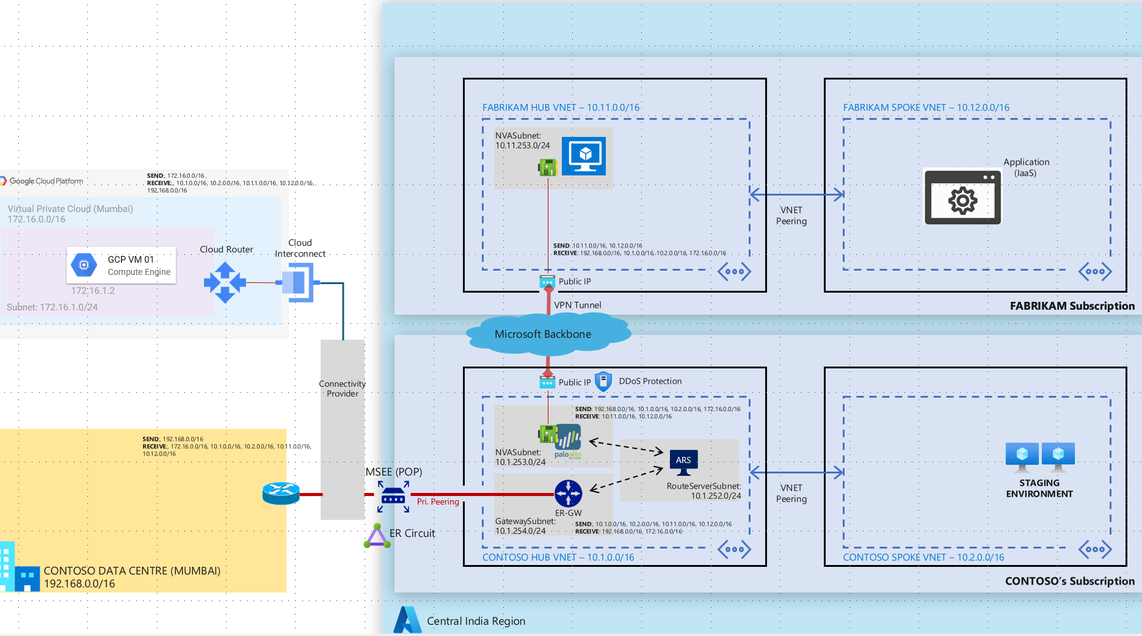
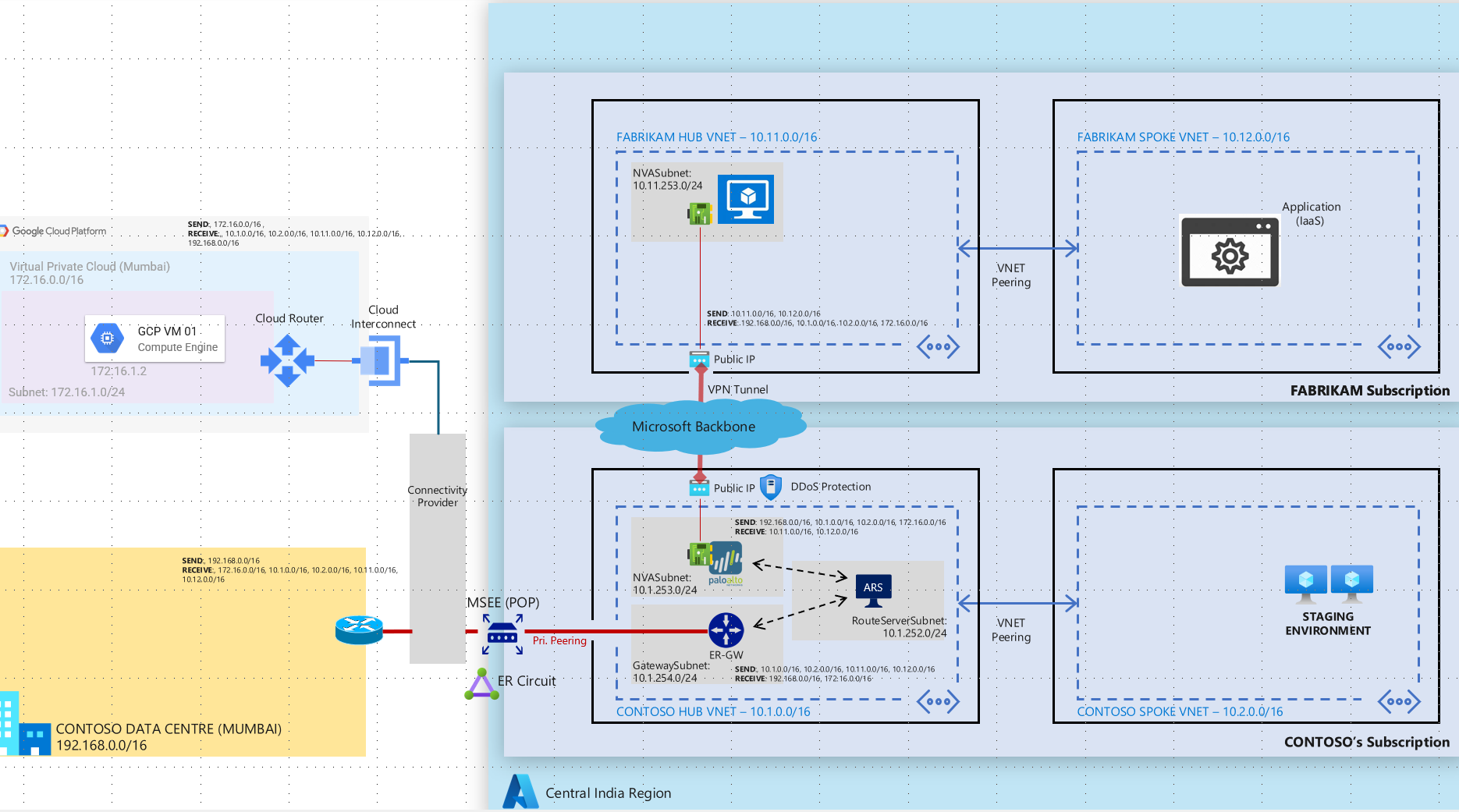
ISV network connectivity pattern for data exchange over public IP address between Azure and onPrem
This blog discusses ISV connectivity patterns for a customer who wants to exchange data with an Azure SaaS provider.
Contoso Corporation (Customer)
Contoso Corporation wants to access a SaaS application hosted on Azure from his on-premises data centres. The customer wants to be able to securely send and receive data.
Fabrikam Technologies(SaaS Solution Provider on Azure)
The SaaS solution provider has a fixed architecture where the incoming connections can only come in via a public IP which would be shared with all their customers. This public IP belongs to the NVA hosted in it's hub subscription. The SaaS provider would in turn whitelist customers public IP address on their NVA to allow exchange of data. It will not accept any incoming connections via VNET peering as it wants to follow a uniform method of connectivity for all it's customers.
Possible Solutions
Provided below are some connectivity patterns that can be used for data exchange in this scenario.
1> Connection over Express route Private Peering
In this connectivity pattern Contoso will need to have a hub and spoke architecture with key components such Express Route Gateway, Azure Route Server and NVA deployed in the hub network. Customer will need to have a Express Route circuit provisioned. Express route gateway will be used to send and receive traffic from on-premises over the express route circuit. Azure route server will be used to exchange traffic using BGP between ER Gateway and NVA as NVA and ER gateway are not capable of exchanging traffic directly between themselves. A secure VPN tunnel between Fabrikam and Contoso NVAs will be used to securely exchange traffic over public IP addresses. In order to further secure this architecture both Fabrikam and Contoso can deploy Azure DDoS per IP protection to secure public IP addresses from DDoS attacks.
2> IP Sec overlay on MS Peering connection
Microsoft Peering is the interconnection between Microsoft’s global network (AS8075) and customer/ISP network for the purpose of exchanging internet traffic from/to Microsoft online services and Microsoft Azure Services or connections to/from public IP address range on Azure. Carriers or Service Providers can request to connect with Microsoft at any of the available Edge locations.
Contoso can request a Microsoft Peering circuit. The connectivity provider will then provision a MS peering connection between the providers location and Microsoft Edge routers. Both Fabrikam and Contoso will be required to announce their public IP addresses over this connection. Fabrikam and Contoso can setup a VPN tunnel over the MS Peering connection to provide a secure encrypted channel for data exchange. Azure DDoS per IP protection to be leveraged for protecting the public IP from DDoS attacks. Contoso does not need to have a subscription on Azure for this end to end connectivity.
Published on:
Learn moreRelated posts
Azure SDK Release (February 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (February 2026...
Recovering dropped tables in Azure Databricks with UNDROP TABLE
Oops, Dropped the Wrong Table? What now? We’ve all been there: you’re cleaning up some old stuff in Databricks, run a quick DROP TABLE… and su...
Azure Developer CLI (azd) – February 2026: JMESPath Queries & Deployment Slots
This post announces the February 2026 release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – February 2026: JM...
Improved Python (PyPi/uvx) support in Azure MCP Server
Azure MCP Server now offers first-class Python support via PyPI and uvx, making it easier than ever for Python developers to integrate Azure i...
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...