Hardening your defense in depth with secrets awareness in Azure command line tools
When using one of the Azure client tools, you will likely have to deal with secrets that are returned by the Azure APIs. A common scenario would be to retrieve a storage account key to be able to perform other operations subsequently in your pipeline.
DevOps engineer developing scripts to be used in the pipelines should pay attention to the sensitivity of the output of the commands being executed at the risk of exposing sensitive information. This becomes particularly important when the output of commands is stored in log files like this would be the case in GitHub actions or other DevOps runners.
This scenario was recently described in details in this article from Palo Alto Network.
“Forewarned is forearmed”
The issue mentioned in the blog from Palo Alto Networks has been fixed in az cli version 2.54 and Azure PowerShell v11.0, however we wanted to provide our customers with a solution that is adaptive to similar situations regardless of the command outputs format or version of the client.
We think that our customers will take the decisions that fits their business needs if we give them the adequate information. Our first step is to detect secrets in the output of any command and display a warning message when a secret has been identified.
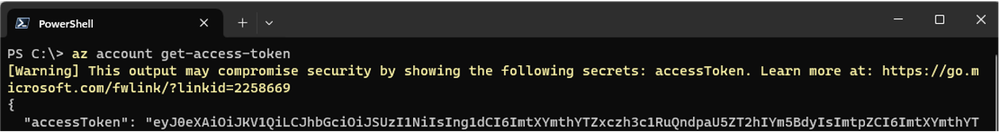
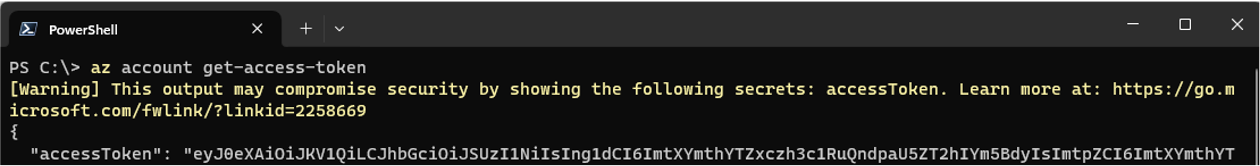
The following image shows the warning message with az cli version 2.57, available on February 6, 2024.
We will enable a similar capability in Azure PowerShell in the next few weeks, stay tuned!
Availability and default behavior
Local installation, Azure DevOps, GitHub action, etc… : Disabled by default.
Adding a warning message in the output of a command line tool may break DevOps pipelines that rely on the tool, so initially, this is disabled by default.
We encourage you to try it out and see if you are exposing secrets in any of your pipelines.
CloudShell: Enabled by default.
Because ClouShell is not indented to be used to execute pipelines and because this capability is security related, we are activating this feature by default in CloudShell.
Configuration
The following options controls the behavior of Azure CLI regarding the detection of secrets.
Environment variable
AZURE_CLIENTS_SHOW_SECRETS_WARNING=True
Value:
- True: warning message will be displayed
- False: warning message will NOT be displayed
Azure cli setting
az config set clients.show_secrets_warning=True
Warning messages will be displayed
az config set clients.show_secrets_warning=False
Warning messages will NOT be displayed
Additional considerations
Impact on your pipelines
Read the following before activating the warning message in DevOps pipelines! We use the stderr stream to show the warning message, this may cause issues if your DevOps pipeline is configured to fail in such circumstances.
For example, if the ‘failOnStderr’ parameter is set to ‘True’ of the Bash v3 task for Azure DevOps, the warning message will halt the pipeline.
Is it a good or a bad thing? It really depends how certain you are that there are no secrets in your Azure DevOps logs. You could consider enabling the warning message to identify if any secrets are exposed in your pipelines and take remediation actions.
Secrets identification
This version identifies a limited set of secrets, like access tokens, storage account keys, … and we will enrich our list in the upcoming releases.
Feedback
We believe this will help anyone using Azure CLI hardening their security defense in depth and be more conscious of secrets.
We want to hear from your experience with warning on secrets in command outputs. Please share a comment or open a GitHub issue https://github.com/Azure/azure-cli/issues/new/choose