Batch pool with user assigned Managed Identity and Key Vault extension

On Feb 29th, 2024, the certificate feature in Azure Batch Account will be retired. To continue using the certificate with Batch task, user will need to migrate the Batch account certificates to Azure Key Vault. But since there is not an existing example provided, that might be a little difficult.
This blog will mainly focus on providing an example about how to recreate the Batch pool with required user assigned Managed Identity and Key Vault extension. Currently the Batch pool with user assigned Managed Identity and extension is only supported by ARM template and REST API call. Creating a pool with extension is unsupported in Azure Portal. Creating a pool with user assigned Managed Identity is unsupported in Az PowerShell module and Azure CLI.
Pre-requisite:
To follow this blog, please prepare the following points:
- A Batch Account
- A Key Vault
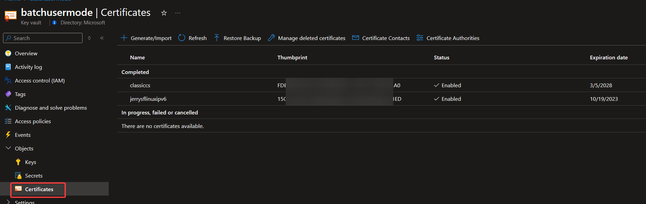
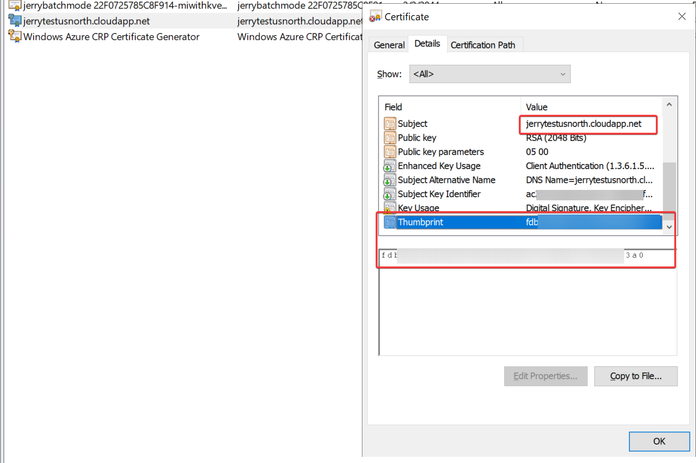
- Upload the certificates which was saved in Batch Account/Certificate, into Key Vault/Certificates
- A user assigned Managed Identity (The msiClientId in ARM template and REST API payload is the client ID of this Managed Identity)
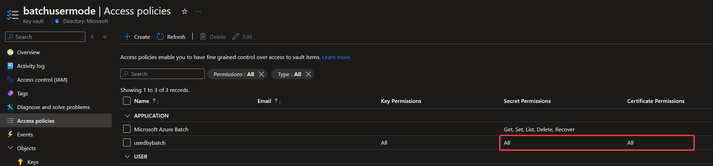
- Assign enough permission to get the certificate from Key Vault on the user assigned Managed Identity (You can also use RBAC assignment to allow permission in Key Vault)
Reminder:
In this blog, a sample Batch pool with the only necessary setup is created. If any additional feature is needed, please kindly modify the related part in ARM/bicep template or REST API request payload.
The pool created in this blog contains the following properties:
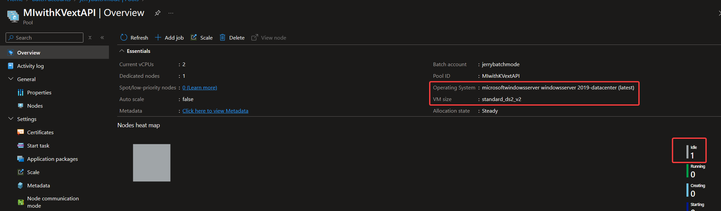
- OS: Windows Server 2019 Datacenter with latest version
- Node Agent: batch.node.windows amd64
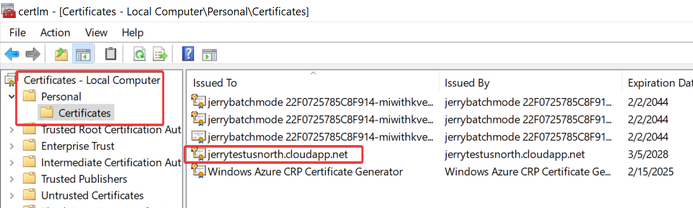
- Key Vault extension version 3.0: Install one certificate with thumbprint FDBB….F3A0 into LocalMachine/My certificate store
- Scale: 1 fixed dedicated node
- VM SKU: standard_ds2_v2
The expected result:
Created pool’s node can be in a healthy status:
And if we RDP into the node, we should be able to see the expected certificate saved into LocalMachine/My path:
Sample REST API call: (The parts in red need to be replaced by own resource information)
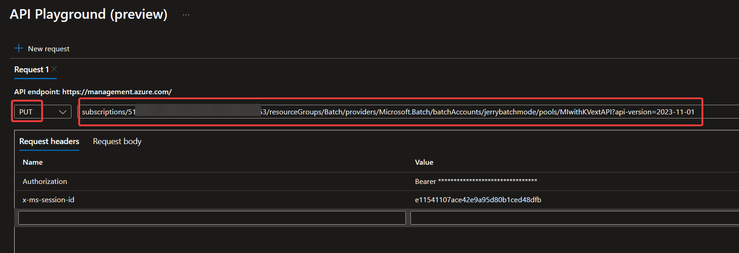
HTTP method: PUT
URL: https://management.azure.com/subscriptions/{subscription ID}/resourceGroups/{resource group name}/providers/Microsoft.Batch/batchAccounts/{batch account name}/pools/{pool name}?api-version=2023-11-01
Request headers: Authorization header with Microsoft Entra ID authentication Bearer token is required. Please refer to this document, or just simply search for API Playground in Azure Portal. The second way is easier because it will automatically generate the Authorization header.
Request body:
{
"identity": {
"type": "UserAssigned",
"userAssignedIdentities": {
"/subscriptions/5102xxxx-xxxx-xxxx-xxxx-xxxxa4473453/resourceGroups/Batch/providers/Microsoft.ManagedIdentity/userAssignedIdentities/usedbybatch": {}
}
},
"properties": {
"vmSize": "STANDARD_DS2_V2",
"deploymentConfiguration": {
"virtualMachineConfiguration": {
"imageReference": {
"publisher": "microsoftwindowsserver",
"offer": "windowsserver",
"sku": "2019-datacenter",
"version": "latest"
},
"nodeAgentSkuId": "batch.node.windows amd64",
"extensions": [
{
"name": "KeyVaultExtension",
"type": "KeyVaultForWindows",
"publisher": "Microsoft.Azure.KeyVault",
"typeHandlerVersion": "3.0",
"autoUpgradeMinorVersion": true,
"enableAutomaticUpgrade": true,
"settings": {
"secretsManagementSettings": {
"pollingIntervalInS": "300",
"linkOnRenewal": true,
"requireInitialSync": true,
"observedCertificates": [
{
"url": "https://batchusermode.vault.azure.net/secrets/classiccs ",
"certificateStoreName": "My",
"certificateStoreLocation": "LocalMachine",
"accounts": ["Network Service", "Local Service"],
"keyExportable": true
}
]
},
"authenticationSettings": {
"msiEndpoint": "http://169.254.169.254/metadata/identity/oauth2/token",
"msiClientId": "58eaxxxx-xxxx-xxxx-xxxx-xxxxf2d41227"
}
}
}
]
}
},
"scaleSettings": {
"fixedScale": {
"targetDedicatedNodes": 1,
"targetLowPriorityNodes": 0
}
}
}
}
Sample ARM template: (The parts in red need to be replaced by own resource information.)
Attention! According to the ARM template rule, to deploy a Batch pool which is child resource type, we must give the Batch Account name in the name property as well. The name here should be {BatchAccountName}/{PoolName}.
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {},
"resources": [
{
"name": "jerrybatchmode/MIwithKVextARM",
"apiVersion": "2023-11-01",
"type": "Microsoft.Batch/batchAccounts/pools",
"identity": {
"type": "UserAssigned",
"userAssignedIdentities": {
"/subscriptions/5102xxxx-xxxx-xxxx-xxxx-xxxxa4473453/resourceGroups/Batch/providers/Microsoft.ManagedIdentity/userAssignedIdentities/usedbybatch": {}
}
},
"properties": {
"vmSize": "STANDARD_DS2_V2",
"deploymentConfiguration": {
"virtualMachineConfiguration": {
"imageReference": {
"publisher": "microsoftwindowsserver",
"offer": "windowsserver",
"sku": "2019-datacenter",
"version": "latest"
},
"nodeAgentSkuId": "batch.node.windows amd64",
"extensions": [
{
"name": "KeyVaultExtension",
"type": "KeyVaultForWindows",
"publisher": "Microsoft.Azure.KeyVault",
"typeHandlerVersion": "3.0",
"autoUpgradeMinorVersion": true,
"enableAutomaticUpgrade": true,
"settings": {
"secretsManagementSettings": {
"pollingIntervalInS": "300",
"linkOnRenewal": true,
"requireInitialSync": true,
"observedCertificates": [
{
"url": "https://batchusermode.vault.azure.net/secrets/classiccs ",
"certificateStoreName": "My",
"certificateStoreLocation": "LocalMachine",
"accounts": [ Network Service", Local Service" ],
"keyExportable": true
}
]
},
"authenticationSettings": {
"msiEndpoint": "http://169.254.169.254/metadata/identity/oauth2/token",
"msiClientId": "58eaxxxx-xxxx-xxxx-xxxx-xxxxf2d41227"
}
}
}
]
}
},
"scaleSettings": {
"fixedScale": {
"targetDedicatedNodes": 1,
"targetLowPriorityNodes": 0
}
}
}
}
]
}