Azure Firewall: New Embedded Workbooks

After our previous announcement in August 2023, we want to delve deeper into the enhanced capabilities of the new embedded workbooks. Within Azure, Workbooks serve as a versatile canvas for conducting data analysis and generating visually compelling reports directly within the Azure portal. They empower users to access diverse data sources across Azure, amalgamating them into cohesive, interactive experiences. Workbooks enable the amalgamation of various visualizations and analyses, making them ideal for unrestricted exploration.
Notably, the Azure Firewall Portal has now incorporated embedded workbooks functionality, offering customers a seamless means to analyze Azure Firewall traffic. This feature facilitates the creation of sophisticated visual reports within the Azure portal, allowing users to leverage data from multiple Firewalls deployed across Azure and unify them into interactive, cohesive experiences.
The Embedded Workbook presents users with consolidated information through charts and logs. It is structured into distinct sections, covering Application rules, Network rules, DNS proxy, Intrusion Detection and Prevention System (IDPS), Threat intelligence, and Investigation. Designed to function across multiple tenants and subscriptions, it offers filtering capabilities for various firewalls. Users can filter their firewalls and resource groups, dynamically refining results by category, providing easily interpretable data sets for investigating firewall-related issues. This powerful tool enables users to gain insights into Azure Firewall events, comprehend application and network rules, and access statistics detailing firewall activities across URLs, ports, and IP addresses.
Prerequisites
To use Azure Firewall embedded workbook, you must enable Azure Firewall logging and send it to your analytics workspace. Follow these steps to enable logging:
- Navigate to your Azure Firewall resource.
- Under Monitoring, select the Diagnostic settings tab.
- Create a new diagnostic setting.
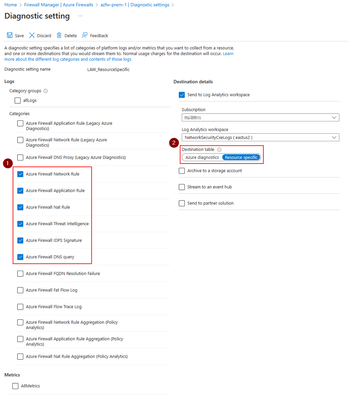
- When creating a new diagnostic setting, enable the following logging categories to ensure that the workbook is populated with all the required logs and works properly:
- Azure Firewall Network Rule
- Azure Firewall Application Rule
- Azure Firewall NAT Rule
- Azure Firewall Threat Intelligence
- Azure Firewall IDPS Signature
- Azure Firewall DNS Query
- Choose ‘Send to Log Analytics workspace’ and select your log analytics workspace where you want to store Firewall logs.
- Under ‘Destination table’, make sure to choose ‘Resource specific’ for the resource-specific table.
Note: Make sure that you are using the new ‘resource specific’ table logging and not the legacy ‘azure diagnostics’ for this workbook to properly work. To learn more about the resource specific logs see here Exploring the New Resource Specific Structured Logging in Azure Firewall - Microsoft Community Hub
Getting started
Once you've set up Firewall logging, you're all set to utilize the Azure Firewall embedded workbooks effortlessly using the following straightforward steps:
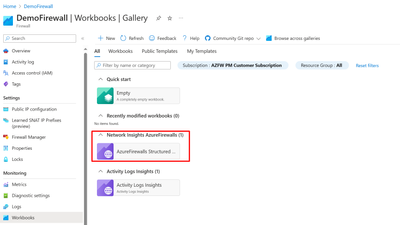
- Navigate to your Azure Firewall resource.
- Under Monitoring, select the Workbooks blade.
- In Gallery, you should be able to create new workbooks or utilize the existing Azure Firewall workbook as shown below:
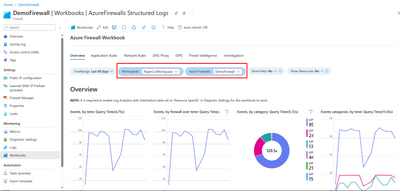
- Select the log analytics workspace and one or more firewall names you would like to use in this workbook as shown below:
Azure Firewall Workbook Sections:
The Azure Firewall workbook comprises seven tabs, each addressing distinct aspects of the service. Let's examine them individually:
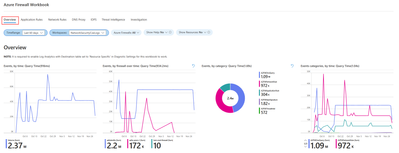
1. Overview
The overview tab showcases graphs and statistics related to all types of firewall events aggregated from various logging categories, including Network rules, Application rules, DNS, Intrusion Detection and Prevention System (IDPS), Threat Intelligence, and more. The available widgets in Overview tab include:
- Events, by time: Displays event frequency over time.
- Events, by firewall over time: Shows event distribution across firewalls over time.
- Events, by category: Categorizes and counts events.
- Events categories, by time: Displays event categories over time.
- Average Throughput of Firewall Traffic: Shows average data passing through the firewall.
- SNAT Port Utilization: Displays usage of SNAT ports.
- Network Rule Hit count (SUM): Counts network rule triggers.
- Application Rule Hit count (SUM): Counts application rule triggers.
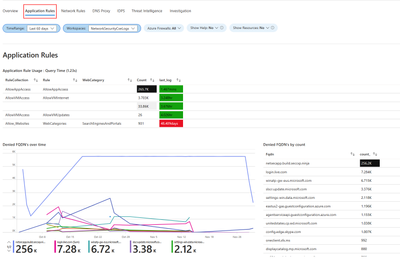
2. Application Rules
The Application rules tab shows layer 7 related events statistics correlated with the customer’s specific application rules in Azure firewall policy. Available widgets in Application Rules tab:
- Application Rule Usage: Shows usage of application rules.
- Denied FQDN's overtime: Displays denied Fully Qualified Domain Names (FQDNs) over time.
- Denied FQDN's by count: Counts denied FQDNs.
- Allowed FQDN's overtime: Displays allowed FQDNs over time.
- Allowed FQDN's by count: Counts allowed FQDNs.
- Allowed Web Categories overtime: Shows allowed web categories over time.
- Allowed Web Categories by count: Counts allowed web categories.
- Denied Web Categories overtime: Displays denied web categories over time.
- Denied Web Categories by count: Counts denied web categories.
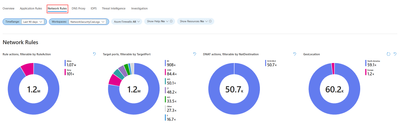
3. Network Rules
The Network rules tab shows layer 4 related events statistics correlated with the customer’s specific network rules in Azure firewall policy. Available widgets in Network Rules tab:
- Rule actions: Displays actions taken by rules.
- Target ports: Shows targeted ports in network traffic.
- DNAT actions: Displays actions of Destination Network Address Translation (DNAT).
- GeoLocation: Shows geographical locations involved in network traffic.
- Rule actions, by IP addresses: Displays rule actions categorized by IP addresses.
- Target ports, by Source IP: Shows targeted ports categorized by source IP addresses.
- DNAT'ed over time: Displays DNAT actions over time.
- GeoLocation over time: Shows geographical locations involved in network traffic over time.
- Actions, by time: Displays network actions over time.
- All IP addresses events with GeoLocation: Shows all events involving IP addresses, categorized by geographical location.
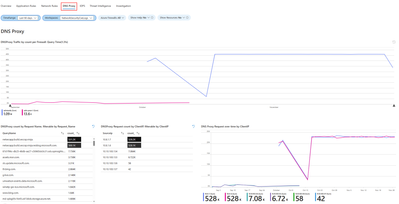
4. DNS Proxy
This segment pertains to customers who have set up Azure Firewall to function as a DNS proxy, serving as an intermediary for DNS requests from client virtual machines to a DNS server. The DNS Proxy tab includes various widgets for your use:
- DNS Proxy Traffic by count per Firewall: Displays DNS proxy traffic count for each firewall.
- DNS Proxy count by Request Name: Counts DNS proxy requests by request name.
- DNS Proxy Request count by Client IP: Counts DNS proxy requests by client IP address.
- DNS Proxy Request over time by Client IP: Displays DNS proxy requests over time, categorized by client IP.
- DNS Proxy Information: Provides log information related to your DNS proxy setup.
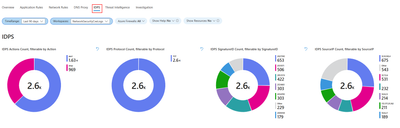
5. Intrusion Detection and Prevention System (IDPS)
The IDPS log statistics tab offers a summary of malicious traffic events and the preventive actions undertaken by the service. Within the IDPS tab, you'll find various widgets at your disposal:
- IDPS Actions Count: Counts Intrusion Detection and Prevention System (IDPS) actions.
- IDPS Protocol Count: Counts protocols detected by IDPS.
- IDPS SignatureID Count: Counts IDPS detections by signature ID.
- IDPS SourceIP Count: Counts IDPS detections by source IP address.
- Filtered IDPS Actions by Count: Counts filtered IDPS actions.
- Filtered IDPS Protocols by Count: Counts filtered IDPS protocols.
- Filtered IDPS SignatureIDs by Count: Counts filtered IDPS detections by signature ID.
- Filtered SourceIP: Displays filtered source IPs detected by IDPS.
- Azure Firewall IDPS count over time: Shows Azure Firewall IDPS count over time.
- Azure Firewall IDPS logs with GeoLocation: Provides Azure Firewall IDPS logs, categorized by geographical location.
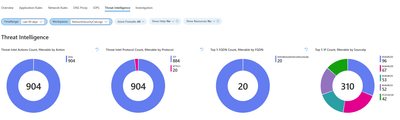
6. Threat intelligence (TI)
This page offers a thorough perspective on threat intelligence activities, spotlighting the most prevalent threats, actions, and protocols. It delineates the top 5 Fully Qualified Domain Names (FQDNs) and IP addresses associated with these threats, showcasing threat intelligence detections over time. Additionally, detailed logs from Azure Firewall’s Threat Intelligence are furnished for comprehensive analysis. Within the Threat Intelligence tab, you'll find various widgets for your utilization:
- Threat Intel Actions Count: Counts actions detected by Threat Intelligence.
- Threat Intel Protocol Count: Counts protocols identified by Threat Intelligence.
- Top 5 FQDN Count: Displays the top 5 most frequent Fully Qualified Domain Names (FQDNs).
- Top 5 IP Count: Shows the top 5 most frequent IP addresses.
- Azure Firewall Threat Intel Over Time: Displays Azure Firewall Threat Intelligence detections over time.
- Azure Firewall Threat Intel: Provides logs from Azure Firewall's Threat Intelligence.
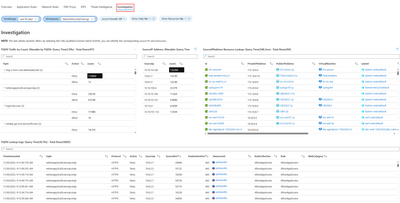
7. Investigation
The investigation section enables exploration and troubleshooting, offering additional details such as the virtual machine name and network interface name associated with the initiation or termination of traffic. It also establishes correlations between source IP addresses, the Fully Qualified Domain Names (FQDNs) they attempt to access as well as geographical location view of your traffic. Widgets available in the Investigation tab:
- FQDN Traffic by Count: Counts traffic by Fully Qualified Domain Names (FQDNs).
- SourceIP Address count: Counts occurrences of source IP addresses.
- SourceIPAddress Resource Lookup: Looks up resources associated with source IP addresses.
- FQDN Lookup logs: Provides logs from FQDN lookups.
- Azure Firewall Premium with GeoLocation – IDPS: Displays Azure Firewall's Intrusion Detection and Prevention System (IDPS) detections, categorized by geographical location.
Conclusion
The Embedded Azure Firewall Workbook emerges as a potent tool, offering users consolidated information through charts and logs. With its versatile filtering capabilities for firewalls and resource groups, coupled with dynamic category filtering, it provides easily interpretable data sets for investigating log-related issues. This tool proves invaluable for gaining insights into Azure Firewall events, understanding application and network rules, and accessing statistics on firewall activities spanning DNS, Threat Intel, and IDPS. Designed to seamlessly function across multiple tenants and subscriptions, with filter options for various firewalls, the workbook stands as a valuable addition to Azure Firewall. It significantly enhances the efficiency of monitoring, managing, and troubleshooting your Azure firewalls.