Terraform integration with Azure VMware Solution

By: Juan Manuel Rey (Microsoft) and Eric Schwindt (HashiCorp)
Azure VMware Solution is a VMware validated first party Azure service from Microsoft that provides private clouds containing vSphere clusters built from dedicated bare-metal Azure infrastructure. It enables customers to leverage their existing investments in VMware skills and tools, allowing them to focus on developing and running their VMware-based workloads on Azure.
Hashicorp Terraform is an open-source tool for provisioning and managing cloud infrastructure. It allows administrators and DevOps engineers to codify infrastructure in configuration files describing the topology of cloud resources.
Many of Azure and VMware customers are currently using Terraform to deploy and manage their Azure and VMware resources; with that in mind and since Azure VMware Solution is a first party service the Terraform Azure Provider has been updated to include functionality that will enable administrators to deploy and manage Azure VMware Solution private clouds.
In its current state the provider allows to create and destroy an Azure VMware Solution private cloud and some limited day-2 and operations like enabling internet access for the workloads and scale up and down the cluster. In this article we will go into the details.
Prerequisites
You will need to have a valid Azure subscription with quota enabled for Azure VMware Solution, review the procedure here. Review Terraform on Azure documentation to get your environment ready for the deployment. Finally use Terraform Azure Provider of at least version 2.69.0.
Private cloud deployment
We will create a Terraform plan with three main files.
- main.tf
- variables.tf
- avs-sddc.tf
With these three manifests there will be enough to deploy a new private cloud.
- variables.tf
In the variables.tf manifest we will declare prefix and location variable.
- main.tf
As in any other Azure Terraform plan this manifest will contain the resource group where we will deploy the different Azure resources and the information about the provider version.
- avs-sddc.tf
Finally in the avs-sddc.tf file we will declare the private cloud, including the SKU and te configuration for the management cluster.
Once all three files have been created run terraform plan -out rg-test.tfplan to generate the plan and terraform apply "rg-test.tfplan to execute the plan and deploy the SDDC.
Day-2 operations and lifecycle management
As mentioned at the begining in this version of the Azure Provider the only supported Day-2 operations are scaling up or down the clusters and enabling internet access operations are supported. However both operations cannot be executed at the same time.
First we will enable internet access for the VMware workloads running in the private cloud.
Edit avs-sddc.tf manifest and add the internet_connection_enabled parameter after the management cluster size as shown in the example.
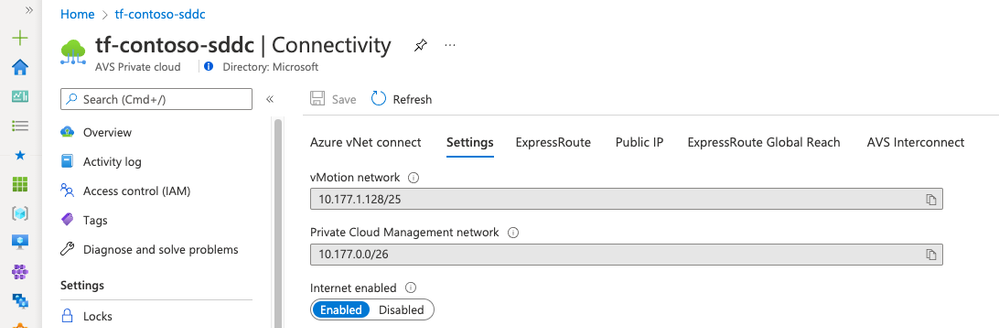
Save the manifest, regenerate the Terraform plan and apply it with terraform apply "tf-contoso.tfplan". The operation will take around 10 minutes to be completed. You can verify and monitor the execution in the Azure portal, access your Azure VMware Solution private cloud resource and go to Manage->Connectivity->Settings.
To scale the cluster we will edit the same avs-sddc.tf manifest and change the cluster size from 3 to 4.
Save the manifest regenerate and apply the plan. The scale up operation will take about 30 to 45 minutes to complete.
With the Azure VMware Solution private cloud up and ready the Terraform provider for Azure can be used to deploy a VNET, a jumpbox virtual machine and an Azure Bastion service to access and manage the private cloud using common VMware vSphere tools. Equally an administrator can leverage the VMware vSphere and NSX-T Terraform providers to deploy workloads and configure resources in their private clouds.
Following are a few resources to learn more about Azure VMware Solution.
Learn Azure VMware Solution Networking
Try Azure VMware Solution Hands-on-lab
Authors:
Juan Manuel Rey - Senior Program Manager, Azure VMware Solution product group at Microsoft
Eric Schwindt - Director, Partner Alliances at HashiCorp
Published on:
Learn moreRelated posts
Azure Developer CLI (azd): One command to swap Azure App Service slots
The new azd appservice swap command makes deployment slot swaps fast and intuitive. The post Azure Developer CLI (azd): One command to swap Az...