| Blogs on Microsoft Security |
 |
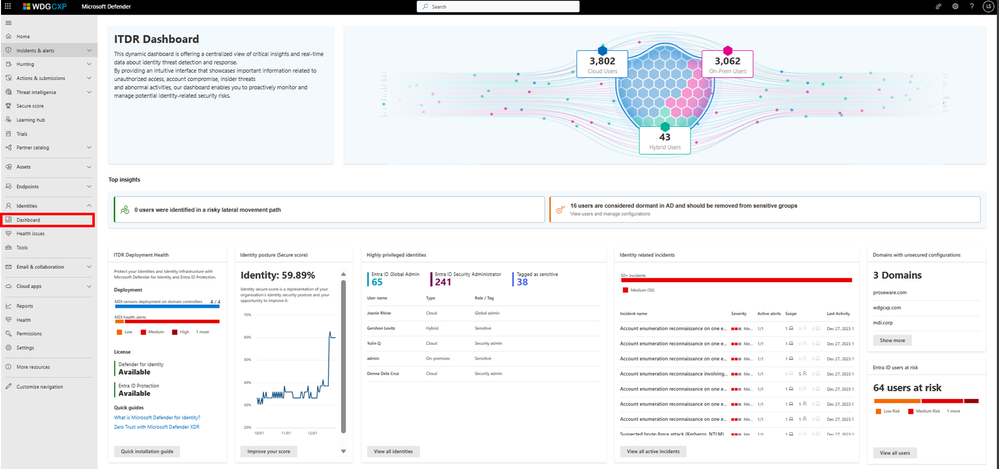
Midnight Blizzard: Guidance for responders on nation-state attack. The Microsoft security team detected a nation-state attack on our corporate systems on January 12, 2024, and immediately activated our response process to investigate, disrupt malicious activity, mitigate the attack, and deny the threat actor further access. The Microsoft Threat Intelligence investigation identified the threat actor as Midnight Blizzard, the Russian state-sponsored actor also known as NOBELIUM. |
 |
Join us at InfoSec Jupyterthon 2024. We’re inviting the community of analysts and engineers to join us at InfoSec Jupyterthon 2024. This online event, to be held on February 15-16, 2024, serves as an opportunity for infosec analysts and engineers to meet and engage with security practitioners using notebooks in their daily work. It is organized by our friends at Open Threat Research, together with folks from the Microsoft Threat Intelligence community. |
 |
New TTPs observed in Mint Sandstorm campaign targeting high-profile individuals at universities and research orgs. Since November 2023, Microsoft has observed a distinct subset of Mint Sandstorm (PHOSPHORUS) targeting high-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the United Kingdom, and the United States. In this campaign, Mint Sandstorm used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files. In a handful of cases, Microsoft observed new post-intrusion tradecraft including the use of a new, custom backdoor called MediaPl. |
|
| Microsoft Threat Analytics Reports (access to the Defender XDR portal needed) |
| |
Activity profile: New TTPs observed in ongoing Mint Sandstorm campaign. In this campaign, Mint Sandstorm used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files. In a handful of cases, Microsoft observed new post-intrusion tradecraft including the use of a new, custom backdoor called MediaPl.
|
| |
Actor profile: Ruby Sleet. The actor that Microsoft tracks as Ruby Sleet (CERIUM) is a nation-state threat actor based out of North Korea. Ruby Sleet is known to primarily target defense-related organizations as well as IT service providers to access downstream targets. |
| |
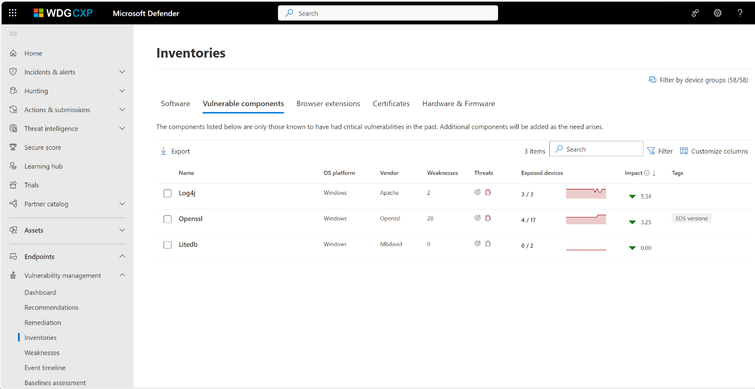
Technique profile: Malicious scheduled task creation. Threat actors take advantage of living-off-the-land binaries (LOLBins) to manipulate scheduled tasks by using schtasks.exe. While scheduled tasks are most often used to maintain persistence on a compromised device, threat actors also leverage scheduled tasks to elevate privileges and permissions by running a malicious process under a different account.
|
| |
Activity profile: Smoke Sandstorm new lures used to deliver SnailResin and SlugResin. Since January 2024, Microsoft has observed Smoke Sandstorm, an Iranian nation state actor, posing as members of the Bring Them Home Now campaign, a movement advocating for the return of individuals taken hostage by Hamas. In this campaign, Smoke Sandstorm attempted to deliver a SnailResin loader followed by SlugResin, a new variant of the BassBreaker backdoor, to Israelis working for organizations in the global payment systems, oil and energy, IT, and semiconductors sectors.
|
| |
Actor profile: Opal Sleet. The threat actor Microsoft tracks as Opal Sleet (OSMIUM) is based out of North Korea and targets organizations and individuals with an interest in or connection to North Korea since 2014. Opal Sleet is known for using spear phishing attacks against specific individuals affiliated with diplomacy and international relations, non-government organizations, universities, and government partnerships by sending weaponized documents related to Korean Peninsula activities or geopolitical issues.
|
| |
Actor profile: Jade Sleet. The threat actor Microsoft tracks as Jade Sleet (formerly Storm-0954) is a threat actor operating on behalf of North Korea that primarily targets organizations and individuals managing cryptocurrency for financial gain. Jade Sleet has also been observed compromising Russian targets for cyberespionage or corporate theft, and conducting social engineering campaigns targeting the personal accounts of employees at blockchain, cryptocurrency, cybersecurity, or online gambling companies. |
| |
Technique profile: Kerberos attacks. Kerberos authentication is a widely used methodology designed to secure access to network resources. However, threat actors often seek to manipulate such protection measures to conduct attacks. |
|
|