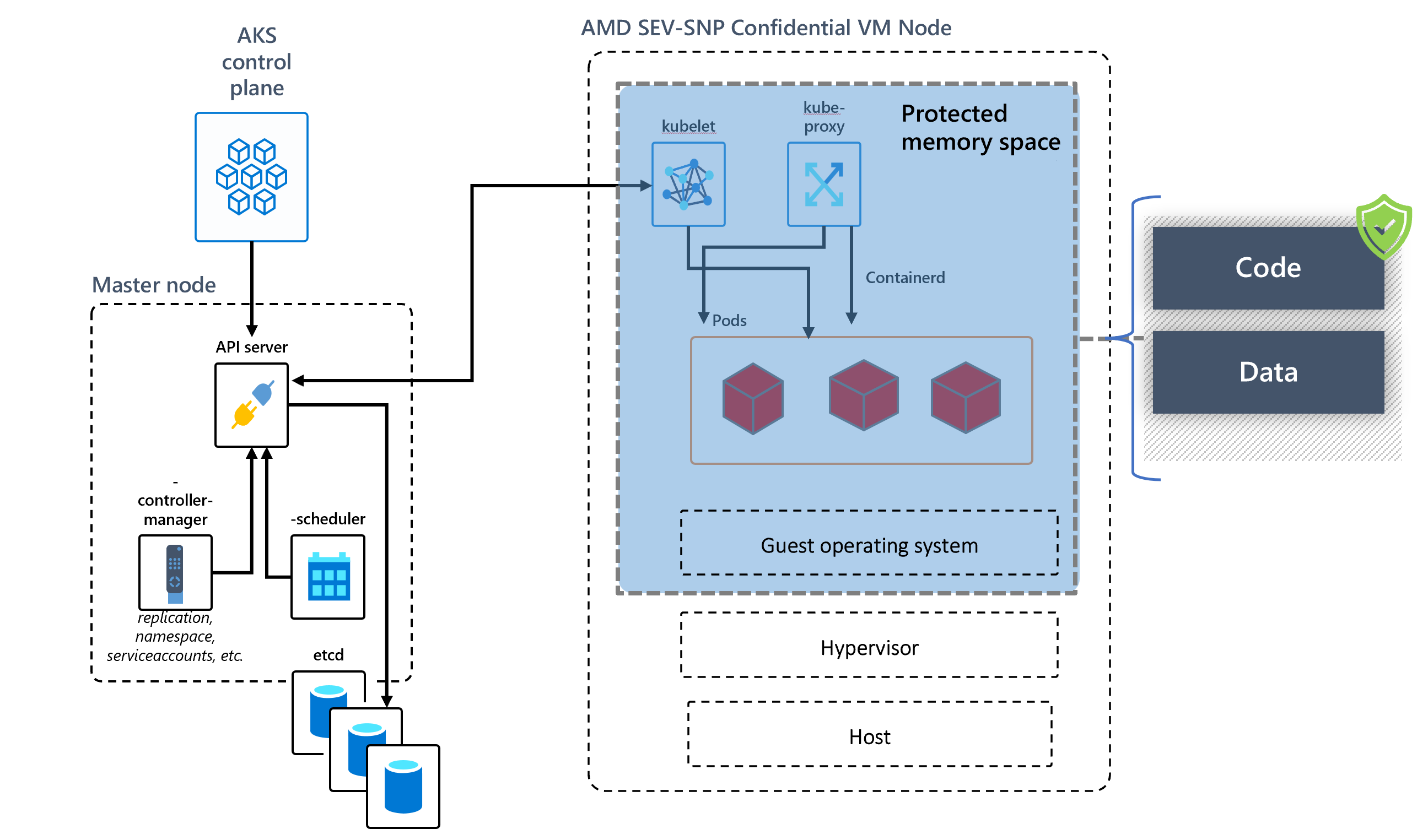
Heterogenous Node Pools
AKS is now equipped to have confidential and non-confidential node pools in a single cluster. This means apps processing sensitive data can reside in a VM-level TEE node pool with memory encryption keys generated from the chipset itself. The DCasv5 and ECasv5 confidential VMs will also support remote guest attestation allowing AKS admins to target pod deployments to only attested nodes in the near future. The below picture shows AKS node's code and data under the AMD SEV-SNP memory protection.
Get Started
You can add confidential VM node pools to an existing AKS cluster using the az aks nodepool add command. Specify the name cvmnodepool, and use the --node-vm-size parameter to specify the Standard_DC2as_v5 size:
This confidential VM size is a part of our generally available DCasv5 and ECasv5 confidential VM-series, click to learn more.
Continue to website...