Announcing General Availability of Confidential VMs in Azure Virtual Desktop
Today we are announcing the General Availability of several confidential VM and Trusted Launch security features via AVD Host Pool Provisioning.
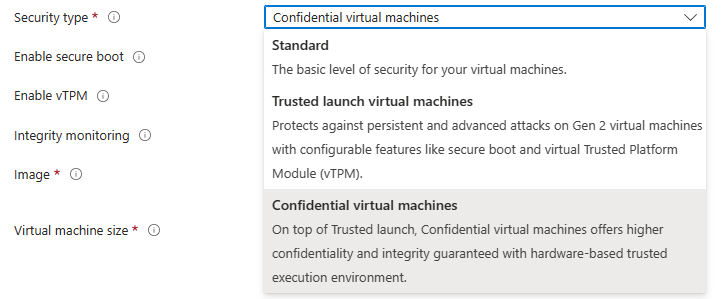
What are Confidential VMs?
The AMD Azure EPYC SEV-SNP DCasV5 and ECasv5-series confidential VM series provides a hardware-based Trusted Execution Environment (TEE) with attestation capability by leveraging AMD SEV-SNP security features. Azure confidential VMs (CVMs) offer VM memory encryption with integrity protection, which strengthens guest protections to deny the hypervisor and other host management components code access to the VM memory and state. For additional CVM security benefits, please see the CVM documentation for more information.
With this general availability, Windows 11 22H1 is now also supported in CVMs, adding to the list of already supported versions of 22H2 and other future versions of Windows 11. In addition, confidential OS Disk Encryption is available for confidential VMs, and Integrity monitoring is available during AVD Host Pool provisioning for both confidential VMs and Trusted Launch VMs.
Confidential disk encryption is an additional layer of encryption that binds the disk encryption keys to the VM’s TPM and makes the disk content accessible only to the VM. For more information about disk encryption, please visit FAQ - Azure Disk Encryption for Windows VMs - Azure Virtual Machines | Microsoft Learn.
Integrity monitoring allows cryptographic attestation and verification of VM boot integrity. It includes monitoring alerts for the VM booting because attestation failed with the defined baseline. For more information about integrity monitoring, please visit the Microsoft Defender for Cloud Integration section of Trusted Launch for Azure VMs documentation.
What is Trusted Launch?
Trusted Launch (TL) protects against advanced and persistent attack techniques. They allow for secure deployment of VMs with verified boot loaders, OS kernels, and drivers. In addition, they protect keys, certificates, and secrets in VMs. For more information about TL benefits, please see the Trusted Launch documentation.
Therefore, we are pleased to announce that Trusted Launch is now enabled by default for all Windows images.
How to deploy CVMs in AVD Host Pool Provisioning with these settings
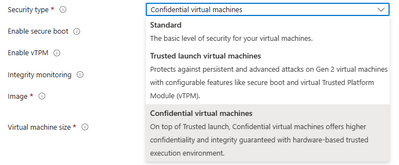
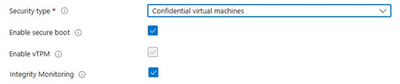
- Select Confidential Virtual Machines from the Security Type dropdown in the AVD Host Pool Virtual Machine blade.
- Once Security Type is set to Confidential Virtual Machines, you will see the option to select Integrity Monitoring.
- Select any CVM compatible Windows 11 images from the Image dropdown. Scroll to Confidential compute encryption and select it for enabling OS Disk Encryption for your CVM.
How Trusted Launch is enabled by default for non-Confidential Virtual Machines for any images.
By default, the Security type will automatically change to Trusted Virtual Machines. This was done to meet the mandatory hardware requirements of Windows 11. For further information about this requirement, please see this reference on Windows 11 requirements.
Getting Started
To get started, please visit Azure Virtual Desktop | Microsoft Azure to learn more about the various benefits AVD provides and to get started with your first deployment.
Visit Create a host pool - Azure Virtual Desktop | Microsoft Learn to start deploying your first confidential VM in Azure Virtual Desktop through the Azure Portal. For more information about any of these features, please visit Azure Virtual Desktop security best practices - Azure | Microsoft Learn.
Published on:
Learn moreRelated posts
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...
General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB
Title: General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB We’re excited to announce the general availability of the ...
Efficiently and Elegantly Modeling Embeddings in Azure SQL and SQL Server
Storing and querying text embeddings in a database it might seem challenging, but with the right schema design, it’s not only possible, ...