Protect faster with Microsoft Defender XDR’s latest UX enhancements

Organizations are facing an unprecedented surge in cyberthreats and a global shortage of security experts, and Security Operations Center (SOC) teams are struggling with managing a rising influx of alerts, incidents, and raw telemetry produced by a variety of security tools to protect endpoints, email, identity, SaaS apps, data, and cloud infrastructure. Balancing the speed of response with the precision required for effective threat detection poses an ongoing challenge for SOC teams in optimizing their operational efficiency.
To help SOC teams protect faster, this week we are excited to share the general availability (GA) of our most recent user experience (UX) enhancements within Microsoft Defender XDR to make our industry-leading XDR platform easier to use than ever. These UX enhancements not only improve efficiency but also deliver an intuitive, smooth experience throughout the incident triage, investigation, and threat hunting processes for the SOC teams.
Incident customization
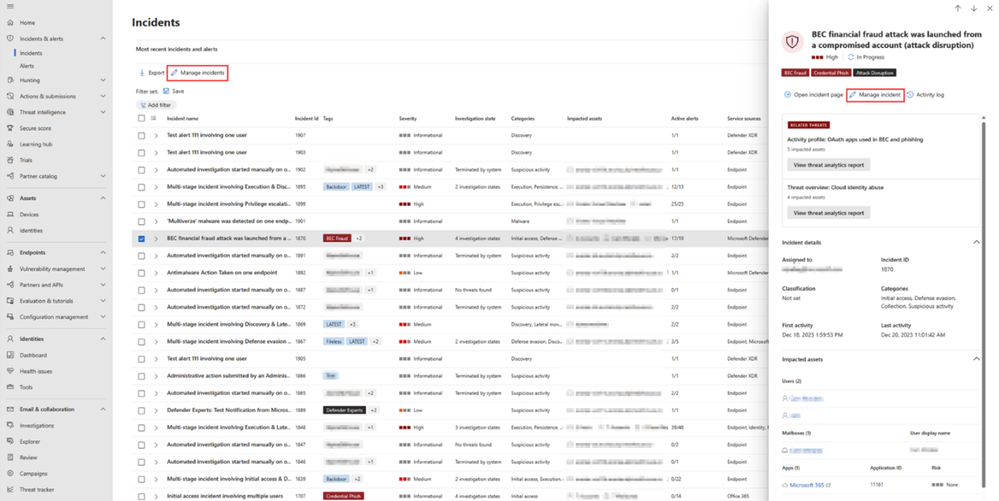
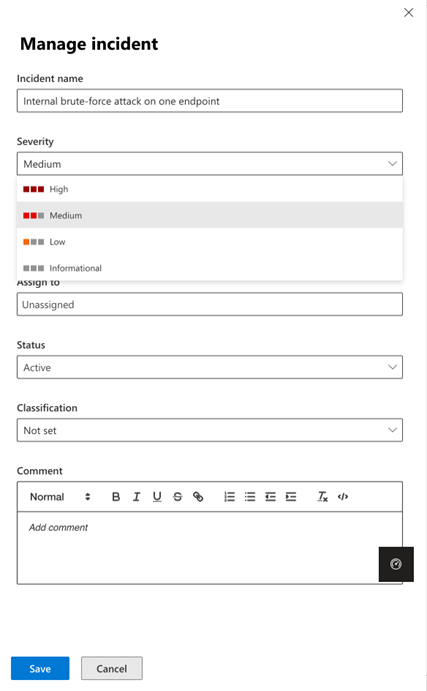
In Microsoft Defender portal, security analysts can choose which incidents should be prioritized based on several factors such as incident severity, incident status and more. To provide SOC analysts with a better and more customized incident management experience, we have added new capabilities to the “Manage incidents” action of the incident page so they can now assign incidents to security groups and change incident severity manually. Once you have the Incident side panel open, select the “Manage incident” action, and you will be able to assign the incident or change the incident severity manually.
In page-filters for the incident queue
Every second counts in cybersecurity. In SOC team’s daily work, customization saves time as it helps security analysts swiftly retrieve their preferred filter configurations. Today we are introducing a set of powerful in-page filters that improve the way you customize your incidents queue within Microsoft Defender XDR. Now, you can easily search for specific filters and save your frequently used filter sets to tailor your incident response experience. The new in-page filters provide a user-friendly interface that allows security analysts to efficiently locate and apply the filters they need. This time-saving capability enables security analysts to manage the incident queue more efficiently in a seamless and productive incident management process.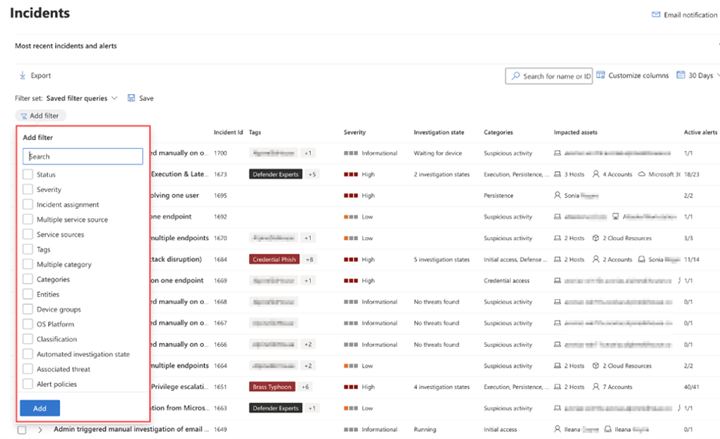
Incident activity log
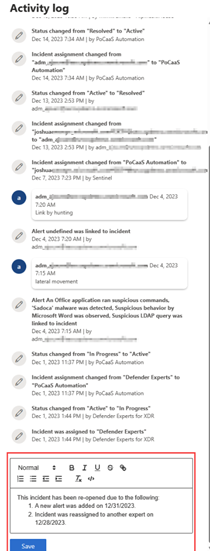
Gaining context in an easier and more efficient way represents another time-saving opportunity in security operations. Now with the new incident activity log, security analysts can thoroughly document the steps taken when investigating an incident. This not only ensures accurate reporting to management but also fosters seamless collaboration amongst coworkers. An analyst can also access records of comments on the incident made by other analysts.
Moreover, instead of plain text comments, analysts now have rich text comments for incidents. They can apply various formatting options such as bold, italics, underline, bullet points, and more, as well as add links and images to make their comments more expressive and informative. Additionally, the bi-directional synchronization feature with Microsoft Sentinel's activity log allows SOC teams to benefit from the seamless integration of logs and comments.
Go hunt within incident page
Go hunt feature is now available in the attack story of the incident page. This new feature allows security analysts to access the Advanced hunting function directly from the Incident Graph, providing a well-organized overview of incident-related data all within the same tab. With Go hunt, analysts can quickly gather more data on various entities such as devices, IPs, URLs, and files as shown in Figure 5. Additionally, they can link advanced hunting query results to a specific incident as shown in Figure 5, all from the same page.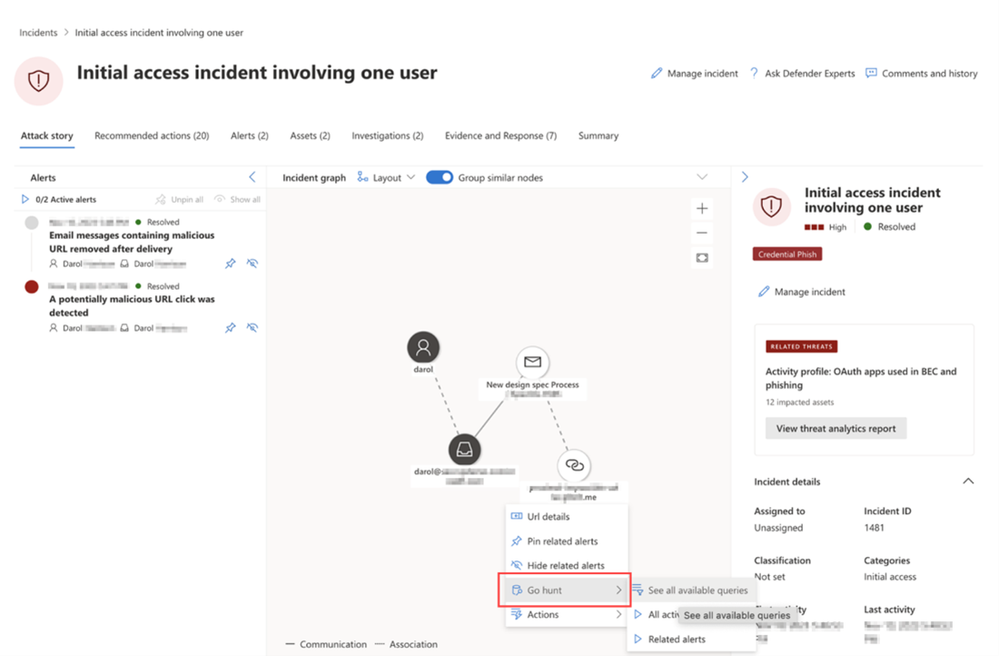
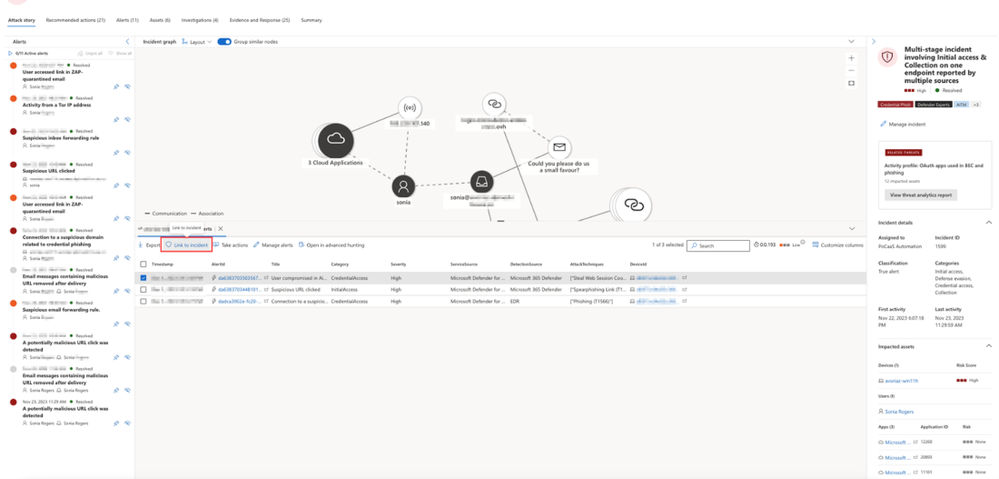
Hunt and investigate from Advanced hunting page
The new query history feature helps SOC analysts to seamlessly resume their work from where they left off. This functionality reduces the risk of losing any unsaved work by automatically retaining security analysts’ recent queries and allows analysts to effortlessly run and modify those queries at their convenience. 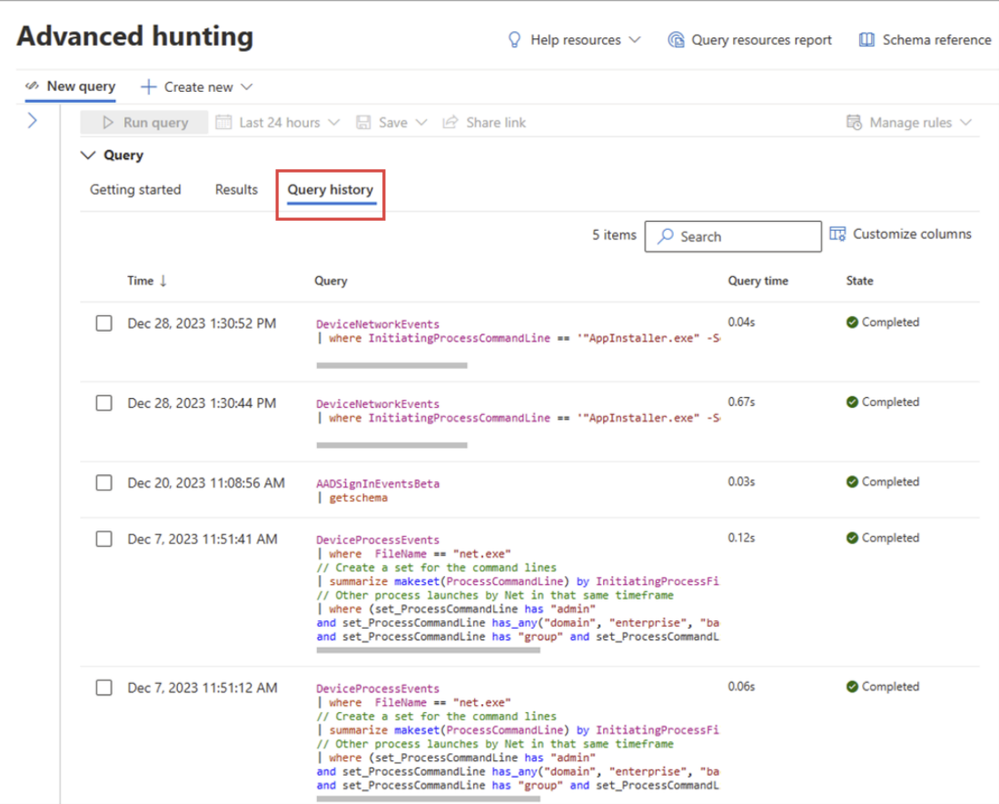
Another enhancement of the Advanced hunting page is the new inline results exploration functionality that facilitates a smoother results exploration experience and allows SOC analysts to conveniently navigate through all the parsed data within the results grid while eliminating the necessity for horizontal scrolling or side panels. SOC analysts now can expand the record of the results to explore its content within the results grid. In addition, they can expand specific cells of type JSON or array to easily explore their parsed content.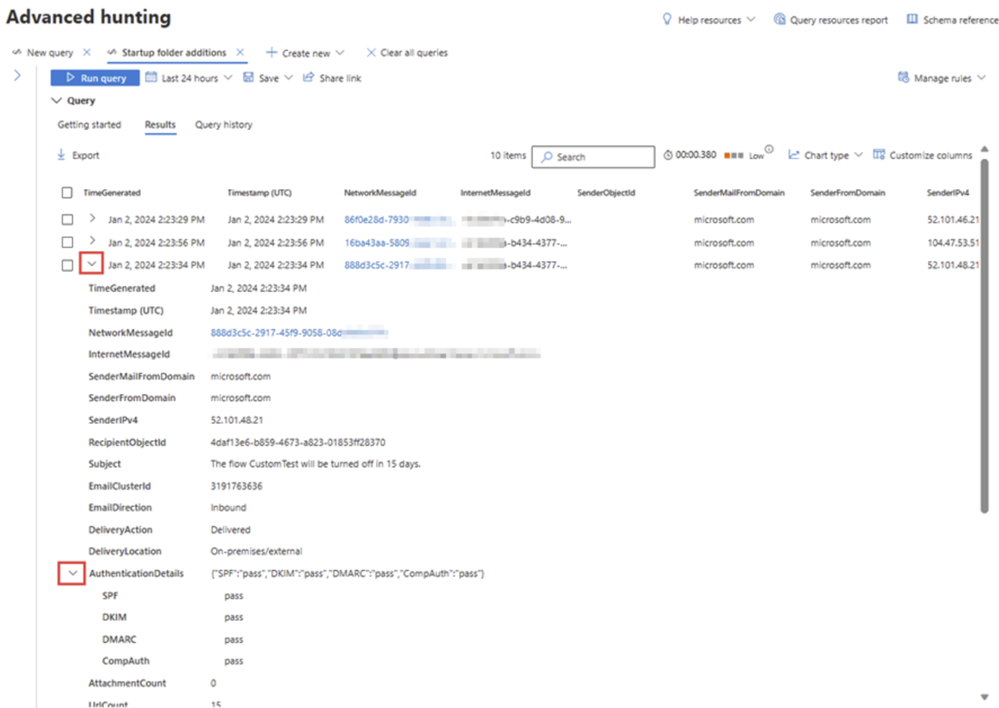
Furthermore, SOC analysts can now right-click on any result value in a row to add it as a filter to the existing query or copy the value to clipboard. This functionality preserves valuable time for analysts, allowing them to modify their queries in seconds based on the results, all without navigating away from the results grid.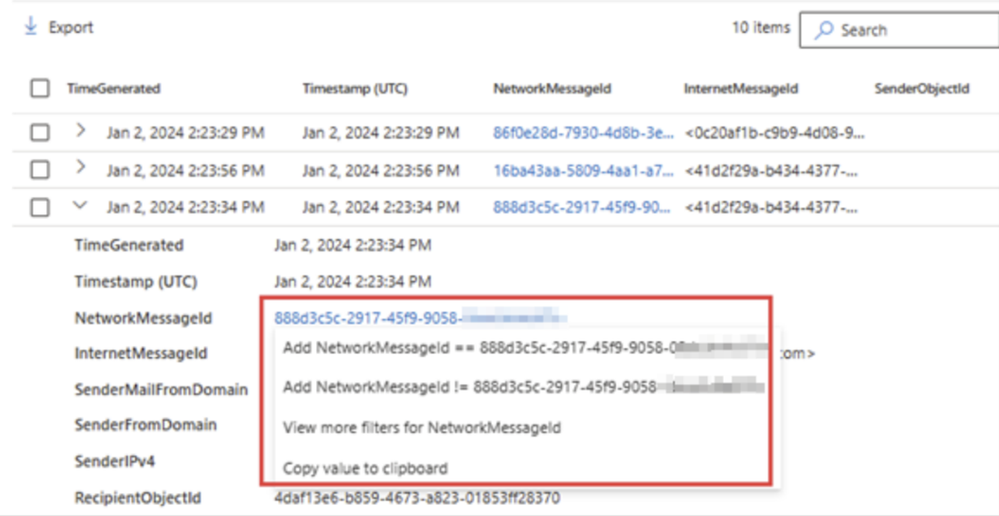
Speed and efficiency are crucial in security operations. The new UX enhancements in Microsoft Defender XDR make our XDR platform more user-friendly than ever before and provide an even more seamless and streamlined experience in incident triage, investigation, and threat hunting for SOC teams. The cumulative impact of each one of these improvements contributes to a significant enhancement in SOC efficiency.
Learn more:
- Read our documentation to get started:
- Visit our websites to learn more about Microsoft Defender XDR and unified security operations platform.
Published on:
Learn more