Announcing general availability of guest attestation for confidential VMs
Published Wednesday, October 12, 2022
Establishing that the underlying cloud infrastructure or a cloud service is in a desired good state is paramount in a confidential computing environment. Minimally, a desired good state is one where the underlying trusted execution environment provides memory and integrity protection. Without an established good state, relying services cannot ensure that confidential computing promises are met and risk negatively impacting their security posture.
Attestation is a key function in the confidential computing ecosystem. Attestation enables verifying trustworthiness (good state) of trusted execution environment. Today, we are excited to announce the general availability of guest attestation for confidential VMs, a new feature that provides customers a means to perform remote attestation to establish trustworthiness of a confidential VM.
Confidence in confidential computing environment
With guest attestation, a relying party can have increased confidence that their software inside a confidential VM that is in a desired good state – memory encryption and integrity security features in confidential hardware platform (e.g.: AMD 3rd Gen EPYC CPUs with SEV-SNP), including secure boot, virtual TPM, etc.
Some of the common customer scenarios for guest attestation are:
- Ensure a Confidential VM is running on a trusted execution environment with memory encryption and integrity confidential hardware platform (currently AMD only) before launching a sensitive workload. This is a basic use of guest attestation.
- Ensure a Confidential VM in a desired good state with properties such as secure boot enabled (protects against rootkits – firmware, bootloader, kernel malware), vTPM, and other claims before launching a sensitive workload.
- Ensure that a relying party is presented evidence that a Confidential VM is running on a confidential hardware platform and in a good state to engage with for making sensitive transactions.
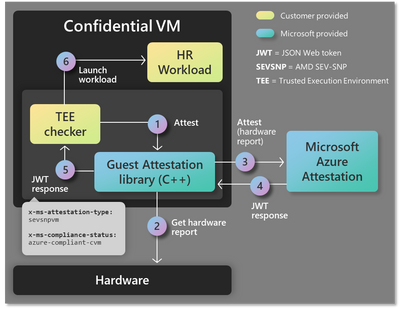
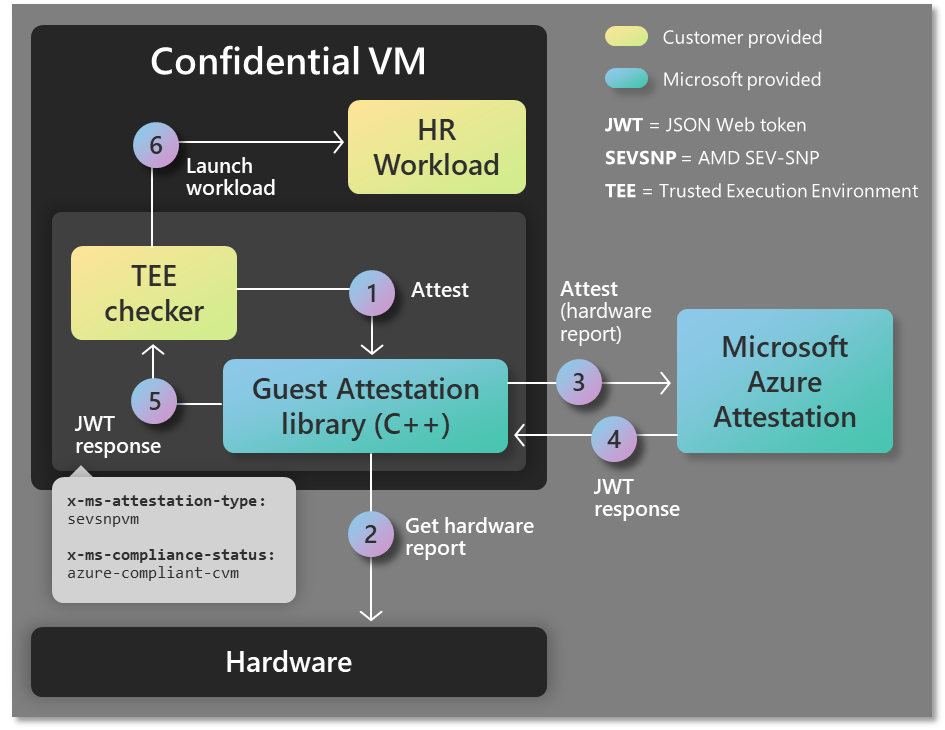
The first scenario is described in this diagram above. Attestation requests are performed by a standalone TEE (Trusted Execution Environment) checker program to determine if the confidential VM is running on trusted execution environment before a workload is launched. To perform attestation, the TEE checker program integrates with the guest attestation library and runs inside a confidential VM. Upon making a request to the attestation library, the TEE checker parses for claims in the JWT (JSON Web Token) response to determine if the VM is a CVM (confidential Virtual Machine) and running AMD SEV-SNP hardware and then launches the sensitive HR (Human Resources) workload.
Guest attestation feature is available as an executable program that can be incorporated in a deployment script and as a library for direct integration inside another program. The above scenarios can be realized using either method. Guest attestation is supported on Windows and Linux OS.
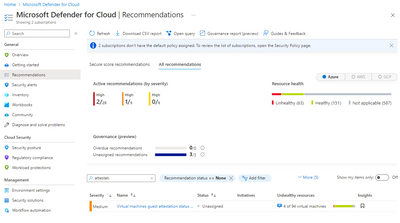
Insights into CVM health with Microsoft Defender for Cloud
Guest attestation is integrated with Microsoft Defender for Cloud (MDC). MDC ensures that your VMs are properly configured by issuing relevant recommendations, and once VMs are properly setup, MDC can detect and alert of any VM health issues.
- Recommendation to enable secure boot
- Recommendation to install guest attestation extension
- Attestation health assessment or boot integrity monitoring
- Alert for VM attestation failure
Note that the guest attestation extension for confidential VMs is required for recommendations and alerts in MDC.
Watch the demo video on guest attestation.
Guest attestation is available in all Azure public cloud regions where confidential VMs are available. To learn more and get started with guest attestation, and related ACC offerings, visit the following resources:
- Guest attestation
- Attestation helper, library on github.com
- Guest attestation documentation
- Demo video
- Microsoft Azure Attestation
- Azure confidential VMs
- Azure confidential computing
If you would like to engage further with the ACC team, please contact us at Azure confidential computing PMs
Continue to website...