Boost your detection and response workflows with alert tuning

As cyber threats become more sophisticated and frequent, organizations need to be vigilant in monitoring their digital assets for potential security breaches.
Microsoft 365 Defender is an XDR platform that delivers a unified investigation and response experience and provides native protection across endpoints, hybrid identities, email, collaboration tools, and cloud applications with centralized visibility, powerful analytics, and automatic attack disruption.
Today we are excited to introduce alert tuning in Microsoft 365 Defender to help security teams detect and respond to potential security threats even more effectively.
Alert tuning enhances how organizations monitor alerts and incidents. It enables analysts to set specific criteria to resolve alerts automatically using different attributes such as user, device, file, or app for all Microsoft 365 Defender sources. This feature makes it easier to calibrate alerts and keep the list of active incidents focused on the most relevant and critical issues.
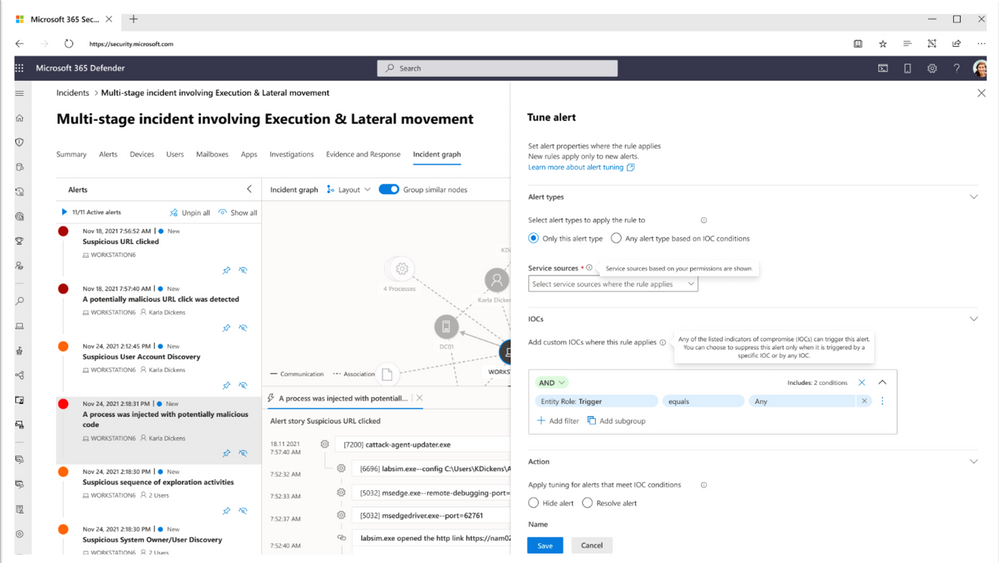
Alert tuning is designed to help security teams streamline their incident response process by automating the resolution of common and repetitive alerts. This will allow analysts to focus on the most critical issues, rather than getting bogged down in routine tasks, while also helping organizations respond to potential threats faster.
In addition, it will help enhance the overall accuracy of alert notifications by setting specific criteria for alerts that are relevant to their environment. This will help reduce the number of false positives and further limit noise to ensure that analysts investigate and focus on prevalent security incidents instead.
The new alert tuning feature in Microsoft 365 Defender helps organization to better protect their digital estate against cyber threats by streamlining the incident response process and reducing false positives even further.
Start exploring this new feature today and find out how it can enhance your organization's detection and response process.
Learn more
- Check out our documentation and start tuning your alerts
- Want to learn more? Go to our website.
- Not using the Microsoft XDR platform yet? Get started today.
Published on:
Learn moreRelated posts
Power Automate – Troubleshoot Copilot in cloud flows designer feature
We are announcing the ability to troubleshoot Copilot in cloud flows designer in Power Automate. This feature will reach general availability ...
Power Automate – Use your voice to interact with Copilot
This rollout will happen automatically by the specified dates with no admin action required before the rollout. Review your current configurat...
Power Automate – Configure Entra hybrid join for hosted machine groups
We are announcing the ability to configure Entra hybrid join for hosted machine groups in Power Automate. This feature will reach general avai...
How To Extract Tables From A PDF In Power Automate
Power Automate can extract tables from a PDF with the help of Azure AI Document ... The post How To Extract Tables From A PDF In Power Automat...
Power Automate – Secure credential retrieval in Power Automate for Desktop
We are announcing the Secure credential retrieval in Power Automate for Desktop feature for Power Automate. This feature enhances security and...
Dynamics 365 Business Central: How to disable/hide Power Automate action group for all users
Hi, Readers.Today I would like to briefly talk about how to disable/hide Power Automate action group for all users in Business Central. Power ...
Power Automate Flow Error: “Owner Needs Premium License” Even with Power Apps Premium
When testing a cloud flow in a Production environment, the following error appeared: This happened even though the flow owner already had a Po...