Ignite news: XDR in an era of end-user-to-cloud cyberattacks and securing the use of AI

Cyber criminals are continuously evolving their tactics, and as trends shift, it’s critical that defenders have solutions that are adapting alongside new cyberattack patterns and security risks. As cloud adoption continues to soar, Microsoft’s security researchers are seeing an increasing trend of attackers crossing the lines from end-user assets into cloud workloads. In just one class of cyberattacks observed by Microsoft over the last few months, targeted organizations incurred more than $300,000 in fees due to cryptojacking.
Separately, Generative AI is introducing opportunities and challenges for security teams. While the rapid adoption and the influx of available apps using LLM is turning into growing concerns around lack of oversight and associated security risks by security leaders, AI can also act as a means for defenders to gain ground against attackers by processing signal faster and disrupting cyberattacks early.
We that in mind we have three exciting announcements to address these challenges:
- End-user-to-cloud XDR: Multicloud alerts, signals, and asset information for Azure, AWS, and GCP from Microsoft Defender for Cloud are now natively integrated into Microsoft Defender XDR, the new name for Microsoft 365 Defender.
- Securing the use of Generative AI apps: Microsoft Defender for Cloud Apps now discovers 400+ AI apps, provides a risk assessment, and lets you control the use in your organization.
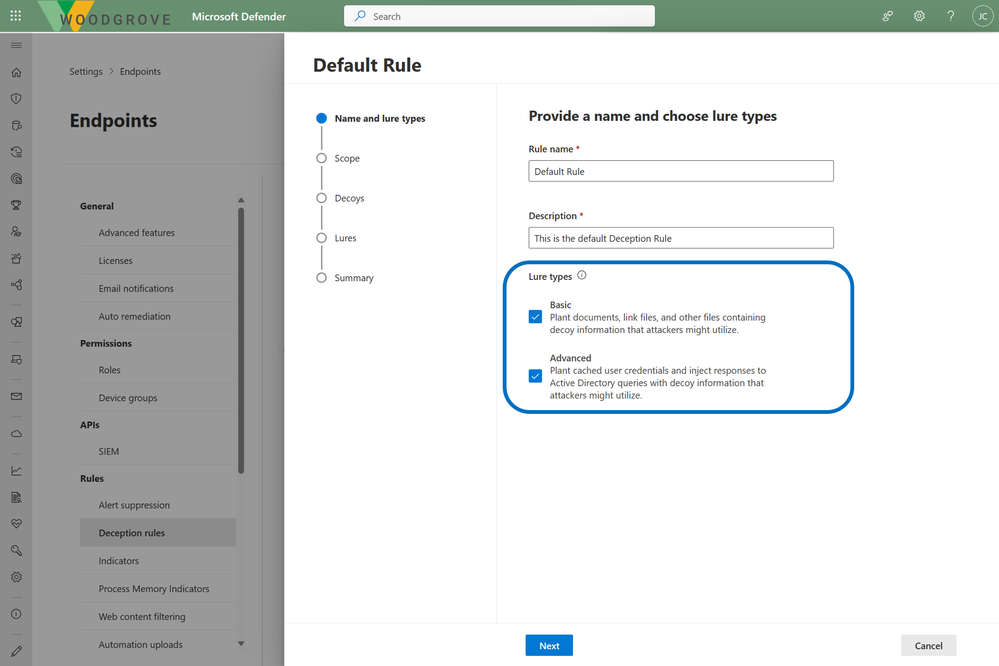
- Deception in Defender for Endpoint: Built-in deception capabilities can now automatically generate and deploy authentic deception decoys and lures built on Open AI’s ChatGPT 4.0 model.
Native end-user-to-cloud XDR
Microsoft’s most recent research revealed that 76% of cloud incidents originated from identity-related compromise, while approximately 60% of incidents identified by Microsoft Defender for Cloud included compromise across email, SaaS apps, or endpoints. This data shows a direct correlation between cyberattacks crossing the boundaries between end user assets into cloud and hybrid workloads.
To effectively stop and prevent the increasing number of cross-domain cyberattacks like infrastructure as a service (IaaS) resource theft, SOC teams need visibility and alert correlation across end-user assets including identity, endpoint, SaaS apps and their cloud workloads. Today we are pleased to announce that we are integrating cloud workload alerts, signals, and asset information from Microsoft Defender Cloud into Microsoft Defender XDR. This integration now removes any infrastructure blind spots in an organization’s digital landscape.
As part of this integration, we are rolling out new correlations and content tailored to cross-workload correlations and cloud-specific content, giving you a richer, more contextual understanding of the threats, your organization faces.
Instant enablement and seamless integration
For existing Microsoft Defender for Cloud customers, the integration will be automatically enabled, and you will see the new insights appear in your assets, alerts, and incidents in the Defender portal. In addition, you will be able to easily pivot from incident experience into the Defender for Cloud portal to take actions against any of your cloud or hybrid resources.
Unified API and third-party SIEM support
The integration also extends to our API. Alerts and incidents from Defender for Cloud are now integrated into the Microsoft Defender XDR public API, enabling seamless export of security alerts data into your preferred systems. Not only does this offer a unified API experience, but it also provides comprehensive support for third-party SIEM solutions. Organizations with existing investments can continue using them while still benefiting from the robust capabilities of this integration.
Investigate cryptojacking in Microsoft Defender XDR
Let’s look at an example. Cryptojacking is a type of IaaS resource theft that involves using computing power to mine cryptocurrency. It often takes the form of abusing cloud computing resources, where threat actors compromise legitimate cloud tenants. This kind of resource abuse could result in financial loss due to computer fees incurred.
Compromised user accounts are the most common entry point. Threat actors target user accounts with high-level privileges and use them to steal cloud resources. For instance, they might spin up virtual machines to mine cryptocurrency at the expense of the compromised organization, as illustrated in Figure 1.
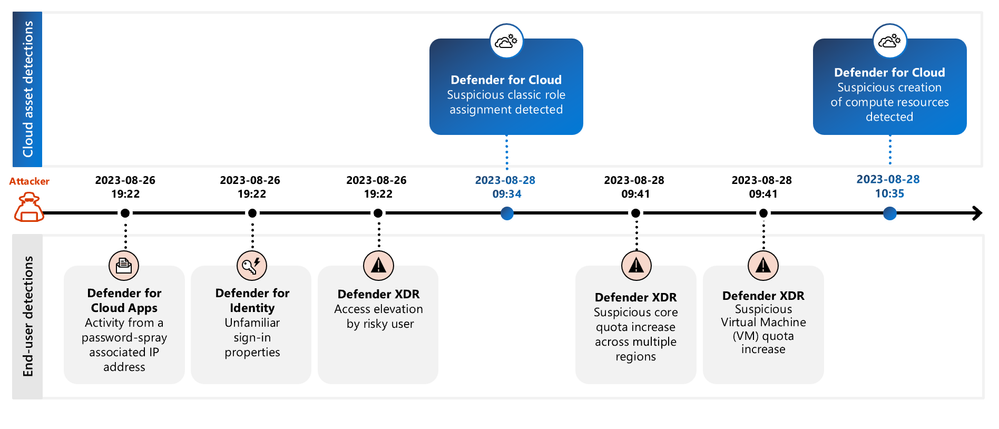
In the Defender portal, SOC analysts can now run end-to-end investigations if they’re faced with this type of cyberattack. They can monitor, triage, and investigate multicloud alerts across Azure, AWS, and GCP. This end-to-end prioritization of information and alerts streamlines the investigation process and greatly improves SOC efficiency. Figure 2 shows an incident that contains compromised user accounts, devices, as well as cloud-based storage.
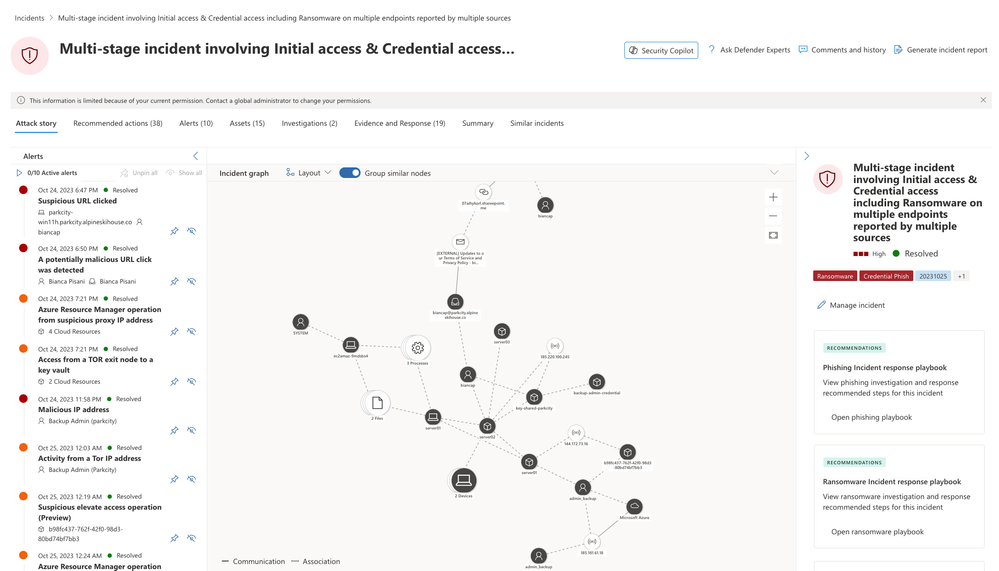
We can see that this incident is composed of alerts generated by our XDR stack from multiple sources, including Microsoft Defender XDR, Microsoft Defender for Endpoint, Cloud Apps, Office 365, Identity, and Cloud. These alerts are correlated via the XDR’s advanced correlation engine for you – no manual work needed.
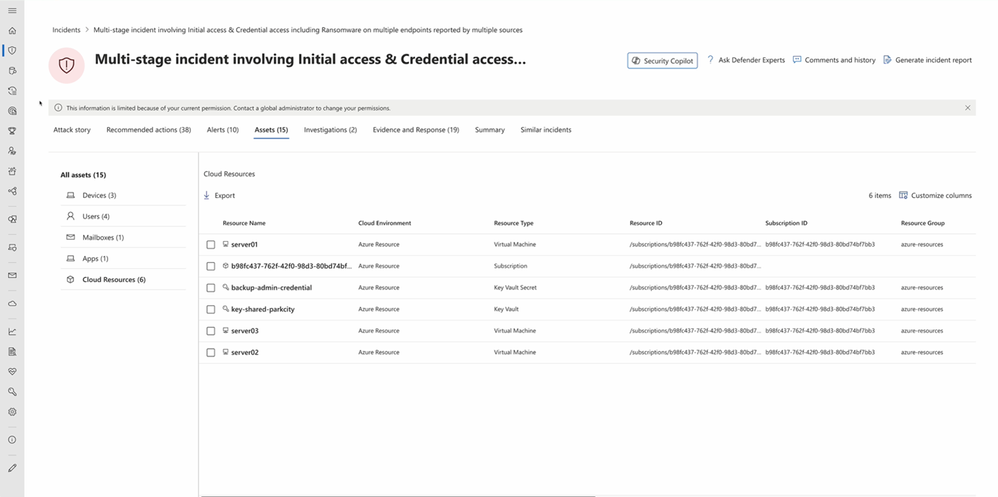
The scope of assets impacted by this incident extends to a list of cloud resources obtained through the insights provided by Microsoft Defender for Cloud as shown in Figure 3. These cloud resources include critical components like virtual machines, and Azure subscriptions. As you can see from this incident, Microsoft Defender for Cloud insights can help the SOC analysts gain holistic visibility across their heterogeneous environment and improve the efficiency for their daily security operations.
With the incorporation of cloud signals into Microsoft’s XDR platform, we have renamed Microsoft 365 Defender to Microsoft Defender XDR to best represent Microsoft’s XDR capabilities that broadly span multiplatform and multicloud assets.
Securing the use of Generative AI apps
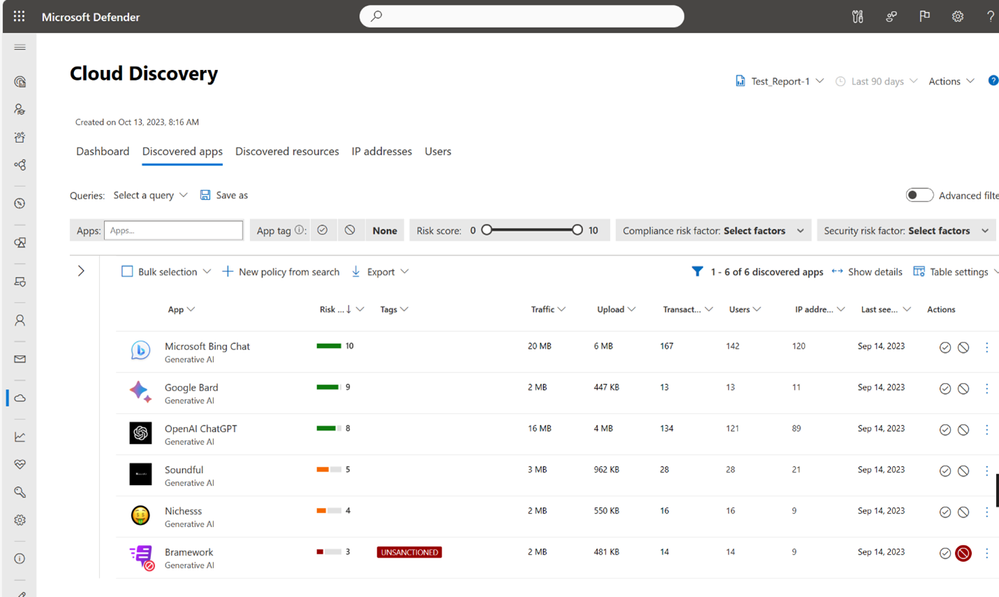
The rapid adoption of Generative AI apps has completely disrupted the way employees work today. As more Generative AI services are introduced in the market, there are growing security concerns over the risks that they pose. 58% of organizations are concerned over the lack of visibility into the unsanctioned use of Generative AI. Another challenge is securing the data that is exchanged between the user and app both from the input and output perspective. Today, we are excited to announce new security capabilities across Microsoft Defender for Cloud Apps and Microsoft Purview to help companies secure the use of Generative AI. Within Defender for Cloud Apps, we’ve extended our rich discovery capabilities to over 400 generative AI apps. This means that customers can now gain visibility into their use, understand their risk, and apply controls such as approving or blocking an app (see Figure 4). To learn more about the new Microsoft Purview features, read the latest announcement blog.
Augment your EDR and XDR with deception tactics to catch adversaries early
Endpoints remain critical entryways for adversaries to begin their reconnaissance before moving laterally through an organization. That’s why endpoint visibility is critical to any XDR solution. Today we are excited to announce deception as an embedded capability in Microsoft Defender for Endpoint, making these capabilities easily accessible. Augmenting its powerful endpoint detection and response capabilities, with built-in deception capabilities you can now auto-generate and deploy authentic decoys and lures such as users, hosts, documents and more. As adversaries interact with any deception asset, it triggers high-fidelity, early-stage signal for the SOC and will also trigger automatic attack disruption – responding and shutting out attackers at machine speed. To learn more about deception, check out this announcement blog.
Microsoft Defender XDR is the broadest, native XDR that gives SOC teams deep visibility across the cyber kill chain. With the addition of cloud workload signals for even more visibility and detection of advanced attacks, the ability to respond at machine speed with deception and attack disruption, and the ability to understand and secure the use of LLM apps, defenders continue to gain ground against attackers.
Learn more:
- Learn more about deception in Defender for Endpoint in this blog.
- Find out how we’re helping organizations secure and govern the use of generative AI apps.
- Explore Microsoft Defender for Cloud
- To learn more about Microsoft Defender XDR, visit our website.
- Read our documentation to get started.