New developments in Microsoft Entra ID Protection

In the Microsoft Digital Defense Report 2023 (MDDR), we shared that on average, there are 11 token replay detections per 100,000 active users in Microsoft Entra ID each month. In addition, there are approximately 18,000 multifactor authentication (MFA) fatigue attempts observed per month.
The latest developments in Entra ID Protection help you reduce the risks of these attacks by making it easier to deploy risk policies, understand their impact, and protect your organization from emerging threats.
Here are the highlights:
- Deploying Entra ID Protection just became easier with Microsoft-managed policies in your environment and an impact analysis workbook.
- You can now investigate and remediate compromised users faster with help from Copilot and expansion of self-remediation to hybrid users.
- You can also fine-tune the Machine Learning (ML) algorithm by providing feedback and identify and block token theft and suspicious actions taken by an attacker within Entra ID with new detections.
Keep reading to learn more!
Deploy with ease and confidence
Microsoft managed policies and impact analysis workbook
Identity and access management is a huge responsibility requiring diligence and expertise. Between policies across identity, infrastructure, network, devices, apps, and data—and weighing the impact to end users and security—there’s a lot on your plate. To help with this, we have two exciting updates so you can get started with protecting your users faster and easier.
As we announced in November, Microsoft-managed Policies will enable some of our most valuable Conditional Access polices by default in select tenants, including requiring end users to perform MFA when we detect high risk to their sign in. This policy blocks attackers and allows your users to self-remediate their risk. We’re enabling Microsoft-managed policies slowly and deliberately to make sure we can incorporate your feedback and maximize value for you. Learn more about our approach to managed policies in our documentation.
We know that changes to how your users authenticate into resources require thoughtful consideration, and it’s helpful to know how the changes will affect your unique environment. Our new Impact analysis of risk-based access workbook will help you see the precise impact of turning on risk-based Conditional Access Policies so you can enable a new policy with confidence. The workbook uses historical sign-in data to allow you to immediately see the impact the policy would have had, with no report-only policy required. You can try out the new workbook here.
New dashboard generally available
In July, Entra ID Protection launched a new dashboard that presents risk insights for your tenant at a glance. We’re excited to announce today that this experience is now generally available and is the default landing page of ID Protection. The dashboard will give you a better understanding of your tenant’s security posture through key metrics, graphics, and recommended actions to improve your organization’s security posture.
In general availability, the attack counts in the Attacks Graphic are also now clickable, and you can easily navigate to them in the Risk Detections report to further investigate. The Risk Detections report has this new “Attack type” column, showing the primary attack type based on MITRE ATT&CK techniques for the detections. This further empowers your admins and SOC teams to understand the risks and take actions accordingly. See the risk detection to MIRTE ATT&CK type mapping in our documentation.

Investigate and remediate efficiently
On-premises password reset remediates user risk of compromise (general availability)
Our new feature to allow on-premises password changes to reset user risk is now generally available for Entra P1 and P2 customers. This feature allows hybrid customers to include their users in risk-based Conditional Access polices that require user password remediation. If you were waiting for GA to enable this feature, now is the time to do so to make user risk policies easier to manage. Visit Remediate risks and unblock users in Entra ID Protection to learn more.

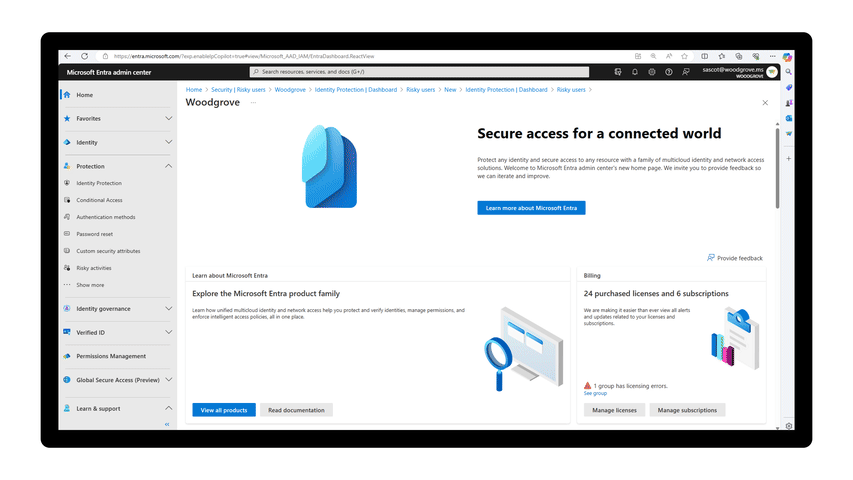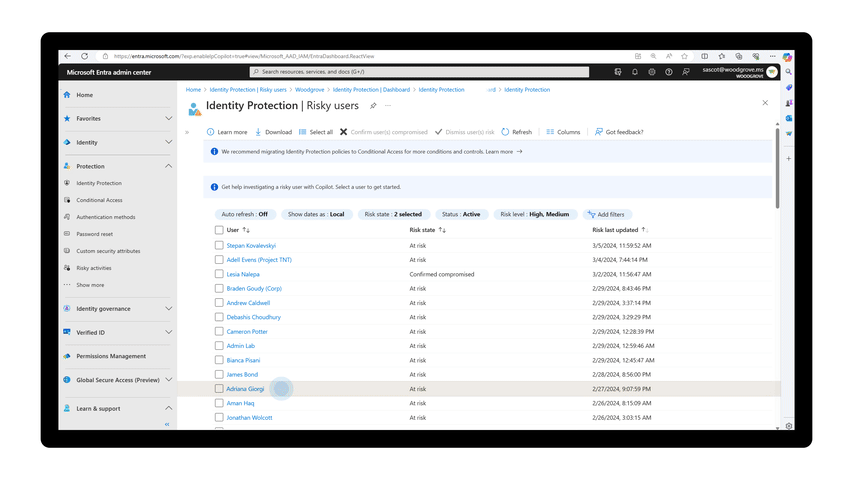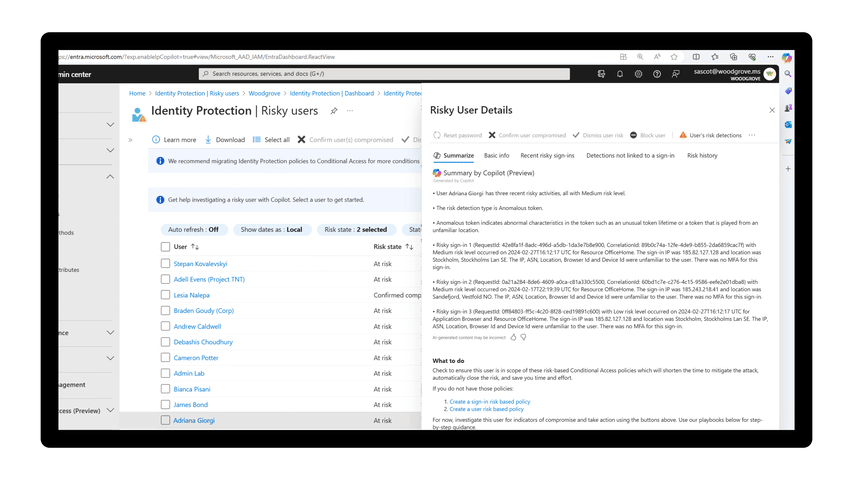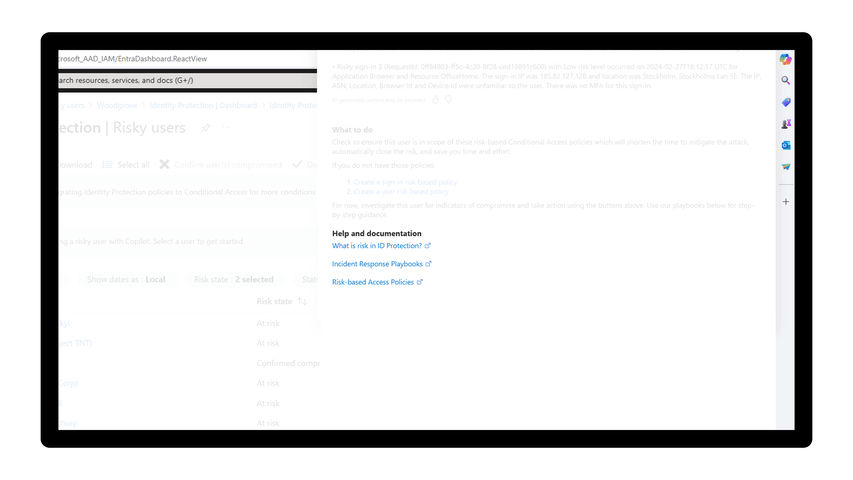
User Risk Investigation Copilot in public preview
Learning more about a user’s risk level and recommendations on how to mitigate a user’s risk is easier than ever with the introduction of the User Risk Investigation skill in Microsoft Entra, which is available in public preview as a part of Copilot for Security. This skill summarizes the risk history of the user, how to remediate risk for that user, and how to scale and automate response and remediation to identity threats.
Improved Threat Prevention and Remediation Capabilities
Over the past few months, multiple new detections have been introduced to Entra ID Protection that protect against new and emerging attack vectors, like anomalous graph usage, token theft, and attacker in the middle (AitM) attacks. In addition, hybrid tenants can now be confident that user risk is resolved when a password is reset on-premises, and all tenants can benefit from our new functionality that takes your feedback into account when determining if an event is risky.
Suspicious API traffic detection (general availability)
When entering an environment, attackers often search for information about users and tenant configuration to prepare for further exploitation. ID Protection will now change a user’s risk level if we observe them making an abnormally high number of calls to MS Graph and AAD Graph compared to that user’s baseline, which will help identify both compromised users and insider threats scavenging for intel.
Detecting token theft in real-time and post-breach
With token-based attacks on the rise, you need detections that help you identify and protect against this emerging threat. Two new detections in ID Protection help you do this. Our industry-first Real-time Anomalous Token Detection automatically disrupts token replay attacks in real-time when paired with a risk-based Conditional Access for sign-ins.
We have also built an offline detection that extends coverage of Microsoft 365 Defender’s Attacker in the Middle signals. This detection will flag the impacted user with high risk to prompt the configured Conditional Access user risk policy, allowing customers to confirm or dismiss the risk on the user. The session token is also revoked in cases where Continuous Access Evaluation is enabled.
You can learn more about our new detections at What are risk detections?
Admin feedback on detections trains our ML
We hold our detections in Entra ID to a very high standard, but occasionally we do issue a false positive detection. You can now help train our ML models by acting on risky sign-ins. You can confirm a sign-in as risky, safe, or dismiss risk. Each of these will send information back to our ML model and optimize future detections for your organization. You can learn more about giving Entra ID Protection risk feedback here.
We hope your organization can benefit from these new detections and features and that you will revisit the positive impact that risk-based Conditional Access can have on your organization's security.
Thanks, and let us know what you think!
Alex Weinert
Read more on this topic
- Microsoft Entra adds identity skills to Copilot for Security - Microsoft Community Hub
- Remediate User Risks in Microsoft Entra ID Protection Through On-premises Password Changes - Microsoft Community Hub
- Act now: Turn on or customize Microsoft-managed Conditional Access policies - Microsoft Community Hub
Learn more about Microsoft Entra
Prevent identity attacks, ensure least privilege access, unify access controls, and improve the experience for users with comprehensive identity and network access solutions across on-premises and clouds.
- Microsoft Entra News and Insights | Microsoft Security Blog
- Microsoft Entra blog | Tech Community
- Microsoft Entra documentation | Microsoft Learn
- Microsoft Entra discussions | Microsoft Community
Published on:
Learn more