Part 1 - Managing Network Rules by using Azure Tags with Illumio for Microsoft Azure Firewall
Written in collaboration between @andrewmathu and @gusmodena
Introduction
In today's ever-evolving realm of the present IT infrastructure, where virtualization and cloud computing have become standard practices, the orchestration of firewall rules has evolved into a delicate balancing act between security and adaptability. Traditionally, firewall rules have relied heavily on the use of IP addresses to control access, which, while effective, often proves to be a complex and labor-intensive approach. The moment has arrived to adopt a more streamlined and effective approach that not only bolsters security but also streamlines the management procedure. This entails employing predefined tags that are assigned to virtual machines, aligning with the applications they run or the specific environment they are a part of, including Development (Dev), Production (Prod), and Quality Assurance (QA).
This is the 1st of a 2-part blog series where we will explore the complexities associated with managing firewall rules using IP addresses and explore the advantages of transitioning to a tag-based approach. We'll discover how this shift can not only make your infrastructure more secure but also significantly reduce the burden on your IT teams, allowing them to focus on what truly matters: safeguarding your digital assets in an ever-evolving threat landscape.
Illumio for Microsoft Azure Firewall
In collaboration with Illumio, the leader in Zero Trust Segmentation, Microsoft has built Illumio for Microsoft Azure Firewall - an integrated solution that extends the advantages of Zero Trust Segmentation into the Azure environment.
Illumio's integration with Microsoft Azure Firewall was released in General Availability in August 2023, empowering Azure users to implement Zero Trust Segmentation, extending their capabilities beyond traditional network and application filtering. This collaboration equips firewall operations teams with enhanced insights into rule management by providing comprehensive context about the resources under protection. This enriched context allows administrators to effortlessly identify the resources covered by each rule, ascertain ownership, and execute rule lifecycle management tasks with increased confidence and efficiency.
Leveraging the Azure platform, this solution protects your assets within Azure Virtual Networks and at the Azure perimeter. It empowers organizations to comprehensively analyze application traffic and dependencies, enforcing consistent protection throughout the environment. As a result, this approach minimizes vulnerabilities, mitigates breaches, and enhances operational efficiency.
Key benefits of using Illumio for Microsoft Azure Firewall include:
- Reduce security risks with a single view of your east-west and north-south traffic based on Azure Firewall flow data within your Azure subscriptions.
- Provides a full view of your application traffic with real-time visibility of interactions and dependencies across your environment.
- Easily deploy and configure Azure application-based policies within the Illumio platform.
- Deploy Azure Firewall policies confidently with policies that automatically scale along with your applications.
- Avoid application downtime by understanding the impact of Azure Firewall policies before they are enforced.
- It works with all 3 SKUs of Azure Firewall – Basic, Standard, and Premium - to meet the needs of any organization.
Connecting Illumio for Microsoft Azure Firewall to Azure subscription
First, we need to have access to Illumio for Microsoft Azure Firewall which is available by registering directly with Illumio or by deploying the solution from Azure’s Marketplace. In this blog, we are using a Tenant which has been registered directly with Illumio. To login into Illumio’s portal we are using the URL https://lumos1.illum.io/login.
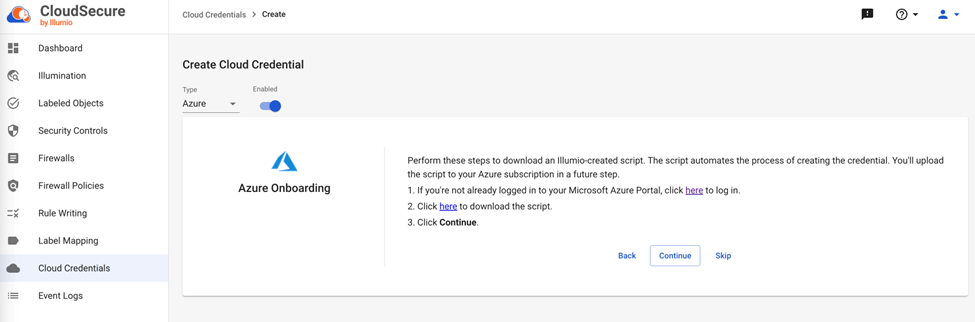
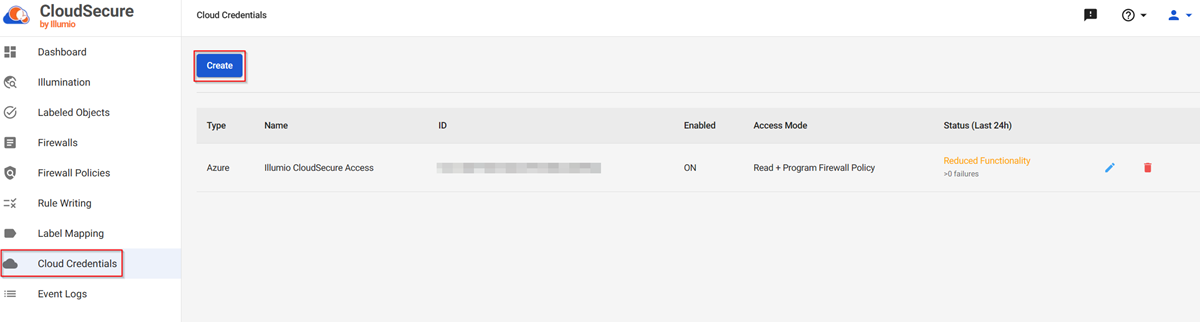
Next, we have to add a new cloud credential, which will connect Illumio for Microsoft Azure Firewall to our Azure Subscription.
The easiest way to add a new credential is by downloading and running an Illumio-created script, which automates the process of creating an App Registration on Azure, assigning the required roles for the newly created credential at subscription level. The roles assigned are Reader, Storage Blob Data Reader and a custom role called Illumio Firewall Administrator-“SubId”. The PowerShell script can be found here or can be downloaded from the Illumio portal. Click on “Cloud Credentials” then “Create” and follow the wizard.
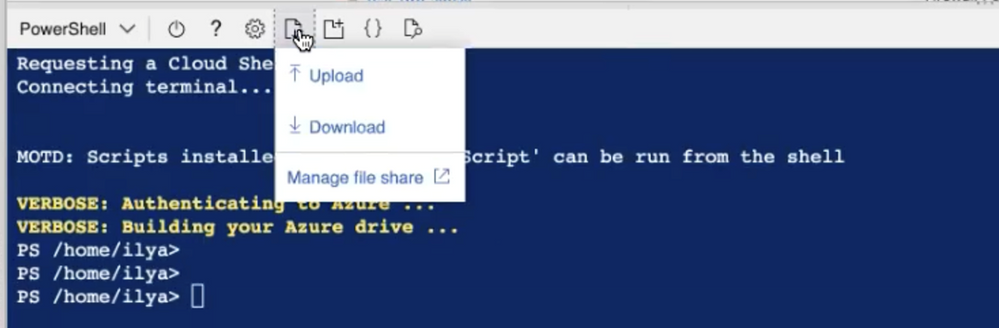
We are running the script via Azure Cloud Shell, so before running the command below, we need to upload the script to our account.
To run the script, we are using the following command line:
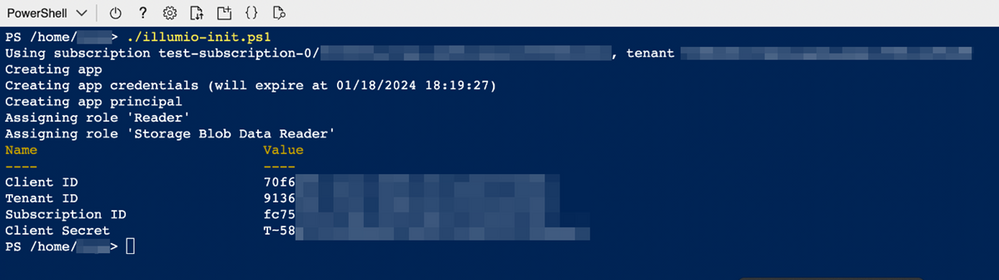
Once the script is completed, we will see the following output with the Client ID, Tenant ID, Subscription ID, and Client Secret, that will be used on the Illumio for Microsoft Azure Firewall portal.
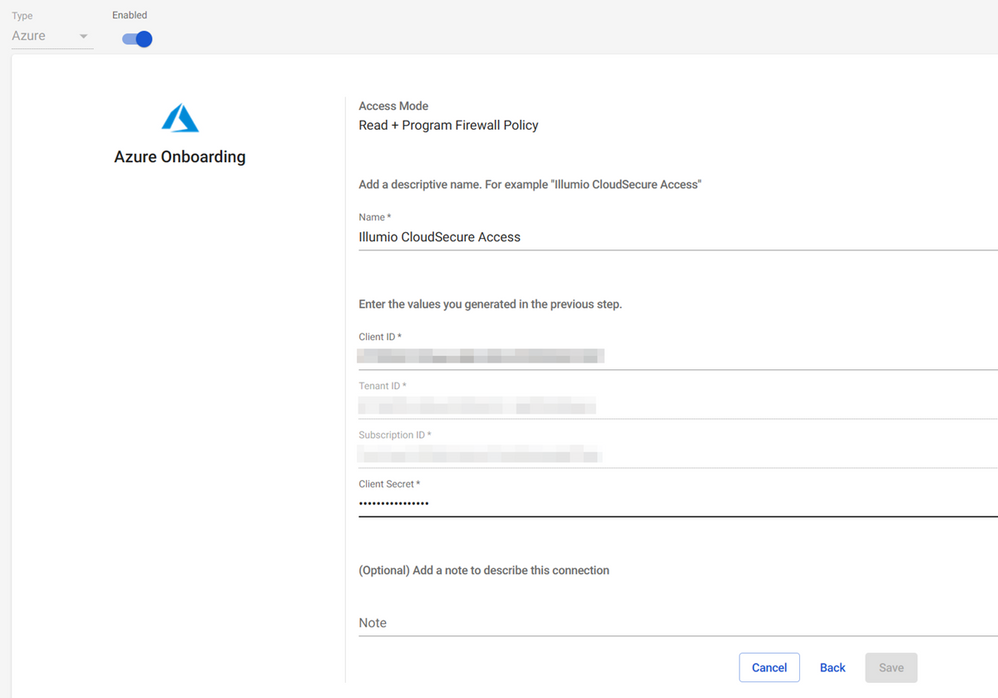
This output data will be added to the form below as part of adding a new credential.
Creating Label Mappings
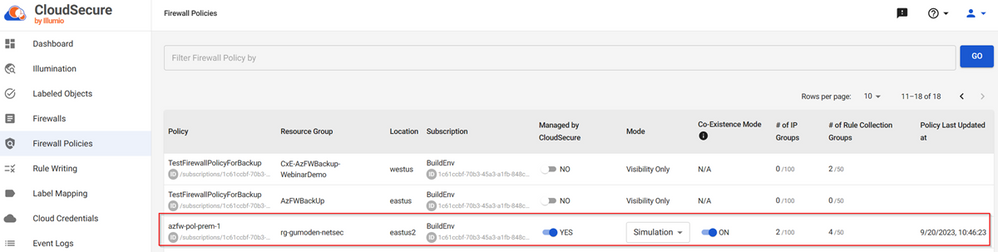
Once we have the credentials added, we can navigate through the Firewalls and Firewall Policies tab to find the resources identified by Illumio for Microsoft Azure Firewall and then start creating the label mappings and choosing the policies that we want to manage.
In the image below, we are seeing multiple Firewall Policies, but for this blog we are only going to enable the management by Illumio for Microsoft Azure Firewall for the policy “azfw-pol-prem-1”.
After enabling the management option, the mode will be automatically changed from “Visibility Only” to "Simulation". There are two modes for policy enforcement: Simulation and Enforcement. The Simulation mode allows security teams to test and validate the outcome and impact of their security policies before fully enforcing them. This mode helps protect applications and workloads by containing cyber-attacks and reducing risk.
In contrast, the "Enforcement" mode is used to enforce the security policies on managed workloads. The Illumio policy model follows an allowlist model, meaning all communication between workloads is denied unless explicitly allowed by Illumio security policy. Users create segmentation rules to allow traffic between their workloads.
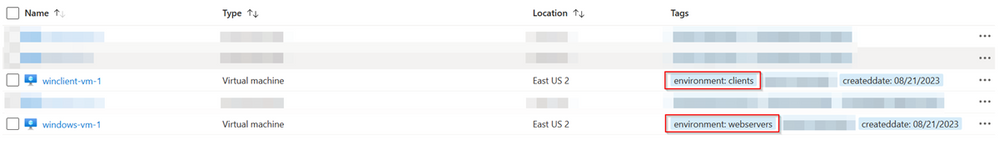
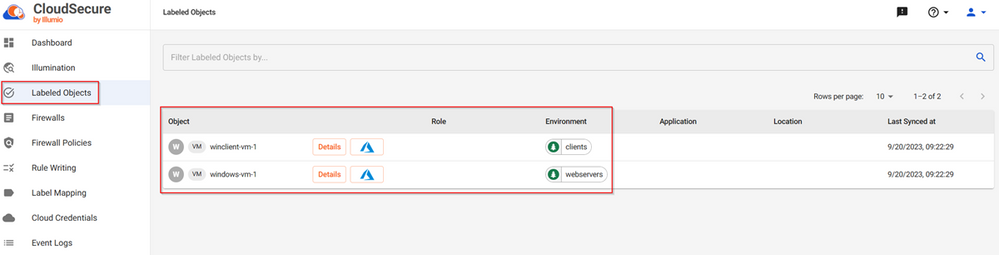
Now that we have enabled the management of the Firewall Policy, we will create label mappings. To create label mappings, we can use specific Cloud Metadata or Cloud Tags. If you use Cloud Tags, ensure that you have a definition for your Tags. In this blog we are using a tag called “environment” with the values “clients” and “webservers”.
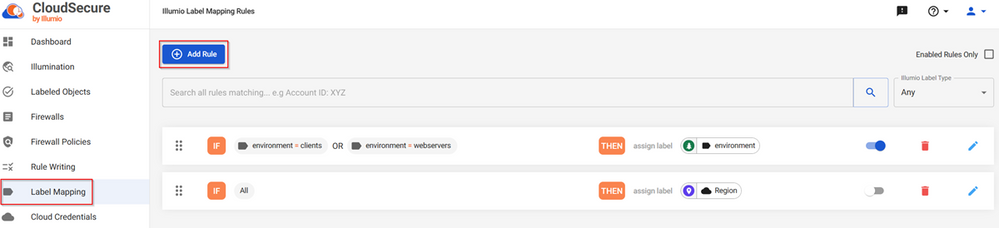
To create the mappings, click on “Label Mapping” located on the left side and then click on “Add Rule”.
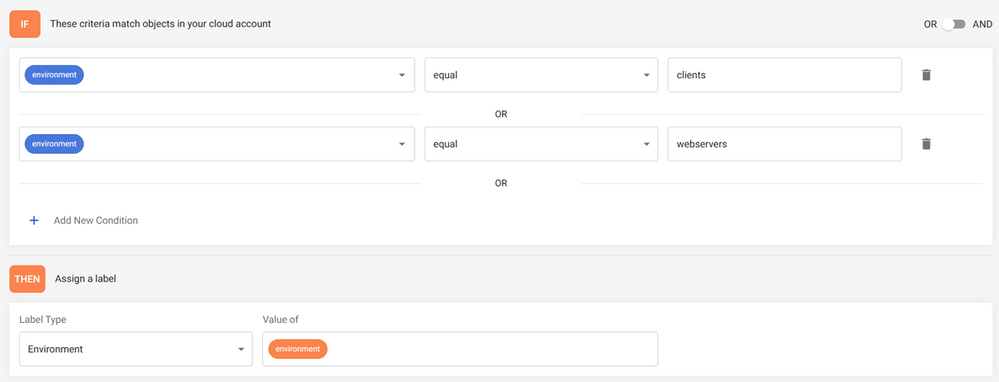
When creating a label mapping, we must define the “match criteria” and the “assign a label”. For the “match criteria” we can have multiple criteria using the operators “AND” or “OR”. This is how our label mapping looks like:
For Label Type we have 4 options:
- Application
- Environment
- Location
- Role
And for the “Value of “, we can use:
- Custom Value
- Cloud Metadata
- Cloud Tag
After creating the Label Mapping, we must wait for Illumio for Microsoft Azure Firewall to scan our Azure Subscription to find resources matching what we just defined. Once the scan is done, we can find the resources under “Labeled Objects”.
Creating Rule Writings
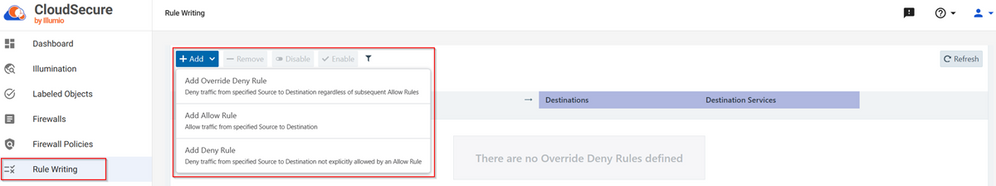
Now it’s time to create Rule Writings which will be provisioned and deployed into our Firewall Policy. Click on “Rule Writing” on the left side and then on “Add”. We can create 3 types of rules:
- Add Override Deny Rule
- Add Allow Rule
- Add Deny Rule
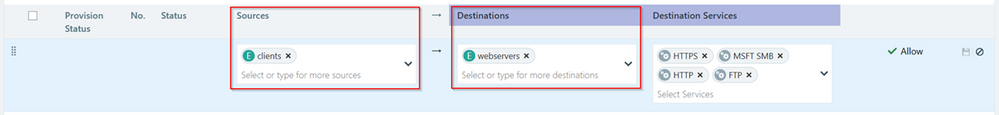
For this demonstration we are creating 1 “Allow” rule, allowing traffic from “Clients” to “Webservers” on ports 443 (HTTPS), 445 (SMB), 80 (HTTP), 21 and 22 (FTP). The Destination Services are predefined, but we can also create new services or even use Port/Port Ranges.
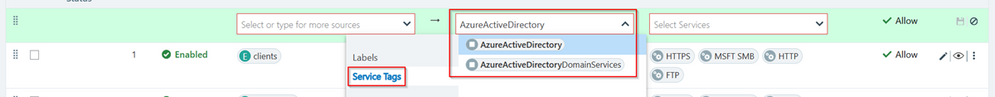
Note: On the destination we can also use Azure Service Tags.
Now that the rule is created, we must wait for the provisioning of the rule. This is an automatic process that runs periodically. In the case the provisioning takes too long it’s recommended to check the Event Logs to ensure that there is no unexpected error occurring, like for example, “AuthorizationFailed”.
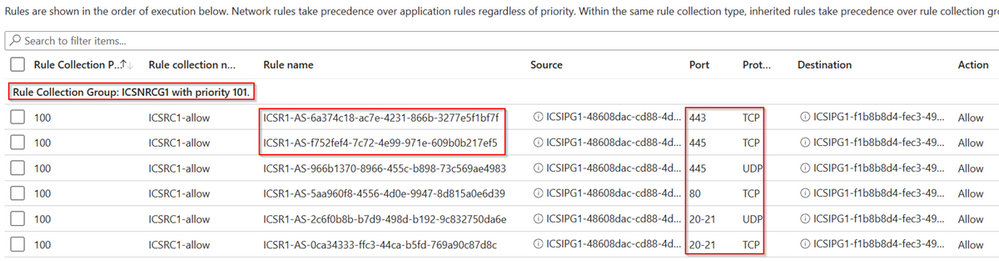
Moving to Azure Portal, we will check our Firewall Policy “azfw-pol-prem-1” to see the details of the new rule created, and this is what the Azure Policy looks like.
We can see that Illumio for Microsoft Azure Firewall has created a Resource Collection Group called “ICSNRCG1” with priority 101 and a Rule Collection called “ICSRC1-allow”. The Rule Collection contains 6 rules, one corresponding to each unique combination of Source IP, Destination IP, Port and Protocol, as it is defined in our Rule Writing previously. Within the source and destination fields, two distinct IP groups are used, “ICSIPG1-48608dac*” for the Cloud Tag value clients and “ICSIPG1-f1b8b8d4*” for the Cloud Tag value webservers.
Conclusion
The adoption of tag-based approaches and the integration of solutions like Illumio for Microsoft Azure Firewall signify a pivotal moment in the ongoing battle to secure our digital environments. As the threat landscape continues to evolve, it's crucial to stay ahead of the curve, and these innovations offer a compelling path forward. By simplifying rule management, enhancing visibility, and providing scalability, Illumio for Microsoft Azure Firewall empowers organizations to navigate the complex world of IT infrastructure security with confidence and agility. It's time to embrace the future of firewall rule management, and the future is bright with solutions like this at our disposal.
In Part 2 of this blog series, we are going to cover the benefits and the steps of using the Illumination feature to help you manage the Firewall rules based on all the traffic passing through and being recorded by Azure Firewall.
Learn More
- What is Azure Firewall: What is Azure Firewall? | Microsoft Learn
- Azure Firewall Policy Overview: Azure Firewall Manager policy overview | Microsoft Learn
- IP Groups in Azure Firewall: IP Groups in Azure Firewall | Microsoft Learn
- Azure Tags: Tag resources, resource groups, and subscriptions for logical organization - Azure Resource Manager | Microsoft Learn
- Illumio for Microsoft Azure Firewall: Illumio for Microsoft Azure Firewall | Illumio
- How Microsoft and Illumio are reinventing firewall security for the cloud era: How Microsoft and Illumio are reinventing firewall security for the cloud era | VentureBeat