Connecting to Azure IoT Hub using IPv6 devices

Introduction
This article introduces an approach to connect IPv6 devices to Azure IoT Hub.
Azure IoT Hub
Azure IoT Hub is a crucial component in the Internet of Things (IoT) ecosystem, designed to facilitate seamless communication between IoT devices and the cloud. It plays an indispensable role in connecting, monitoring, and managing large networks of IoT devices, making it a cornerstone for businesses across various industries. Azure IoT Hub not only ensures secure and reliable device-to-cloud and cloud-to-device communication but also provides features like device provisioning, scalability, and integration with Azure services, making it a fundamental tool for harnessing the power of IoT. For more details, please follow – Azure - IoT Hub documentation
Emergence of IPv6 IoT Devices
With the rapid proliferation of IoT devices, the need for a larger address space and improved network capabilities has led to the emergence of IPv6-enabled IoT devices. IPv6 provides a vastly expanded address pool, which is essential for accommodating the growing number of devices in IoT ecosystems. As IoT continues to evolve and diversify, the adoption of IPv6 for IoT device connectivity is becoming increasingly prevalent, ensuring that devices can connect and communicate efficiently and securely in a connected world.
Challenges
At this moment, some of the Azure services including Azure IoT Hub does not natively support IPv6 device connectivity or communication. However, this can be achieved by deploying an IPv6-to-IPv4 gateway that can bridge the gap between IPv6-enabled devices and Azure IoT Hub, facilitating communication and data exchange.
In the architectural flow mentioned below, our Nginx act as a proxy stream server which translates the IPv6 address to IPv4 address.
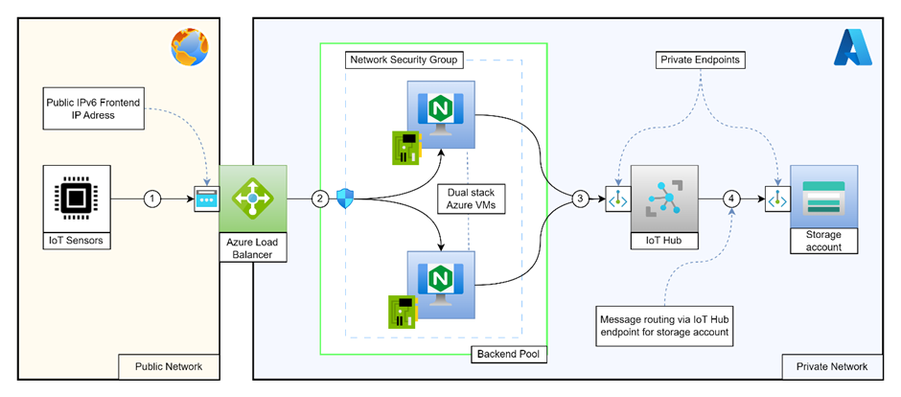
Architectural overview
Please note: The entire communication from device to IoT Hub happens over port 8883.
As shown in the above diagram, this setup involves below major Azure services:
- Public Azure load balancer with IPv6 frontend IP.
- Dual stack (IPv4 & IPv6 enabled) virtual machines as a load balancer’s backend.
- Nginx running as a streaming server on the virtual machines.
- IoT Hub enabled with private endpoints.
- Azure storage account enabled with private endpoints.
Resource deployment and configuration
Dual stack NIC
Dual stack network virtual machine
Standard SKU public IPv6 IP
Public Azure load balancer
For more details, please follow – Azure - Deploy an IPv6 dual stack application
Setting up Nginx stream server
Installing Nginx
Please note: We have used the Ubuntu, commands may be vary depending upon the OS flavour.
Configuring Nginx
Edit Nginx configuration:
Paste the following block:
Test the Nginx configuration:
Nginx reload for the latest configuration:
Verify the listening ports:
NSG configuration
Since the communication happens via Azure load balancer which is a layer 4 load balancer, the traffic initiated by IPv6 devices is forwarded as it is to VM by load balancer keeping the session intact.
Hence, we have to allow the traffic for devices on the NSG level. For more details, please follow – Azure - Create, change, or delete a network security group
Sample NSG rule
|
NSG rule parameter |
NSG rule value |
|
Source |
IP Addresses |
|
Source IP addresses/CIDR ranges |
Device IPv6 Address |
|
Source port range |
* |
|
Destination |
IP Addresses |
|
Destination IP addresses/CIDR ranges |
Nginx VM IPv6 Address |
|
Service |
Custom |
|
Destination port ranges |
8883 |
|
Protocol |
TCP |
|
Action |
Allow |
Route device messages to Azure storage
You can also leverage message routing feature of IoT Hub to route the messages to Azure storage account. Follow the document for the same – Azure - IoT Hub message routing
Validating entire setup
- Setup an Azure virtual machine with Public IPv6 address.
- Map the custom host entry for IoT Hub hostname:
- edit /etc/hosts
- add custom entry as mentioned below:
<lb_ipv6_fip> <iot_hub_hostname>
- Download the IoT Hub required certificates from – Azure Samples – IoT MQTT Sample - IoTHubRootCA
- Convert pem to crt file by using below command:
$ openssl x509 -outform der -in IoTHubRootCA.crt.pem -out IoTHubRootCA.crt - Trust the certificate:
$ cp IoTHubRootCA.crt /usr/local/share/ca-certificates/ $ sudo update-ca-certificates - Follow the guide to generate messages using sample code - Using MQTT to connect an IoT Hub with Python
- Install paho-mqtt client:
$ pip install paho-mqtt - Get the sample code from the same repo – Sample code
- Generate SAS token for your device by using following command:
$ az iot hub generate-sas-token -d <device_id> -n <hub_name> - Modify the sample code by adding below details:
- IoT Hub name
- Device ID
- SAS token
- Run the code i.e. python file.
- Observe the traffic in following ways:
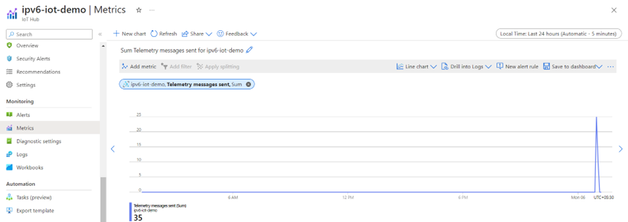
$ tail –f /var/log/nginx/access.log $ tcpdump port 8883 Azure > IoT Hub > Metrics > Select metric as telemetry message sent
Published on:
Learn moreRelated posts
What’s new with Azure Repos?
We thought it was a good time to check in and highlight some of the work happening in Azure Repos. In this post, we’ve covered several recent ...
Part 1: Building Your First Serverless HTTP API on Azure with Azure Functions & FastAPI
Introduction This post is Part 1 of the series Serverless Application Development with Azure Functions and Azure Cosmos DB, where we explore ...
Announcing GPT 5.2 Availability in Azure for U.S. Government Secret and Top Secret Clouds
Today, we are excited to announce that GPT-5.2, Azure OpenAI’s newest frontier reasoning model, is available in Microsoft Azure for U.S. Gover...