Azure Firewall: New Features and Region Availability
Contributors: Eliran Azulai, Gopikrishna Kannan, and Mark Gakman
With the increasing demand for cloud capabilities, we are continuing to observe new firewall use cases and deployment scenarios, and we are incredibly thankful for all the feedback that we have received. With today’s announcement, our goal is to continue to help IT administrators achieve their firewall goals efficiently and effectively. We are thrilled to announce a new set of releases that allows you to cater to your application needs, learn your network routes for determining SNAT behavior, migrate between SKUs with a single click, and introduce a new region.
- Explicit Proxy is now in public preview
- Auto-learn SNAT routes is now in public preview
- Single-Click Upgrade/Downgrade is now in general availability
- Poland Central is now in general availability
Azure Firewall is a cloud-native firewall as a service offering that enables customers to centrally govern and log all their traffic flows using a DevOps approach. The service supports both application and network-level filtering rules and is integrated with the Microsoft Threat Intelligence feed to filter known malicious IP addresses and domains. Azure Firewall is highly available with built-in auto-scaling.
Explicit Proxy is now in public preview
Azure Firewall offers advanced features to optimize your network traffic routing. By default, Azure Firewall operates in a transparent proxy mode, where traffic is routed through the firewall using a user-defined route (UDR) configuration. This mode ensures that the firewall intercepts the traffic inline and forwards it to its intended destination.
In addition to the default mode, Azure Firewall now supports Explicit proxy mode on the outbound path. With this mode enabled, you have the option to configure a proxy setting directly on the sending application, such as a web browser, with Azure Firewall acting as the designated proxy. This configuration allows traffic from the sending application to be directed to the private IP address of the firewall, facilitating direct egress from the firewall without the need for a UDR.
The Explicit proxy mode, currently available for HTTP/S traffic, empowers you to define proxy settings in your browser, pointing it to the private IP address of the firewall. You can choose to manually configure the IP address on the browser or application or leverage a proxy auto-config (PAC) file. If you opt for the latter, you can conveniently upload the PAC file to the firewall, which will then host and serve the proxy requests.
By leveraging the Enhanced Capabilities of Azure Firewall, you can optimize network traffic routing and enhance the performance and security of your applications.
Auto-learn SNAT routes is now in public preview.
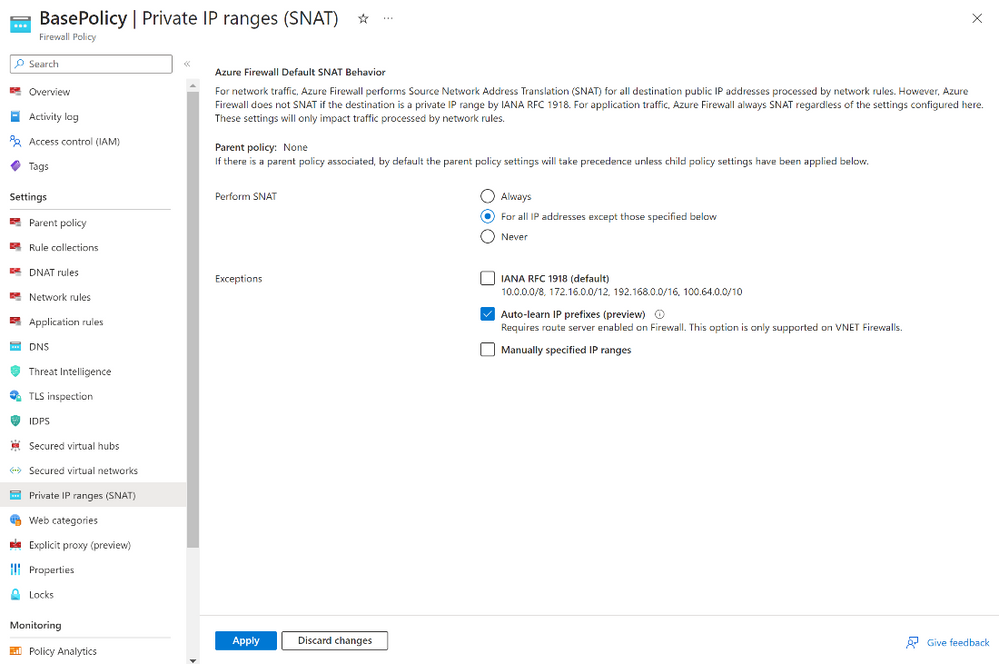
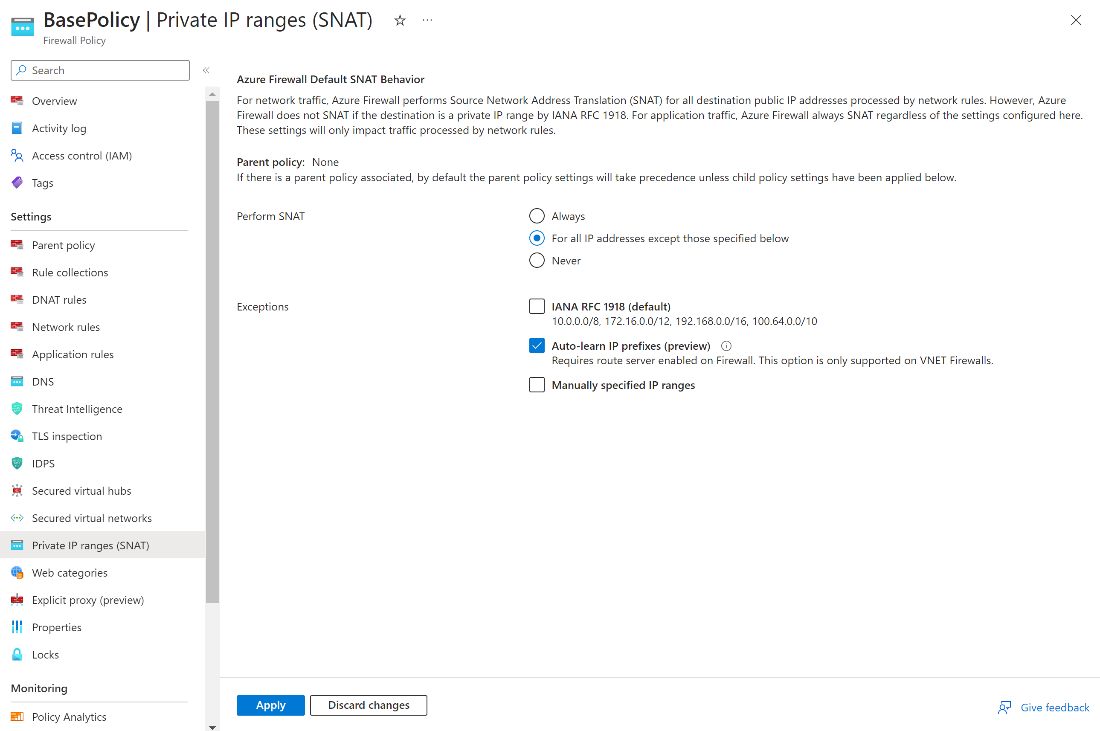
The Azure Firewall SNAT (Source Network Address Translation) feature is a built-in capability designed for routing outbound traffic to the Internet. By default, Azure Firewall will SNAT all traffic, excluding the IANA RFC 1918 addresses or shared address spaces per IANA RFC 6598 ranges (referred to as private ranges). In other words, the addresses will not undergo SNAT treatment through the Azure Firewall. In some cases, IT administrators may find it necessary to tailor the private ranges to avoid SNAT. For instance, an organization’s IT security might mandate the original client IP to remain unchanged for “all traffic flows” in a network with registered IP ranges outside of IANA RFC 1918 or IANA RFC 6598 ranges. In such cases, customers can modify the Firewall SNAT behavior by adjusting the network ranges following the documented steps.
This manual SNAT customization through the Azure Portal is suitable for small and medium sized organizations. However, large enterprises or government entities maintain extensive networks, and staying current with the dynamic changes in IP range can be a daunting task when relying solely on custom scripts. Any errors in the network range definitions have the potential to trigger application outages or a compromise security compliance.
As a result, organizations may prefer auto-learning of IP ranges, which is now in preview. This feature leverages Azure Route Service integration to auto-learn both registered and private ranges every hour and use the learned routes for SNAT purposes. The routes learned can be retrieved using APIs, Portal, or PS/CLI interfaces.
Figure 1: Image shows Private IP ranges (SNAT) settings, including Auto-Learn mode in (preview)
Single-Click Upgrade/Downgrade is now generally available
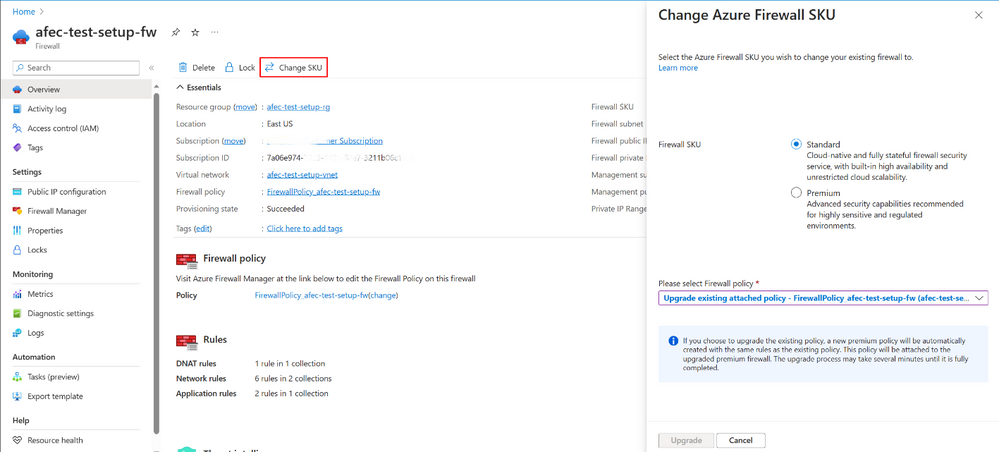
Azure Firewall Upgrade/Downgrade is a new capability that simplifies the process of upgrading your Azure Firewall Standard to the Premium SKU and downgrading your Azure Firewall Premium to Standard SKU. This feature allows you to upgrade your firewall without service downtime, with a single click of a button. The new capability enhances the existing migration procedure and eliminates the need for manual operations which are prone to errors.
In the upgrade process, users can select the policy to be attached to the upgraded Premium SKU, either by using an existing Premium Policy or by utilizing their existing Standard Policy. Customers can utilize their existing Standard policy and let the system automatically duplicate, upgrade to Premium Policy, and attach it to the newly created Premium Firewall.
Upgrading a firewall can be a time-consuming and complex process, especially in large and complex environments. It requires careful planning, testing, and execution to ensure that the upgrade process goes smoothly and does not cause any disruptions to the network. The new upgrade feature in Azure Firewall simplifies the upgrade process by reducing the effort and time required to upgrade the firewall. Instead of having to go through a lengthy and complex process, administrators can now upgrade the firewall with just a single click of a button.
This means that administrators can spend less time planning and executing upgrades, and more time focusing on other important tasks such as improving network security and performance. Additionally, the reduced time and effort required for upgrades can result in cost savings for organizations, as administrators can allocate their time and resources to other important tasks.
Furthermore, the new upgrade feature also ensures that during the upgrade/downgrade process, the firewall is always up and running and service downtime is not expected. This means that organizations can reduce the risk of cyber-attacks and other security incidents that may occur during Azure Firewall service downtime.
Figure 2: Image shows Change SKU setting, allowing user to migrate to Premium SKU with a single-click
New generally available region in Poland Central
To meet new workload demands, Azure Firewall Basic, Standard, Premium and Azure Firewall Manager are now generally available in Poland Central. With this new region, Azure Firewall is now available in 52 regions worldwide., utilizing the Microsoft global network backbone.
Figure 3: Image shows Microsoft's global network
Learn more
When you’re ready to try these new capabilities, just navigate to Azure Firewall Policy Settings for Explicit proxy and Private IP ranges (SNAT) under and Azure Firewall to Change SKU. And continue to provide us with feedback! To give us feedback just tap the feedback icon in the Azure Portal. Your feedback is invaluable in crafting an improved experience that caters to your specific needs.
Learn more in the following support articles:
Explicit Proxy (Preview) – Microsoft Learn
Auto-learn SNAT routes (Preview) - Microsoft Learn
Upgrade/Downgrade – Microsoft Learn
Azure Firewall – Microsoft Learn
Azure Firewall Manager – Microsoft Learn
About the author
Suren Jamiyanaa is a Product Manager in Azure Network Security. She joined the team in 2019 where she focuses on innovating the Azure Firewall product for customers in a modern cloud network strategy.
Published on:
Learn moreRelated posts
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...
General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB
Title: General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB We’re excited to announce the general availability of the ...
Efficiently and Elegantly Modeling Embeddings in Azure SQL and SQL Server
Storing and querying text embeddings in a database it might seem challenging, but with the right schema design, it’s not only possible, ...