How to Create Azure AD Security Group using Microsoft Graph APIs (Postman & Python Code Sample)
Azure Active Directory (Azure AD) groups are used to manage users that all need the same access and permissions to resources, such as potentially restricted apps and services. Instead of adding special permissions to individual users, you create a group that applies the special permissions to every member of that group.
You can refer to below steps for the scenarios in which you have Azure AD service principle with required permissions to create Security Groups in Azure Active Directory and need to call Microsoft Graph REST APIs from your dev or local environment via Postman or through python code.
First step is to register a client application with Azure AD and assign required permissions to create AD groups
1. Sign in the Azure portal, search for and select Azure Active Directory.
2. In the left panel, under Manage, select App registrations > All Applications > Select your registered application (Service Principal Account) > API Permissions
3. Least Privileged Permissions required to create AAD groups are:
- Group.Read.All
- Group.ReadWrite.All
- Group.Create
Python Source Code:
Refer attached python source code (SecurityGroupCreatePythonSample.zip)
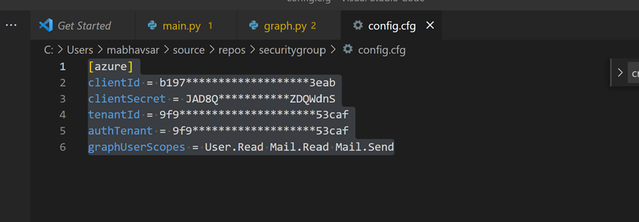
- Update ClientId, ClientSecret and Tenant details in config.cfg file
- Update Request body to create new group in graph.py file
- Install Required dependencies to build the project.
python3 -m pip install azure-identity python3 -m pip install msgraph-core -
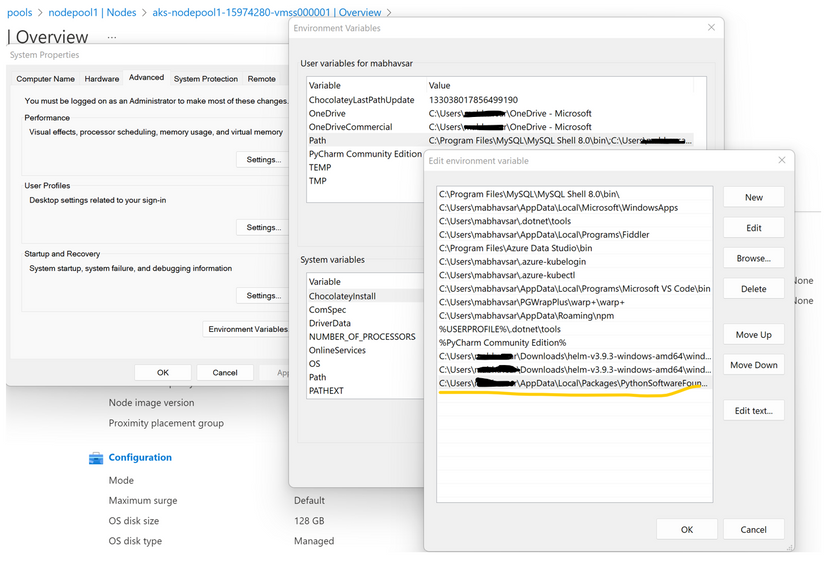
Ensure that installed package script path are added into System Environment Variables.
- Run Main.py file. Choice 6 and 7 are the methods to list or create group using SPN (App Only Authentication)
Reference Link:
Build Python apps with Microsoft Graph - Microsoft Graph | Microsoft Docs
Step 7: Build Python apps with Microsoft Graph - Microsoft Graph | Microsoft Docs
Step 8: Build Python apps with Microsoft Graph - Microsoft Graph | Microsoft Docs
Postman:
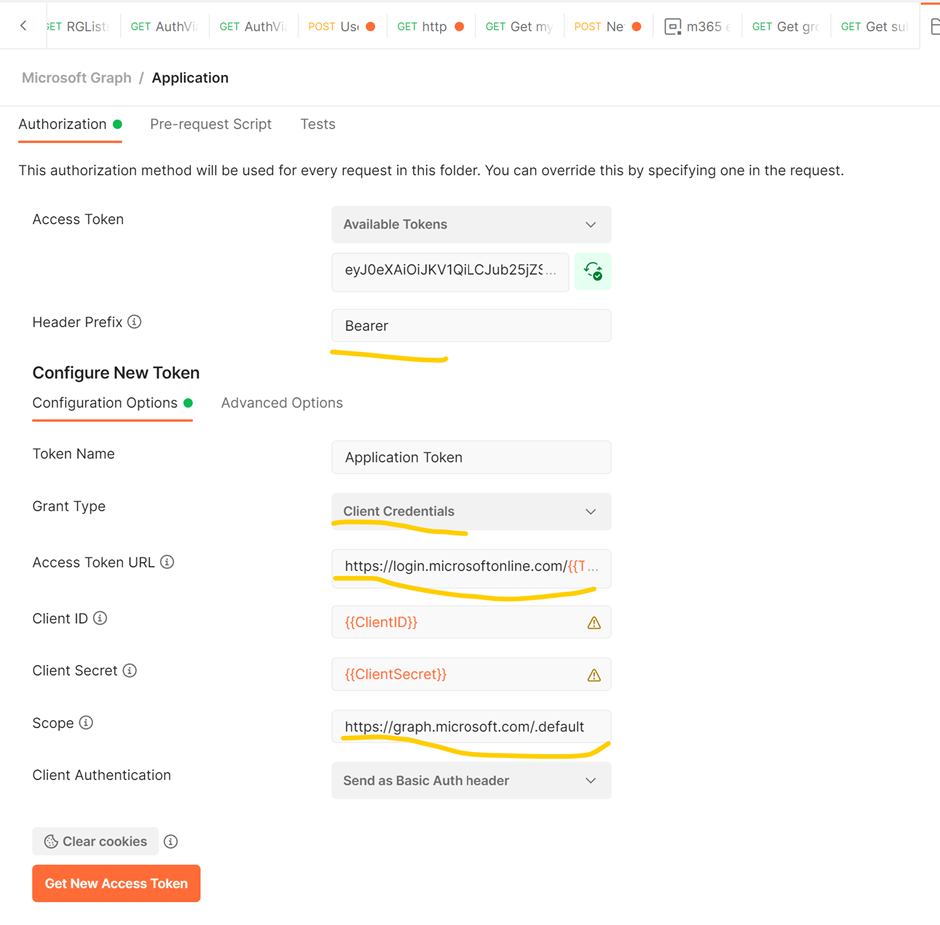
Create Authorization Header in Postman Requests Collection Folder Level:
Access Token Url: https://login.microsoftonline.com/{{TenantID}}/oauth2/v2.0/token
Scope: https://graph.microsoft.com/.default
Grant_Type = Client Credentials
Rest API to create Group:
Url: https://graph.microsoft.com/v1.0/groups
Request Type: Post
Authorization Type: Bearer Token. Copy the access token created from above step
Request Body:
Reference Link:
Use Postman with the Microsoft Graph API - Microsoft Graph | Microsoft Docs
Note:
- If SPN is granted with Delegated permission, you need to follow User Authorization Code to generate access token
- If SPN is granted with Application permission, you can follow Grant type= Client Credentials
Published on:
Learn moreRelated posts
Build business understanding with Dataverse in Microsoft 365 Copilot
Microsoft 365 Copilot is now embedded as an in-app sidecar within Power Apps, Dynamics 365 Sales, and Dynamics 365 Customer Service—removing t...
Microsoft Teams: Improved copy and paste support for @mentions and shared contacts
Microsoft Teams preserves @mentions and shared contacts when you copy and paste messages in chats and channels. Instead of defaulting to plain...
Microsoft Teams: Account Switching for Native Mac Controls via Dock and Menu Bar
Users will now find controls for switching between the accounts and tenants that they are signed into making it easier to navigate on Mac. Pro...
Upcoming change: disabling Teams meeting recording expiration notification emails
Starting June 1, 2026, Microsoft will disable Teams meeting recording expiration notification emails for all Microsoft 365 tenants to reduce n...
New URBAC permission to preview email content in Microsoft Defender for Office 365
Microsoft Defender for Office 365 introduces a new URBAC permission allowing admins to preview and download email content linked to “Ema...
Unified RBAC enabled by default for new Microsoft Defender for Office 365 tenants
Starting May 30, 2026, new Microsoft Defender for Office 365 Plan 2 tenants will have Unified RBAC enabled by default, offering centralized, g...
How to get better with Graph API – Part one
Check out this article via web browser: How to get better with Graph API – Part one As you might know, Graph API is an important part of...
Microsoft Teams: Ad-hoc room reservation from Teams Rooms on Windows console
Microsoft Teams Rooms on Windows will support ad-hoc room reservations directly from the console, enabling quick bookings without personal dev...