Consistently upgrade your server TLS protocol using Azure Arc and Automanage Machine Configuration
IT admins and operators have struggled to standardize secure communication protocols across server environments. With workloads distributed across hybrid, multicloud, and edge environments, setting and maintaining the desired communication protocol is a challenge.
The need to upgrade server TLS protocols is clear given the security vulnerabilities identified with TLS versions 1.0 and 1.1 Notable cryptographic threats impacting these previous TLS versions include BEAST, POODLE, and HEARTBLEED. As of 2020, TLS versions 1.0 and 1.1 are no longer supported. TLS 1.2 is required to maintain secure connections and offers higher performance on top of improved reliability.
Using Azure Automanage Machine Configuration, you can configure your secure communications protocol across servers running both within and beyond Azure. Through Azure Arc-enabled servers, you can extend Azure Policies to deploy and audit configurations in-guest through Azure Automanage Machine Configuration to non-Azure infrastructure. This is because the Connected Machine agent, powering Arc-enabled servers, has a built-in Machine Configuration component.
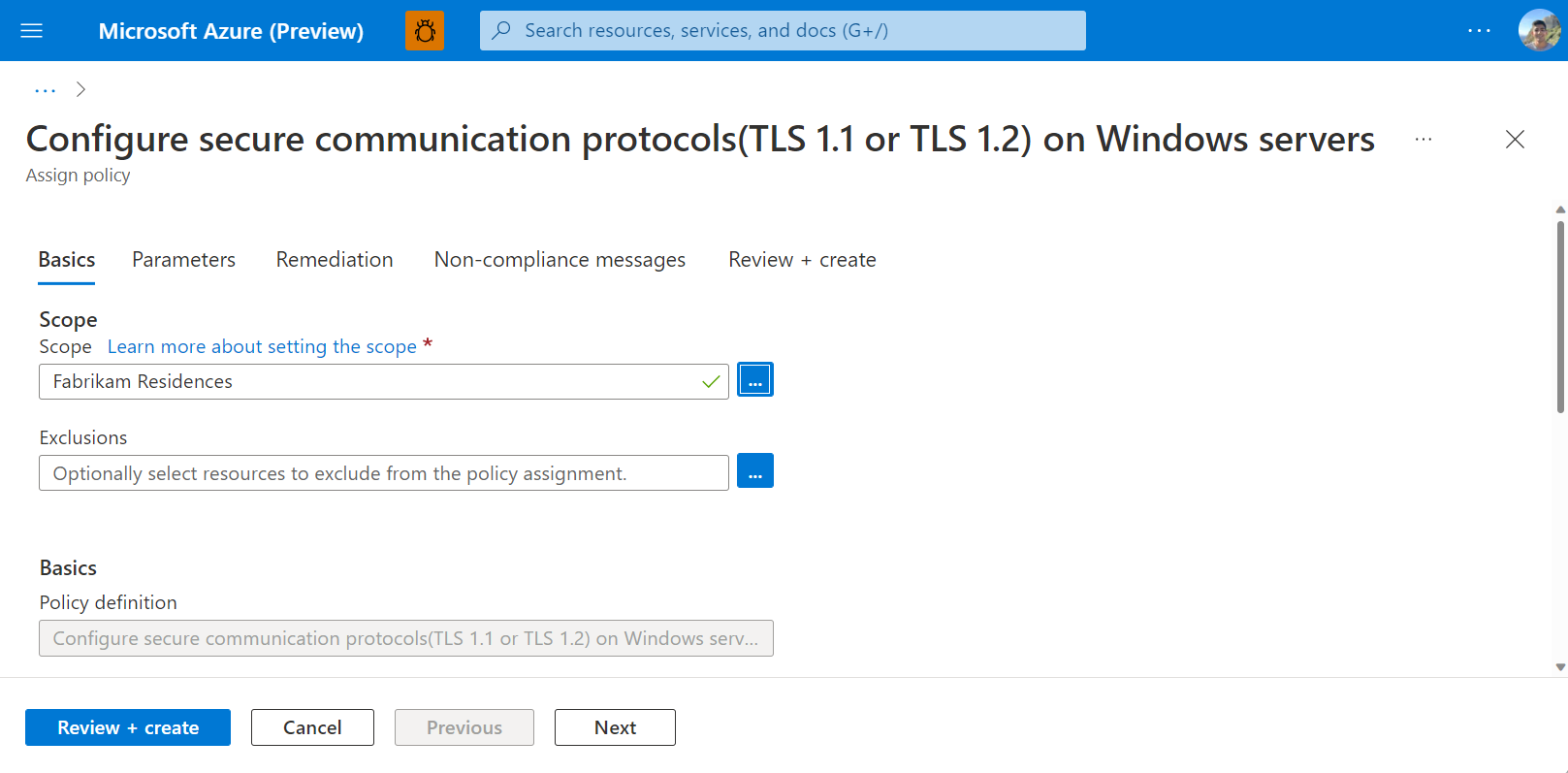
All you need to do is point and click in Azure Portal to get started with deploying this policy to your Arc-enabled servers. Simply, navigate to Azure Policy and select the built-in policy definition: Configure secure communication protocols (TLS 1.1 or TLS 1.2) on Windows servers. You can assign this policy’s scope to the subscription, resource group, or management group. Moreover, you can specify any resources for exclusion from the policy definition.
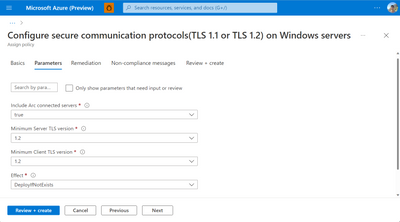
Next, you need to explicitly select to apply the policy to Arc-enabled servers. At this stage, you can also choose which communications protocol to apply. TLS 1.2 is set by default.
After assigning the configuration, simply navigate to the corresponding Arc-enabled servers in Azure portal. From the Guest Assignments tab, you can view the Guest Assignments applied to the Arc-enabled server and view the compliance status. By clicking into a guest assignment, you will be able to see the compliance status of your resources, as well as a deeper explanation describing the reasons for compliance or non-compliance.
Ensuring updated TLS protocol is just one application of Azure Automanage Machine Configuration to govern servers anywhere through Azure Arc. By authoring custom configurations using DSC, leveraging Azure Automanage Machine Best Practices, and applying additional Azure policies, you can extend Azure governance and compliance from cloud to edge. For more information on Automanage Machine Configuration, please see aka.ms/mc-docs.
Please note that the use of Automanage Machine Configuration on Azure Arc-enabled servers will incur a charge of $6/server/month. You only pay the charge once no matter how many machine configuration policies you apply to the server. If policies are assigned by Microsoft Defender for Servers Plan 2 or the policy is an Azure Security Benchmark, no charges will be incurred. Additionally, if Azure Change Tracking or Inventory Management are being used or the server is on Azure Stack HCI with Connected Machine agent version 1.13, no charges will be incurred.
Published on:
Learn moreRelated posts
Restricting PAT Creation in Azure DevOps Is Now in Preview
As organizations continue to strengthen their security posture, restricting usage of personal access tokens (PATs) has become a critical area ...
Building Copilot Studio agents with Azure AI Search and Mapped Citations
Integration with custom systems and enterprise use cases often requires more than the out-of-the-box Copilot Studio knowledge sources. Azure A...
Azure AI Foundry Voice Live API video
Azure SDK Release (May 2025)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (May 2025) app...