Remediate your Azure Kubernetes Service clusters at scale using Azure Policy’s mutation support!
We are thrilled to announce Azure Policy for Kubernetes Public Preview support for Mutation, available for Azure Kubernetes Service clusters! This release is brought to you in collaboration with Azure Kubernetes Service and Azure Container Compute Upstream.
Gatekeeper's mutation capability enables users to change Kubernetes resources at create/update time based on different criteria defined in mutation templates. By embedding mutation templates in your Azure Policy custom definitions, Azure Policy extends Gatekeeper’s mutation feature to programmatically modify components within your Kubernetes clusters at-scale across your subscriptions and management groups, with the help of various Azure Policy features, like selectors and overrides. For an overview of Azure Policy capabilities for Kubernetes, go to Azure Policy for Kubernetes.
When using mutation, you can do things like:
- Ensure all pods in a given scope have imagePullPolicy set
- Setting security context of containers in a selected scope to be non-privileged
- Adding a sidecar to a Pod
Get started
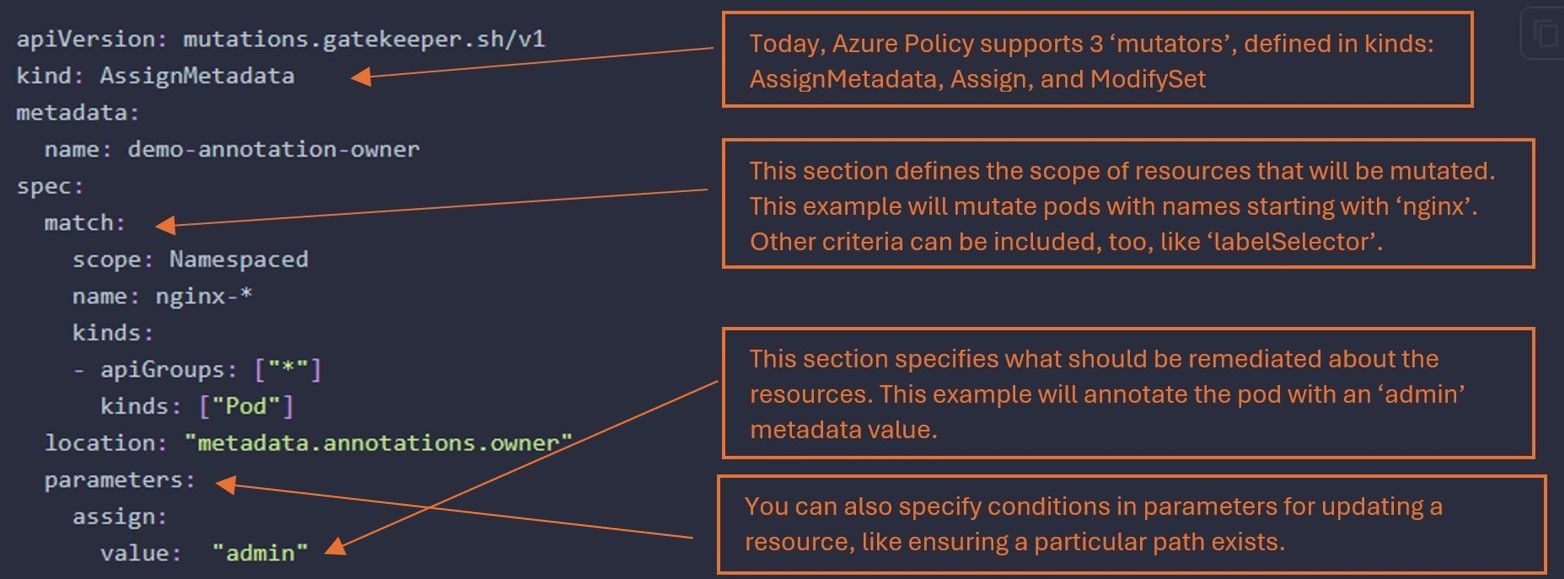
Here’s an example of a simple Gatekeeper mutation template, pulled from Gatekeeper documentation. It is annotated to highlight a few things:
Note: Azure Policy for Kubernetes does not currently support Gatekeeper’s ‘AssignImage’ mutator
You can choose to author your own mutation templates to embed in Azure Policy definitions, or you can use a sample from an existing repository, such as the Gatekeeper library.
Note: you will need to register the mutation feature on subscription(s) that you’d like to assign mutation policies within. The mutation feature’s resource ID is: Microsoft.Features/providers/Microsoft.ContainerService/features/AKS-AzurePolicyMutation
For more information, go to: Set up preview features in Azure subscription - Azure Resource Manager | Microsoft Learn.
When crafting a mutation policy definition, use the ‘mutationInfo’ property to embed your mutation template in your JSON definition. To learn more, go to: Understand how effects work - Azure Policy | Microsoft Learn. You can apply mutation policies similarly to how you apply other Azure Policies today (such as via API, Portal and PowerShell). This example will walk you through applying a mutation definition through the Azure Portal.
Azure Portal
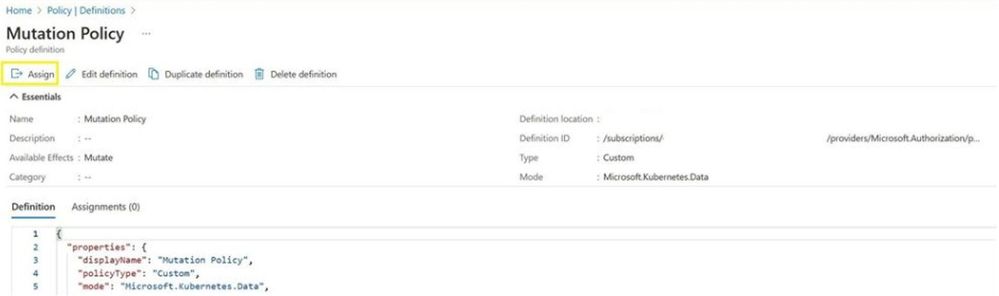
- Go to Azure Policy’s Portal view by searching ‘Policy’. Next, click the ‘Definitions’ tab to create a new definition.
- Create your Azure custom policy with a mutation template embedded. Ensure that you are using mode = “Microsoft.Kubernetes.Data”. Note that the “mutate” effect only works with mutation templates, not constraint templates.
- Assign your policy definition to the scope of your choice (such as your management group, subscription or resource group)
This definition will then apply to all clusters in that scope! You can choose to leverage Azure Policy's exclusions or exemptions if certain clusters should not be mutated by this policy assignment.
Your work is done! You can navigate to the ‘Compliance’ view to see all the clusters in scope for this mutation policy assignment.
If you run into issues, feel free to navigate to our troubleshooting tools in ‘Related Resources’. Try it out, and we would love to hear what you think in the comments below!
For related resources, go to:
- Learn Azure Policy for Kubernetes - Azure Policy | Microsoft Learn
- Mutation | Gatekeeper (open-policy-agent.github.io)
- gatekeeper-library/mutation at master · open-policy-agent/gatekeeper-library (github.com)
- Determine causes of non-compliance - Azure Policy | Microsoft Learn
- Troubleshoot common errors - Azure Policy | Microsoft Learn.