Announcing public preview for watermarking on Azure Virtual Desktop

We're pleased to announce Watermarking for Azure Virtual Desktop (AVD) is now in public preview. This feature helps prevent sensitive information from being captured on client endpoints by enabling watermarks to appear as part of remote desktops.
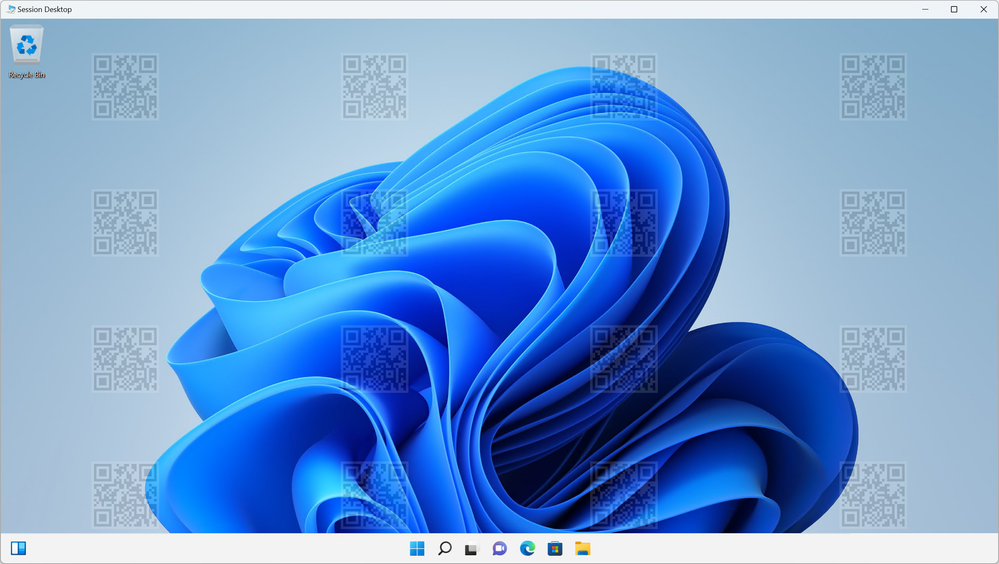
What can I do with AVD watermarking?
- Enable QR code watermarks on AVD desktops
- Scan the QR code watermarks to discover the session's connectionID
- Use the session's connectionID to find the session information via AVD Insights or Azure Monitor Log Analytics
Why is this important?
Alongside AVD screen capture protection, watermarking protects content on AVD from being stolen, used, or altered without the owner's permission. QR code watermarks allow you to trace the session's information.
How can I use it?
AVD watermarking is currently available for full desktops and Windows Desktop clients. Learn how to enable watermarking on AVD here.
Published on:
Learn moreRelated posts
November Patches for Azure DevOps Server
Today we are releasing patches that impact our self-hosted product, Azure DevOps Server. We strongly encourage and recommend that all customer...
Configuring Advanced High Availability Features in Azure Cosmos DB SDKs
Azure Cosmos DB is engineered from the ground up to deliver high availability, low latency, throughput, and consistency guarantees for globall...
IntelePeer supercharges its agentic AI platform with Azure Cosmos DB
Reducing latency by 50% and scaling intelligent CX for SMBs This article was co-authored by Sergey Galchenko, Chief Technology Officer, Intele...
From Real-Time Analytics to AI: Your Azure Cosmos DB & DocumentDB Agenda for Microsoft Ignite 2025
Microsoft Ignite 2025 is your opportunity to explore how Azure Cosmos DB, Cosmos DB in Microsoft Fabric, and DocumentDB power the next generat...
Episode 414 – When the Cloud Falls: Understanding the AWS and Azure Outages of October 2025
Welcome to Episode 414 of the Microsoft Cloud IT Pro Podcast.This episode covers the major cloud service disruptions that impacted both AWS an...