Protect against PaperCut vulnerability with Azure Firewall Premium

Summary
On May 16th, 2023, PaperCut, a software company known for its multi-platform print management software, released an update to their advisory, stating that the exploitation of CVE-2023-27350 had been observed in real-world attacks
This vulnerability allows remote attackers to bypass authentication and execute arbitrary code in the context of SYSTEM. It affects PaperCut MF and NG Application and Site Servers version 8.0 and above, across all supported operating systems. A patch was made available by PaperCut in versions 20.1.7, 21.2.11, and 22.0.9 and it is recommended to apply it at the earliest on all vulnerable servers.
Although the vulnerability had already been addressed by a released patch, attackers take advantage of a vulnerability that has been patched but not yet updated by all users. This situation is commonly referred to as an "n-day attack”.
To avoid exploitation of "n-day attack”, it is recommended to apply extra measure by protecting your network with a network security service such as Azure Firewall. Customers using Azure Firewall Premium have enhanced protection from this RCE vulnerability and exploit from the get-go. The Azure Firewall Premium IDPS (Intrusion Detection and Prevention System) ruleset automatically updates include detection and protection against CVE-2023-27350 vulnerability since May 5th, 2023. At Microsoft and in the Azure Firewall product engineering team, we are committed to protecting our customers from malicious exploits by constantly updating our IDPS signature database to detect and prevent attacks on your environment.
In this blog post, we will reveal the activities made by threat actors, we will discuss the process of uncovering the vulnerability, examining its root cause based on the security advisory and analyzing the solution provided with Azure Firewall Premium. Our aim is to provide a comprehensive understanding of this vulnerability and its implications.
Threat Actor Activities
Based on information from the FBI, it was discovered, in early May 2023, that the Bl00dy Ransomware Gang managed to infiltrate the networks of various educational facilities. These facilities had PaperCut servers that were vulnerable to CVE-2023-27350 and exposed to the internet. As a result, the gang was able to carry out operations that involved stealing data from the compromised systems and encrypting them. To notify the victims, ransom notes were left on their systems, demanding payment in exchange for the decryption of the encrypted files (refer to Figure 1)
Figure 1: Example Bl00dy Gang Ransomware Note
The FBI also identified information relating to the download and execution of command and control (C2) malware such as DiceLoader, TrueBot, and Cobalt Strike Beacons, although it is unclear at which stage in the attack these tools were executed.
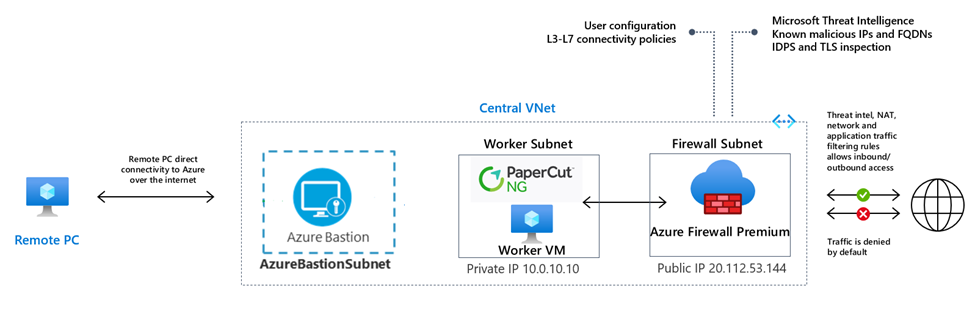
Building Lab Setup
We'll use a template to deploy a lab environment that has a central VNet (10.0.0.0/16) with three subnets:
- A Worker subnet (10.0.10.0/24)
- An Azure Bastion subnet (10.0.20.0/24)
- An Azure Firewall subnet (10.0.100.0/24)
To easily deploy this Lab setup to Azure using a predefined template, you can just click:
A Bastion Host is also deployed and can be used to connect to the Windows testing machine (Worker VM). Login to the Worker VM using Bastion and install a vulnerable version of PaperCut NG, I was using NG version 18.3.9. You can use this link to download old NG versions: Download past/old PaperCut NG versions | PaperCut
Note: Azure Firewall Public IP addresses differ from one deployment to another.
Customizing Azure Firewall Premium
Now, let’s configure Azure Firewall Premium to NAT (Network Address Translation) and route incoming HTTP requests destined to Azure Firewall Public IP 20.112.53.144:9191 to the PaperCut NG application that we just installed on the Worker VM private IP 10.0.10.10:9191.
You can use this Destination NAT (DNAT) rule to perform this setting:
Finally, let’s activate Azure Firewall IDPS by setting its mode to ‘Alert’, in this mode Azure Firewall will generate a log entry for malicious detected traffic.
Detecting PaperCut CVE-2023-27350 in Lab
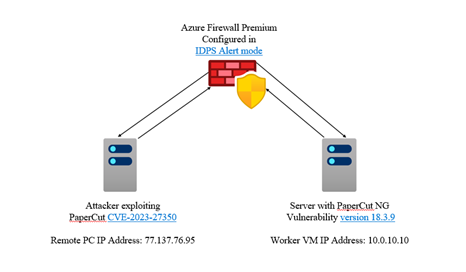
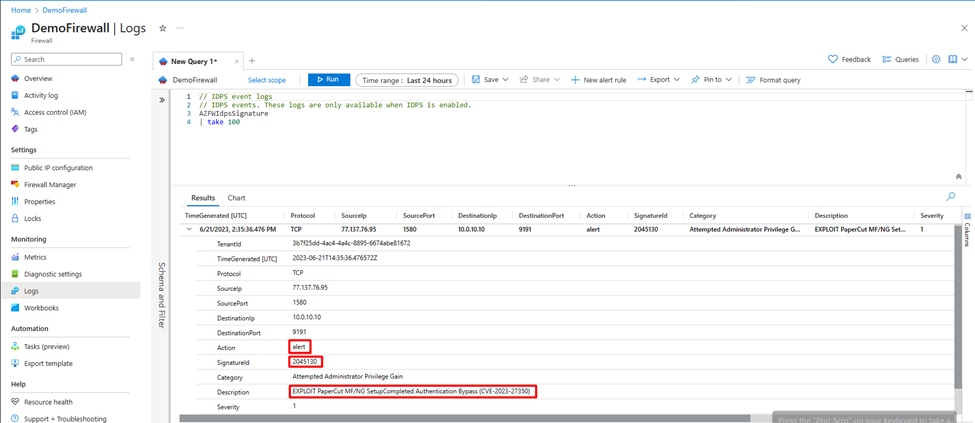
To exploit CVE-2023-27350, a malicious actor must first visit the SetupCompleted page of the intended target, which will provide the adversary with authentication to the targeted PaperCut server. Azure Firewall Premium IDPS signature ID 2045130 will detect when GET requests are sent to the SetupCompleted page.
The following simplified diagram shows the three main components which are involved in this exploit simulation. A malicious HTTP GET request is submitted from the attacker towards PaperCut NG server. The request is being inspected by Azure Firewall Premium to detect, alert and deny this malicious HTTP request.
To simulate the exploit, open the browser on your remote PC and access the following URL:
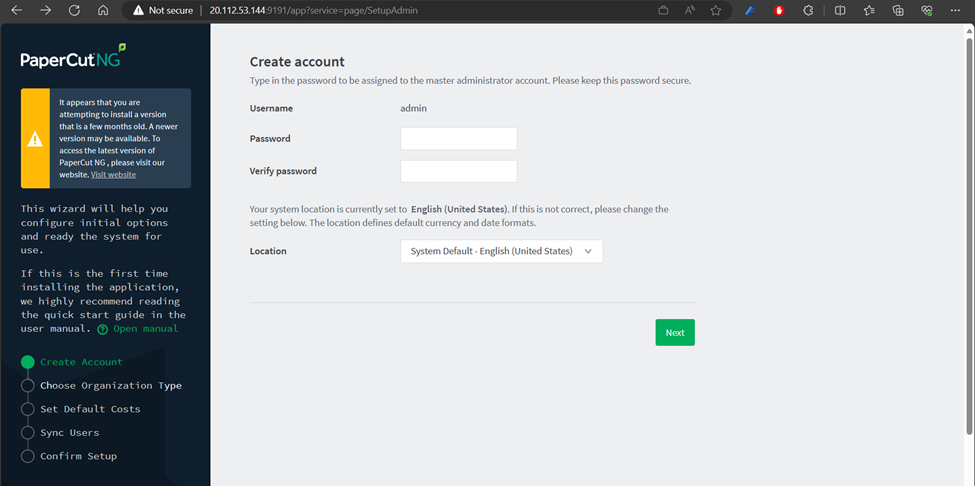
http://20.112.53.144:9191/app?service=page/SetupAdmin
You should be able to view this PaperCut NG service login page:
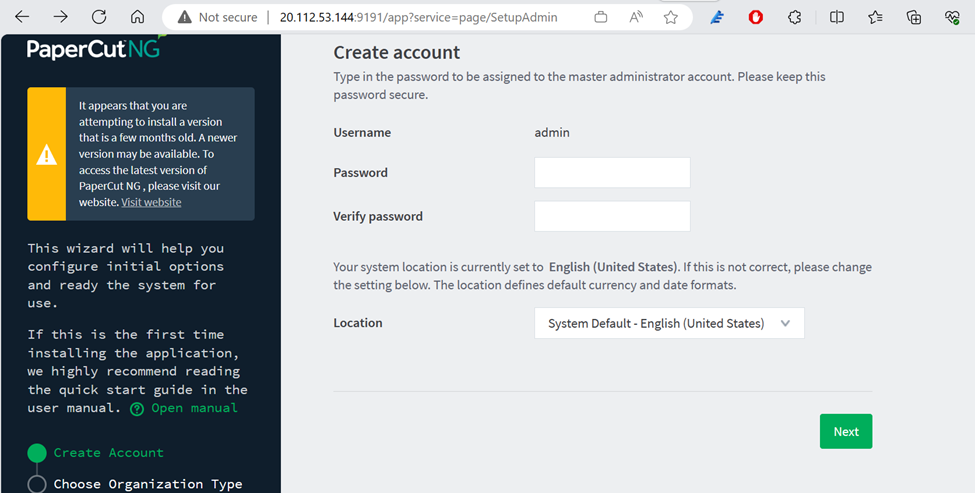
To exploit PaperCut NG vulnerability, edit the URL suffix and replace ‘SetupAdmin’ with ‘SetupCompleted’
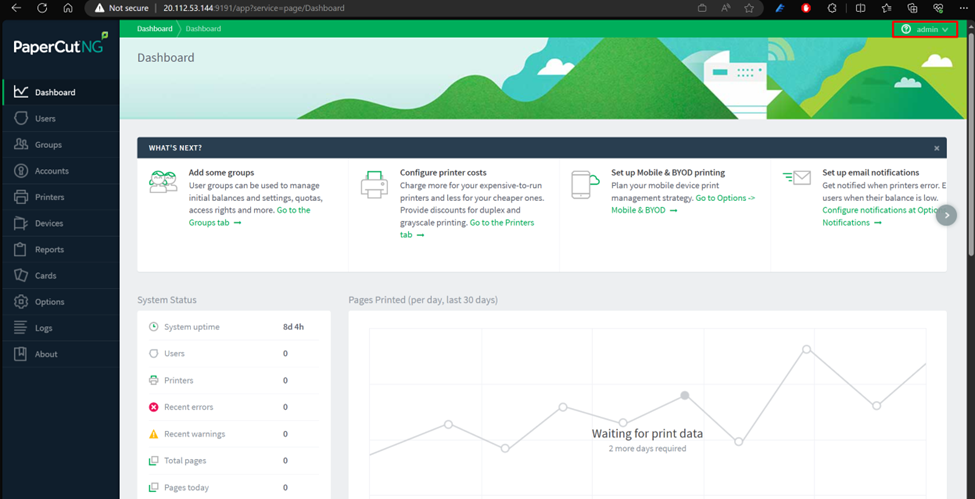
http://20.112.53.144:9191/app?service=page/SetupCompleted
You should be able to view this html screenshot, and by clicking on the ‘login’ button you shall have full admin access to the service (see top right ‘admin’ user in the second figure).
In Azure Firewall IDPS logs, you can clearly identify your HTTP request being alerted by Azure Firewall due to a match with Signature ID 2045130.
Protecting against CVE-2023-27350 in Lab
Change Azure Firewall IDPS mode to ‘Alert and deny’ as captured below:
Open the browser on your remote PC and access the following URL:
http://20.112.53.144:9191/app?service=page/SetupAdmin
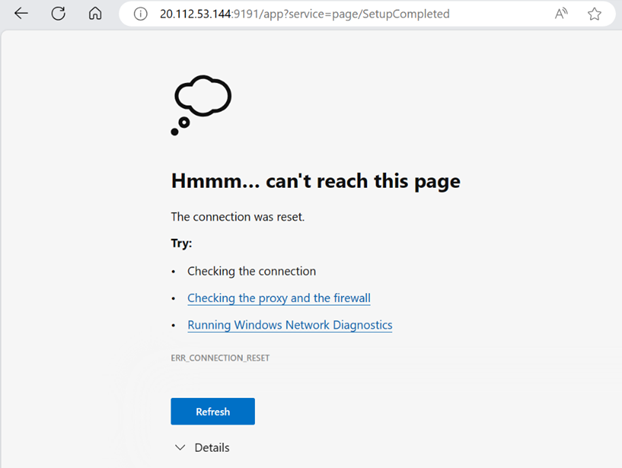
This time, when you’ll change the URL suffix to “SetupComeleted”, you should be blocked by Azure Firewall Premium, and the following page shall be displayed:
In Azure Firewall IDPS logs, you can clearly identify your HTTP request being blocked by Azure Firewall due to a match with Signature ID 2045130.
Conclusion
To protect against the PaperCut vulnerability CVE-2023-27350 and its associated exploits, it is crucial to promptly update your servers with the provided patches. However, to mitigate the risk of "n-day attacks," additional measures are recommended.
Implementing Azure Firewall Premium can provide enhanced protection against CVE-2023-27350. With its Intrusion Detection and Prevention System (IDPS) ruleset of 65,000 signatures being updated daily, Azure Firewall Premium detects and prevents attacks on your environment. Customers can have peace of mind knowing that they don't have to manually update their Azure Firewall configuration. The IDPS signature database is automatically updated for them, ensuring continuous protection against evolving threats.
To safeguard your network:
- Apply PaperCut's patches promptly.
- Consider utilizing Azure Firewall Premium for added protection.
- Monitor Azure Firewall's IDPS logs for suspicious activity.
- Stay informed about security advisories and best practices.
By taking these actions, you can significantly reduce the risk of falling victim to CVE-2023-27350 and similar exploits. Protect your network and data with a proactive and multi-layered approach, utilizing Azure Firewall Premium as part of your security strategy.
For more information on everything we covered above, please see the following documentation:
- URGENT MF/NG vulnerability bulletin | PaperCut
- NVD - CVE-2023-27350 | (nist.gov)
- Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG | CISA
- Azure Firewall Premium features | Microsoft Docs
Published on:
Learn moreRelated posts
Linux on Azure customer montage
June Patches for Azure DevOps Server
Today we are releasing patches that impact the latest version of our self-hosted product, Azure DevOps Server. We strongly encourage and recom...
BYOM: Using Azure AI Foundry models in Copilot Studio
Copilot Studio gives you a fast, secure way to build conversational agents and deploy them into the Microsoft 365 environment without writing ...
Building a Modern Python API with Azure Cosmos DB: A 5-Part Video Series
I’m excited to share our new video series where I walk through building a production-ready inventory management API using Python, FastAP...
Azure Developer CLI (azd) – June 2025
This post announces the June release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – June 2025 appeared first o...
Restricting PAT Creation in Azure DevOps Is Now in Preview
As organizations continue to strengthen their security posture, restricting usage of personal access tokens (PATs) has become a critical area ...