Microsoft Entra Private Access: An Identity-Centric Zero Trust Network Access Solution

On July 11, 2023, we introduced Microsoft’s identity-centric security service edge (SSE) solution and two new services: Microsoft Entra Private Access and Microsoft Entra Internet Access, which are now in public preview. In this blog, we take a deeper look into Microsoft
Entra Private Access.
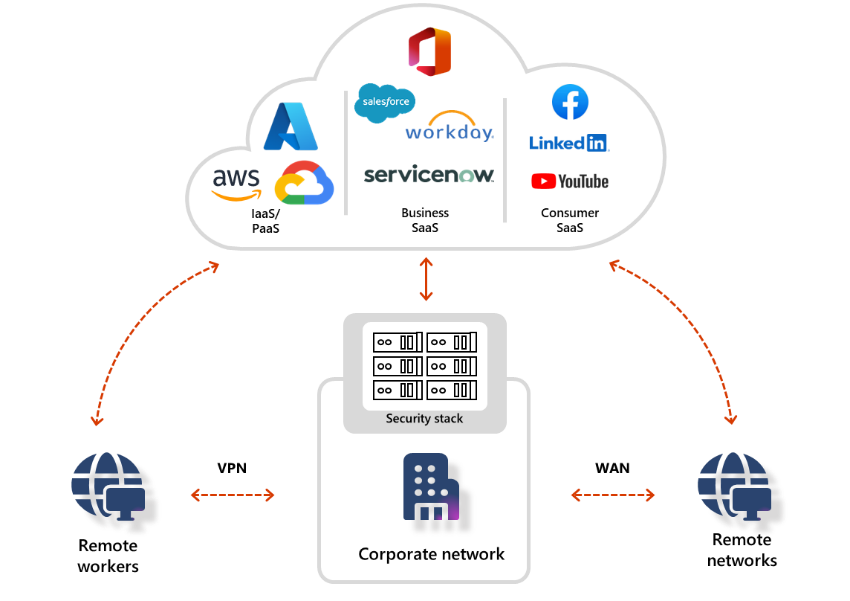
Microsoft Entra Private Access
Traditional network security approaches that use legacy VPNs simply cannot scale to modern demands. Once your remote users connect to your corporate network through VPN, they are granted excessive access to your entire network, all it takes is a single compromised user account, infected device, or open port for an attacker to gain entry, move laterally, and access your most critical assets.
Microsoft Entra Private Access, an identity-centric Zero Trust Network Access (ZTNA), reduces the operational complexity and cost of legacy VPNs, while eliminating excessive access and preventing lateral movement. It modernizes access to private applications and resources, helping users quickly and easily connect to private applications from any device and any network, whether they’re at home, remote, or in their corporate office.
What makes Private Access unique
As part of Microsoft’s SSE solution, Private Access is built on Zero Trust principles. It verifies every user and enforces least privilege, giving users access only to the private applications and resources they need. Private Access significantly expands Entra ID Application Proxy capabilities in Microsoft Entra to a complete ZTNA solution that shares the same connectors but offers so much more, it helps you simplify and secure access to any private resource on any port, and protocol. You can apply policies that enable secure, segmented, and granular access to all your private applications in your corporate network, on-premises, or in the cloud. For customers already using Application Proxy, they can seamlessly transition to Private Access – all existing use-cases and access to existing private web applications would continue to work with no disruption.
You can create and enforce per-app, least privilege access controls based on the granular Conditional Access policies that are enriched with context about users, devices, and their locations. You can also terminate ongoing sessions in response to anomalies or changes in user context or device health. For example, if a user connects from one part of the world and then immediately connects from another part of the world (what we call “impossible travel"), you can enforce re-authorization or step up to a stronger authentication method.
Private Access enables secure access to any application, on-premises or cloud-based, and it works across any port or protocol, including RDP, SSH, SMB, FTP, and anything else that uses TCP or UDP. In addition, you can enable single sign-on (SSO) using SAML or http headers or even legacy Kerberos authentication for both web and non-web applications, without making any changes to those applications.
With Private Access delivered from one of the largest global private networks, Microsoft global network, your private applications are not only more secure, but your employees can also access them faster compared to legacy VPNs. The unmatched scale and vast global network edge presence enables you to optimally connect your users and devices to private resources, especially those who work in a hybrid or remote work environment.

Private Access key capabilities
Microsoft Entra Private Access can help you enable secure access to all your private applications and resources. Key capabilities include:
Fast and easy migration from legacy VPNs with Quick Access. Replacing legacy VPNs with an identity-centric ZTNA minimizes the risk of implicit trust and lateral movement. Using Quick Access, you can easily configure broad private IP ranges and fully qualified domain names (FQDNs) to quickly enable identity-centric, Zero-Trust-based access to all private resources.

Enhanced identity-centric security controls for all private applications. With Private Access, you can create Conditional Access policies and multi-factor authentication (MFA) that require modern authentication for accessing any private application, even those using legacy protocols such as Kerberos and NT LAN Manager (NTLM). This brings policies based on the sensitivity of the application, level of user risk, network compliance, and so forth to legacy applications. For example, you can easily require multi-factor authentication (MFA) and device compliance checks for users trying to access remote desktop (RDP), secure shell (SSH) or SMB applications.

Automatic private application discovery and onboarding. You can discover private applications, including existing App Proxy private web applications, whether the applications are hosted locally in a private network, in an on-premises data center, or in the cloud. You can then onboard them to Microsoft Entra ID, group them, and define granular access policies.

Granular segmented application access. Instead of granting remote users access to your entire network, as traditional VPNs do, you can define granular segmented access policies for each application or group of applications based on user, device, or processes running on the endpoint.
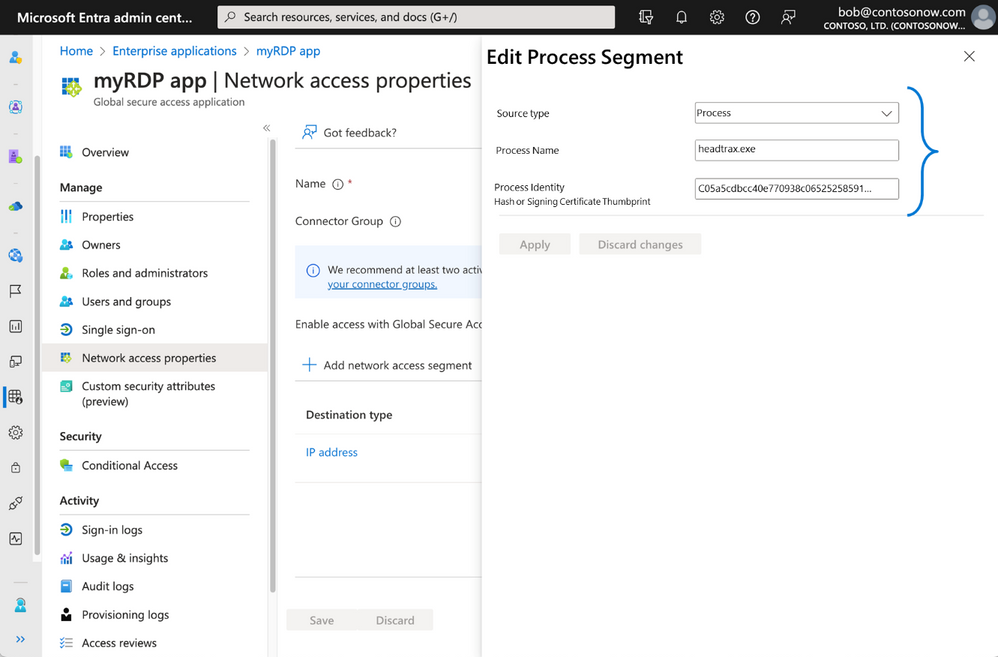
Intelligent local access. Employees need a consistent security posture whether they’re accessing private applications remotely or on-premises. The intelligent local access capability enables fast and seamless ZTNA for users, whether they’re within the corporate network or connecting remotely from anywhere outside corporate network boundaries. For example, a user while on the corporate network can connect to on-premises private applications such as RDP or SMB while CA policies such as MFA are still enforced, and application traffic remains local on the corporate network.

Getting started with Entra Private Access
Global Secure Access (preview) is the centralized location in the Microsoft Entra admin center where you can configure and manage Microsoft Entra Private Access. Remote workers don't need to use a VPN to access these resources if they have the Global Secure Access Client installed. The client quietly and seamlessly connects them with the resources they need. The most current version of the client can be downloaded from the Microsoft Entra admin center. You can install the client interactively, silently with the /quiet switch, or use mobile device management platforms like Microsoft Intune to deploy it to their devices.
QuickAccess makes it very easy to get started with a minimum configuration for Private Access, especially when you are planning to move from legacy VPN to ZTNA. After completing initial configurations, and once you deploy a connector agent on-premises, to enable quick access all you need to do is specify the IP address, IP address range, or FQDN and port number. You can then assign specific conditional access policies, which QuickAccess applies to ALL app segments you configured. For example, you can create a “myRDP app” and assign it an IP address-based app segment. You only need to provide a name for the private app, then select the connector you wish to use with the app, and then specify the IP address/range and port number. You can then access your destination by simply launching an RDP session from your remote client machine.

To learn about different use cases and scenarios, configuration prerequisites and how to enable secure access to your private network resources through the client, remote network connectivity, Quick Access, and more, go to the Global Secure Access documentation page.
You can learn more about Private Access in action via our on-demand Tech Accelerator product deep dive sessions.
Learn more about Microsoft’s SSE solution:
- Microsoft Entra expands into security service edge with two new offerings
- Microsoft Entra Private Access
- Microsoft Entra Internet Access
- Get started with Global Secure Access (preview) | Microsoft Learn
Learn more about Microsoft Entra:
- Related Articles:
- See recent Microsoft Entra blogs
- Dive into Microsoft Entra technical documentation
- Join the conversation on the Microsoft Entra discussion space and X
- Learn more about Microsoft Security
Published on:
Learn more