Identity Protection alerts now available in Microsoft 365 Defender
Azure Active Directory (Azure AD) Identity Protection alerts are now part of Microsoft 365 Defender.
Identity compromise is a pivotal component in any successful attack. By taking control over a legitimate organizational account, attackers gain the ability to move around the network, access organizational resources, and compromise more accounts. With sufficient permissions in hand, attackers have the “keys to the kingdom” to finally achieve their objective – encrypting the entire network, exfiltrating emails or other confidential information, or any other malicious goals. Because of this, it is critical for defenders to have wide visibility into identity activities and gain assistance in spotting suspicious or abnormal activities. This helps defenders identify, investigate, and respond to identity compromise, stopping and evicting attackers from the network.
With the appearance of modern attackers like Nobelium, we have seen identity compromise scenarios taken to the next level - extending across the organization’s on-prem network and cloud environment.
With Nobelium, attackers infiltrated the on-prem network and managed to compromise accounts with permissions to the AD FS server, which serves as an “LSASS of the cloud” – enabling users of the organization to gain access to cloud resources and services. Once attackers gained control of the AD FS server, they were able to mint tokens for cloud access and reach into user’s mailboxes to read and exfiltrate content.
Defenders must be able to monitor and protect identities of all kinds, across on-prem, in the cloud, and in-between.
Identity Protection is an important defense in your battle against identity compromise, bringing visibility and protection of Azure Active Directory identities.
You might already be familiar with the Identity Protection experience in the Azure or Entra Portals. Until now, if you wanted a full understanding of the role of Azure AD identities in end-to-end attacks, you needed to traverse both the Azure portal and the Microsoft 365 Defender portal. Now, we are bringing the Identity Protection alerts into Microsoft 365 Defender. Identity Protection alerts are now correlated into related incidents along with alerts from the other security domains, and can be reviewed directly in Microsoft 365 Defender for a full view of the end-to-end attack. No need to switch portals! This helps drive efficiency and simplicity for security teams investigating incidents to understand the full scope of the attacker’s activity and take action in one place.
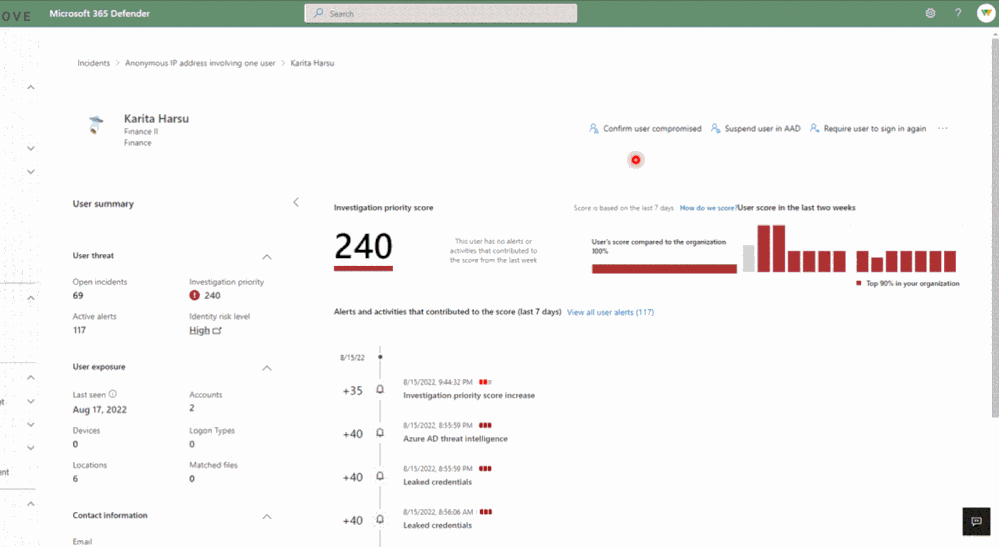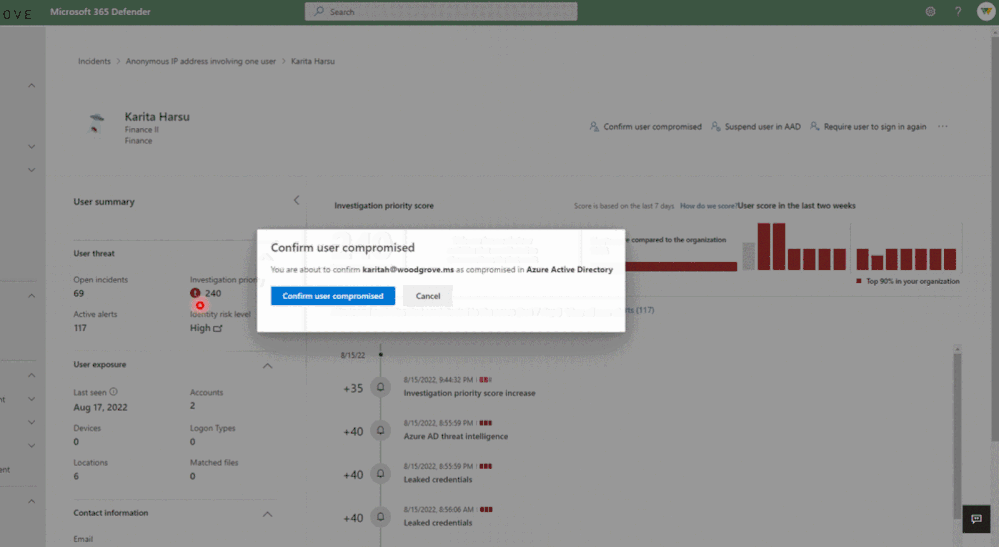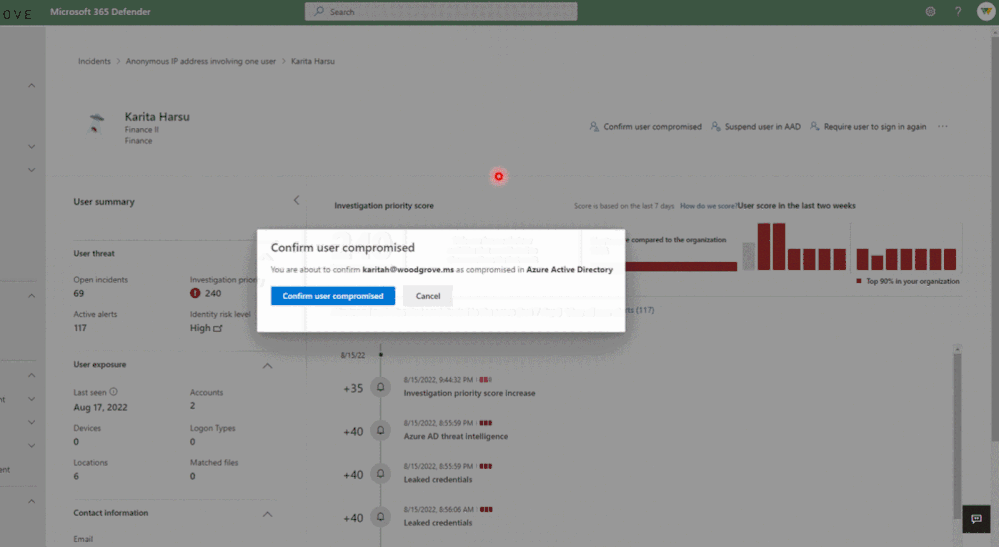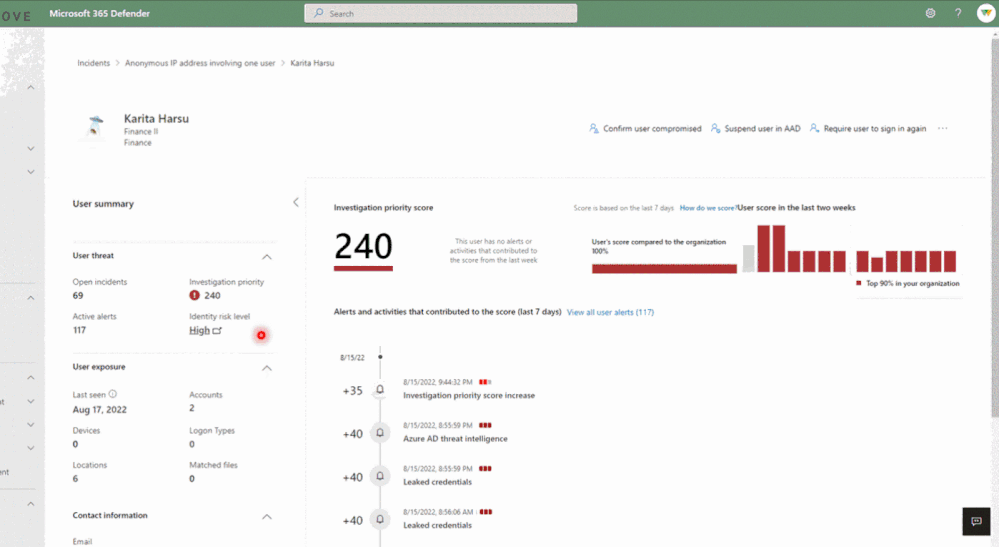
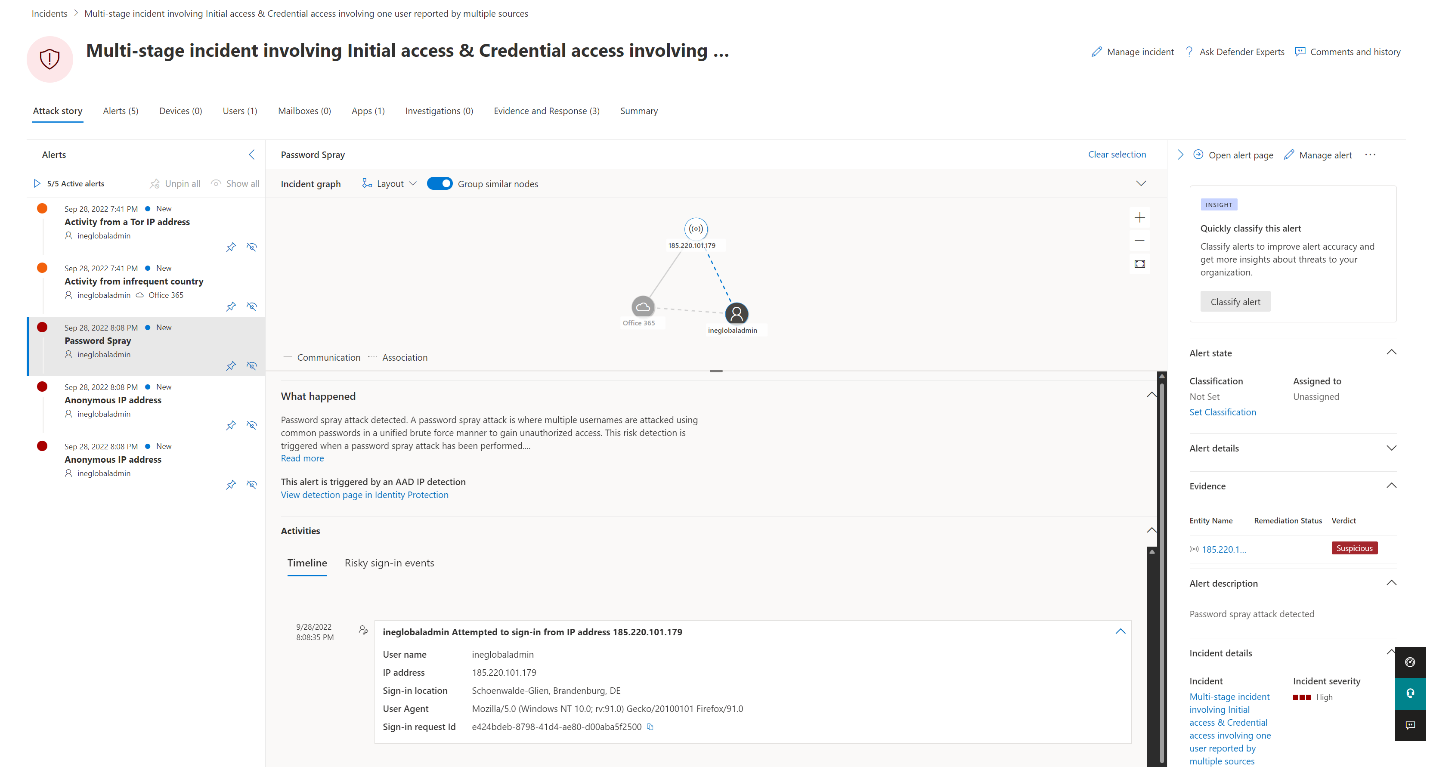
Example of an Azure AD Identity Protection alert within an incident
Azure Active Directory Identity Protection leverages trillions of signals to spot compromised identities. Identity Protection takes individual risk detections to compute a user’s overall likelihood of compromise, known as their user risk score. Identity Protection detects suspicious sign-in attempts by Azure AD accounts and uses additional signal to detect indicators of compromise offline. Some of these detections include unfamiliar sign-in properties, anomalous token, anonymous IP address, and leaked credentials. With Identity Protection, you not only gain insights into risky users, but have mechanisms to automatically mitigate and remediate risk.
To best leverage these Identity Protection signals and tune your environment to reduce false positive, we recommend you enable the risky user and risky sign-in policies for automatic remediation.
Additionally, there are several Microsoft 365 Defender correlations that generate new cross-product detections based on the compromised user alerts coming from Azure AD Identity Protection. Alerts include: "Suspicious searches in Exchange Online", "Suspicious quantity of downloaded archive files", "Suspicious domain trust modification following risky sign-in", and "Suspicious Addition of an Exchange related App Role". With this integration, you will also benefit from the combined detection signal.
Investigating Azure AD identity compromise alerts as part of the end-to-end incident helps security teams more easily determine root cause, identify affected identities in the attack, and handle the compromised identities more quickly and efficiently. For example, you can suspend specific accounts to block an attack progression and limit its impact. You can also confirm a user as compromised to move them to high risk in Identity Protection and trigger the aforementioned risky user policy to securely change their password.
A risky user in Microsoft 365 Defender with risk level generated by AAD Identity Protection and confirming that the user is compromised.
Once the incident investigation and response is done, the incident and Azure AD Identity Protection alert can be resolved in Microsoft 365 Defender. You can mark a user as compromised in Azure AD directly from the Microsoft 365 Defender user page. The incident status will automatically update in the Azure AD Identity Protection portal.
In addition to Azure AD Identity Protection alerts now being integrated into the Microsoft 365 Defender experience, they are also available via the Microsoft 365 Defender Incident API, so you can track incidents that include Azure AD Identity Protection alerts in Microsoft Sentinel or any other solution in your SOC.
Example of an Azure AD Identity Protection alert in the Microsoft 365 Defender portal
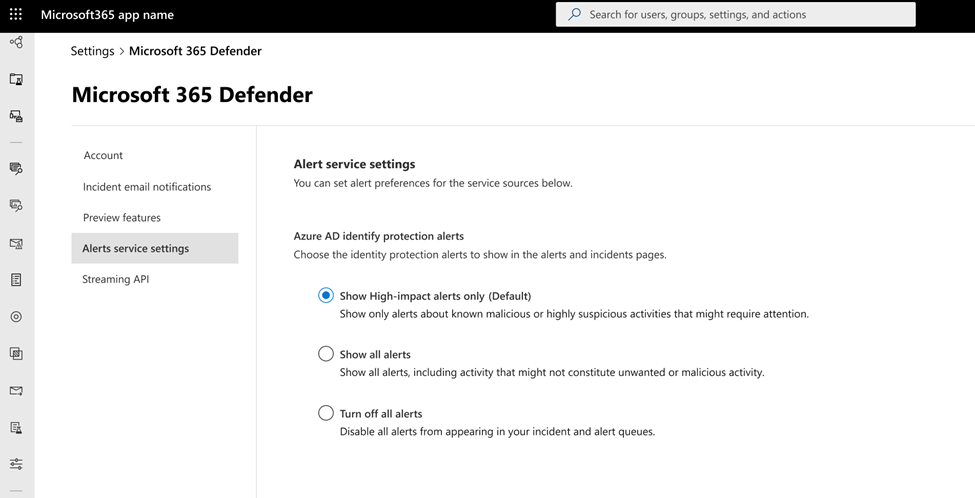
By default, only the most relevant alerts for the security operation center are enabled. If you want to get all AAD IP risk detections or turn the integration off, you can change it in Microsoft 365 Defender setting page under “Alert service setting” section
We’re excited for you to use and test this new capability, and we’re interested in your feedback! Let us know what you think by using the feedback tool in the Microsoft 365 Defender portal.
Published on:
Learn moreRelated posts
Update #21 for Automating Microsoft 365 with PowerShell
Update #21 for the Automating Microsoft 365 with PowerShell eBook is now available for current subscribers to download from Gumroad.com. Refre...
Microsoft 365 Copilot: Ground Chat in SharePoint Lists using Context IQ
Microsoft 365 Copilot will allow users to search for and insert SharePoint Lists into chat prompts via Context IQ, enhancing response accuracy...
Microsoft Copilot (Microsoft 365): Explain slide selection during PowerPoint Live
This feature enhances the PowerPoint Live meeting experience by using Copilot to let attendees select slide text and get explanations for the ...
SharePoint: New SharePoint Experience
We are introducing a reimagined SharePoint experience designed to be simple and intuitive, centered on the core jobs of discovering knowledge,...
Microsoft Viva: Copilot Analytics: Copilot adoption PBI version update including Power user insights
The updated Copilot adoption Power BI report will come with a streamlined UX and new Power user insights. Product Microsoft Viva Release phase...
SharePoint Actions Without JSON in Seconds
Microsoft Teams: Upcoming changes to Microsoft Places licensing and feature access
Starting April 1, 2026, Microsoft Places licensing will shift from user-based to space-based, making core features widely available without Te...
Microsoft Teams: Reduced automatic updates in Meet Now channel meeting threads
Microsoft Teams will reduce automatic updates in Meet Now channel meeting threads to keep channels cleaner and show actual user replies. Meeti...