How to use Azure Container registry to standardize deployments using Bicep across your organization

This post is part of a series
- How to deploy Azure LogAnalytics Workspace and link Application Insights to it
- 📍 you are here - How to use Azure Container registry to standardize deployments using Bicep across your organization
- How to utilize the Azure Container Registry in your Azure DevOps pipeline - to be published soon
I like to deploy my Azure resources using Bicep - If you never heard about it, I blogged a while ago on how to get started with Bicep - please catch up first!
You might now know, that I am a big fan of infrastructure as code
- no more manual clickety-clackety in the Azure portal
- it’s just less prone to human error
- our deployment files can be logged into source control
I did not realize that many fellow developers still copy/paste code from their previous Bicep files to their current files. Or, even worse, they need to ask other developers in the organization how they use to deploy a certain resource. Infrastructure as Code is good, but wouldn’t it be better if we had a centralized repository across our organization with ready-to-use deployment files?
Azure Container Registry to the rescue!
What is Azure Container Registry?
Azure Container Registry (ACR) is a powerful tool for managing Docker container images, and it comes with several practical benefits:
- ACR works effortlessly with other Azure services like Azure DevOps (more in this in a later part of this series). This makes it easier to set up continuous integration and deployment (CI/CD) pipelines
- ACR provides a private, secure registry for your container images - You can control access with Microsoft Entra Id
- It supports both Linux and Windows containers
Using ACR for our Bicep files will help with managing, versioning, and deploying our IaC as efficiently as possible. (And who wouldn’t want to spend less time on deployments 🤭)
How to create an Azure Container Registry
⚠️ If you don’t already have Docker installed, please go ahead and do this! If you are unsure, you can verify the installation in your terminal with
docker --version, ot should return something like this: Docker version 27.1.1, build 6312585 - if your version number is significantly lower, an update can’t hurt!
Once this is done, in your terminal using Azure CLI
# Set variables
$ACR_NAME="building-blocks"
$RESOURCE_GROUP="building-blocks-rg"
$LOCATION="westeurope"
# Create the ACR
az acr create --name $ACR_NAME --resource-group $RESOURCE_GROUP --location $LOCATION --sku Basic
(You can choose a name and a location to your liking!)
Build and publish your Bicep modules to the ACR
We will use the bicep files that we created in the last blog post of this series - if you did not follow that one, please do so now:How to deploy Azure LogAnalytics Workspace and link Application Insights to it and publish them to the ACR.
In your terminal using Azure CLI:
# Log in to the ACR
az acr login --name $ACR_NAME
# Publish the Log Analytics workspace module
bicep publish --file ./loganalyticsworkspace.bicep --target br:$ACR_NAME.azurecr.io/bicep/modules/loganalyticsworkspace:1.0.0
# Publish the Application Insights module
bicep publish --file ./appinsights.bicep --target br:$ACR_NAME.azurecr.io/bicep/modules/appinsights:1.0.0
If you gave your modules names in camelCase, you will get an error - only lower case letters are allows –> ask me how I know 🙄
Update your main Bicep File
As a last step, we will update our main Bicep file:
param location string = resourceGroup().location
param logAnalyticsWorkspaceName string
param appInsightsName string
param applicationType string = 'web'
// Link the Log Analytics workspace module from ACR
module logAnalytics 'br:<yourACRName>.azurecr.io/bicep/modules/loganalyticsworkspace:1.0.0' = {
name: 'logAnalyticsDeployment'
params: {
location: location
logAnalyticsWorkspaceName: logAnalyticsWorkspaceName
}
}
// Link the Application Insights module from ACR
module appInsights 'br:<yourACRName>.azurecr.io/bicep/modules/appinsights:1.0.0' = {
name: 'appInsightsDeployment'
params: {
location: location
appInsightsName: appInsightsName
applicationType: applicationType
logAnalyticsWorkspaceId: logAnalytics.outputs.logAnalyticsWorkspaceId
}
}
Verify that the modules got published
Now we want to see that things worked, right? Easy enough, you can run az acr repository list --name $ACR_NAME --output table, which will return
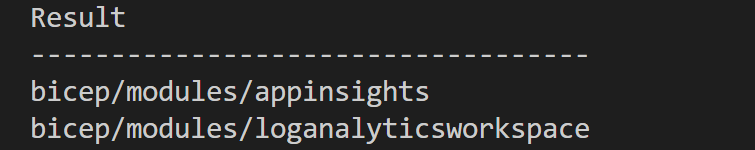
Conclusion
With ACR, you can now setup templates on how you want to deploy resources across the organization. This is especially helpful if you have resources with lots of properties like VMs :-). In the next blog post, I will cover how to utilize this approach in in Azure DevOps- Stay tuned!
Published on:
Learn moreRelated posts
Azure Backup-SAP HANA DB Backup Delivers More Value at Lower TCO with Reduced Protected Instance Fee
Azure Backup for SAP HANA Database Delivers More Value at Lower TCO with Reduced Protected Instance Fees starting 1st Sept’2024 At Azur...
Utilizing Azure DDoS Protection Workbook for DDoS attack traffic Analysis
In today's digital age, the security of applications, servers, and networks is paramount. One of the most significant threats to this security...
How to secure access to an Azure Container registry with a Managed Identity and RBAC
This post is part of a series How to deploy Azure LogAnalytics Workspace and link Application Insights to it How to use Azure Container Regi...
Unified Routing – Diagnostics in Azure
You may (or may not) be aware that the diagnostics option in Unified Routing has been deprecated. It is being replaced by diagnostics in Azure...
Service health and Message center: Azure Information Protection consolidation
This post is about the consolidation of Azure Information Protection communications under Microsoft Purview in Service Health and Message Cent...
Switch to Azure Business Continuity Center for your at scale BCDR management needs
In response to the evolving customer requirements and environments since COVID-19, including the shift towards hybrid work models and the incr...
Optimizing Azure Table Storage: Automated Data Cleanup using a PowerShell script with Azure Automate
Scenario This blog’s aim is to manage Table Storage data efficiently. Imagine you have a large Azure Table Storage that accumulates logs from ...
Microsoft Fabric: Resolving Capacity Admin Permission Issues in Automate Capacity Scaling with Azure LogicApps
A while back, I published a blogpost explaining how to use Azure LogicApps to automate scaling Microsoft Fabric F capacities under the PAYG (P...
The Azure Storage product group is heading to the SNIA Developer Conference 2024
The Azure Storage product group is heading to the SNIA Developer Conference (SDC) 2024 in Santa Clara, California, USA from September 16th thr...