Azure DDoS Standard Protection Now Supports APIM in VNET Integration
Introduction
Azure DDoS Protection Standard provides enhanced DDoS mitigation features to defend against volumetric and protocol DDoS attacks, such as Adaptive real time tuning, always-on traffic monitoring, Azure DDoS Rapid Response support, cost protection telemetry, monitoring, and alerting.
DDoS protection standard currently supports Public IPs in ARM based VNets such as Load Balancers, Bastion, Azure Firewall and Application Gateway. Now you can also protect your public IPs attached to VNet integrated Azure API Management (APIM) instances with Azure DDoS Protection Standard.
Scenario
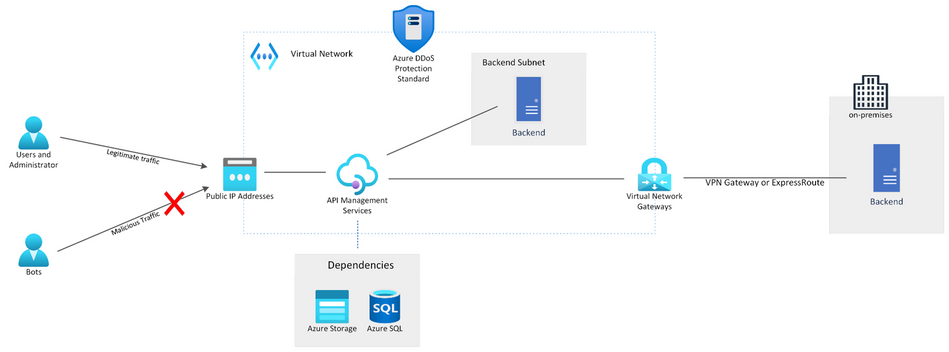
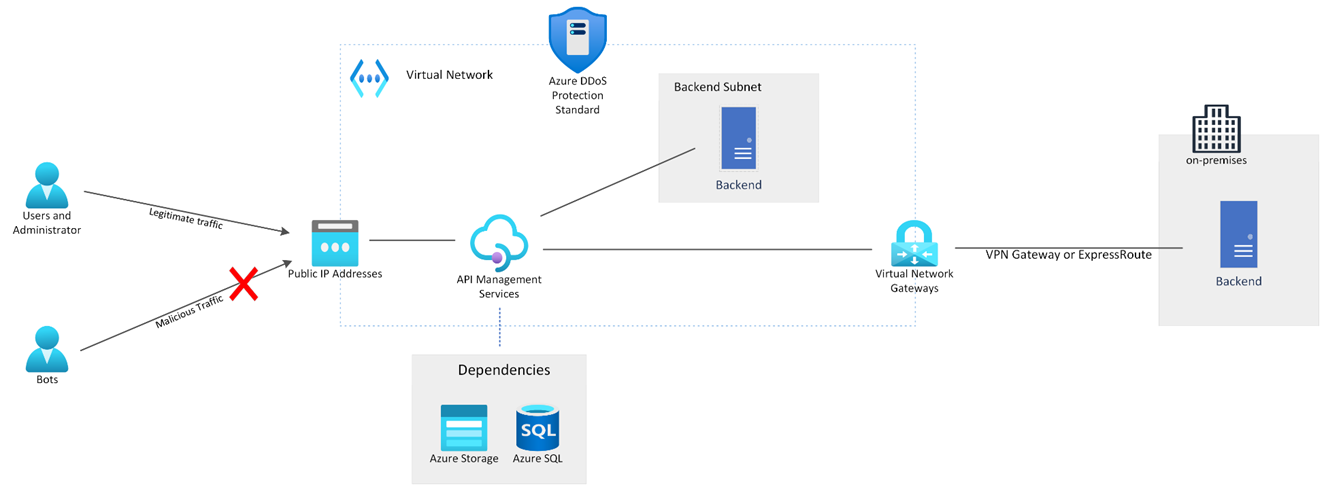
When you deploy your APIM instance in Azure virtual networks (VNets) and attach a public IP to it, you get external inbound connectivity to the gateway and API Management endpoints, giving your API Management instance secure access to other peered Azure resources and connectivity to your on-premises networks using different VPN technologies and Express route. This type of setup will open external access to private and on-premises backends, which makes your API Gateway vulnerable to DDoS attacks.
In a scenario where you have infrastructure/workloads such as gaming and sensitive web applications, even a small downtime will sustain huge financial costs and reputational damage to your organization. Attackers will try to overload the backend using bots and block legitimate traffic or bring down the system. With Azure DDoS Protection Standard, you can mitigate volumetric and protocol DDoS attacks which are targeting your APIs on Azure.
In a VNet integrated scenario you can control access by using Network Security Groups however NSGs do not provide DDoS protection for your APIM. You can also integrate with Application Gateway WAF for layer 7 protection against attacks such as SQL injection, cross-site scripting, protocol violations and so on (Something to point out here is that DDoS protection Standard was already available in a setup where you have Application Gateway intercepting the traffic before reaching the APIM instance however for this blog we will be focusing on the new DDoS protection support where you directly protect your APIM instance when it’s integrated with a VNet). If you want to learn more about Application Gateway integration with APIM see Use API Management in a virtual network with Azure Application Gateway - Azure API Management | Microsoft Learn
This blog will show you how to:
- Create APIM instance in Virtual Network setup
- Create DDoS Standard plan and configure the Public IP logging
- Identify when you’re under a DDoS attack and investigate the mitigation logs
Create APIM Instance with VNet Integration
For this blog’s purpose we will create an APIM instance with minimum configuration as shown above. Make sure to choose Virtual network as connectivity type under Virtual network tab to enable inbound connection from the internet through the VNet and get the option to enable DDoS Protection Standard. We will use the API Management instance in external mode however you can choose either Internal or External mode depending on if you require connectivity to your API Management endpoints from the internet or only within the VNet, for the second option choose Internal mode. Full configuration steps can be found here Connect to a virtual network using Azure API Management | Microsoft Learn
APIM VNet integration Requirements:
- The minimum size of the subnet in which API Management instance can be deployed is /29
- Public IP must have a Fully qualified domain name of the A DNS record associated with it
Note: Public IP attached to APIM instance is used for runtime API traffic or for managing configuration on port 3443, for more information check IP addresses of Azure API Management service | Microsoft Docs
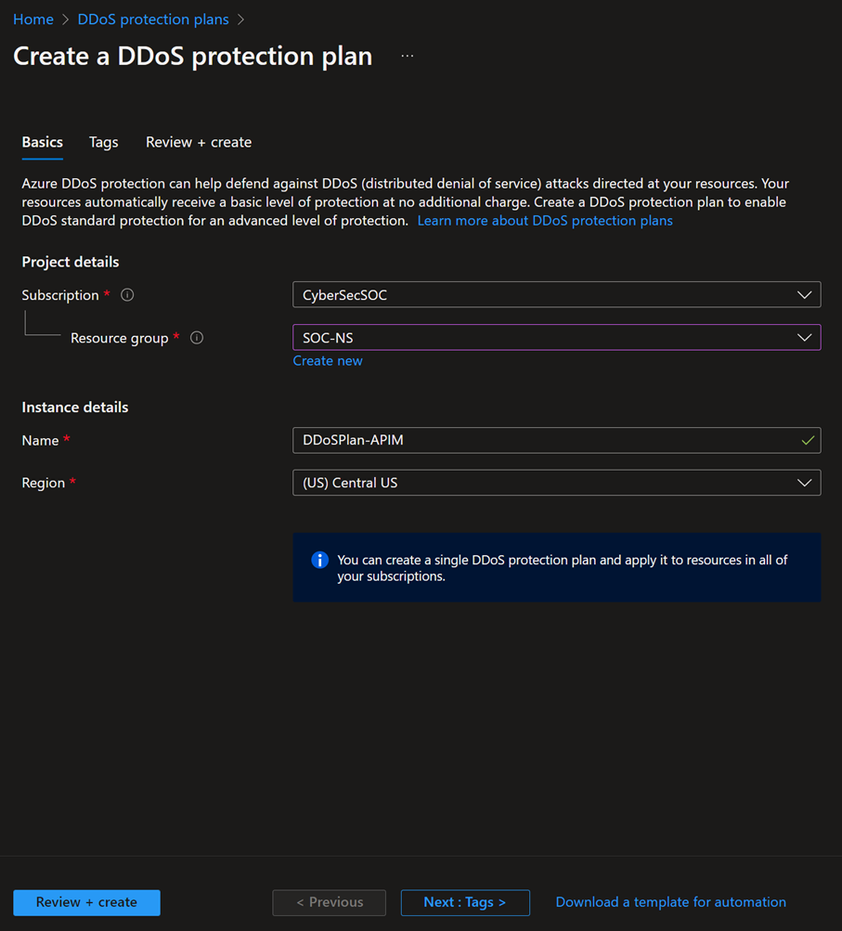
Create DDoS Protection plan
Creating Azure DDoS protection plan is straightforward. Choose your subscription and make sure that the Public IP used is under the same Tenant. DDoS Protection Standard plan spans over all subscriptions you have under the same AAD tenant.
After deploying DDoS plan, go to protected resources and add the VNet where you have the API Management instance deployed.
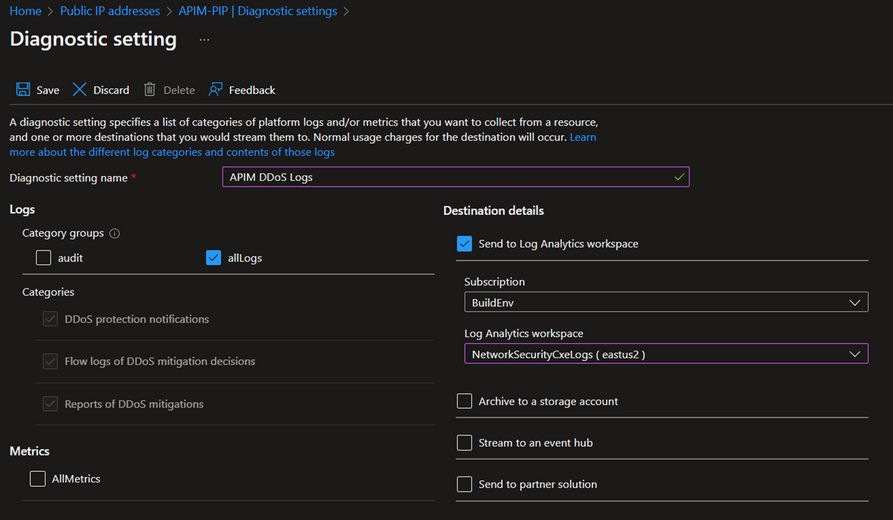
Enable logging on your Public IP
In your Public IP configuration, create a diagnostic setting with all categories selected and your log analytics workspace destination.
Testing
At this stage you should have created the APIM instance in your VNET and Azure DDoS Standard protection for the public IP. For our test we will be using our DDoS simulation partner. More information about our DDoS attack simulation partners is available here Azure DDoS Protection simulation testing | Microsoft Docs
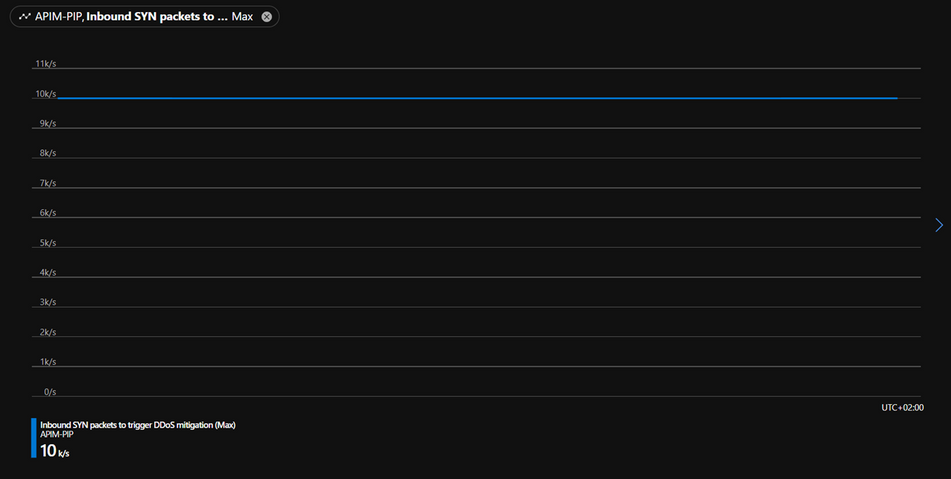
Before starting the simulation attack let’s check the metrics and current threshold for our public IP. Under your public IP resource click on metrics, add a new metric, and choose “Inbound SYN packets to trigger DDoS mitigation”.
This metric will show us the current TCP SYN packets threshold for triggering DDoS mitigation. In our case we can see that it’s 10k/s.
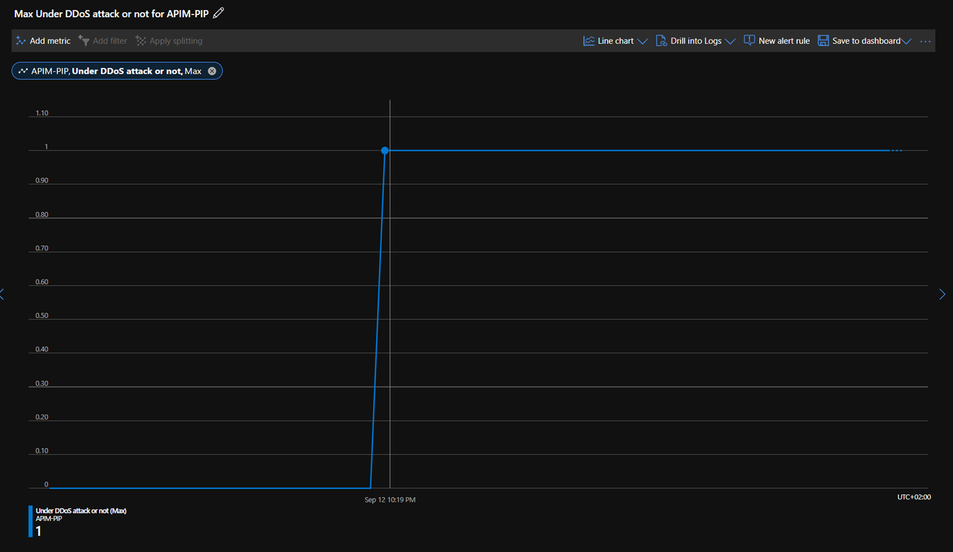
The other metric which we want to look at is “Under DDoS attack or not”. This metric has only 2 values 0 and 1:
0 = your public IP is not under DDoS attack, 1 = Your public IP is under DDoS attack and DDoS attack mitigation has started.
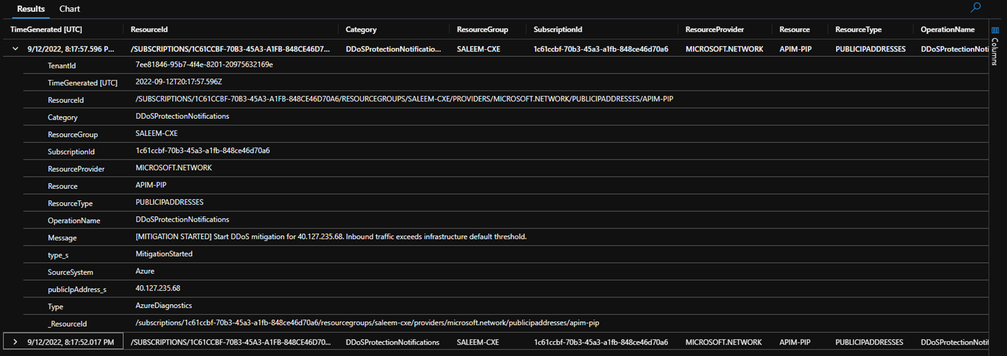
Once we start the DDoS simulation attack you will see the metric changing to 1 as shown above, DDoS attack started at 10:19PM. To get more information about this attack and its mitigation we will have a look at our logging. Go to your log Analytics workspace where you have the Public IP logs sent to and under logs run the following query:
AzureDiagnostics
| where Category == "DDoSProtectionNotifications"
We should see one entry with the message [MITIGATION STARTED] as shown in the screenshot below.
Let’s run another query with Category as "DDoSMitigationFlowLogs"
AzureDiagnostics
| where Category == "DDoSMitigationFlowLogs"
DDoS mitigation flow logs will provide us with all the logs of packets being allowed or dropped, in the example below we can see that in the message it states “Protocol violation invalid TCP syn” which means that the packet was dropped because it was identified as malicious packet.
Summary
Enabling internet connectivity to your API services creates a huge risk of getting attacked by DDoS as any endpoint that is publicly reachable from the internet is vulnerable to these attacks, With the recent Azure DDoS protection support for VNet integrated API Management instances in Azure, you are now able to mitigate volumetric and protocol DDoS attacks on a global scale with minimum configuration and overhead. After reading this blog you should be able to create an APIM instance with VNet integration, configure Azure DDoS protection standard and investigate DDoS mitigations that occurred in your environment.
Additional resources
Azure API Management with an Azure virtual network | Microsoft Docs
Azure DDoS Protection Standard documentation | Microsoft Docs
Connect to a virtual network using Azure API Management | Microsoft Docs
Published on:
Learn moreRelated posts
Coding at the Speed of Innovation: AI and more with Azure SQL Database
The Azure SQL Database team is all set to unveil new product announcements as Build 2024 approaches. Innovation is the prominent theme this ti...
Generate insights from audio and video data using Speech analytics in Azure AI Studio
In this video, we explore the power of speech analytics in Azure AI Studio to extract insights from audio and video data. This technology help...
Azure Custom Policy- PostgreSQL Product - Compliance Report not Available- New Feature Request
If you're attempting to create custom policies for Azure Cosmos DB for PostgreSQL at the subscription level and are running into issues where ...
Microsoft Causes Fuss Around Azure MFA Announcement
Microsoft's recent announcement regarding the requirement of Azure MFA for connections to services starting in July 2024 has caused quite a st...
PostgreSQL for your AI app's backend | Azure Database for PostgreSQL Flexible Server
If you want to use Postgres as a managed service on Azure and build generative AI apps, then the Azure Database for Postgres Flexible Server i...
Storage migration: Combine Azure Storage Mover and Azure Data Box
If you are looking to migrate your data from on-premises to Azure Storage, it can be challenging, but with Microsoft's solutions, you can make...
Loop DDoS Attacks: Understanding the Threat and Azure's Defense
This article provides a comprehensive overview of Loop DDoS attacks, a sophisticated and evolving cybersecurity threat that exploits applicati...
Azure Communication Services at Microsoft Build 2024
Join us for Microsoft Build 2024, either in-person in Seattle or virtually, to learn about the latest updates from Azure Communication Service...
Azure Developer CLI (azd) – May 2024 Release
The Azure Developer CLI (`azd`) has received a May 2024 update, version 1.9.0, making it simpler for developers to create, manage, and deploy ...
Join us at Build 2024: Get the latest on Azure Cosmos DB in Seattle or online!
Join Microsoft Build 2024 to get a sneak peek into the future of AI and data innovation. Taking place in Seattle and online from May 21 to 23,...