Microsoft Graph Activity Log is Now Available in Public Preview

Hi friends,
Today we’re excited to announce the public preview of Microsoft Graph Activity Logs. Have you wondered what applications are doing with the access you've granted them? Have you discovered a compromised user and hoped to find out what operations they have performed? If so, you can now gain full visibility into all HTTP requests accessing your tenant’s resources through the Microsoft Graph API.
*Note: We're enabling the feature starting today. Public preview will be available in all public cloud regions within two weeks.
You’re currently able to collect SignIn logs to analyze authentication activity and Audit logs to see changes to important resources. With Microsoft Graph Activity Logs, you can now investigate the complete picture of activity in your tenant – from token request in SignIn logs, to API request activity (reads, writes, and deletes) in Microsoft Graph Activity Logs, to ultimate resource changes in Audit logs.
The Microsoft Graph Activity Logs include information about the request and client application. Some common use cases include:
- Identifying the activities that a compromised user account conducted in your tenant.
- Building detections and behavioral analysis to identify suspicious or anomalous use of Microsoft Graph APIs – such as an application enumerating all users; or making probing requests with many 403 errors.
- Investigating unexpected or unnecessarily privileged assignments of application permissions.
- Identifying problematic or unexpected behaviors for client applications – such as extreme call volumes that exhaust rate-limits for the tenant.
To illustrate working with these logs, we can look at some basic LogAnalytics queries:
Summarize applications and principals that have made requests to change or delete groups in the past day:
|
MicrosoftGraphActivityLogs | where TimeGenerated > ago(1d) | where RequestUri contains '/group' | where RequestMethod != "GET" | summarize UriCount=dcount(RequestUri) by AppId, UserId, ServicePrincipalId, ResponseStatusCode |
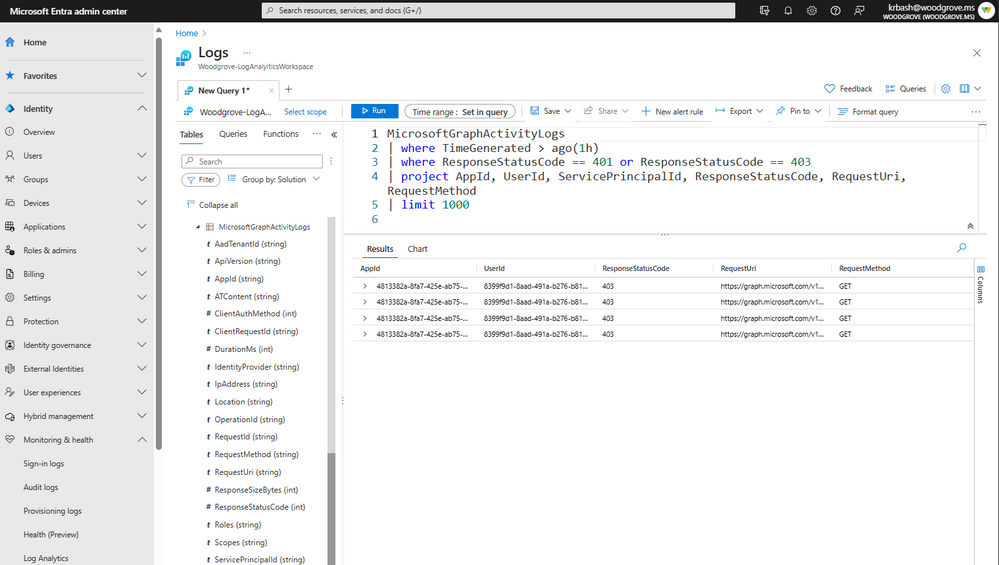
To see recent requests that failed due to authorization:
|
MicrosoftGraphActivityLogs | where TimeGenerated > ago(1h) | where ResponseStatusCode == 401 or ResponseStatusCode == 403 | project AppId, UserId, ServicePrincipalId, ResponseStatusCode, RequestUri, RequestMethod | limit 1000 |
Get top 20 app instances by request count:
|
MicrosoftGraphActivityLogs | where TimeGenerated > ago(1d) | summarize RequestCount=count() by AppId, IpAddress, UserAgent | sort by RequestCount | limit 20 |
Microsoft Graph Activity Logs are available through the Azure Monitor Logs integration of Entra. Administrators can configure the collection and storage destinations of Microsoft Graph Activity Logs through Diagnostic Setting in the Entra Portal. These settings allow you to configure the collection of the logs to a storage destination of your choice. The logs can be stored and queried in an Azure Log Analytics Workspace, archived in Azure Storage Accounts, or exported to other SIEM tools through Azure Event Hubs.
For logs collected to a Log Analytics Workspace, you can use the full set of Azure Monitor Logs features, such as a portal query experience, alerting, saved queries, and workbooks.
Find out about how to enable Microsoft Graph Activity Logs, sample queries, estimated costs, and more in our documentation.
Learn more about Microsoft Entra:
- See recent Microsoft Entra blogs
- Dive into Microsoft Entra technical documentation
- Join the conversation on the Microsoft Entra discussion space and Twitter
- Learn more about Microsoft Security
Published on:
Learn moreRelated posts
Microsoft 365 & Power Platform Call (Microsoft Speakers) – Community Takeover – August 19th, 2025 – Screenshot Summary
Call Highlights SharePoint Quicklinks: Primary PnP Website: https://aka.ms/m365pnp Documentation & Guidance SharePoint Dev Videos Issues...
Interact with SharePoint content in Teams channels using agents
SharePoint agents in Microsoft Teams Channels enable users to access and summarize SharePoint content via @mentions without leaving Teams. Rol...
Viva Glint: Export Team Summary report in Viva Glint to editable PowerPoint slides
Viva Glint’s Team Summary report will soon export directly to editable PowerPoint slides, enabling faster, customizable presentations wi...
Additional document processing rule actions for Microsoft SharePoint libraries
SharePoint libraries will gain new document processing rule actions—copy file to, move file to, and set content type—available to users with e...
Streamlined file preview and Copilot Chat experience in Microsoft 365 Copilot app for iOS
Microsoft 365 Copilot iOS app will offer file previews and Copilot Chat for Word, Excel, and PowerPoint files starting September 15, 2025, on ...
Microsoft Copilot (Microsoft 365): [Copilot Extensibility] View Index browser, schema and errors for Custom Connectors on MAC
View index browser, schema, and the errors for custom connectors from the M365 Admin center for better troubleshooting. Product Release phase ...
Streamlined file preview experience in Microsoft 365 Copilot app for iOS
Microsoft 365 Copilot iOS app will offer file previews and Copilot Chat for Word, Excel, and PowerPoint files starting September 15, 2025, on ...
Microsoft 365 admin center: New usage intensity and host apps metrics available in Copilot Chat usage report
New Microsoft 365 admin center metrics track Copilot Chat usage intensity and app-specific engagement for users without Copilot licenses acros...
Live events using Microsoft Teams town hall in Viva Engage
Microsoft is rolling out an enhanced Teams town hall experience in Viva Engage for live events starting September 2025. Community admins can c...
Manager insights now in Viva Insights web app, with new team view for Copilot Dashboard
Manager insights in the Viva Insights web app will centralize manager tools, including a team-scoped Copilot Dashboard, additional reports, de...