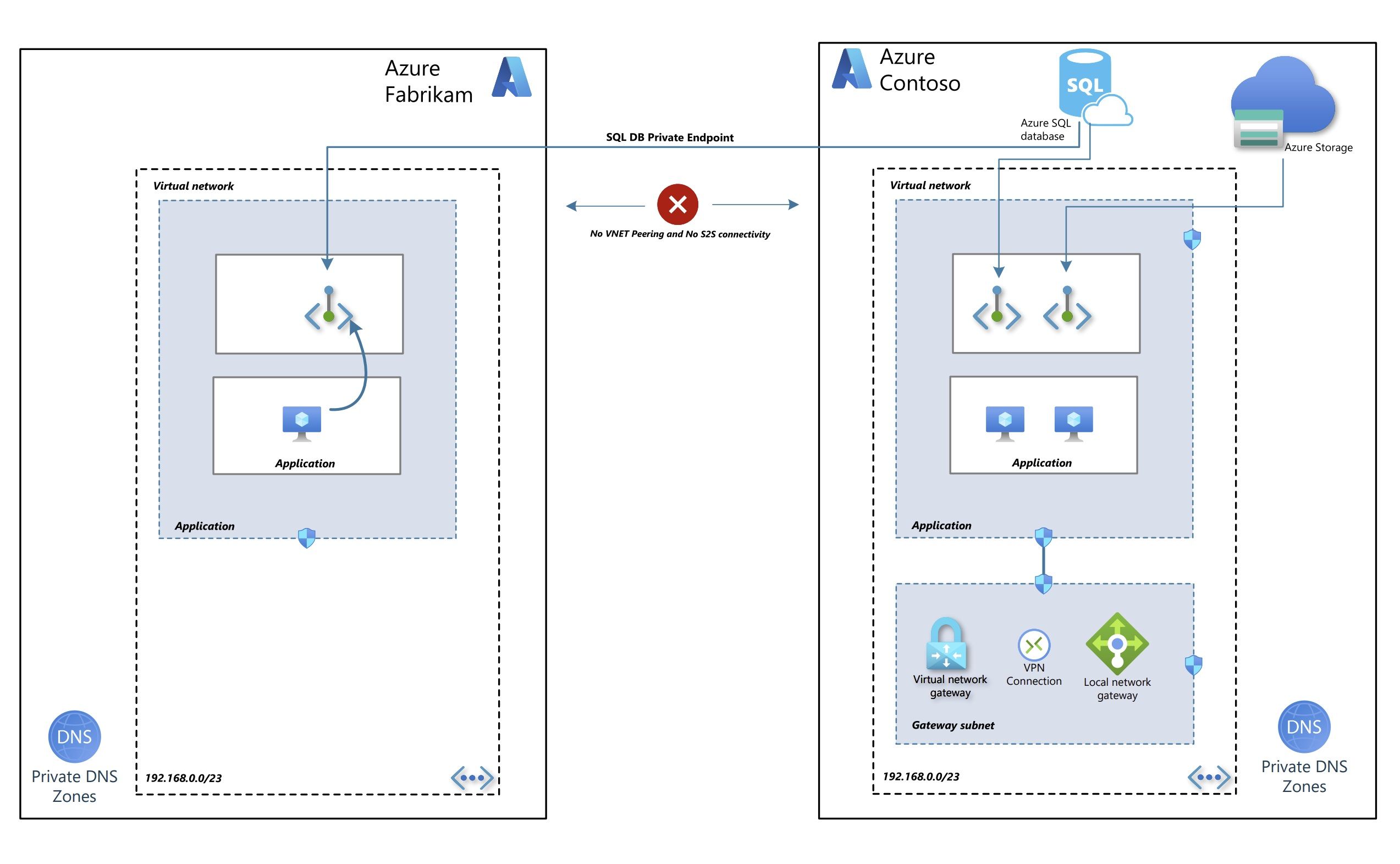
When Azure Policy starts a template deployment when evaluating deployIfNotExists policies or modifies a resource when evaluating modify policies, it does so using a managed identity that is associated with the policy assignment. Policy assignments use managed identities for Azure resource authorization. You can use either a system-assigned managed identity that is created by the policy service or a user-assigned identity provided by the user.
Each Azure Policy assignment can be associated with only one managed identity and, after adding a managed identity to policy assignment, it is possible to edit only some managed identity related settings of the policy assignment. For instance, the type of managed identity can be switched from system assigned and user assigned, but if a system assigned managed identity has been selected and created before, its location can’t be changed. E.g.:
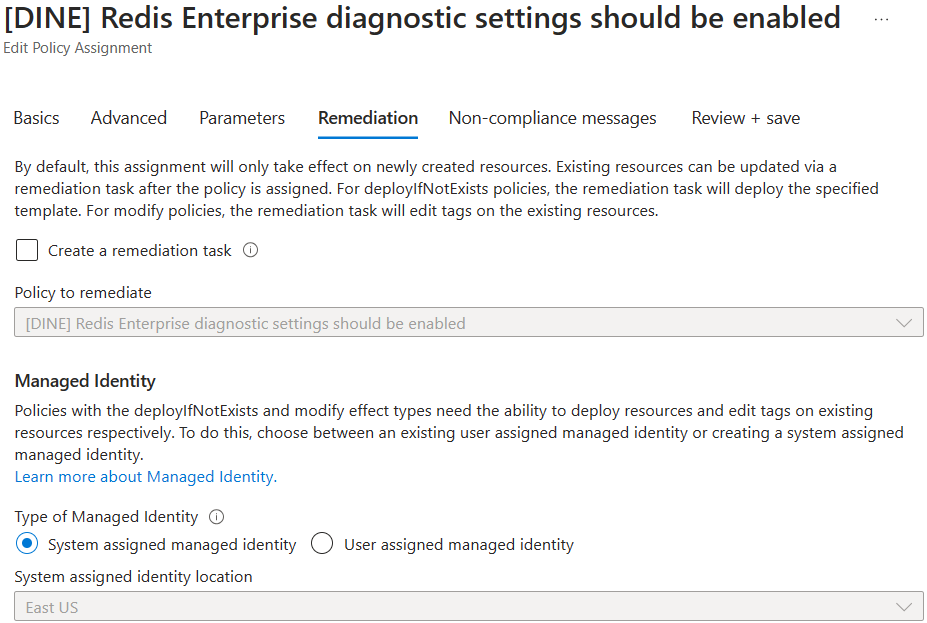 Edit policy assignment
Edit policy assignment
Azure Portal, CLI or PowerShell rely on the resource providers’ REST APIs and, in this case, on Policy Assignments - Update - REST API (Azure Policy) that allows the update of the identity property type, but does not allow the change of a system assigned managed identity location, for instance.
Therefore, to change the system assigned managed identity location, a new policy assignment should be created. As a suggestion, the policy assignment can be duplicated, and the system assigned managed identity location can be specified on the remediation section (that triggers the creation of a new system assigned managed identity) from the Azure Portal. Alternatively, a custom script (using CLI or PowerShell, for instance) can be used that gets the existing policy assignment’s properties and creates a new policy assignment with the same properties’ values except for the system assigned managed identity location. E.g.:
<# Disclaimer: This script is not supported under any Microsoft standard support program or service. This script is provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the script and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the script be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the current script or documentation, even if Microsoft has been advised of the possibility of such damages.
Additional note: The following script generates a new policy assignment id. Please take into consideration that any existing solution(s) built around the policy assignment id might be impacted.#>
$subscriptionId = "subscriptionId"
$policyAssignmentId = "policyAssignmentId"
$newSystemAssignedManagedIdentityLocation = "location"
Connect-AzAccount
Set-AzContext -Subscription $subscriptionId
# Check modules requirements
# Check if Az.Accounts module version 2.13.2 (or higher) is installed
if (-not((Get-Module -ListAvailable -Name Az.Accounts | Select-Object -ExpandProperty Version -First 1) -ge ([System.Version]"2.13.2"))) {
# Install Az module if not installed
Install-Module -Name Az.Accounts -Force
}
# Check if Az.Resources module version 6.12.1 (or higher) is installed
if (-not((Get-Module -ListAvailable -Name Az.Resources | Select-Object -ExpandProperty Version -First 1) -ge ([System.Version]"6.12.1"))) {
# Install Az.Resources module if not installed
Install-Module -Name Az.Resources -Force
}
Import-Module -Name Az.Accounts -RequiredVersion ([System.Version]"2.13.2")
Import-Module -Name Az.Resources -RequiredVersion ([System.Version]"6.12.1")
# Get policy assignment
$policyAssignment = Get-AzPolicyAssignment -Id $policyAssignmentId
# Get policy assignment's policy definition
$policyDefinition = Get-AzPolicyDefinition -Id $policyAssignment.Properties.PolicyDefinitionId
# Get policy assignment's managed identity
$policyIdentity = $policyAssignment.Identity
# Get policy's managed identity role assignments
$policyIdentityRoleAssignments = Get-AzRoleAssignment -ObjectId $policyIdentity.PrincipalId
# Create new policy assignment's parameters from previous assignment
$newPolicyAssignmentParameters = @{}
$policyAssignmentParametersObject = $policyAssignment.Properties.Parameters.psobject.Properties | Select-Object -ExpandProperty Value -Property Name
$policyAssignmentParametersObject | ForEach-Object { $newPolicyAssignmentParameters[$_.Name] = $_.Value }
# Generate a 24 character long alphanumeric string to be used on the new policy assignment as id
$newPolicyAssignmentName = -join ((48..57) + (97..122) | Get-Random -Count 24 | % {[char]$_})
# Create new policy assignment
$newPolicyAssignment = New-AzPolicyAssignment -Name $newPolicyAssignmentName -DisplayName $policyAssignment.Properties.DisplayName -PolicyDefinition $policyDefinition -Scope $policyAssignment.Properties.Scope -PolicyParameterObject $newPolicyAssignmentParameters -IdentityType SystemAssigned -Location $newSystemAssignedManagedIdentityLocation
# Get new policy assignment's managed identity
$newPolicyIdentity = $newPolicyAssignment.Identity
if($newPolicyAssignment -ne $null) {
# Create new policy's managed identity role assignments
foreach ($roleAssignment in $policyIdentityRoleAssignments) {
New-AzRoleAssignment -ObjectId $newPolicyIdentity.PrincipalId -ObjectType "ServicePrincipal" -Scope $roleAssignment.Scope -RoleDefinitionName $roleAssignment.RoleDefinitionName
}
# Delete previous policy assignment
Remove-AzPolicyAssignment -InputObject $policyAssignment
}
In the case of a policy initiative assignment, it is not possible to duplicate the policy assignment from the Azure Portal. Again, a custom script can be used that gets the existing policy assignment’s properties and creates a new policy assignment with the same properties’ values except for the system assigned managed identity location. E.g.:
<# Disclaimer: This script is not supported under any Microsoft standard support program or service. This script is provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the script and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the script be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the current script or documentation, even if Microsoft has been advised of the possibility of such damages.
Additional note: The following script generates a new policy assignment id. Please take into consideration that any existing solution(s) built around the policy assignment id might be impacted.#>
$subscriptionId = "subscriptionId"
$policyAssignmentId = "policyAssignmentId"
$newSystemAssignedManagedIdentityLocation = "location"
Connect-AzAccount
Set-AzContext -Subscription $subscriptionId
# Check modules requirements
# Check if Az.Accounts module version 2.13.2 (or higher) is installed
if (-not((Get-Module -ListAvailable -Name Az.Accounts | Select-Object -ExpandProperty Version -First 1) -ge ([System.Version]"2.13.2"))) {
# Install Az module if not installed
Install-Module -Name Az.Accounts -Force
}
# Check if Az.Resources module version 6.12.1 (or higher) is installed
if (-not((Get-Module -ListAvailable -Name Az.Resources | Select-Object -ExpandProperty Version -First 1) -ge ([System.Version]"6.12.1"))) {
# Install Az.Resources module if not installed
Install-Module -Name Az.Resources -Force
}
Import-Module -Name Az.Accounts -RequiredVersion ([System.Version]"2.13.2")
Import-Module -Name Az.Resources -RequiredVersion ([System.Version]"6.12.1")
# Get policy assignment
$policyAssignment = Get-AzPolicyAssignment -Id $policyAssignmentId
# Get policy assignment's policy definition
$policySetDefinition = Get-AzPolicySetDefinition -Id $policyAssignment.Properties.PolicyDefinitionId
# Get policy assignment's managed identity
$policyIdentity = $policyAssignment.Identity
# Get policy's managed identity role assignments
$policyIdentityRoleAssignments = Get-AzRoleAssignment -ObjectId $policyIdentity.PrincipalId
# Create new policy assignment's parameters from previous assignment
$newPolicyAssignmentParameters = @{}
$policyAssignmentParametersObject = $policyAssignment.Properties.Parameters.psobject.Properties | Select-Object -ExpandProperty Value -Property Name
$policyAssignmentParametersObject | ForEach-Object { $newPolicyAssignmentParameters[$_.Name] = $_.Value }
# Generate a 24 character long lower case alphanumeric string to be used on the new policy assignment as id
$newPolicyAssignmentName = -join ((48..57) + (97..122) | Get-Random -Count 24 | % {[char]$_})
# Create new policy assignment
$newPolicyAssignment = New-AzPolicyAssignment -Name $newPolicyAssignmentName -DisplayName $policyAssignment.Properties.DisplayName -PolicySetDefinition $policySetDefinition -Scope $policyAssignment.Properties.Scope -PolicyParameterObject $newPolicyAssignmentParameters -IdentityType SystemAssigned -Location $newSystemAssignedManagedIdentityLocation
if($newPolicyAssignment -ne $null) {
# Create new policy's managed identity role assignments
foreach ($roleAssignment in $policyIdentityRoleAssignments) {
New-AzRoleAssignment -ObjectId $newPolicyIdentity.PrincipalId -ObjectType "ServicePrincipal" -Scope $roleAssignment.Scope -RoleDefinitionName $roleAssignment.RoleDefinitionName
}
# Delete previous policy assignment
Remove-AzPolicyAssignment -InputObject $policyAssignment
}