Strengthening Your Defenses: Simulation Testing for Azure DDoS Protection
Introduction
In the battle against Distributed Denial of Service (DDoS) attacks, it is crucial to have robust protection mechanisms in place. Azure DDoS Protection provides a powerful shield for your infrastructure, but how can you ensure it can handle real-world scenarios? This blog post walks you through DDoS simulation testing and its role in evaluating and enhancing Azure DDoS Protection. Discover how simulation testing can fortify your defenses and enable you to confidently withstand DDoS attacks.
Azure DDoS Protection Overview
Azure DDoS Protection is a comprehensive security solution offered by Microsoft Azure to protect applications and resources from Distributed Denial of Service (DDoS) attacks. DDoS attacks are attempts to overwhelm a target application or service by flooding it with a massive volume of malicious traffic, thereby rendering it unavailable to legitimate users. Azure DDoS Protection addresses these concerns by providing advanced mitigation capabilities and ensuring the availability of resources. Some of the key features are:
- Traffic Monitoring and Mitigation: Azure DDoS Protection continuously monitors incoming traffic patterns to identify potential DDoS attacks. Upon detection, it automatically triggers mitigation measures to ensure the application's availability.
- Adaptive Real-Time Tuning: The system intelligently profiles application traffic patterns over time and updates mitigation profiles accordingly. This adaptive approach ensures effective protection even as traffic evolves.
- Azure DDoS Rapid Response (DRR): During an active attack, customers can access the DDoS Rapid Response team for assistance with attack investigation and post-attack analysis.
Currently Azure offers two SKUs for DDoS protection: the first is Network protection which can be enabled on VNETs and is more ideal for larger enterprises that have a higher number of public IPs to protect. Network protection also provides Rapid response team support and cost guarantee. The other SKU is IP protection which is more targeted towards customers and organizations that have fewer public IPs to protect. IP protection currently costs $199 and can be enabled directly on public IP resource.
Note: Azure DDoS Rapid Response (DRR) and Cost guarantee are available only in DDoS Network Protection SKU.
For more information about Azure DDoS Protection see here Azure DDoS Protection Overview | Microsoft Learn
Azure DDoS Simulation Partners
The simulation environments of our partners are built within Azure. Simulation testing is restricted to Azure-hosted public IP addresses associated with your unique Azure subscription, a step that simulation partners will have to verify prior to conducting any tests.
Approved Simulation Partners:
- BreakingPoint Cloud: A self-service traffic generator that enables the generation of traffic against DDoS Protection-enabled public endpoints for simulations. This tool offers a practical way to test your defenses against DDoS attacks.
- Red Button: Collaborate with a dedicated team of experts to simulate real-world DDoS attack scenarios within a controlled environment. This partner provides specialized insights and guidance for your simulation testing.
- RedWolf: A self-service or guided DDoS testing provider with real-time control. RedWolf empowers you to create tailored simulation scenarios to assess your readiness against DDoS threats.
For more information about the simulation partners see here Azure DDoS Protection simulation testing | Microsoft Learn
Benefits of Azure DDoS Simulation Testing:
- Azure DDoS Protection Validation: Simulations allow you to verify the effectiveness of Azure DDoS Protection in safeguarding your Azure resources against DDoS attacks. This verification reinforces your confidence in Azure's security capabilities.
- Gap Identification: Through these simulations, you can identify gaps in both technology and processes. This dual perspective empowers you to refine your DDoS response strategy, strengthening your overall security posture.
- Incident Response Optimization: Under the simulated conditions of an attack, you can optimize your incident response procedures. This hands-on experience in a controlled environment hones your team's ability to effectively manage real-world DDoS attacks.
- DDoS Compliance Documentation: Documentation resulting from simulation testing provides evidence of your organization's compliance with DDoS resilience and response standards. This documentation is invaluable in audits and regulatory assessments.
- Team Training: Through simulations, your network security teams can undergo realistic training scenarios. These experiences enhance their skills, readiness, and confidence in dealing with DDoS threats.
Setting up your environment for Simulation Testing
For this test we will use BreakingPoint Cloud to initiate a DDoS attack against our resources in Azure, before starting, make sure you meet all the requirements below.
Testing Environment and Requirements:
- Simulations are performed against Azure-hosted public IP addresses owned by your Azure subscription.
- These public IP addresses must be protected under Azure DDoS Protection.
- Partners will need to validate your subscription before testing to ensure compliance, make sure you have read access to all your public IP resources.
Note: Conduct simulations in controlled environments, such as staging environments or during non-peak hours, to minimize impact on production systems
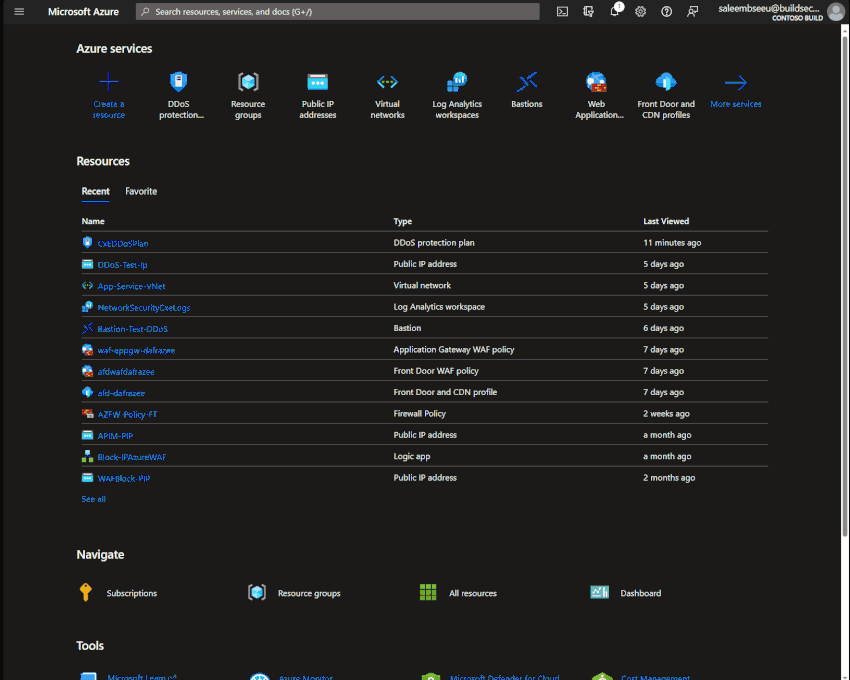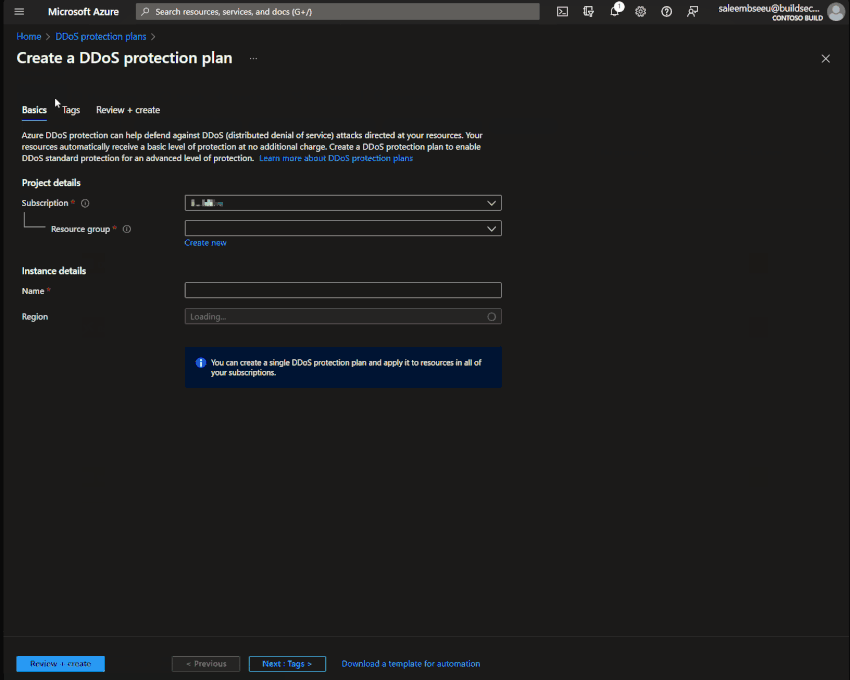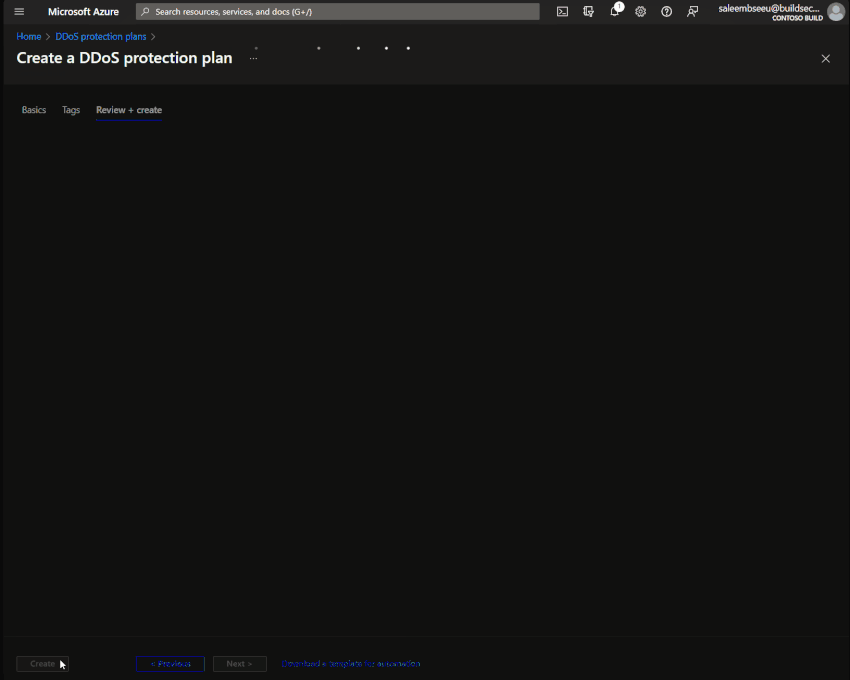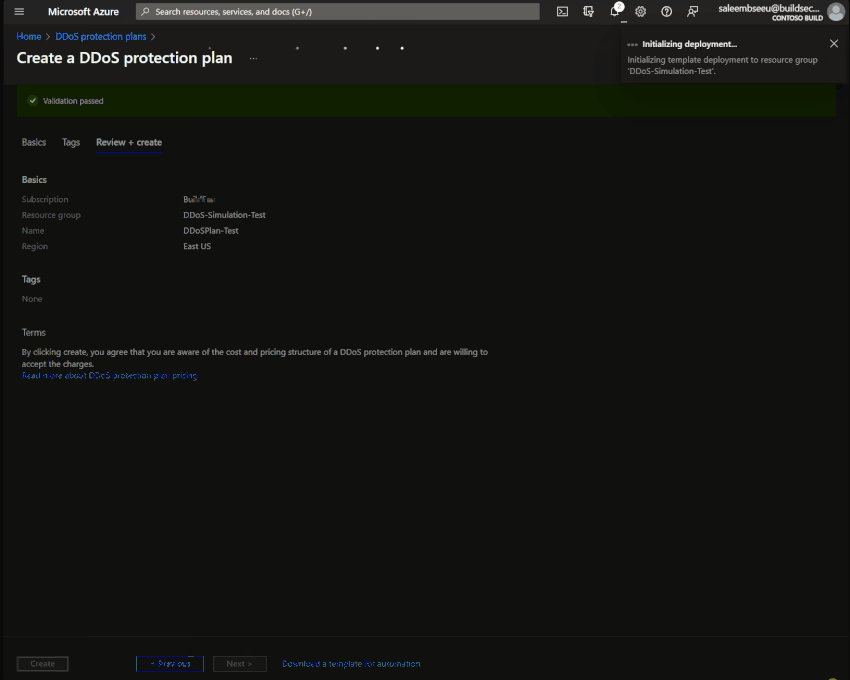
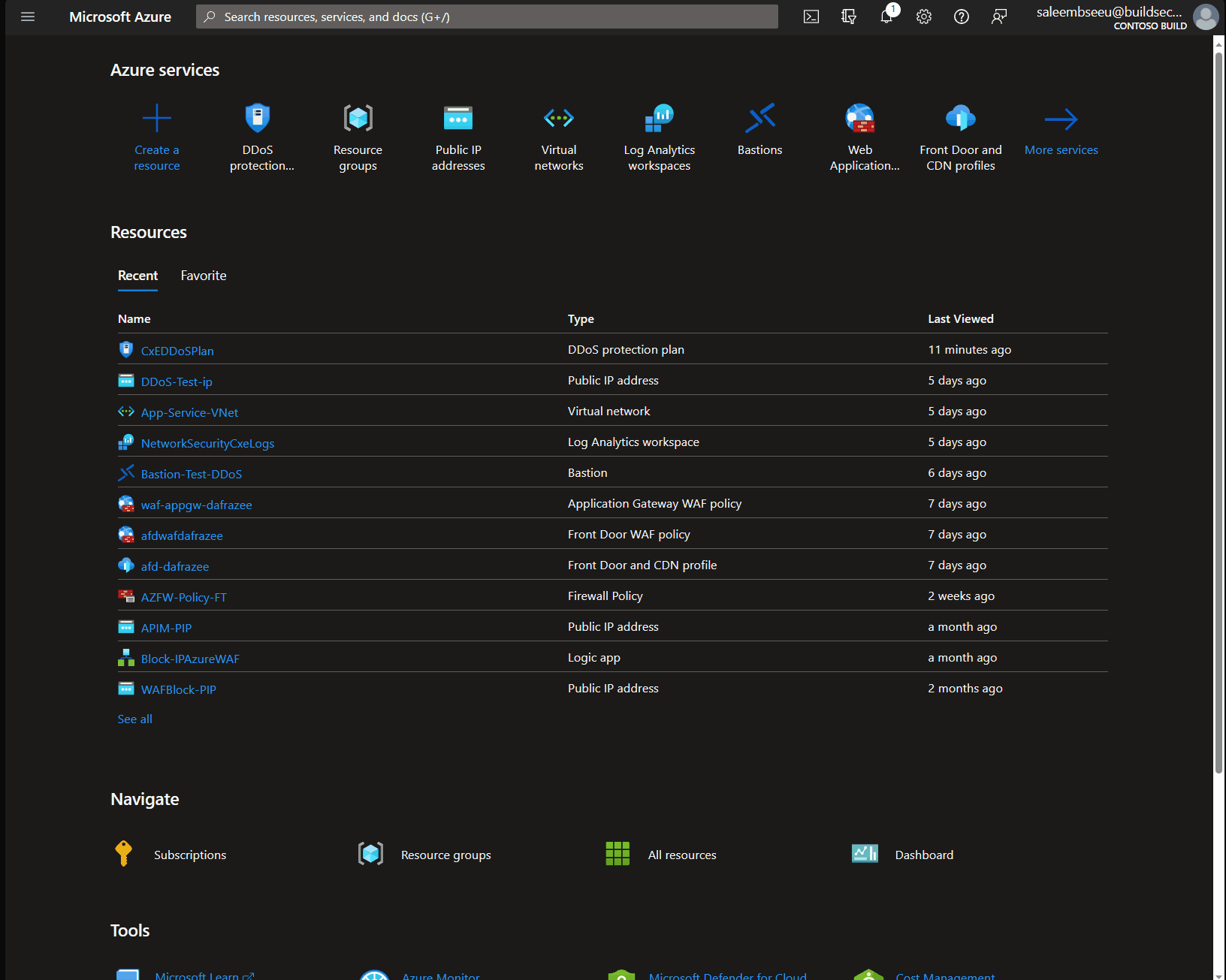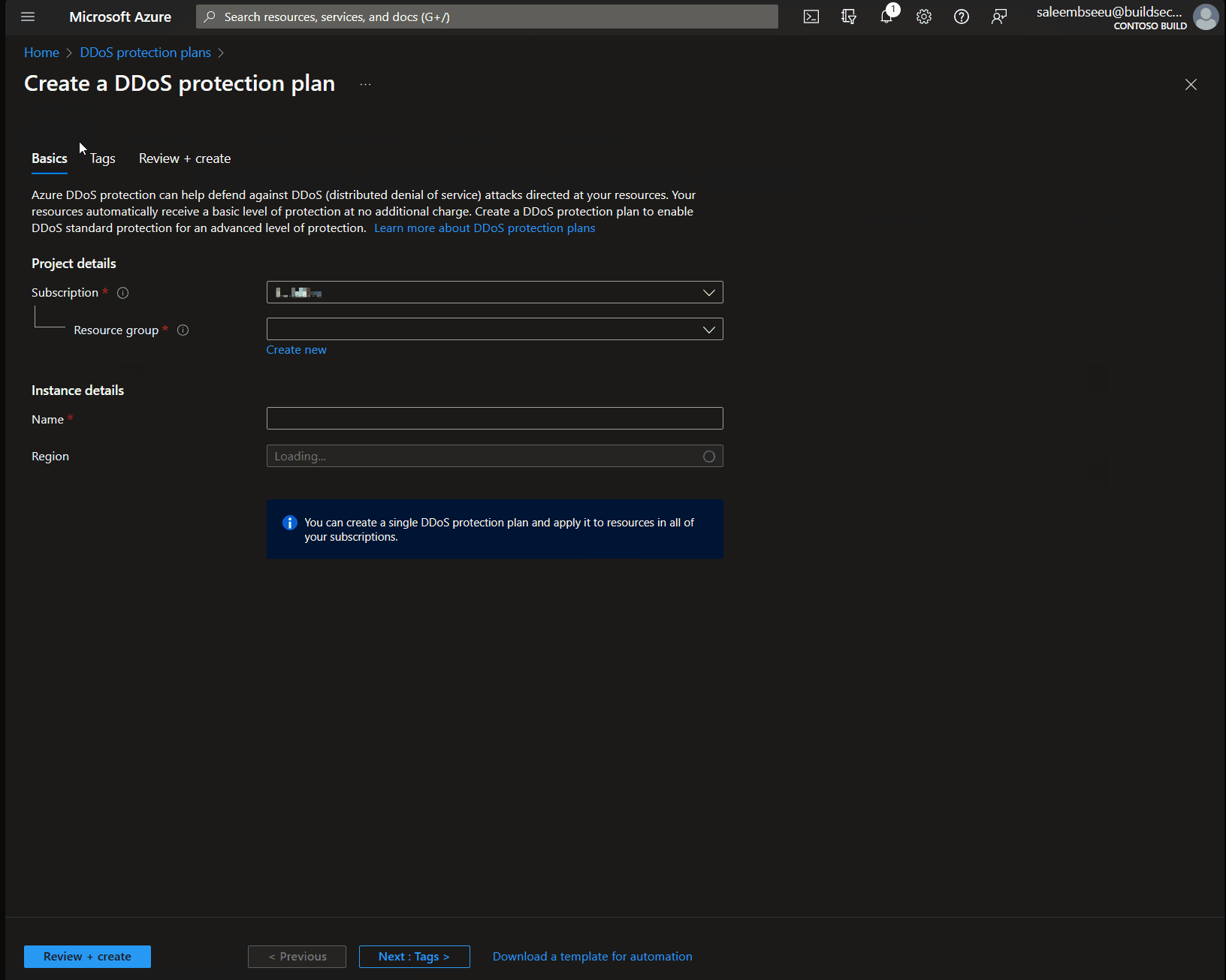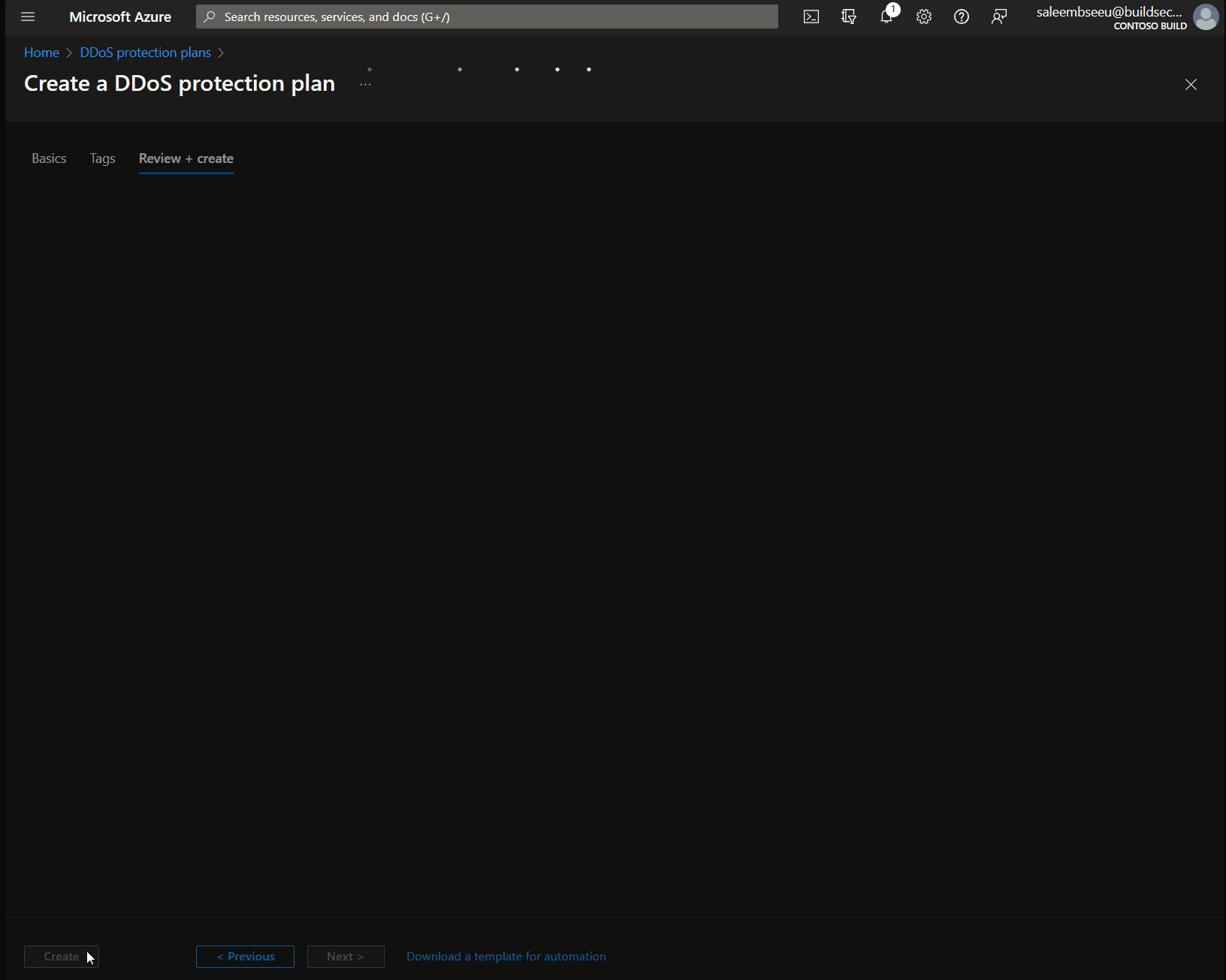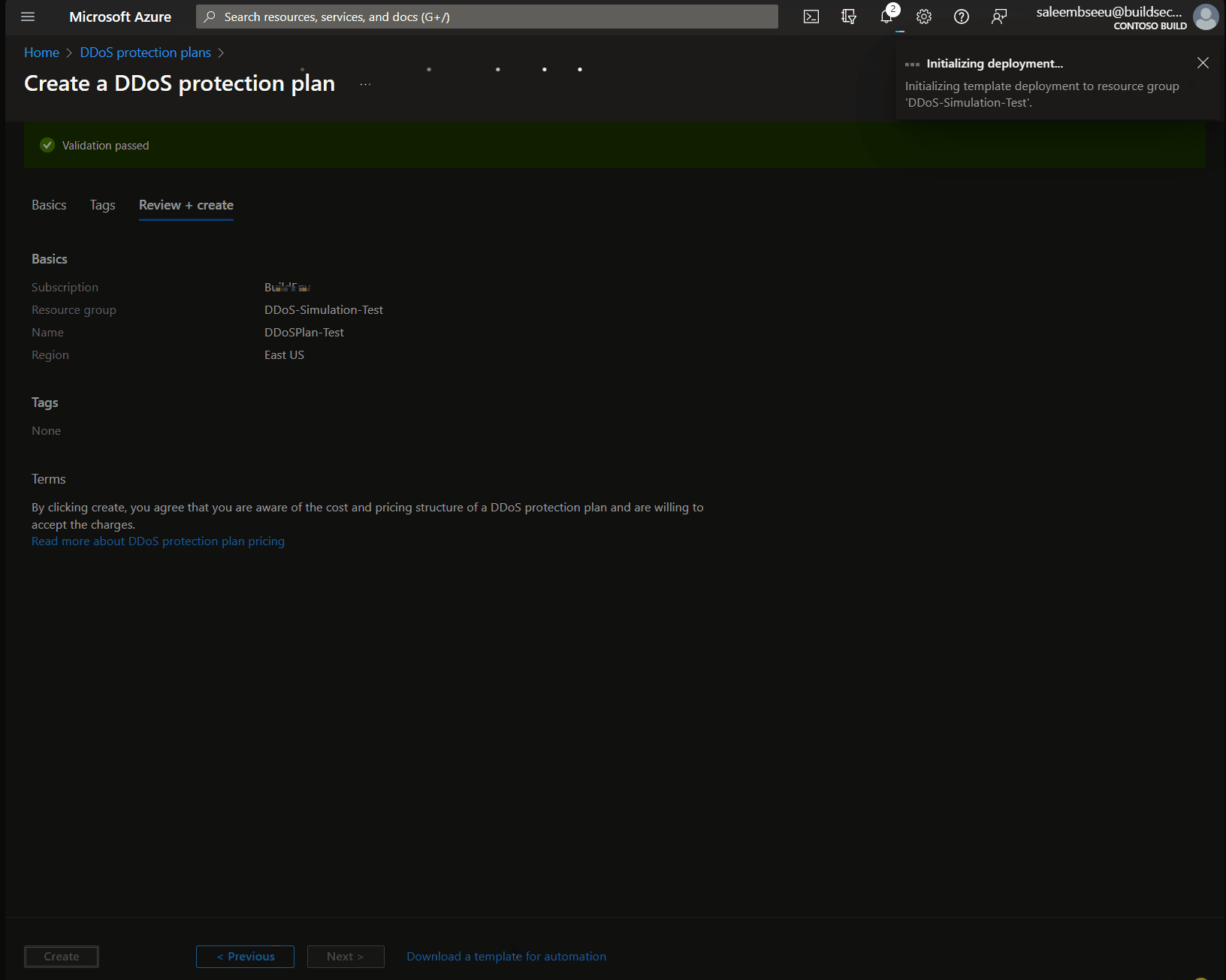
Step 1: Create a DDoS Protection Plan
Creating an Azure DDoS Protection plan is straightforward and simple. Under DDoS protection plans select create, Add your subscription, resource group, plan name and region. Then review and create. That’s all needed to create a DDoS plan.
Note: Azure DDoS Network Protection can be enabled on all subscriptions under the same tenant.
Step 2: Enable DDoS protection plan for VNET
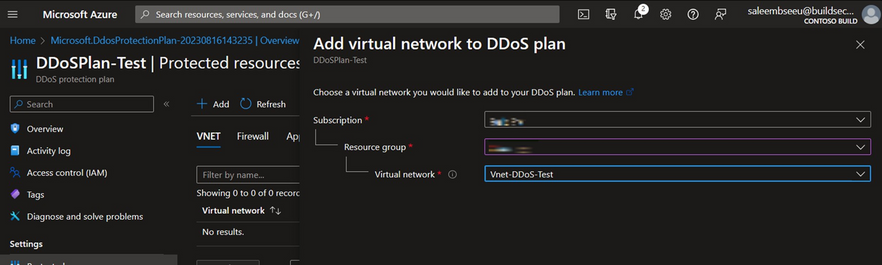
Next, we will enable the DDoS protection plan for our Virtual Network (VNET), where the public IP is currently located. Within the "protected resources" section, you'll find a list of all VNETs, and resources protected by the DDoS protection plan. To get started, click on the "add" button and choose the VNet containing your public IP.
For this specific test, we'll be utilizing a public IP attached to a Bastion host. However, you have the flexibility to test any public IP that’s in ARM-based VNETs. If you're uncertain about the VNet containing your public IP, simply access your public IP resource and click on the value next to "Associated to." This will lead you to the resource associated with your public IP, allowing you to identify the specific VNet where it is deployed.
Step 3: Enable logging for DDoS mitigation traffic.
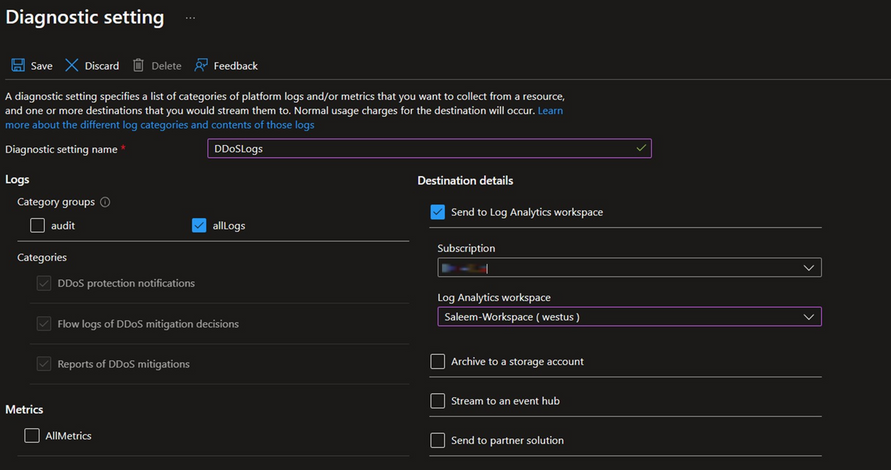
Now, let's proceed to enable logging for DDoS mitigation traffic. To achieve this, navigate to the public IP resource and locate the "Diagnostic settings" section. Here, you'll have the option to add a new setting. You'll notice three distinct categories that can be enabled.
- DDoS Protection Notifications: This category offers insights into the initiation and conclusion of DDoS mitigation instances. It provides details about the triggered threshold and identifies the impacted public IP.
- Flow Logs: Under this category, you gain access to comprehensive information about each packet encountered during the mitigation process. You will see whether a packet was forwarded or dropped because it was found malicious.
- DDoS Mitigation Reports: This category offers regular reports on DDoS mitigation, with updates provided every 5 minutes. Additionally, a post-mitigation report is generated for a comprehensive overview.
The choice of category selection should align with the specific needs and requirements of your organization. For the purposes of this guide, we will enable all three categories, and send the generated logs to our analytics workspace for further investigation and analysis.
Step 4: Authorize Azure subscriptions within our simulation partner.
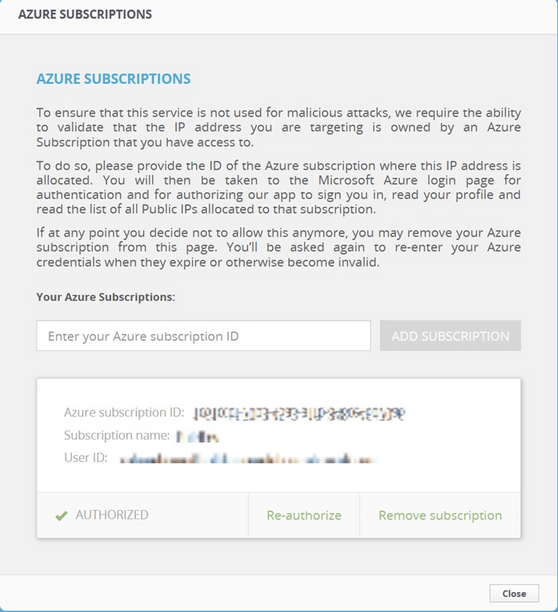
let's move on to authorizing the Azure subscription within our simulation partner, BreakingPoint Cloud. Begin by logging into BreakingPoint using your credentials. In the upper-right corner of the interface, you'll see a settings icon. Click on it, then proceed to select "Azure Subscriptions."
This action will open a window displaying your Azure subscriptions. Within this window, you have the options to add, authorize, and remove subscriptions. To proceed, paste your subscription ID and click on the "Add Subscription" button. Then, select "Re-authorize." This step will trigger a redirection to the Azure portal, prompting you to sign in using your Azure account. This authentication step is essential to authorize the application to access your Azure subscription and obtain a list of all public IPs associated with it.
Initiating the DDoS Simulation Attack
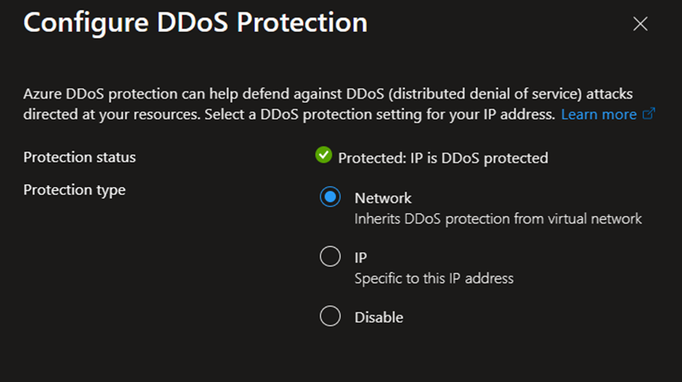
Step 5: validating That DDoS protection is enabled on your public IPs.
Before initiating the test, let's ensure that our public IP is protected by Azure DDoS protection. Navigate to your public IP resource, and on the overview page, select "Protect" under the "Protect IP Address" section. As shown in the image below, you should see a green checkmark and the label "protected". For this test it’s protected by the Network SKU however you can also use the DDoS IP Protection option if you need to protect only 1 or few public IPs.
Step 6: Launching DDoS simulation attack
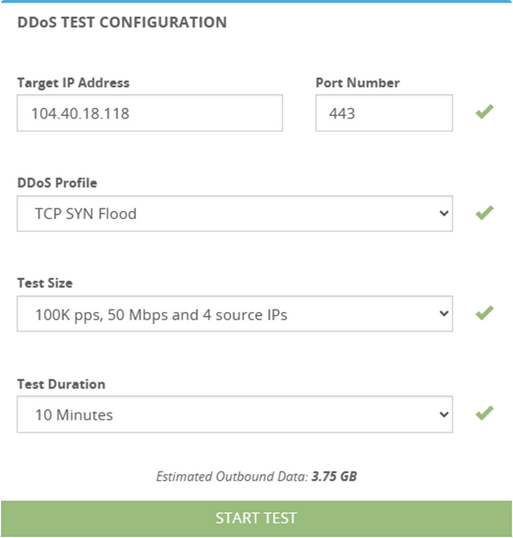
Now that the testing environment is set up, let's launch our DDoS simulation attack. Head over to your BreakingPoint page and begin by selecting your desired DDoS test configuration. For this particular test, we'll direct the attack towards port 443 of our public IP, using a TCP SYN Flood attack method, and send 100,000 packets per second for a duration of 10 minutes.
Note: A TCP SYN Flood DDoS attack floods a target server with a massive stream of connection requests, overwhelming its ability to respond. Sending numerous SYN packets but not completing the handshake, tying up server resources and causing denial of service for legitimate users
Post-Attack Investigation
Step 7: Monitoring metrics
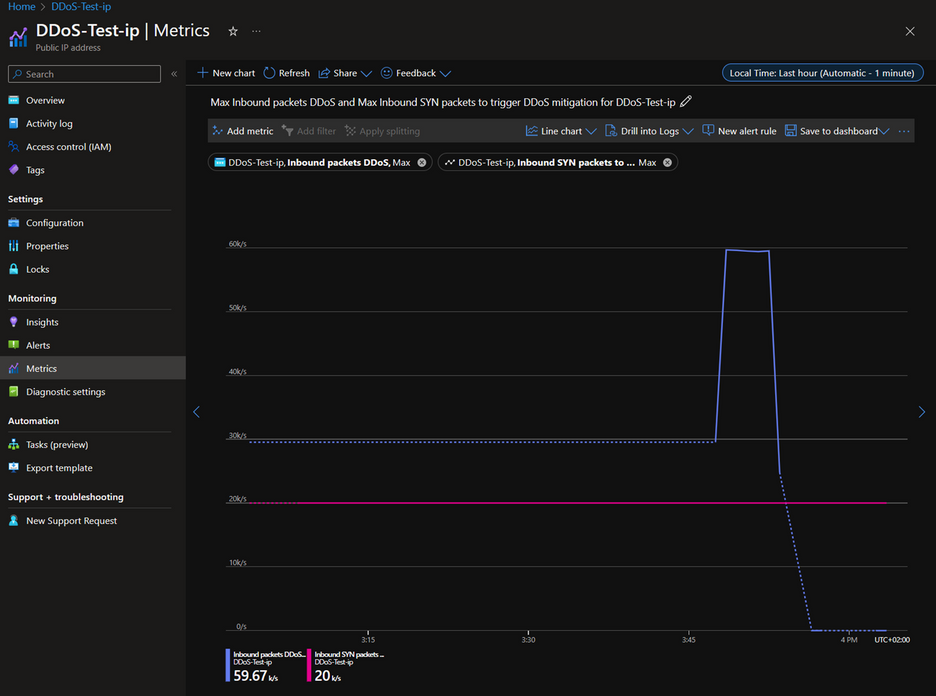
Once the simulation attack is done, we will start investigating the logs and metrics. Navigate to your public IP resource and access the metrics section. To track the DDoS mitigation initiation time, choose the specific metric "Under DDoS attack or not" and apply the "Max" aggregation. This metric reveals when the resource experienced a DDoS attack.
Now let’s check the threshold for Syn packets related to this Public IP resource. Pick the metric "Inbound SYN packets to trigger DDoS mitigation." This metric displays the threshold determined by adaptive real-time tuning. Include another metric named "Inbound packets DDoS" using the Max aggregation. As shown in the image below, you can observe the volume of packets directed at this resource surpassing the threshold, which triggered the DDoS mitigation.
Step 8: Investigating DDoS mitigation logs
Next, Let's look at the generated logs from DDoS simulation attack. Navigate to your work analytics workspace where you are sending the logs and access the Logs section. Our first focus will be on exploring the DDoS Protection Notifications category. Run the following query to look for DDoS notifications:
AzureDiagnostics
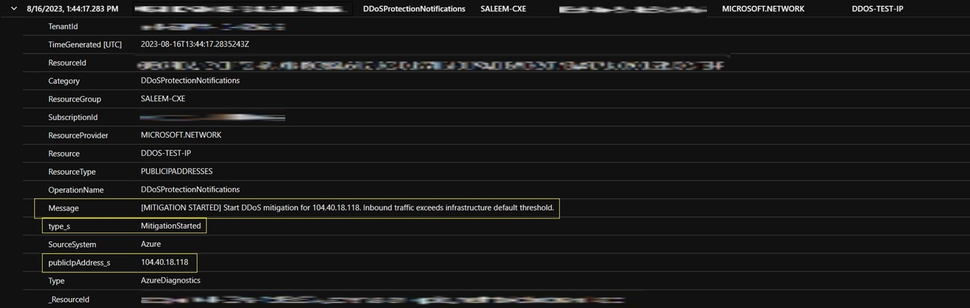
| where Category == "DDoSProtectionNotifications"
The earliest log entry for DDoS notifications will usually be this type "MitigationStarted." This entry signifies the start of DDoS mitigation, and you can also see information regarding which Public IP is impacted. Additionally you can create an alert to notify you of the initiation of a DDoS attack, for more information about creating an alert see here Configure Azure DDoS Protection diagnostic logging alerts | Microsoft Learn
Next, let's delve into the mitigation flow logs. Run this query to look for mitigation flow logs category:
AzureDiagnostics
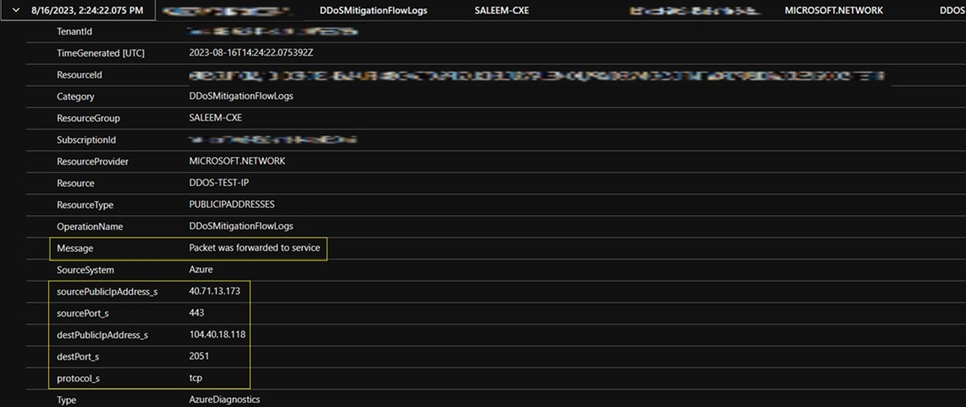
| where Category == "DDoSMitigationFlowLogs"
These DDoS mitigation flow logs provide you with real-time insight into all the traffic that was either forwarded or dropped during the DDoS mitigation process. This data is valuable for understanding the traffic that was allowed through and distinguishing it from the malicious traffic that was rejected. Moreover, it allows you to investigate false positives. In the image below you can see an example of a packet which was found legitimate and forwarded to the resource.
Note: It's important to be aware that DDoS mitigation flow logs can generate a substantial volume of data, depending on the amount of traffic during the DDoS attack.
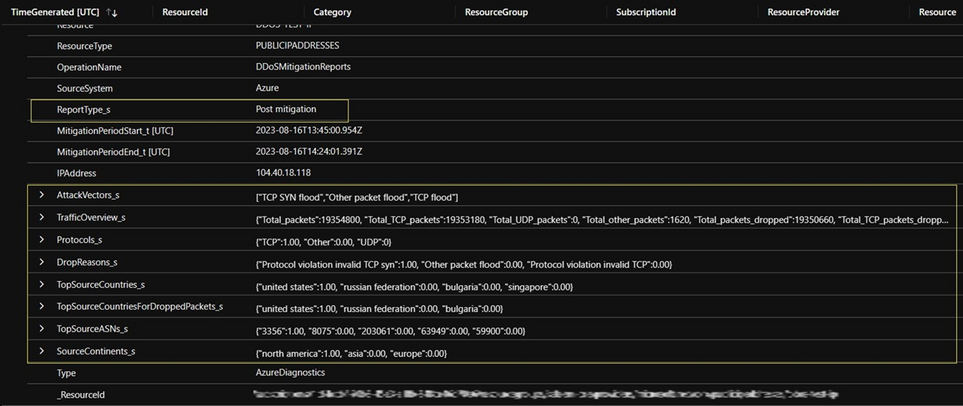
Finally, let’s explore the DDoS mitigation reports. Run the following query to get the logs:
AzureDiagnostics
| where Category == "DDoSMitigationReports"
These DDoS mitigation reports come in two types. The first is the incremental report, generated every five minutes throughout the DDoS attack. The second is the post-mitigation report, which consolidates all attack-related data into a single log entry.
Within this report, you'll find valuable insights. These include details like the originating countries and ASNs (Autonomous System Numbers) from which the attack started, the source IPs involved, the attack vectors used, reasons for dropped packets, and an overview of the traffic involved. In the image below, you'll see the post-mitigation report that was generated from our simulated DDoS attack.
Azure Monitor Workbook for DDoS Protection
The previous report shows data exclusively for a single public IP. However, if you're dealing with multiple attacked public IPs, an effective approach is to leverage our Azure Monitor workbook designed for DDoS protection. This workbook consolidates all DDoS log data associated with your public IPs and presents it through user-friendly panels and charts for enhanced readability.
To deploy this workbook, you can use the following GitHub link to deploy the workbook within your Azure environment: Azure-Network-Security/Azure DDoS Protection/Workbook - Azure DDOS monitor workbook/README.md at master · Azure/Azure-Network-Security (github.com)
Conclusion
Simulation testing is an indispensable tool for evaluating and strengthening Azure DDoS Protection. By designing and executing simulation tests, organizations can proactively identify weaknesses, optimize protection configurations, and enhance their incident response strategies. Utilize the power of simulation testing to fortify your defenses and confidently defend your Azure infrastructure against the ever-evolving threat of DDoS attacks.
Resources
- Azure DDoS Protection simulation testing | Microsoft Learn
- Quickstart: Create and configure Azure DDoS Network Protection using - Azure portal | Microsoft Learn
- Quickstart: Create and configure Azure DDoS IP Protection - Azure portal | Microsoft Learn
- Tutorial: View and configure DDoS protection telemetry for Azure DDoS Protection | Microsoft Learn
- View Azure DDoS Protection logs in Log Analytics workspace | Microsoft Learn
Published on:
Learn moreRelated posts
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...
General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB
Title: General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB We’re excited to announce the general availability of the ...
Efficiently and Elegantly Modeling Embeddings in Azure SQL and SQL Server
Storing and querying text embeddings in a database it might seem challenging, but with the right schema design, it’s not only possible, ...