How to attach an additional network interface to the Azure Stack HCI VM using SDN
Azure Stack HCI is a hyperconverged infrastructure (HCI) cluster solution consists of windows servers (Hyper-V), Storage Spaces Direct, and Azure-inspired SDN. All clustered servers share common configurations and resources by leveraging the Windows Server Failover Clustering feature. A Windows Failover Cluster consists of multiple windows servers running in a cluster to provide high availability i.e. If one server node goes down, then another node takes over. We can create multiple windows/Linux VMs on the failover cluster. In this blog, we have provided steps to attach a new network interface to an existing VM running on the failover cluster with static MAC and valid static IP address (from the given VNet/subnet pool). For this we will be performing following steps:
- Create a new network interface on NetworkController node with given tenant virtual network and subnet along with the static MAC/IP
- Create a new network adapter for VM
- Associat NetworkController network interface to VM’s new network adapter’s properties. So that VM will get connected to your tenant virtual network with the similar network properties. Here tenant virtual network is created with Hyper-V Network Virtualization on Network controller using SDN.
Prerequisites
- A role (VM) running on the Azure Stack HCI cluster.
- A virtual network, subnet with a valid CIDR range already created on Network Controller.
- Install NetworkController feature to perform network related operations from the cluster node. (More details can be found here: https://learn.microsoft.com/en-us/windows-server/networking/sdn/deploy/deploy-network-controller-using-windows-powershell)
Install-WindowsFeature -Name NetworkController -IncludeManagementTools
Disclaimer:
- Microsoft does not intend to officially support any source code/sample scripts provided as part of this blog. This blog is written only for a quick walk-through on how to run PowerShell scripts to create a new network interface for a VM and connect to Vnet/subnet through SDN.
- This blog assumes you have the basic understanding of Stack-HCI/Windows Server Failover Cluster.
Steps to attach a new Network interface to an existing VM:
(Note: Before running below commands, ensure that the values of assigned variables are updated based on your environment configurations)
- Run following commands on HCI Cluster node where your VM is running. In this, it will first shutdown running VM, then create a new network adapter for an existing VM, and finally assigns static MAC address to new adapter. VM’s new network adapter is created with static MAC address for the lifetime of the VM. This will be required as if MAC address changes during the VM lifetime, Network Controller won’t be able to configure the necessary policies for the attached network adapter.
$vm_name = "myvm" $adapter_name = "nic2" $mac = "9E-4C-0B-03-78-21" # static mac, should be unique $switch_name = "sdnswitch" # stopping vm stop-vm -Name $vm_name # creating new adapter for vm with nic2 name Add-VMNetworkAdapter -VMName $vm_name -SwitchName $switch_name -Name $adapter_name # Assign static mac to created new nic Set-VMNetworkAdapter -VMName $vm_name -Name $adapter_name -StaticMacAddress $mac Start-Sleep -Seconds 5 - Assign all network interface specific information in the variables, we will need it to perform all network controller specific operations in next step.
# add your network controller service url $uri = "https://<network-controller-service-uri>" # mention virtual network name where vm/new nic to be attached $vnet_name = "vnet01" # mention subnet name where vm/nic to be attached $subnet_name = "subnet01" # use free ip address to be assigned to new nic/vm $ip_address = "10.0.0.6" # plz change it as per your network dns $dns_server = @("192.168.1.254", "8.8.8.8") - Create a network interface object in Network Controller.
$vmnicproperties = New-Object Microsoft.Windows.NetworkController.NetworkInterfaceProperties # give same mac address below as created before.. $mac = -join($mac.split("-")).toupper() $vmnicproperties.PrivateMacAddress = $mac Write-host $mac $vmnicproperties.PrivateMacAllocationMethod = "Static" $vmnicproperties.IsPrimary = $true $vmnicproperties.DnsSettings = New-Object Microsoft.Windows.NetworkController.NetworkInterfaceDnsSettings $vmnicproperties.DnsSettings.DnsServers = $dns_server $ipconfiguration = New-Object Microsoft.Windows.NetworkController.NetworkInterfaceIpConfiguration $ipconfiguration.resourceid = $vm_name + "_IP2" $ipconfiguration.properties = New-Object Microsoft.Windows.NetworkController.NetworkInterfaceIpConfigurationProperties $ipconfiguration.properties.PrivateIPAddress = $ip_address $ipconfiguration.properties.PrivateIPAllocationMethod = "Static" $ipconfiguration.properties.Subnet = New-Object Microsoft.Windows.NetworkController.Subnet # do: programatically decide subnet full ref, or form path directly # $ipconfiguration.properties.subnet.ResourceRef = $vnet.Properties.Subnets[0].ResourceRef $ipconfiguration.properties.subnet.ResourceRef = "/virtualNetworks/" + $vnet_name + "/subnets/" + $subnet_name $vmnicproperties.IpConfigurations = @($ipconfiguration) $NIC_name = $vm_name + "_Eth2" New-NetworkControllerNetworkInterface -ResourceID $NIC_name -Properties $vmnicproperties -ConnectionUri $uri -Confirm:$false -force Write-host 'NIC config created..' Start-Sleep -Seconds 8 $nic = Get-NetworkControllerNetworkInterface -ConnectionUri $uri -ResourceId $NIC_name - Set the Interface ID on the VM's new network adapter port. So new network adapter of VM will get associated with Network controller's network-interface created in step 3
# following snippet is borrowed as is from : https://learn.microsoft.com/en-us/windows-server/networking/sdn/manage/create-a-tenant-vm#create-a-vm-and-connect-to-a-virtual-network-by-using-the-windows-powershell-network-controller-cmdlets #Do not change the hardcoded IDs in this section, because they are fixed values and must not change. $FeatureId = "9940cd46-8b06-43bb-b9d5-93d50381fd56" $vmNics = Get-VMNetworkAdapter -VMName $vm_name -Name $adapter_name $CurrentFeature = Get-VMSwitchExtensionPortFeature -FeatureId $FeatureId -VMNetworkAdapter $vmNics if ($CurrentFeature -eq $null) { $Feature = Get-VMSystemSwitchExtensionPortFeature -FeatureId $FeatureId $Feature.SettingData.ProfileId = "{$( $nic.InstanceId )}" $Feature.SettingData.NetCfgInstanceId = "{56785678-a0e5-4a26-bc9b-c0cba27311a3}" $Feature.SettingData.CdnLabelString = "TestCdn" $Feature.SettingData.CdnLabelId = 1111 $Feature.SettingData.ProfileName = "Testprofile" $Feature.SettingData.VendorId = "{1FA41B39-B444-4E43-B35A-E1F7985FD548}" $Feature.SettingData.VendorName = "NetworkController" $Feature.SettingData.ProfileData = 1 Add-VMSwitchExtensionPortFeature -VMSwitchExtensionFeature $Feature -VMNetworkAdapter $vmNics } else { $CurrentFeature.SettingData.ProfileId = "{$( $nic.InstanceId )}" $CurrentFeature.SettingData.ProfileData = 1 Set-VMSwitchExtensionPortFeature -VMSwitchExtensionFeature $CurrentFeature -VMNetworkAdapter $vmNics } Write-host 'finally applyed setting..' Start-Sleep -Seconds 5 Get-VM -Name $vm_name | Start-VM
Sample:
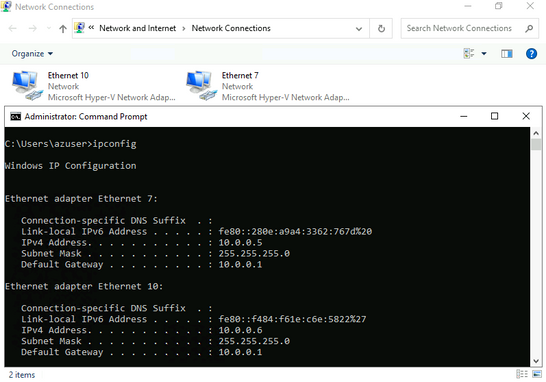
Below is an example of a VM, showing two adapters- "Ethernet 10" is attached as new using the steps as mentioned above and "Ethernet 7" was already present with VM. Both are showing assigned IPs from NetworkController nic level.
Same can be seen in Hyper-v manager:
Summary
In this article, we saw that how we can attach a new network interface connected to virtual network/subnet along with the fixed MAC/IP address, so even if VM is migrating to another node in the cluster, VM will preserve it’s same NIC since we are providing static MAC/IP address to it.
Reference Links:
Published on:
Learn moreRelated posts
Powering Real-Time Gaming Experiences with Azure Cosmos DB for NoSQL
Scenario: When Every Millisecond Counts in Gaming Imagine millions of players logging in at the exact moment a new game season launches. Leade...
Access Azure Virtual Desktop and Windows 365 Cloud PC from non-managed devices
Check out this article via web browser: Access Azure Virtual Desktop and Windows 365 Cloud PC from non-managed devices Many organizations use ...
Power Pages + Azure AD B2C: “The Provided Application Is Not Valid” Error
If you are new to configuring Azure AD B2C as Identity Provider in Power Pages, refer Power Pages : Set up Azure AD B2C After completing the s...
Semantic Reranking with Azure SQL, SQL Server 2025 and Cohere Rerank models
Supporting re‑ranking has been one of the most common requests lately. While not always essential, it can be a valuable addition to a solution...
How Azure Cosmos DB Powers ARM’s Federated Future: Scaling for the Next Billion Requests
The Cloud at Hyperscale: ARM’s Mission and Growth Azure Resource Manager (ARM) is the backbone of Azure’s resource provisioning and management...
Automating Business PDFs Using Azure Document Intelligence and Power Automate
In today’s data-driven enterprises, critical business information often arrives in the form of PDFs—bank statements, invoices, policy document...
Azure Developer CLI (azd) Dec 2025 – Extensions Enhancements, Foundry Rebranding, and Azure Pipelines Improvements
This post announces the December release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) Dec 2025 – Extensions En...