Automation for Large Scale Deployment of Agents on Servers managed by Azure Arc
|
There is a growing need for the deployment of tools or agents on on-premise servers in bulk. Its highly time consuming to manually deploy the agent in bulk.
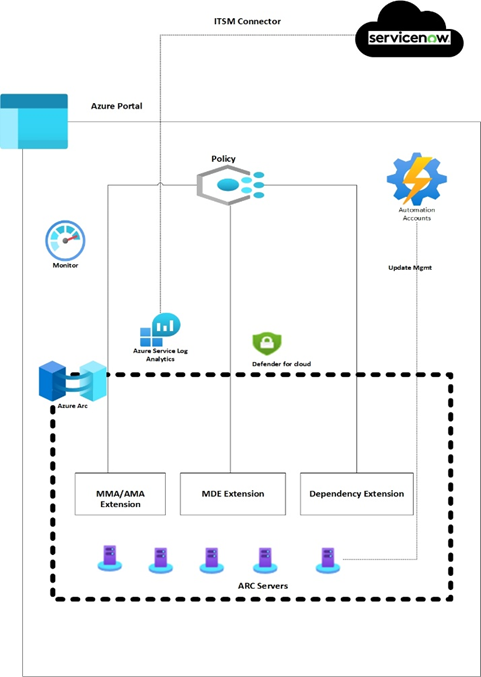
Microsoft Azure uses Azure Arc for the agents/tools/application deployments and can be combined with Azure policy for large scale mass deployment. In the below usecase Log Analytics and Dependency agents pushed via the policy.
Agents can be deployed manually using Azure portal, though for large environment, it is recommended to push these agents via custom Azure Policy or using PowerShell automation scripting.
|

|
Deployment using Azure Policy
Below usecase helps deploying Log Analytics and Dependency agents using Azure policy.
There are 2 core functionalities of Azure policy that allows the automation
- Creating Azure Policy Definition
- Policy assignment & Remediation
Creating Azure Policy Definition
In order to push through Azure policy the first step is to define policy rule as below, for Arc the resource type is Microsoft.HybridCompute, For Linux we just need to change imageOffer to “linux*”.
|
"policyRule": { "if": { "allOf": [ { "field": "type", "equals": "Microsoft.HybridCompute/machines" }, { "field": "Microsoft.HybridCompute/imageOffer", "like": "windows*" } If we want to deploy MMA only to certain Arc servers, then we can add a tag to the machine, for example “loganalytics:true” and define the below section in PolicyRule, then it will push MMA agent only to VMs where this tag is set as true. { "field": "tags.loganalytics", "equals": "true" } |

|
Define OMSagent for Linux & MMA for Windows.
Policy Assignment and Remediation
After creating policy definition create policy assignment to define scope, resource exclusion against the assignment defined in the first step.
Next is to create remediation task with managed identity to auto remediate all non-compliant Arc Machine.
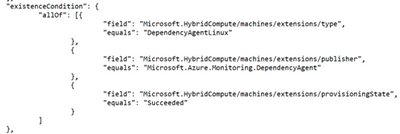
For Dependency Agent, the policy rule will remain same as defined for MMA, define imageOffer “windows*” for windows server & “Linux*” for Linux respectively. Existence condition will change based on the extension type.
Define Parameter, Variables and resources as below:
Deployment using Powershell Script
We can also deploy MMA/OMSAgent extensions to Arc servers via PowerShell command for all the servers aligned within same resource group.
In order to run the below command, put all the VMs, separated per line, in a text file and create a loop logic as below
$VMname=get-content "C:\list.txt"
foreach($vm in $VMname){
$vm1 = Get-AzConnectedMachine -Name $vm -ResourceGroupName <RGNAME>
$Setting = @{ "workspaceId" = "workspaceId" }
$protectedSetting = @{ "workspaceKey" = "workspaceKey" }
New-AzConnectedMachineExtension -Name OMSLinuxAgent -ResourceGroupName "RGName" -MachineName $vm1.Name -Location "regionName" -Publisher "Microsoft.EnterpriseCloud.Monitoring" -Settings $Setting -ProtectedSetting $protectedSetting -ExtensionType "OmsAgentForLinux"
}
For windows change the value for the -ExtensionType parameter to "MicrosoftMonitoringAgent".
References
Azure Arc
Azure Arc helps client to bring their distributed workloads under single control planes using Azure Public Cloud. This will allow for direct enablement and integration with Microsoft Security tools and monitoring agents.
https://learn.microsoft.com/en-us/azure/azure-arc/servers/overview
Azure Policy
Azure policy helps assess organization compliance and overall environmental state. Azure policy allows to restrict usage of Azure resources based on compliance requirements.
https://learn.microsoft.com/en-us/azure/governance/policy/
About Author
Kritika Gupta
I am an experienced IT professional, focused on cloud technologies and DevOps. I specialize in Azure, Azure DevOps, Arc, AKS , PowerShell/CLI.
I am currently working at DXC Technology as an Azure Sr. Engineer in the Global India Azure Delivery Team. LinkedIn: "linkedin.com/in/kritika-gupta-609757b6"
Published on:
Learn moreRelated posts
AI Builder – Actions name changes in Power Automate
The names of the following AI Builder actions have been updated in the Power Automate flow designer: “Create text with GPT using a promp...
Copilot Agent Flows vs Power Automate Cloud Flows – key differences
Agent flows are a powerful way to automate repetitive tasks and integrate your apps and services. But how do they differ from Power Automate f...
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...
General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB
Title: General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB We’re excited to announce the general availability of the ...