Making it easier to apply and manage security settings for your users in Microsoft 365

The Microsoft 365 commercial support team resolves customer support cases and provides support to help you be successful and realize the full potential and value of your purchase. Our support services extend across the entire lifecycle and include pre-sales, onboarding and deployment, usage and management, accounts and billing, and break-fix support. We also spend a considerable amount of time working to improve the supportability of Microsoft 365 services to reduce the number of issues you experience as well as minimize the effort and time it takes to resolve your issues if they do occur.
We’re excited to welcome one of our Microsoft 365 Supportability team members to talk more about how to manage security settings for users.
Brian: Welcome John! Let’s start with a little about your role in the CSS Modern Work Supportability team and what you’re focused on these days.
John: Sure. My name is John Inman and I’m a Senior Supportability Program Manager covering Identity and Azure Active Directory (Azure AD) with Microsoft 365. This includes scenarios with security, multi-factor authentication (MFA), single sign-on, and synchronization with Azure AD Connect. I spend most of my time working on feature and service improvements, self-help and diagnostics, and troubleshooting assets for our support engineers. I also watch for emerging issues our customers are reporting and work with the team to get ahead of those with solutions.
Brian: Security is definitely top of mind for a lot of our customers. What are you working on in the security area with Azure AD engineering for Microsoft 365?
John: I’d like to share a little background first… as part of an ongoing effort to reduce compromised accounts, Microsoft has implemented security policies that ensure our customers are secure by default.
For example, the rollout of the Security Defaults policy for newly created Microsoft 365 tenants on all license levels began in 2019 and finished in 2020. That meant that all tenants created after October 22, 2019, had the Security Defaults policy applied by default-unless the tenant admin disabled it after tenant creation. Security defaults requires two-factor authentication for all users and requires a user to register for MFA within 14 days.
For some admins, this didn’t work for various reasons. Usually, it’s because some users were still using Basic authentication in some way or had service accounts that can’t use two-factor authentication. For these tenants, we continue to recommend Conditional Access policies or per-user MFA settings.
The latest news is that security defaults is now rolling out in 2022 for existing Microsoft 365 tenants who have not already applied MFA and have yet to enable security defaults, Conditional Access policies, or per-user MFA settings.
So, with all this in mind, making it as easy as possible for admins to secure their tenant and manage MFA are the reasons behind the creation of the new Configure Multi-Factor Authentication feature in the Microsoft 365 admin center. Prior to this, and with the rollout of Security Defaults in 2019–2020, our admins had to go to the Azure Portal to manage Security Defaults, some didn’t know where to find it initially or weren’t expecting MFA–it led to a lot of support calls.
Brian: Wow, so the new Configure Multi-Factor Authentication feature will make it easier for Microsoft 365 admins to secure their users. So how do admins use this to manage MFA, Security Defaults or Conditional Access policies, and how is that changing exactly?
John: Managing MFA, security defaults and Conditional Access policies has traditionally been performed through the Azure Portal. While this method to manage security is effective and is absolutely still a good option, we recognized that many admins don’t regularly use the Azure Portal–some never do. So, now we have the capability in the Microsoft 365 admin center too!
With this, admins can manage MFA, Conditional Access policies and security defaults from within Microsoft 365. This is available to any Global admin, has context-sensitive help, and only shows the options that are available for that license. There are links or hover-over help for additional explanations at each step along with feedback links. Oh, and that feedback is reviewed regularly too; it doesn’t just disappear into the ether.
Managing MFA, Conditional Access and security defaults can still be done in the Azure Portal, for admins who prefer to manage it there. Nothing is being removed there-we just want our customers secure!
Here are a few snapshots of the configuration starting with the initial splash screen that includes an overview and stats for the number of admins protected by MFA within the last month.
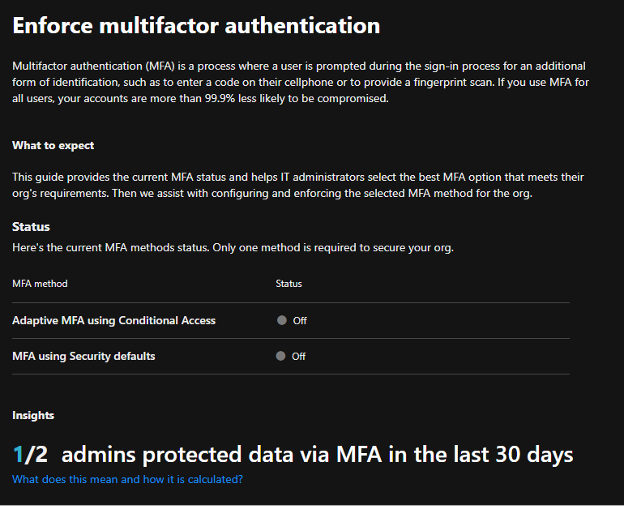
On the next screen, you choose whether to use Conditional Access policies or security defaults. These options are tailored to the license level of the tenant. If the tenant license supports Conditional Access, context-sensitive help will be displayed for that. We also recommend Conditional Access if possible as it provides the most flexibility and secure options for your environment.
The Security Default policy applies an MFA requirement across the entire tenant and blocks legacy authentication. With security defaults, there are no provisions for excluding specific user accounts from the policy requirement. Per-user or Conditional Access policies for MFA should be implemented if the tenant has requirements for basic/legacy authentication.
With Conditional Access policies, you can exclude certain accounts, such as an older email client, printer account or other application that may continue to require basic/legacy authentication methods, or users that may not have access to a phone for two-factor authentication.

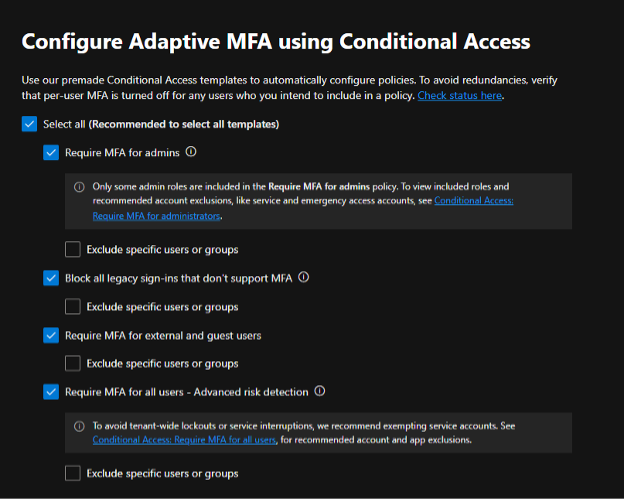
There are some basic templates that allow an admin to quickly deploy MFA using pre-defined Conditional Access policy options. Additional information is available under the “Learn more” section.

On this next screen for Conditional Access, you can provide one or more users or groups to exclude from the policy. This can be especially useful to still apply security across your tenant while excluding one or more specific accounts using legacy application, such as an account used for SMTP, printing, backup, or a service account.
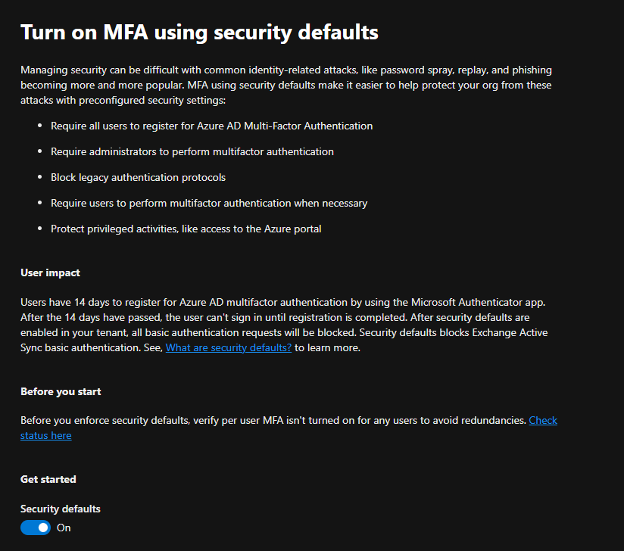
If your license doesn’t support Conditional Access policies, you can quickly turn on/off security defaults for your tenant. This setting will apply the Security Defaults policy to your tenant for all users. The setting can simply be toggled on or off as shown at the bottom of this screen. If you need to configure per-user MFA settings that can still be done in the Azure Portal, too.
Important: Admins should complete the registration for MFA within the 14-day period after enabling security defaults.
Finally, the summary screen will show which policy you’ve applied before exiting. In the example below, security defaults was applied, and a link is provided to manage it again if you change your mind.

Brian: Thanks John, for the detailed explanation and step-by-step! Any final words before we go?
John: We hope administrators find the option to configure MFA through the Microsoft 365 admin center helpful in deploying and managing MFA settings. We believe it’s a quick and easy way to secure your tenant using ready-to-apply security settings, such as the Security Defaults or Conditional Access policies depending on your license.
Check out these helpful resources for more information:
To configure MFA through the Microsoft 365 admin center:
Security Defaults:
- Security defaults in Azure AD - Microsoft Learn
- Security defaults and multi-factor authentication | Microsoft Learn
- Raising the Baseline Security for all Organizations in the World - Microsoft Tech Community
For a comparison of MFA capabilities by license:
John Inman is a Senior Supportability Program Manager in the CSS Modern Work Supportability team focused on Identity and Azure AD with Microsoft 365.
Brian Stoner is a Director in the CSS Modern Work Supportability team where he leads a team of technical and business program managers.
The CSS Modern Work Supportability team delivers innovative self-help solutions and diagnostics, in-service enhancements, and support programs to help customers get maximum value from their Microsoft 365 commercial subscriptions and create an easy-to-use, connected support experience.
Continue the conversation by joining us in the Microsoft 365 community! Want to share best practices or join community events? Become a member by "Joining" the Microsoft 365 community. For tips & tricks or to stay up to date on the latest news and announcements directly from the product teams, make sure to Follow or Subscribe to the Microsoft 365 Blog space!
Published on:
Learn moreRelated posts
Microsoft Copilot in Teams: Visual Insight for intelligent recap
Microsoft Copilot in Teams will soon provide intelligent meeting recaps that include content shared on screen, enhancing the summary’s r...
Microsoft Teams | Enhance your Teams experience with new accent colors
Microsoft Teams will introduce a new feature allowing users to select accent colors for visual customization. This update will be available on...
Take actions with Viva Pulse after Viva Glint engagement surveys is now GA!
Viva Pulse now integrates with Viva Glint, allowing managers to take targeted actions after Glint engagement surveys. This feature is availabl...
Introduction of secure workflow to bypass retention/legal holds on OneDrive and SharePoint
Microsoft is introducing a feature in Microsoft Purview Data Lifecycle Management allowing admins to bypass retention policies and delete cont...
Microsoft Viva: View and moderate private community content without being a member
This feature enables verified admins and Engage admins to access and moderate private community conversations without needing to be members of...
Microsoft Viva: Custom font and theme support for Viva Amplify
Viva Amplify now supports custom themes and fonts published to Brand Center, empowering communicators to align their campaigns with brand iden...
Microsoft Teams Premium: SMS support expands to Australia
Microsoft Teams Premium will soon support SMS appointment notifications to Australian phone numbers starting late July 2025. This update requi...
Microsoft 365 admin center: Usage reports – Copilot Chat – Usage intensity and new app coverage
The Copilot Chat usage report will include metrics on prompts submitted and expanded coverage across new host applications. Admins will now se...

