Intrusion Detection and Prevention System (IDPS) Based on Signatures

Written in collaboration between @andrewmathu and @gusmodena
Introduction
An Intrusion Detection and Prevention System (IDPS) is a vital component of modern cybersecurity strategy, designed to safeguard networks by actively monitoring and responding to potential security threats. Among the types of IDPS currently available such as signature-based and anomaly-based, signature based IDPS stands out as a reliable and efficient method for identifying known security risks. This blog delves into signature-based IDPS, with a specific focus on the Azure Firewall Premium IDPS.
Why is IDPS based on signatures important?
Signature-based IDPS leverages a signature database of well-known anomalies, attack patterns and exploits making it best suited for identifying known cyber threats. Several benefits arise from this type of IDPS:
- Minimal False Positives: Through precise pattern matching, the likelihood of false positive alerts is minimized. This accuracy helps security teams focus their efforts on legitimate threats.
- Rapid Detection: Signature-based IDPS excels in swiftly recognizing established attack patterns, ensuring that potential threats are identified in real-time.
- Comprehensive Analysis: The system conducts in-depth analyses of various attack vectors, pinpointing specific patterns of malicious behavior.
The above attributes and benefits are important as they allow security administrators to tune, organize and implement effective security controls.
How does it work?
At its core, signature based IDPS operates by comparing network traffic against an extensive database of known attack signatures:
- Packet Inspection: Incoming and outgoing packets of data are subjected to thorough inspection, analyzed to reveal their underlying characteristics.
- Signature Matching: The analyzed packets are then matched against a repository of recognized attack patterns, looking for a "signature" that matches any of the known threats.
- Alert Generation: Should the system discover a match, it promptly generates an alert, notifying administrators about the potential threat.
- Blocking: Once the system finds a match, it promptly blocks the traffic, protecting the network against potential threat.
Examples:
An example of a signature based IDPS is the IDPS that runs in Azure Firewall Premium. Azure Firewall Premium provides advanced threat protection that meets the needs of sensitive and regulated environments, such as the payment and healthcare industries. Organizations can use the Azure Firewall Premium SKU features such as IDPS and TLS inspection to prevent exploits, and malware from spreading across networks in Ingress, Egress, and internal directions.
The IDPS capabilities of Azure Firewall encompass more than fifty categories with over 67,000 signature rules. The range of detection categories comprises malware command and control, phishing, trojans, botnets, informational events, exploits, vulnerabilities, SCADA network protocols, exploit kit activity, and numerous others. The Azure Firewall IDPS signatures are continuously updated in real-time to ensure protection against the latest zero-day threats. The Azure Firewall IDPS signatures can be applied based on the traffic direction – inbound, spoke-to-spoke (East-West) and outbound traffic.
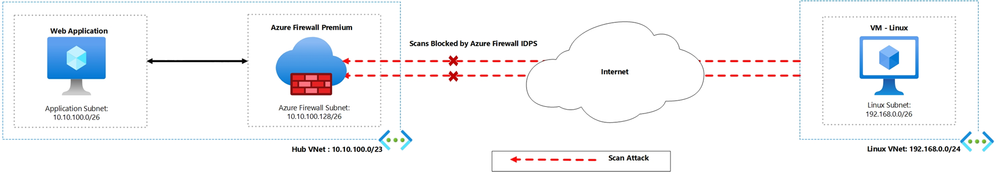
Azure Firewall Premium IDPS: Mitigating Scanning Attacks
In this section, we look at how the Azure Firewall Premium IDPS detects and blocks attacks, specifically scanner attacks. Consider a scenario where an attacker aims to exploit vulnerabilities by conducting scanning attacks using a tool like Nmap. Nmap, short for Network Mapper, is an open-source Linux command-line tool. It facilitates broad network exploration by enabling users to scan IP addresses and ports, revealing active devices, accessible services, and potential vulnerabilities.
In our setup, we have deployed the following to illustrate the scenario:
- Azure Firewall Premium.
- A web application that runs on a Windows Virtual Machine.
- A Linux virtual machine to simulate the scan attack using the Nmap utility tool (a Windows-based GUI version of Nmap is also available).
Azure Firewall Setup
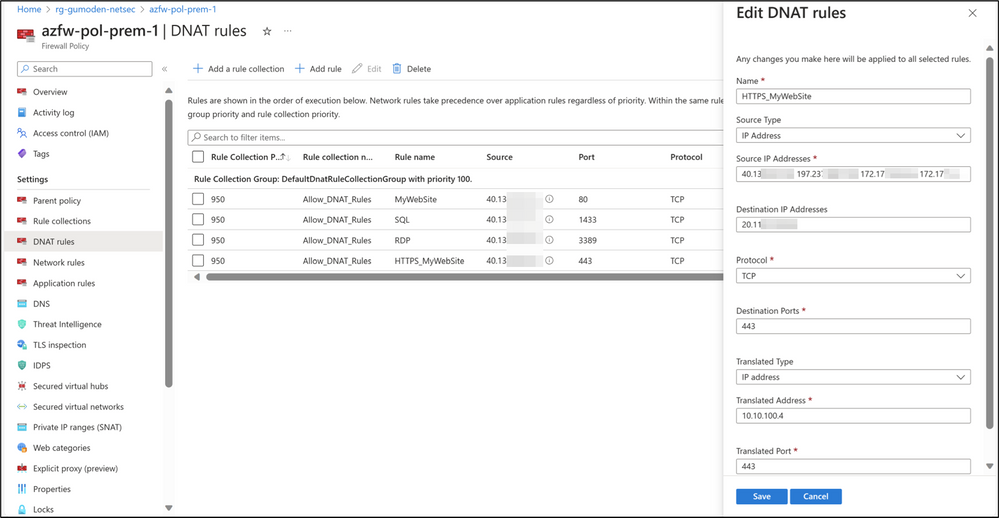
To access the web application, The Azure Firewall Premium has been deployed with DNAT rules to NAT traffic on the firewall’s public IP address and translate to the backend web application.
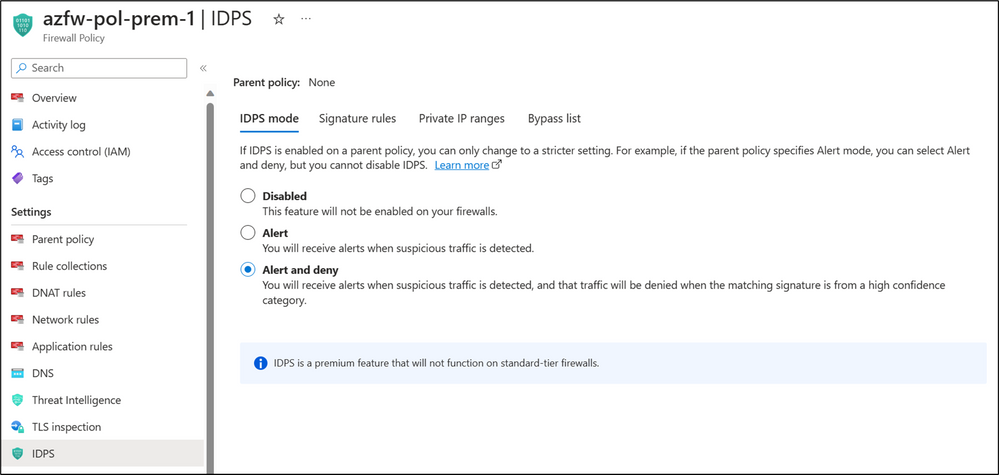
The Azure Firewall IDPS is activated by navigating to the Firewall Policy, then Settings and clicking on IDPS. Three modes are available as seen in the diagram below. In our setup, we are using the IDPS in Alert and deny mode. In this mode the IDPS engine is scanning all the requests in line. We recommend having IDPS in Alert and deny mode to scan and block any suspicious traffic.
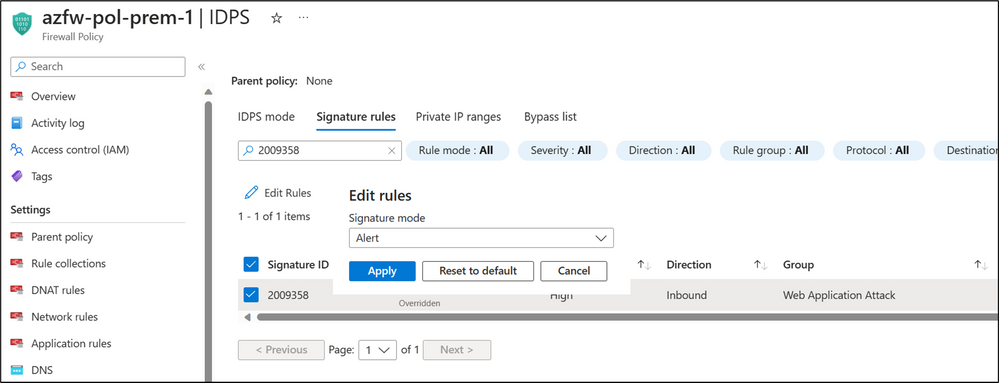
By default, there are signatures set to Alert mode, even though the global configuration is set to Alert and deny. If you would like to change the mode of individual signatures you can use the signature overrides, by selecting and editing the signatures.
In this blog post we are using signature override for the signatures below:
- 2009358
- 2010935
- 2023753
- 2036252
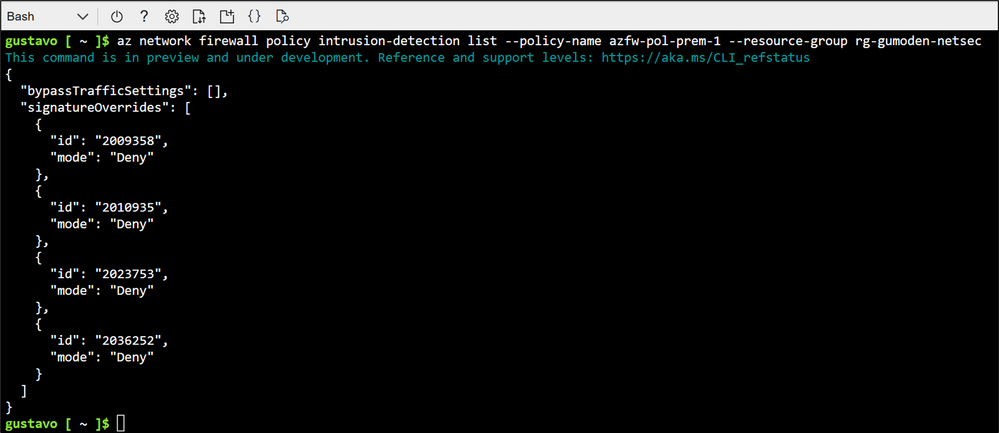
If you are using multiple signature overrides, a better way to list the signatures and see what modes are assigned to each one is by running the following Az CLI command:
Once the command runs successfully, this is what the result will look like:
Web Application Setup:
The web application runs in a Windows virtual machine and listens to traffic on ports 80 (HTTP) and 443 (HTTPS). There are other services running on the same virtual machine - 3389 (RDP) and 1433 (SQL Server). These ports are published over the internet and are accessed via the Azure Firewall public IP address configured in the DNAT rules illustrated previously.
Scanning Detection:
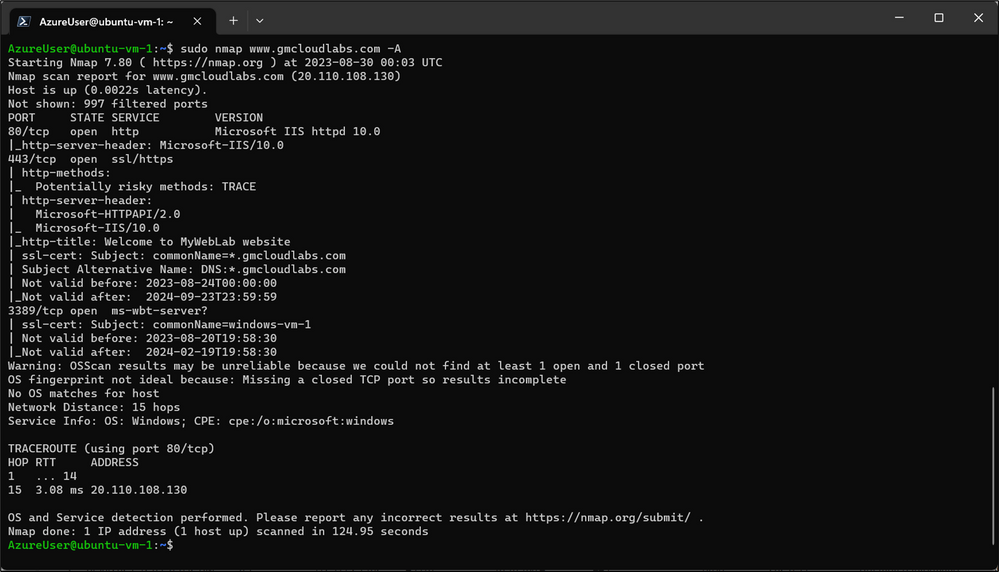
With the above setup, the next step is to simulate the scan attack/detection. From the Linux machine, we run the command below to begin the scan:
The command performs a comprehensive network scan on the specified IP address using the Nmap tool. The "-A" flag enables a series of aggressive scan options that include:
- Operating System Detection.
- Version Detection.
- Script Scanning (script against the target to gather additional information and potentially identify vulnerabilities or misconfigurations).
- Traceroute.
The command is run targeting our web application public IP address, with the output displayed as shown below:
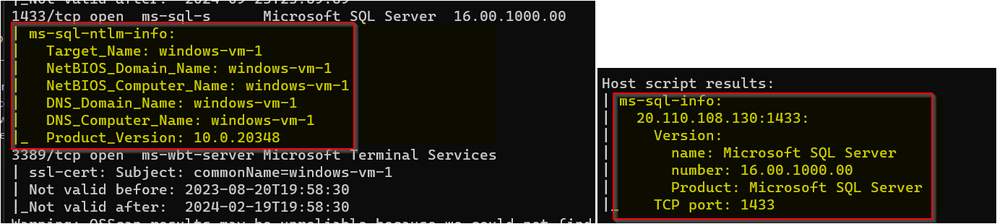
Since there are DNAT rules allowing traffic from our Linux virtual machine public IP to different ports, as demonstrated in the DNAT rules previously, the NMAP result will list the ports and show some information from the Windows virtual machine. The IDPS in this case will alert and deny any request that matches the signatures. This will be seen on the firewall logs.
If we run the same command with IDPS mode set to disabled or alert, we will have some additional details on the results since the scripts are not being blocked by IDPS.
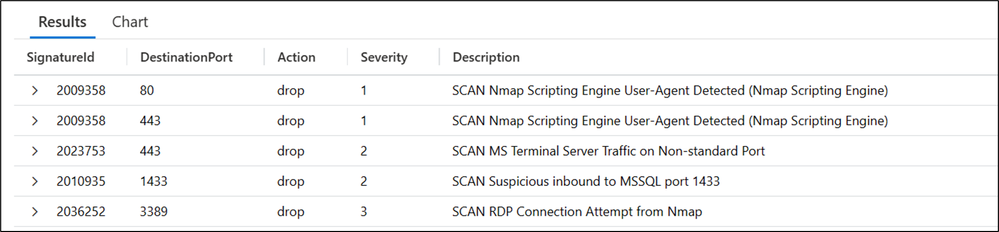
Now let's check the logs and see what requests have been dropped. For checking the logs, we are using the following KQL:
On the logs we can find what signature IDs have been triggered, as well as the Destination Port, Action, Severity, and Description. Each signature has an associated severity level and an assigned priority that indicates the probability that the signature is an actual attack.
- Low (priority 3): An abnormal event is one that doesn't normally occur on a network or Informational events are logged. The probability of attack is low.
- Medium (priority 2): The signature indicates an attack of a suspicious nature. The administrator should investigate further.
- High (priority 1): The attack signatures indicate that an attack of a severe nature is being launched. There's little probability that the packets have a legitimate purpose.
Conclusion
An Intrusion Detection and Prevention System (IDPS) based on signatures is an important security solution that helps to identify known cyber threats by comparing network data to a predetermined list of known indicators of compromise. It is quick, effective, and has an insignificant risk of raising false alarms.
The Azure Firewall Premium IDPS plays a critical role in stopping significant threats by leveraging its base of signature rules, making it an indispensable tool in safeguarding your Azure environment.
Resources
Azure Firewall Premium – Azure Firewall Premium features | Microsoft Learn
Azure Firewall IDPS Signatures – Azure Firewall IDPS signature rule categories | Microsoft Learn
Published on:
Learn more