Architecting For File Security : Solution Design Approaches to Encrypting and Decrypting File Data in Dynamics 365 Finance - Part I

The security of data is one of the most pressing concerns in the digital age. Whether you're sharing sensitive information over the internet, protecting your files, or storing sensitive information, encryption is critical.
This series of posts will focus on encryption and decryption concepts, common frameworks, solution design approaches, and step-by-step implementation in Dynamics 365 Finance.
In this article, we will be looking at the core concepts and design principles of file encryption and how to go about it.
Every Dynamics 365 Finance implementation especially when the business is focused on Finance processes has a use case that involves 3rd party file integration, such as banks, contractors & partners.
Let's first understand the common use cases of file data encryption and decryption before diving into the core concepts.
What are the common use cases?
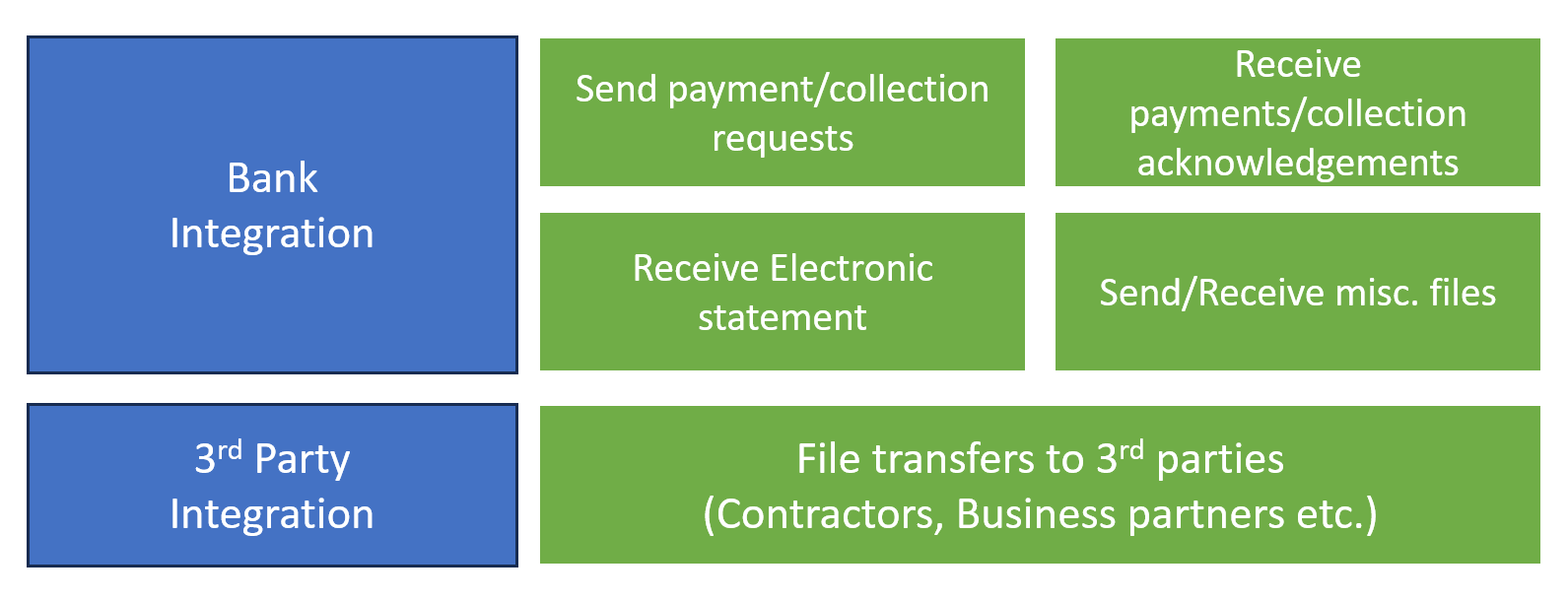
These are the list of scenarios that we used in the file integration where we need to encrypt and decrypt the file data before it is sent to third party or received from a third party.
One of the common scenarios is bank integration and any Dynamics 365 Finance transformation implementation project without this scenario is incomplete.
As we are all aware any finance application, we interact with banks for various purposes such as sending a payment collection request or receiving the payment details, acknowledgment of those payments, and electronic statements. So when there is involvement of financial data and those need to be transmitted via files there is a possibility of getting changed or altered. And to prevent that bank or customer recommends that all the communications happen via secure format so that there should not be a trade-off with security.
There can be other scenarios in 3rd party integrations such as contractors, business partners, collectively working with customers. for ex. customer used to send a file via SFTP and the contractor was managing the logistics. And they were processing the logistics based on the request sent via file.
When to Encrypt?
Whenever you have sensitive data that shouldn't be shared with the general public, such as bank files, you should encrypt it.
What is encryption & decryption?
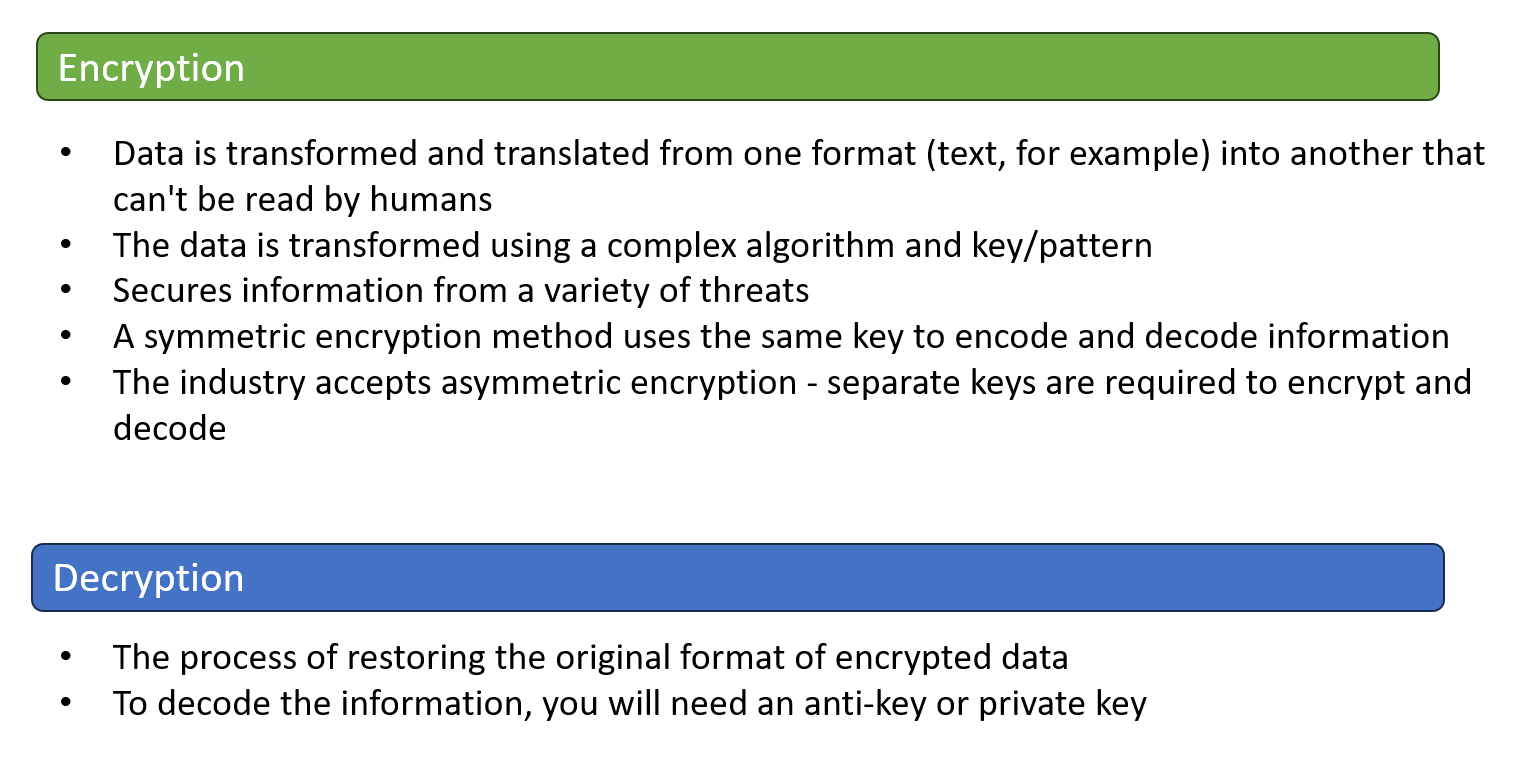
There are two types of encryptions Symmetric & Asymmetric. In the case of Symmetric, only a single key will be used for encryption or decryption. However, in the Asymmetric type encryption will happen in one pattern and decryption will follow another pattern.
Key core concepts
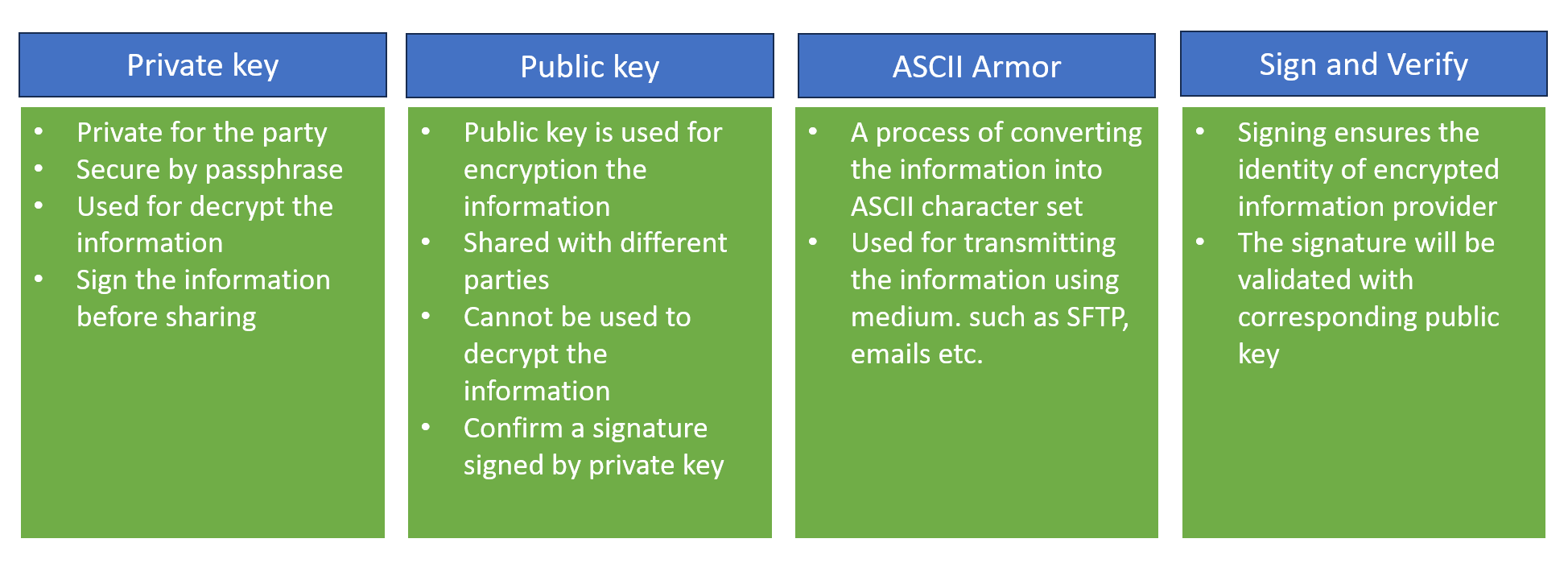
Let's understand the core concepts
A private key is a key private for the primary party and is used only for decryption and not encrypting the data. The public key used to encrypt the data before sharing it with another party. This public key can be shared with among multiple parties such as banks.
Normally bank provides the public key so that we can use their public key and encrypt the data and send it back to them.
The bank uses its own private key to decrypt the data. The public is also used for signing the information, consider the scenario where information or files are encrypted and shared with another party but another party will not know whether the information received from any channel is authenticated or not.
So, they will validate with a signature and that signature will be used through a public key, if that signature is valid then only one party can process the data.
However, in the case of ASCII Armor, when encrypting the data there is possibility that information is converting into binary format and binary format cannot be transmitted over the email or other channel such as SFTP.
So, it is advisable that that information will be converted into ASCII format so it can be easily transmitted to over various channel.
As we understand earlier, when we transmit the information to any party, another party has to validate the information whether it is received from the correct source or not. so, the receiver can validate the signature
for e.g. when we work with the bank and the bank has provided the public key so that we can encrypt the data and share it with bank. but before we share with bank, we will sign the data with the public key provided by bank and information will be transmitted to the bank. the bank will validate the signature with the public key and if it is valid then it will receive information and process it.
Common framework - Pretty Good Privacy

PGP stands for Pretty Good Privacy. It is one of the common frameworks and industry-wide accepted with various supported algorithms.
Solution design approaches
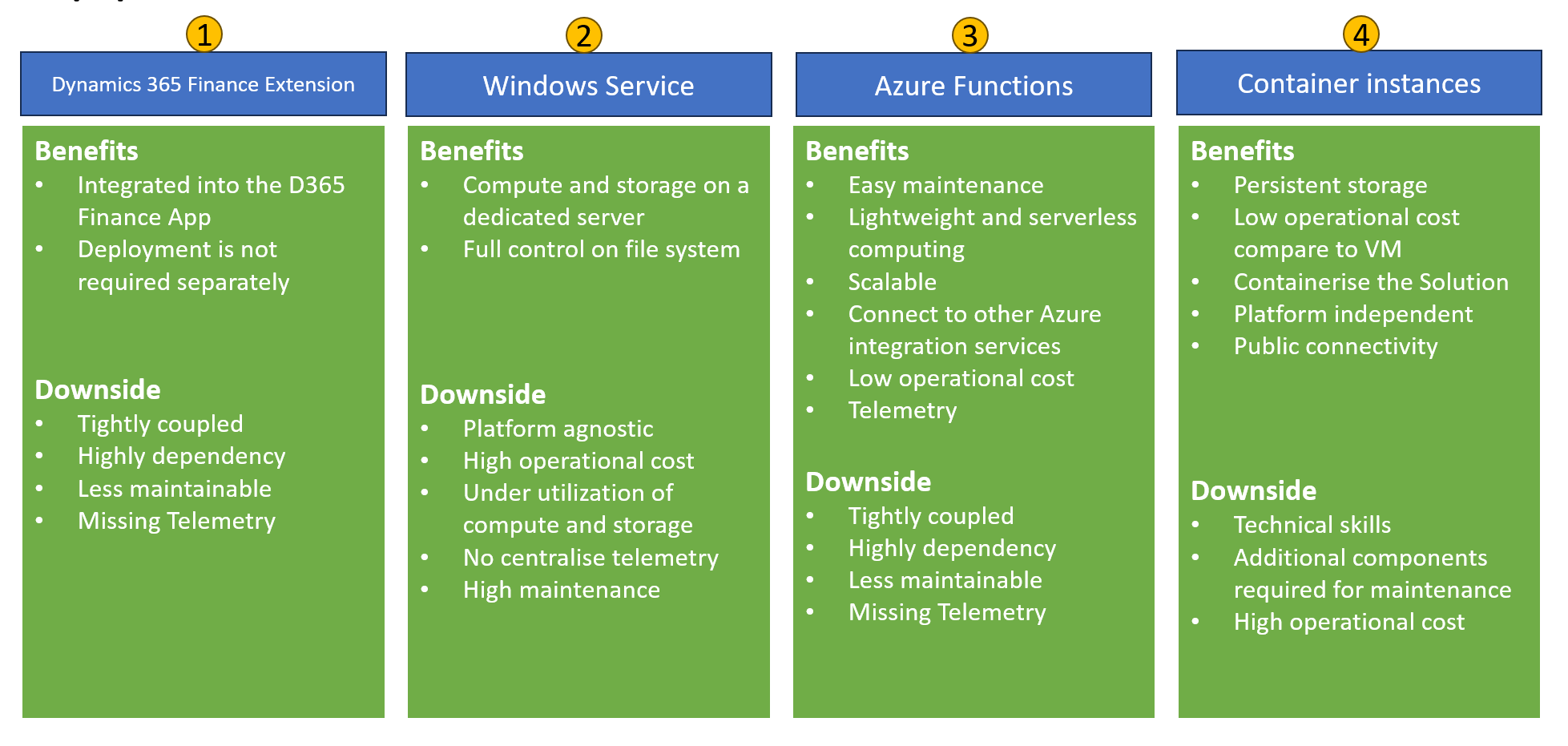
There are multiple approaches that can be considered while designing the file encryption solution.
In the first approach, where we can leverage the D365 Finance App via an extension. But it has high dependency and less control over IT Pros in case of failure or telemetry support as well as less maintainable. For e.g. change in encryption approach from the bank.
The second approach is hosting a dedicated Cloud VM by using Windows Service. On the one side, you are getting dedicated computing and storage resources. However, high operational cost & no centralized telemetry is involved.
In the third approach, leverage Azure serverless computing such as Azure Functions. One of the biggest advantages is lightweight and serverless computing as well as low operational cost. Another benefit of this approach is end-to-end telemetry and low operational cost.
The last approach is Container Instances, let's take one example where a bank uses a dedicated application before the file is sent for encryption and decryption via a specific channel. In this approach, we can create the software or package and deploy it to the Cloud. It will have a very low operational cost compared to a dedicated Virtual machine.
Reference Solution Architecture & How it works?
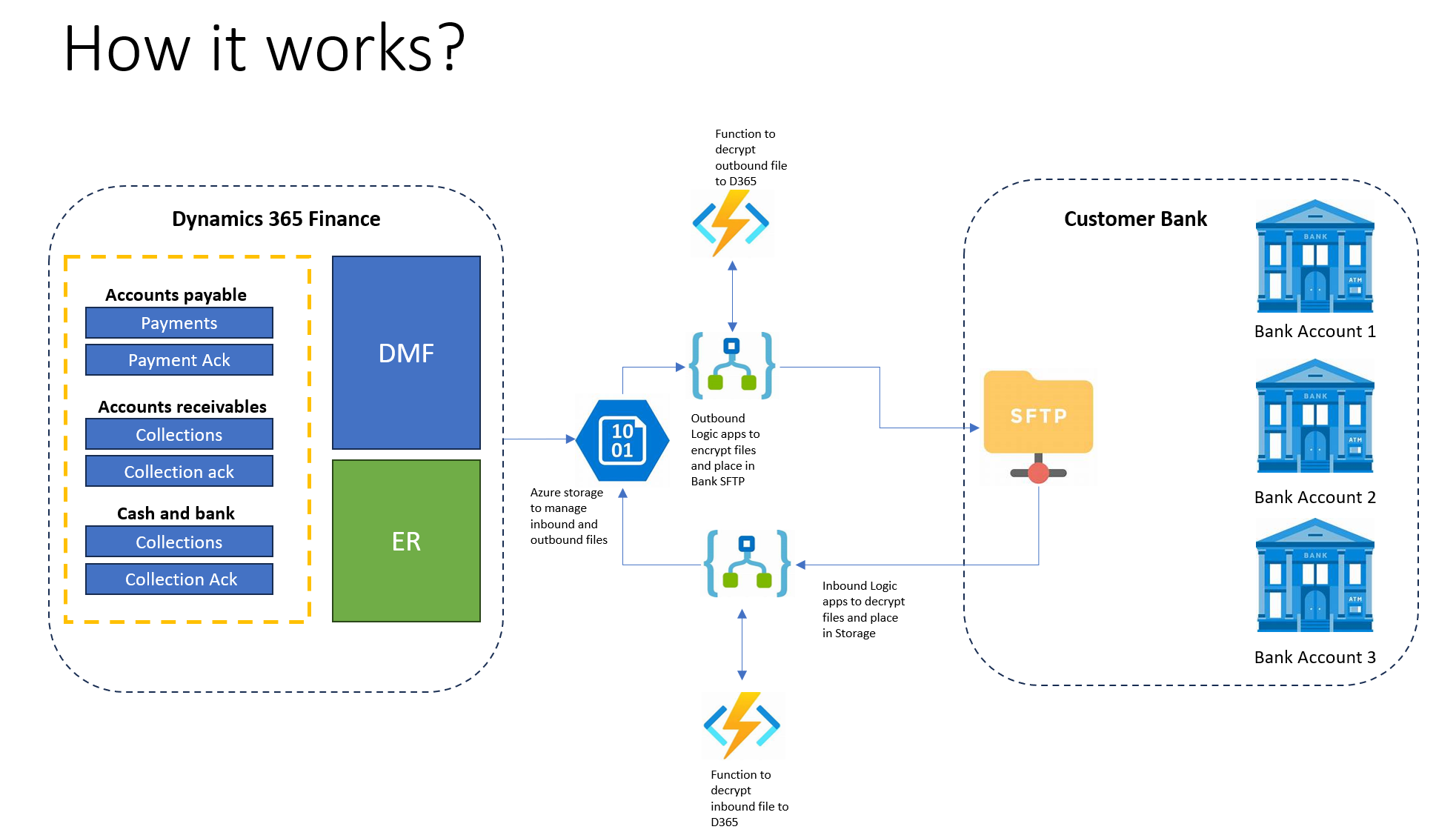
Let's understand how encryption and decryption work using Azure Function.
Let's assume payment files are being generated through Dynamics 365 Finance and sent to Azure Storage and middleware (Logic Apps or Power Automate) will encrypt the file and send it to banks. What it means is that Azure Function is being called to encrypt the file data and goes with decryption as well.
Conclusion
To conclude, encryption & decryption is an important element of data authentication and privacy. Let's deep drive practicality of Azure Function in next blog.
Thank you for Reading - Let's Connect!
Thank you for reading this piece. If you enjoyed it, please let others know. Hit the subscribe button to read more posts from this blog. LinkedIn, Twitter, YouTube
Stay tuned!
Published on:
Learn moreRelated posts
Architecting Scalable Business Logic in Dynamics CRM Using Plugin Life Cycle
Dynamics CRM Plugin Life Cycle: Optimizing for Scalability means designing plugins in a way that keeps the system fast, stable, and easy to ma...
Avoiding Currency Mismatch Errors in Dynamics 365 CE
When working with Dynamics 365 Sales, it’s important to understand how currency behaves across related entities like Opportunity, Quote, Order...
Sales Collaboration: How Sales Teams Work in Dynamics 365 CE
A Sales Team in Microsoft Dynamics 365 Sales represents a group of users who collaborate to manage and close sales opportunities efficiently. ...
Environment Variables vs Configuration Tables vs Hardcoding in Dynamics 365 Customer Engagement (CE)
In Dynamics 365 Customer Engagement (CE), managing configuration values effectively is key to building scalable and maintainable solutions. En...
Ticket sales management with Dynamics CRM in the Sports Industry
Mohona Dutta By Mohona Dutta | Reading time 5 mins So, how do you prospect? Pulling names out of lists on your laptop? Repeatedly calling...
How to create an impactful fan experience in sports with Dynamics CRM?
Mohona Dutta By Mohona Dutta | Reading time 5 mins For a salesperson, every day is game day. Sports organizations are always looking to i...
Updating JavaScript code in Dynamics CRM Made Easy for Developers
Hema Shamala By Hema Shamala | Reading time 5 mins Why do we need JavaScript in D365 CRM? It allows us to implement custom logic by using...
How To Use Advanced Find in Dynamics CRM 365
Nikhil Rajendran By Nikhil Rajendran | Reading time 5 mins One of the most commonly used features in Dynamics 365 is Advanced Find. A d...
Security Model of Dynamics CRM
Business Unit – It is a way to group business activities.When an organization is created, a Root Business Unit is created by default. Thi...