Enhancing Your Azure Security: Azure DDoS Sentinel Solution and WAF Playbook Integration

Introduction
In today's digital landscape, the rise of complex cyber threats poses a significant challenge for businesses relying on cloud-based services. Specifically, Distributed Denial of Service (DDoS) attacks are now often being used as a diversion in multi-layer attacks. To safeguard their applications and ensure uninterrupted service availability, organizations must deploy robust security solutions. Microsoft Azure offers powerful security solutions - Azure DDoS Protection, Azure Web Application Firewall (WAF) and Microsoft Sentinel - to help you proactively defend your assets against such attacks.
In this blog, we will explore how to integrate the Azure DDoS Sentinel Solution with the Azure WAF Playbook to enable a powerful automated detection and response system. By combining these two solutions, you can ensure a secure and uninterrupted experience for users, protect your services, and minimize the risk of DDoS attacks.
Prerequisites
Before proceeding with the integration of the Azure DDoS Sentinel Solution and the Azure WAF Playbook, ensure you have the following prerequisites in place:
- Azure DDoS Protection Plan protecting your public resources. To configure and deploy Azure DDoS Protection, you can refer to these links:
- Diagnostic logging - Enabled on the protected public resource and sending logs to a Log Analytics Workspace. You can refer to this article on how to configure the diagnostic logging - Configure Azure DDoS Protection diagnostic logging through portal | Microsoft Learn
- Microsoft Sentinel Workspace which is linked to a Log Analytics Workspace created in step (2) above.
- Web Application Firewall policy installed in an Application Gateway or Front Door instance. You can refer to the links below on how to create a WAF policy in Application Gateway or Azure Front Door.
With these prerequisites in place, we now take the Azure DDoS Sentinel Solution and the WAF Playbook to create an automated system that prevents DDoS attacks and further blocks the attacker IP addresses within a custom WAF rule.
Integrating Azure DDoS Sentinel Solution with the WAF Playbook
DDoS attacks often serve as a cover for concealing more sophisticated attack vectors such as exfiltration of confidential data. Manually correlating the IPs from DDoS attacks with these advanced threats can be demanding and time intensive. However, by harnessing the combined power of the Azure DDoS Sentinel Solution and the Azure WAF Playbook, you obtain a simplified process of detecting, responding to, and preventing such attacks.
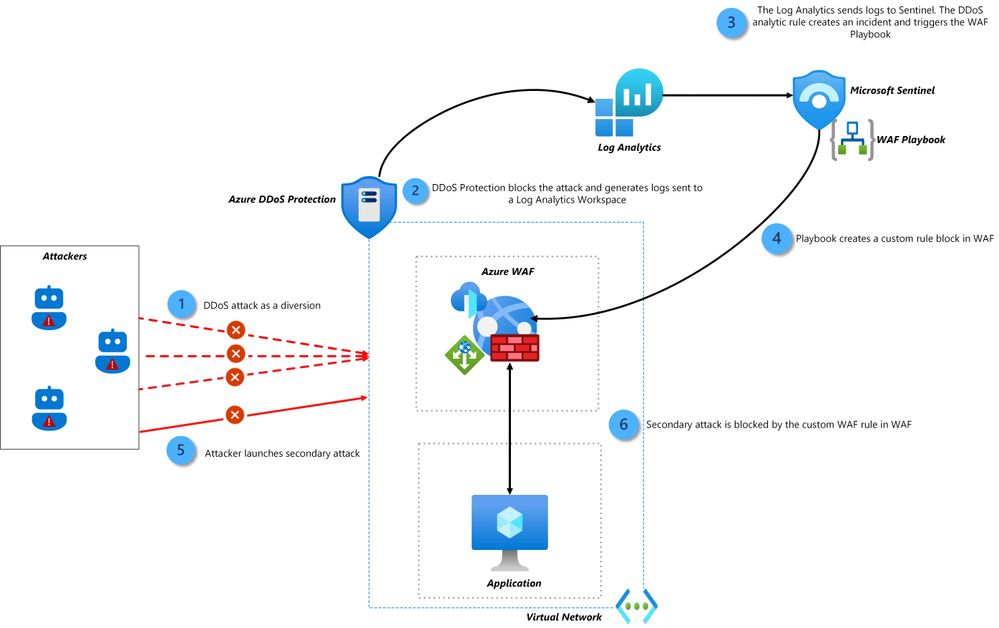
The integration of the Azure DDoS Sentinel Solution and WAF Playbook works following these main steps:
- Azure DDoS Protection is deployed to protect Azure resources. Azure DDoS Protection continuously monitors the targeted resources for DDoS attacks and blocks the attacks.
- Logging is enabled in the diagnostic settings of the protected resource.
- The Azure DDoS Sentinel Solution is installed. The Azure DDoS Sentinel Solution has analytic rules that identify the DDoS attack IP addresses and create an incident.
- Azure Web Application Firewall policy is deployed in an Application Gateway or Front Door instance.
- The WAF Playbook is deployed to modify a custom rule in the WAF Policy to block the attacker IP addresses.
- An automation rule is deployed to run the WAF Playbook whenever an incident is created by the DDoS analytic rules.
With this integration, the Azure DDoS Sentinel Solution and the WAF Playbook work together to prevent attacks with the steps described below:
- During the first stage of a multi-vector attack campaign, initiated by a malicious actor, the DDoS attack floods the customer’s application, creating chaos and serving as a diversion for the subsequent attack.
- Upon identifying the DDoS attack, Azure DDoS protection mitigates the attack and generates logs that are transmitted to Microsoft Sentinel.
- Microsoft Sentinel extracts the source IP addresses of the attackers from the logs and triggers the WAF Playbook.
- The WAF Playbook adds the attack IP addresses to a custom WAF rule with a block action. Azure WAF becomes ready to mitigate the forthcoming stages of the adversary's attack cycle.
- Having employed the DDoS attack as a smokescreen, the adversary now attempts to breach the application to take the sensitive data.
- Azure WAF acts by blocking access from the source IP addresses of the attacker, thereby preventing them from reaching the data.
Azure DDoS Sentinel Solution Configuration and Deployment
The Azure DDoS Solution for Microsoft Sentinel involves integrating Azure DDoS Protection with Sentinel for easy ingestion of protection logs. This integration facilitates the analysis of the data in workbooks, the ability to formulate customized alerts, and the incorporation of the data to enhance investigative procedures, thereby providing heightened visibility into platform security.
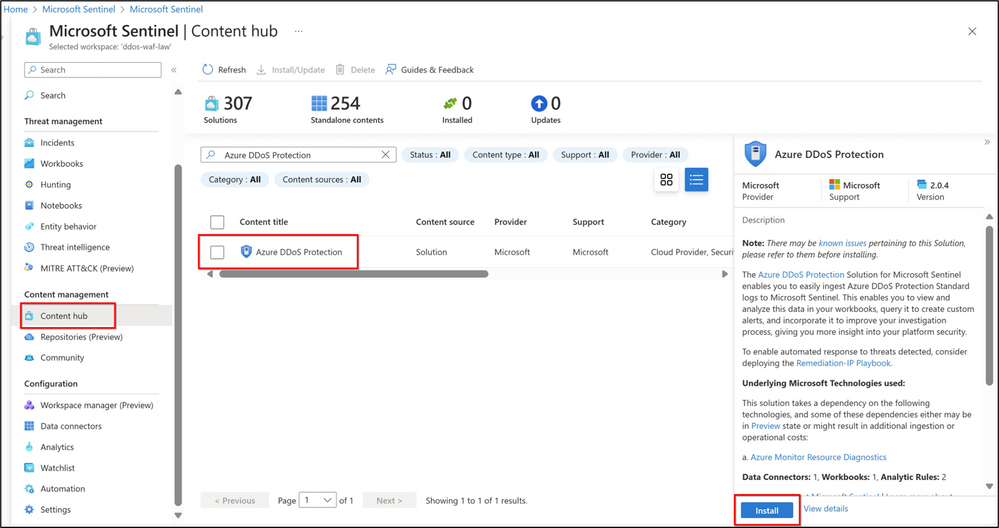
This solution can be installed from the Azure marketplace - https://azuremarketplace.microsoft.com/en-us/marketplace/apps/azuresentinel.azure-sentinel-solution-azureddosprotection?exp=ubp8&tab=Overview or directly from Microsoft Sentinel by navigating to the Content Hub and searching for “Azure DDoS Protection”.
In our scenario, we deploy the solution from Sentinel. Navigate to Content management and select Content Hub. Search for Azure DDoS Protection and select Install to begin the deployment.
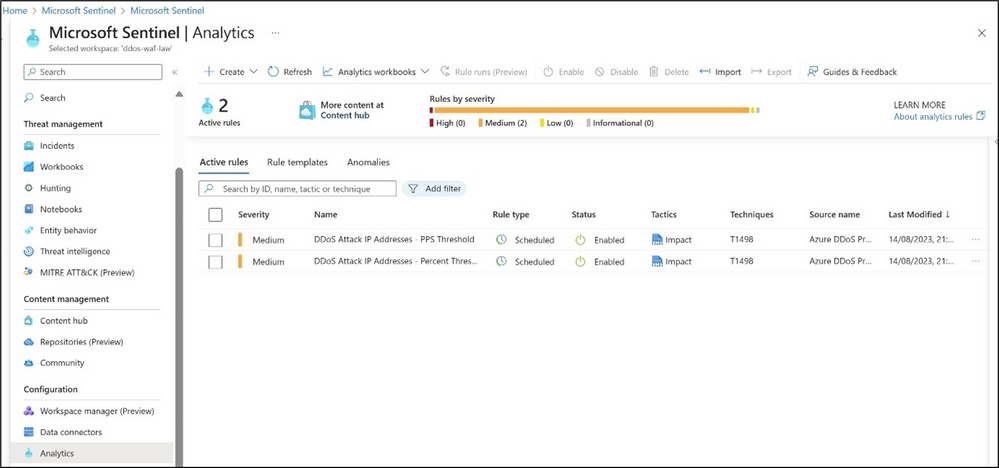
Once the Solution is installed, the two main analytic rules appear in your Microsoft Sentinel Workspace under Analytics:
The two analytic rules are:
- DDoS Attack IP Addresses - PPS Threshold: Identifies IP addresses that generates maximal traffic rate over 10,000 PPS during DDoS attack mitigation.
- DDoS Attack IP Addresses - Percent Threshold: Identifies IP addresses that generate over 5% of traffic during DDoS attack mitigation.
To complete the solution setup, it is essential to configure the analytic rules. This configuration process also encompasses establishing the query scheduling, which can be adjusted according to your preferences. For detailed instructions on configuring the analytic rules, refer to the New Azure DDoS Solution for Microsoft Sentinel blog.
Azure WAF Playbook Configuration and Deployment
The Azure WAF Sentinel Playbook adds the source IP address passed from a Sentinel incident to a custom WAF rule, blocking the IP. The Playbook supports Application Gateway WAF policies as well as WAF policies for Front Door Standard and Front Door Premium.
The older WAF Playbook has been updated to concurrently add multiple IP addresses to the WAF custom rule and eliminate duplicate IP addresses in the rule by checking if the IP address is already in the rule.
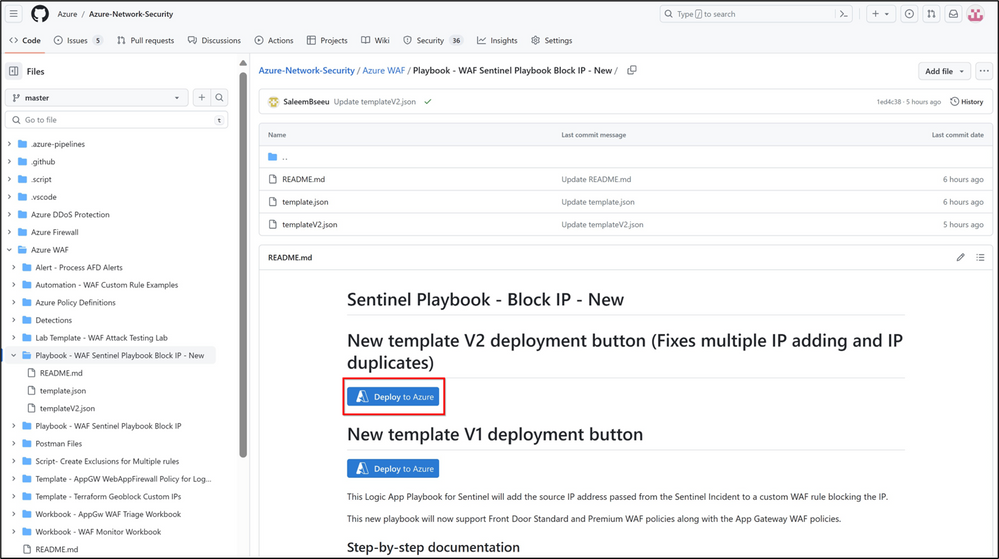
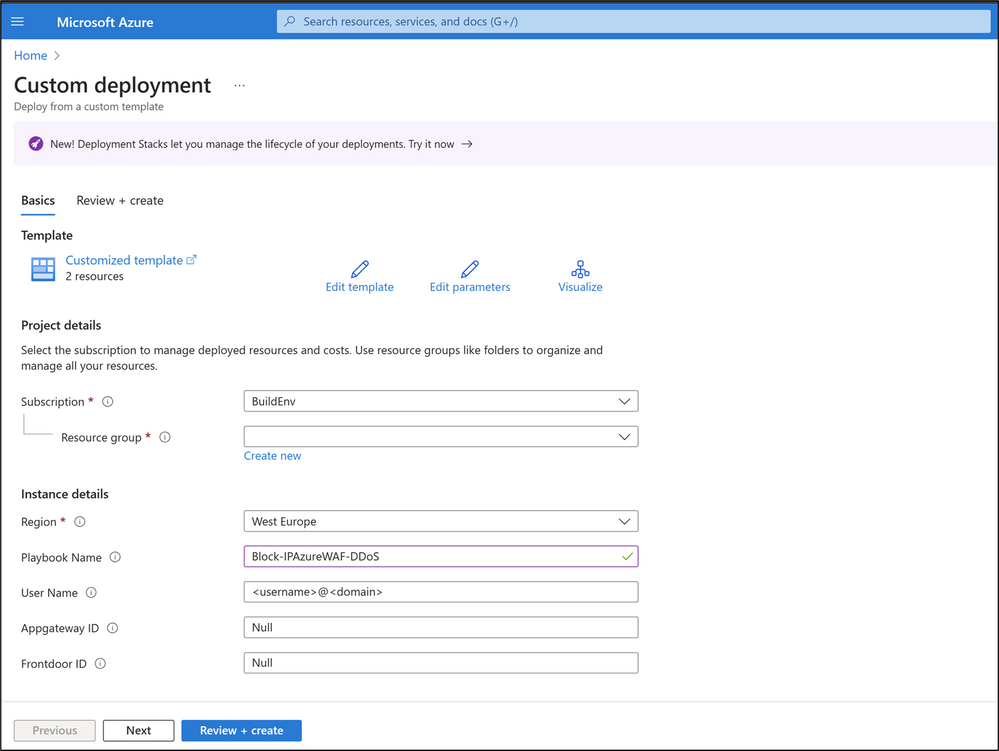
To deploy the Playbook, navigate to Azure-Network-Security/Azure WAF/Playbook - WAF Sentinel Playbook Block IP - New at master · Azure/Azure-Network-Security. On the page, click on “Deploy to Azure” (v2 Deployment button) and begin the installation process.
The following fields will be displayed on the new Azure portal page:
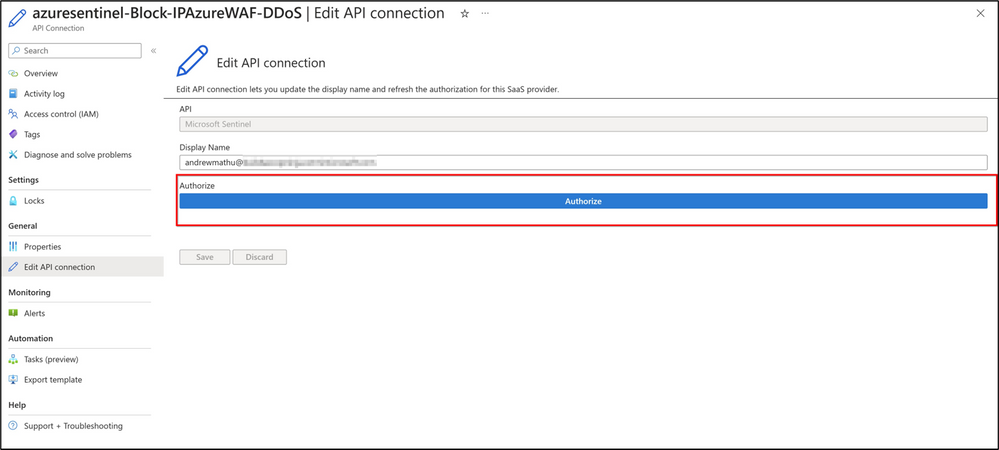
Fill in the details and proceed to deploy the template. Once the Playbook is deployed, the next step is to authorize the API connection created as part of the deployment. Navigate to the resource group specified during the Playbook creation and select the API connection. Inside the API connection, navigate to Edit API connection and click on Authorize. Ensure to authenticate against Azure AD.
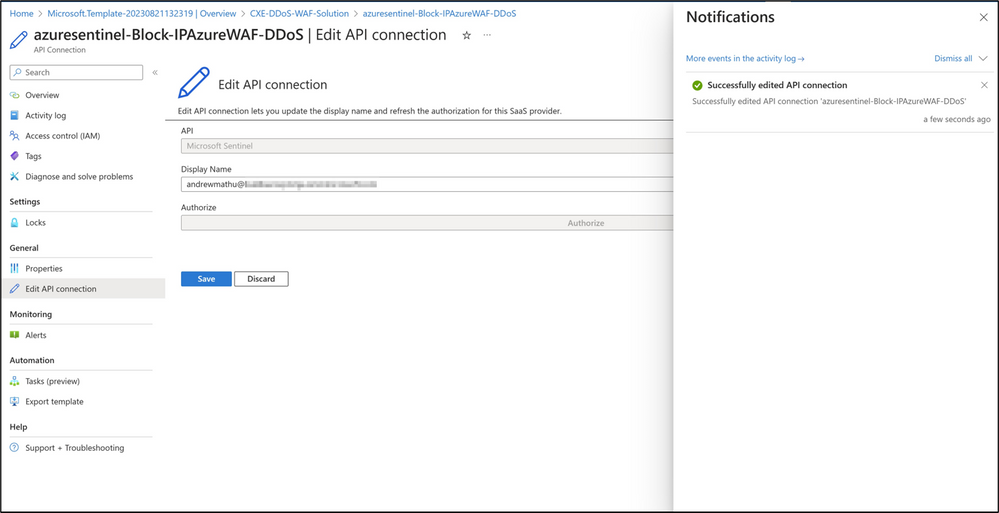
Once authorized, save the changes. You will receive a notification that the API connection has been successfully edited.
To finalize the Playbook setup, along with their respective WAF policies. This will ensure that the Playbook has the necessary authorizations to query and modify the existing WAF policy via the REST API. To assign this managed identity, navigate to:
- Application Gateway/Front Door instance.
- Select Access Control (IAM).
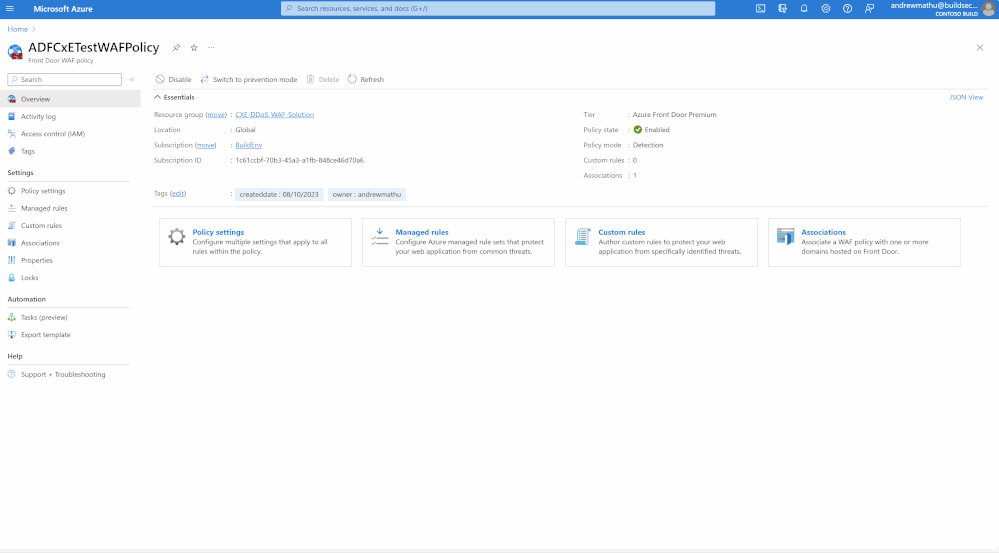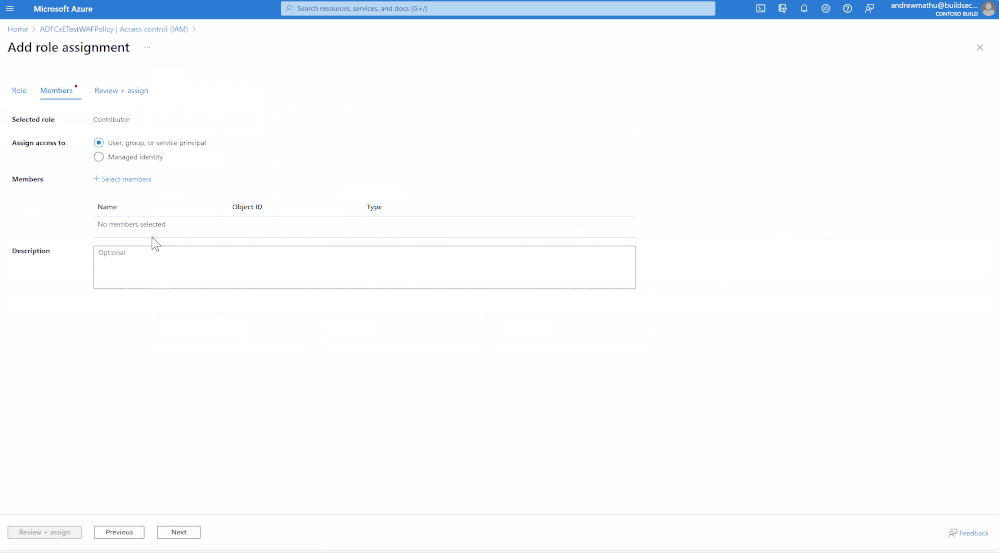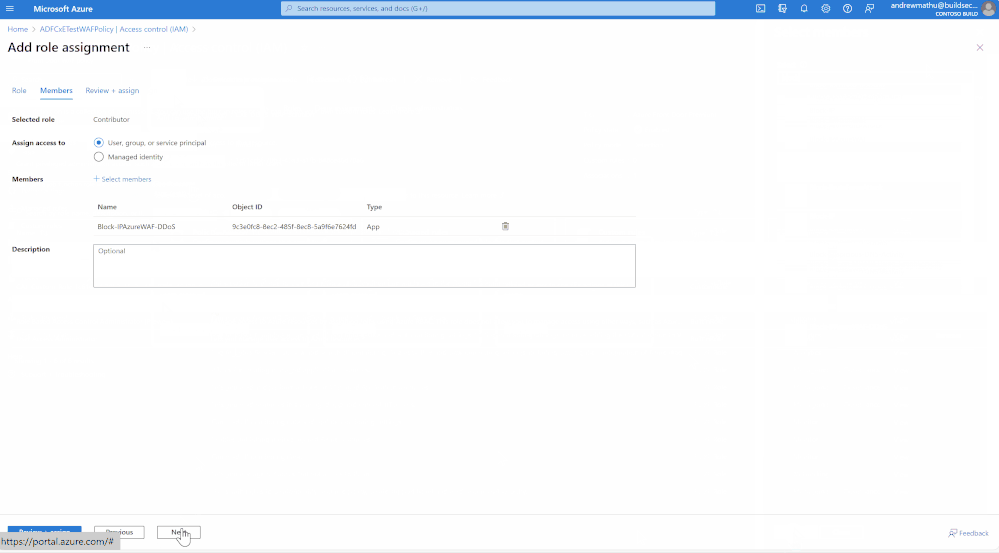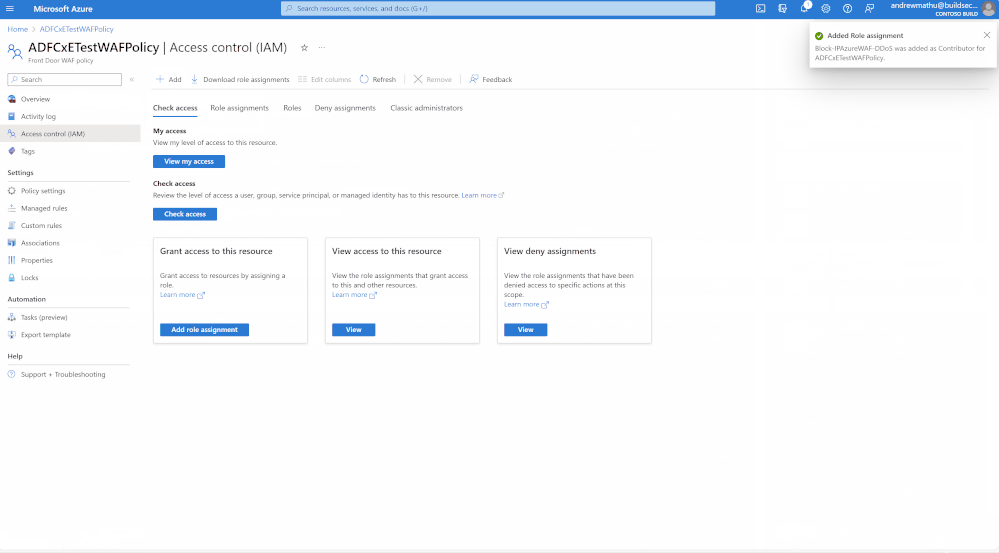
- Click on Add – then select - Add role assignment.
- In the new page:
- Select Contributor under Privileged administrator roles.
- Under the Members tab, in Assign access to, select User, group, or service principal.
- Click on +Select Members in the Members section.
- On the side page that appears, select the WAF Logic app created in the deployment.
- Complete the assignment by selecting Next and then Review + Assign.
- Repeat the above steps for your WAF policy in Application Gateway or Front Door.
For further details on the WAF Playbook deployment and setup you can also refer to the blog - Automated Detection and Response for Azure WAF with Sentinel.
Automation
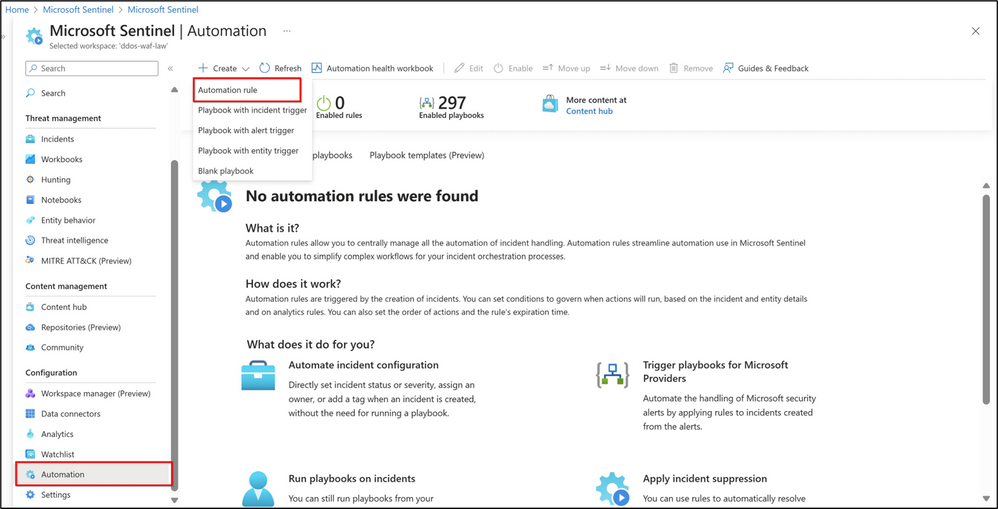
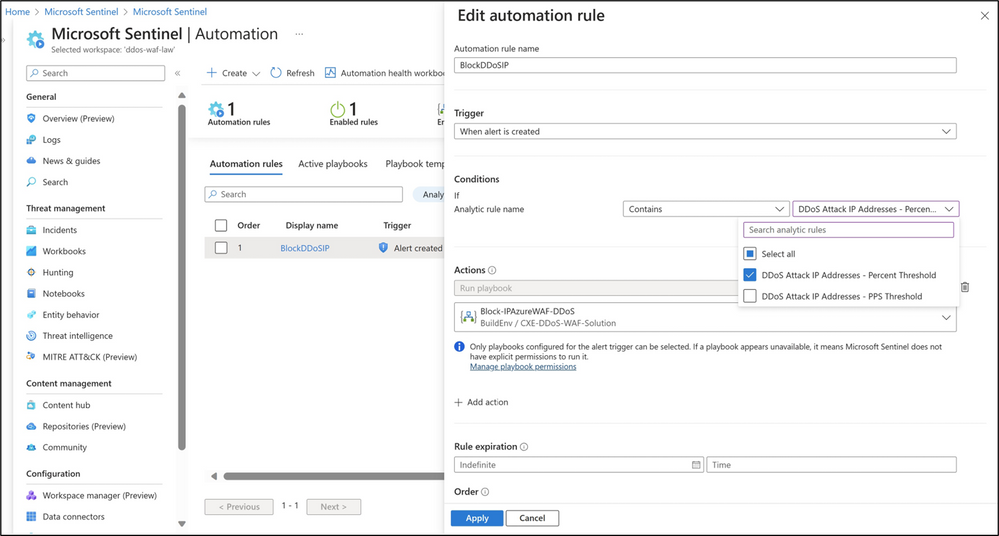
The concluding step is to bring the two solutions together through the creation of an automation rule. In the Microsoft Sentinel workspace, navigate to Automation and select Create and then Automation Rule.
In the Create new automation rule page:
- Provide a name for the automation rule.
- Under trigger, select When alert is created.
- In the Conditions section, select the analytic rule(s) previously configured.
- Under Actions, select Run Playbook and select the WAF Playbook deployed.
- Lastly, click on Apply, to save and deploy the automation rule.
The Integration is now complete and ready to defend your environment.
Simulating a DDoS Attack
To test the solution against a DDoS attack, you can use one of the approved testing partners found in - Azure DDoS Protection simulation testing. You can also check out this blog - Strengthening Your Defenses: Simulation Testing for Azure DDoS Protection - Microsoft Community Hub – for in-depth details and a step-by-step guide of Azure DDoS simulation testing. Carrying out the simulation will validate that the solution works and provide a proactive means of ensuring that your services and applications maintain their anticipated functionality in the event of an attack.
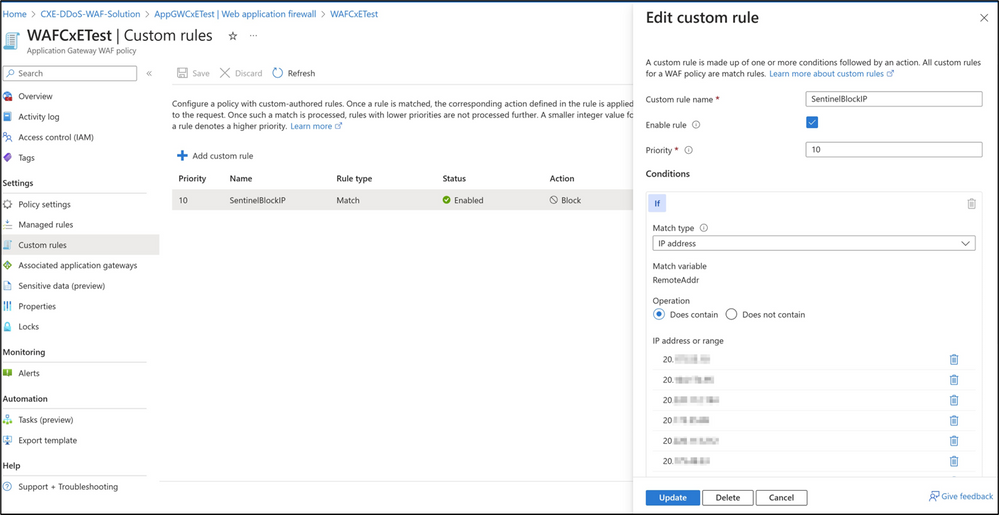
With the integration having been successfully deployed, and a DDoS simulation attack conducted, we can see the attacker IPs added to a WAF custom rule called “SentinelBlockIP” as displayed below:
Conclusion
With the integration of the Azure DDoS Sentinel Solution and the Azure WAF Playbook, you establish a strong defense against advanced cyberattacks, mitigating the risk of service disruptions and maintaining a secure environment. The automated detection and response process allows security teams to focus on proactive measures, ensuring that their applications and services remain protected from the ever-evolving cyber threats.
Resources
- Azure DDoS Protection Overview - Azure DDoS Protection Overview | Microsoft Learn.
- Create and configure Azure DDoS IP Protection using Azure portal - QuickStart: Create and configure Azure DDoS IP Protection - Azure portal | Microsoft Learn.
- Create and configure Azure DDoS Network Protection using the Azure portal - QuickStart: Create and configure Azure DDoS Network Protection using - Azure portal | Microsoft Learn.
- Azure DDoS Simulation testing - Azure DDoS Protection simulation testing | Microsoft Learn.
- Azure Web Application Firewall Overview - Introduction to Azure Web Application Firewall | Microsoft Learn.
- Azure Web Application Firewall on Application Gateway – What is Azure Web Application Firewall on Azure Application Gateway? - Azure Web Application Firewall | Microsoft Learn.
- Azure Web Application Firewall on Azure Front Door - Web Application Firewall on Azure Front Door | Microsoft Learn.
- Microsoft Sentinel - What is Microsoft Sentinel? | Microsoft Learn.
Published on:
Learn moreRelated posts
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...
General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB
Title: General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB We’re excited to announce the general availability of the ...
Efficiently and Elegantly Modeling Embeddings in Azure SQL and SQL Server
Storing and querying text embeddings in a database it might seem challenging, but with the right schema design, it’s not only possible, ...