Building a POC for TLS inspection in Azure Firewall

Authored by - Deepak Maheshwari
This blog post will provide a step-by-step guide to build a Proof of Concept (POC) Lab that uses the Transport Layer Security (TLS) Inspection feature of Azure Firewall Premium by using the Certification Auto-Generation mechanism, which automatically creates the following three resources for you:
- Managed Identity
- Key Vault
- Self-signed Root CA certificate
Azure Firewall TLS Inspection requires Public Key Infrastructure (PKI) to issue certificates. Setting up a PKI system is a complex process, as it requires deploying some additional resources such as Windows Virtual machine(s) to host Active Directory Certificate Services (ADCS) - to issue certificates - and additional configurations to set up the environment. This makes it a non-ideal solution for a POC where time to value is limited. The full process of generating, exporting, and configuring PKI certificates for Azure Firewall is documented in this article - Deploy and configure Enterprise CA certificates for Azure Firewall Premium. Azure Firewall also supports Self-Signed certificates, but this configuration also requires some additional steps.
What is TLS Inspection in Azure Firewall Premium?
Azure Firewall Premium provides TLS inspection capability by decrypting the outbound traffic, inspecting it, processing it, and then re-encrypting the data and sending it to the destination. Azure Firewall Premium intercepts outbound HTTPS traffic and auto-generates a server certificate for the URL that you are trying to access. End-user browsers and the client applications must trust your organization’s Root CA certificate or intermediate CA certificate for this procedure to work.
Additionally, Azure Firewall Premium supports TLS inspection for East-West traffic and inbound traffic (when an Application Gateway is deployed before Azure Firewall Premium). For more information on the supported use cases refer to - Azure Firewall TLS Inspection.
Why TLS inspection is important
Encrypted traffic has a security risk, as it can hide illegal user activity and malicious traffic. Azure Firewall without TLS inspection has no visibility into the data that flows in the encrypted TLS tunnel, and so it cannot provide full protection coverage for the outbound traffic.
- Azure Firewall without TLS Inspection:
- Azure Firewall with TLS Inspection:
How TLS inspection works in Azure Firewall Premium
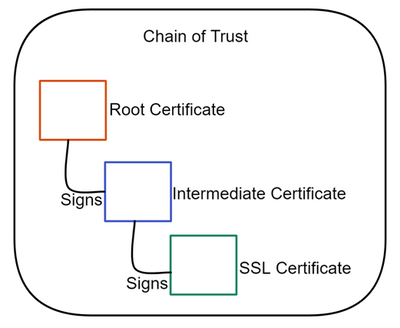
TLS inspection is achieved by using an Intermediate CA certificate. An intermediate certificate works as a substitute of a root certificate. Intermediate certificates are also used as a stand-in for a root certificate by playing a “Chain of Trust” between an end entity certificate and a root.
How to Enable TLS Inspection in Azure Firewall Premium with auto-generate new certification feature in a POC environment:
- Navigate to the Azure Firewall Premium Policy you want to enable TLS inspection.
- From the left menu pane, Select - TLS Inspection - and click on the Enabled option.
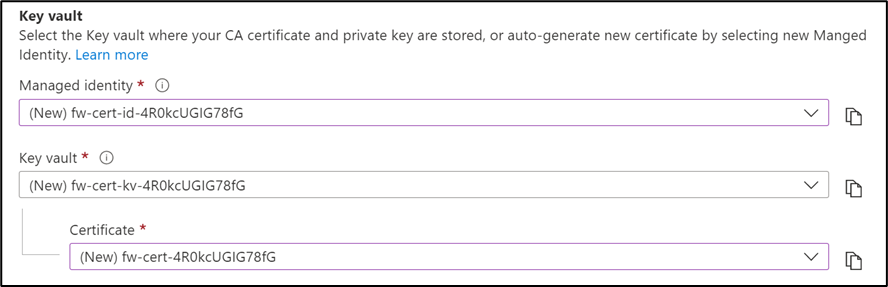
- In the Key Vault section, under Managed identity, select (New) Managed Identity Name.
- The following new resources with a random name will be created
- Managed Identity
- Key Vault
- Self-signed Root CA certificate
4. Click on Save button at the bottom of the page to commit the changes.
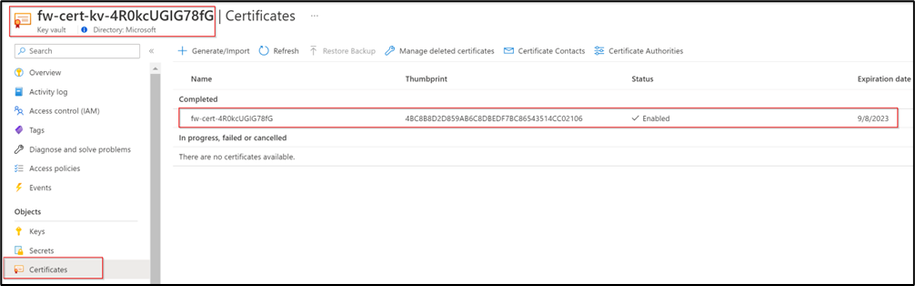
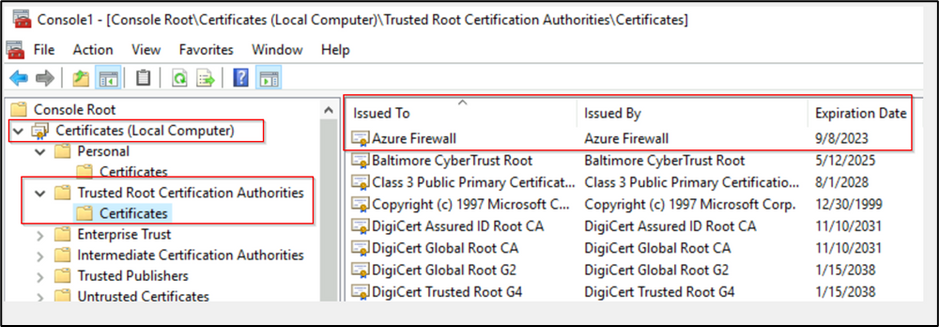
5. Once saved, a new Managed identity and new Azure Key vault will be created along with a new root certificate (You can view the certificate under the certificates section).
6. Once you click on certificate, you will get an option to download the certificate in both PFX/PEM and CER format. Download the certificate in .CER format and copy it to the end user’s machine from where you would like to access a secure public website.
7. Configure an Application Rule in the Azure firewall policy to allow the outbound web traffic from the end user’s machine. Since TLS inspection is enabled in this outbound rule, all outbound traffic will be inspected by the Azure Firewall. An example of an application rule created for our test can be seen in the following figure:
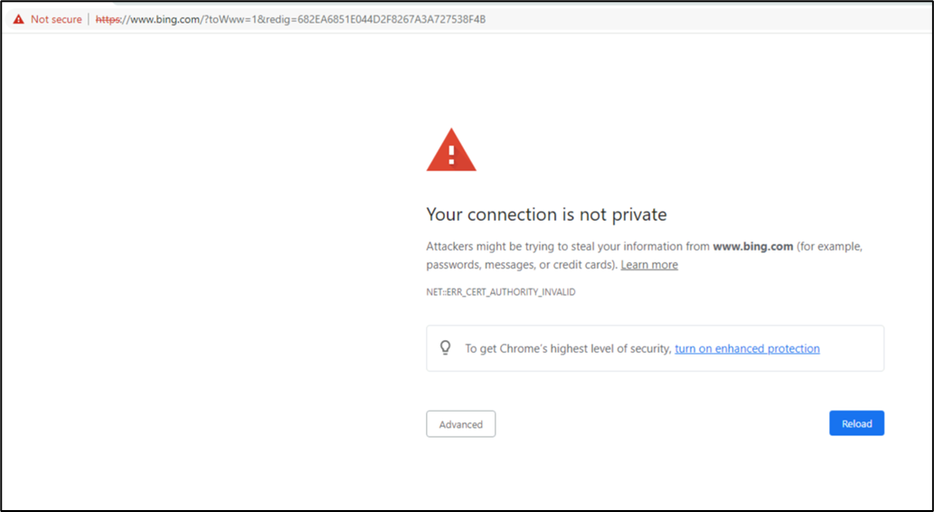
8. Now let’s try to access a secure website such as https://bing.com from the end user’s machine. If you do not have the newly downloaded .CER certificate installed in your trusted root certificate store on your machine, you will receive the following error message
9. Import the downloaded .CER certificate to the “Trusted Root Certification Authority” on the end user’s machine from where you are trying to access https://bing.com.
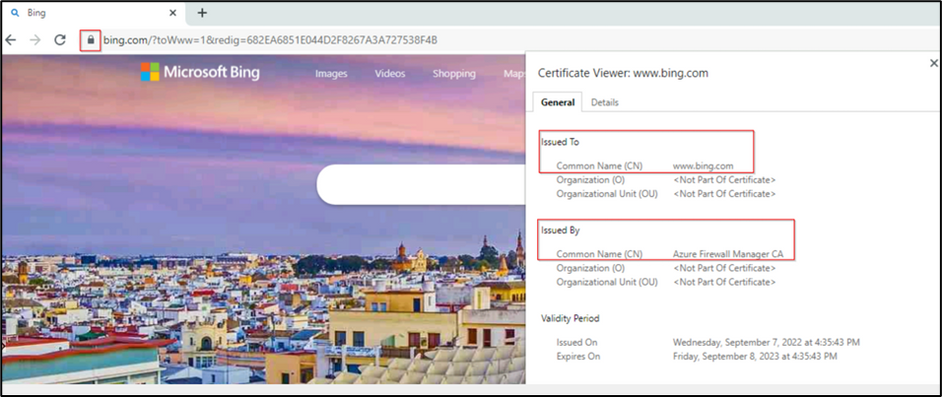
10. Now, reopen the https://bing.com or any other secure website. You should be able to access the website. Look at the connection security in the browser. You should now see the certificate is issued by the Azure Firewall Manager.
This confirms that TLS inspection is working, and all outbound traffic is inspected by the Azure Firewall.
Conclusion
TLS inspection in Azure Firewall Premium is a powerful tool to decrypt encrypted traffic and allow for further inspection by Application Rules or IDPS. This POC guide can be leveraged by organizations to build a POC lab to demonstrate the TLS inspection capability of Azure Firewall Premium in a non-production environment without the need of setting-up a new PKI infrastructure.
Further reference - To generate a POC environment with Azure Firewall Premium in a single click - check out the template in Deploy and configure Azure Firewall Premium.
Published on:
Learn moreRelated posts
Powering Real-Time Messaging at Scale with Azure Cosmos DB
Microsoft Teams, Copilot, Azure Communication Services and many other product offerings from Microsoft, rely on a unified messaging platform t...
Azure SQL Cryptozoology AI Embeddings Lab Now Available!
Missed out on MS Build 2025? No worries! Our lab is now available for your exploration. Dive into a unique cryptozoology experience using Azur...
Vector Support Public Preview now extended to Azure SQL MI
We are thrilled to announce that Azure SQL Managed Instance now supports Vector type and functions in public preview. This builds on the mome...
Building Multi-Agent AI Apps in Java with Spring AI and Azure Cosmos DB!
As AI-driven apps become more sophisticated, there’s an increasing need for them to mimic collaborative problem solving – like a t...
What runs ChatGPT, Sora, DeepSeek & Llama on Azure? (feat. Mark Russinovich)
Build and run your AI apps and agents at scale with Azure. Orchestrate multi-agent apps and high-scale inference solutions using open-source a...
Azure Cosmos DB TV – Everything New in Azure Cosmos DB from Microsoft Build 2025
Microsoft Build 2025 brought major innovations to Azure Cosmos DB, and in Episode 105 of Azure Cosmos DB TV, Principal Program Manager Mark Br...
Azure DevOps with GitHub Repositories – Your path to Agentic AI
GitHub Copilot has evolved beyond a coding assistant in the IDE into an agentic teammate – providing actionable feedback on pull requests, fix...