Enhancements to Microsoft Entra certificate-based authentication

At Ignite 2022, we announced the general availability of Microsoft Entra certificate-based authentication (CBA) as part of Microsoft’s commitment to Executive Order 14028, Improving the Nation’s Cybersecurity. Based on our experience working with government customers, PIV/CAC cards are the most common authentication method used within the federal government. While valuable for all customers, the ability to use X.509 certificate for authentication directly against Entra ID is particularly critical for federal government organizations using PIV/CAC cards and looking to easily comply with the Executive Order 14028 requirements as well as customers who want to migrate from a federated server like Active Directory Federated Server to Entra ID for CBA.
Since then, we’ve added many new features and enhancements, which made CBA available on all platforms, including mobile, with support for certificates on devices as well as external security keys like YubiKeys. Customers now have more control and flexibility to tailor authentication policies by certificate and resource type, as well as user group and select certificate strength for different users, use CBA with other methods for multi-factor or step-up authentication, and set high affinity (strong) binding for either the entire tenant or by user group.
Vimala Ranganathan, Product Manager on Microsoft Entra, will now talk about how these new features will help in your journey toward phishing-resistant MFA.
Thanks, and please let us know your thoughts!
Alex Weinert
--
Hello everyone,
I’m Vimala from the Microsoft Entra PM team, and I’m excited to walk you through all the new features and enhancements to CBA in detail.
CBA username bindings CBA added support for three remaining username bindings and is now at parity with on-premises Active Directory. The three bindings that are being added are:
- IssuerAndSerialNumber
- IssuerAndSubject
- Subject Only
The username binding policy allows admins to customize how Entra ID will match the certificate being presented by the user with their user account in Entra ID. By default, we map Principal Name in the subject Alternative Name (SAN) attribute of the certificate to UserPrincipalName in the user object. An admin can override the default and create a custom mapping.
More at Configure Username binding policy.
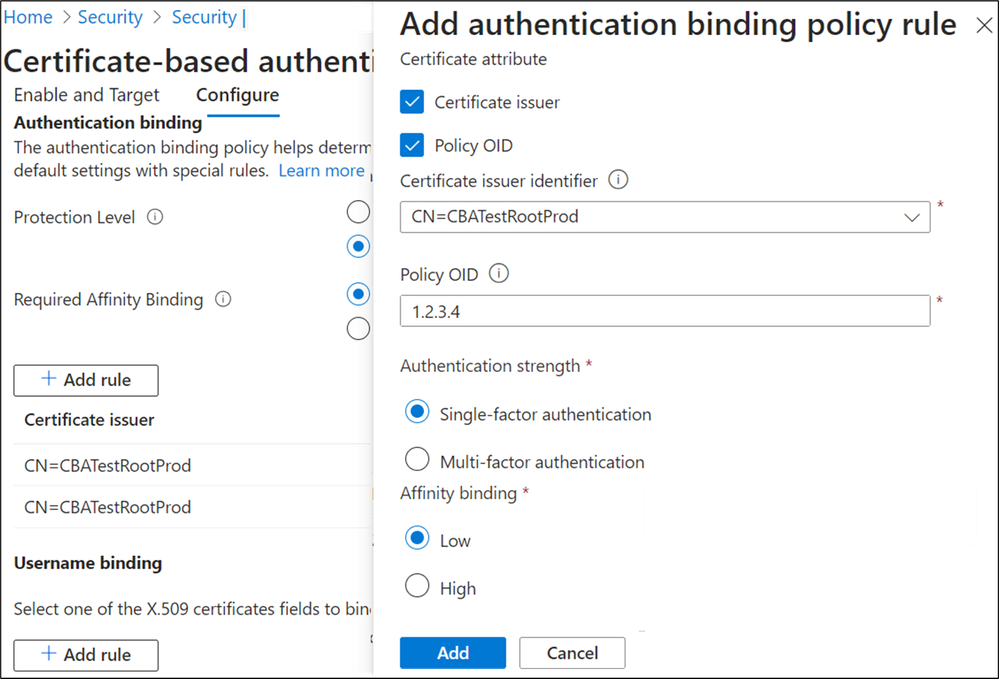
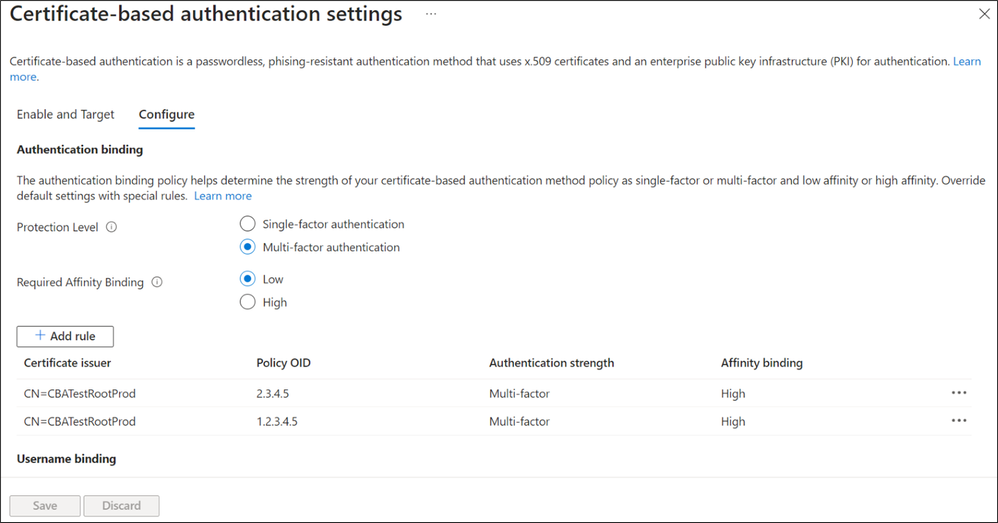
CBA Authentication policy rules help determine the strength of authentication as either single-factor or multi-factor. Unlike other authentication methods available in Entra ID, which are either always, CBA is capable of being either. We like to refer to this as CBA being a multi-factor capable authentication method, and the authentication policy rules allow the admin to configure protection levels to determine when Entra ID should consider a certificate to be single-factor or multi-factor. Multiple custom authentication binding rules can be created to assign default protection level for certificates based on the certificate attributes (Issuer or Policy OID or by combining the Issuer and OID).
More at Configure authentication binding policy.
CBA Affinity Binding refers to certificate attributes used for validating a certificate for user authentication. As we introduced earlier, there are several ways a certificate can be bound or matched to a user object. Some methods rely on properties of a user’s certificate that are easily reusable. This reusability characteristic is the key indicator to whether a particular user binding method is High (strong) or Low (weak) affinity. For example, implementing a user binding based on SAN Principal Name would be low affinity, whereas a user binding policy based on Issuer+SerialNumber would be high affinity. Entra ID allows admins to set affinity binding at tenant level, as well as create custom rules to use high affinity or low affinity mapping for covering many potential scenarios our customers have in use today.
More info at CBA Affinity Bindings.
CBA as second factor will now support CBA as one of the factors to get multifactor authentication (MFA) to access Entra resources. More info at MFA with CBA.
|
First factor |
Second factor |
MFA |
|
CBA with single-factor strength |
Passwordless Phone Sign in (PSI) |
Something you have + Something you have/know |
|
CBA with single-factor strength
|
FIDO 2 |
Something you have + Something you have/know |
|
Password |
CBA (single-factor or multi-factor strength) |
Something you know + Something you have |
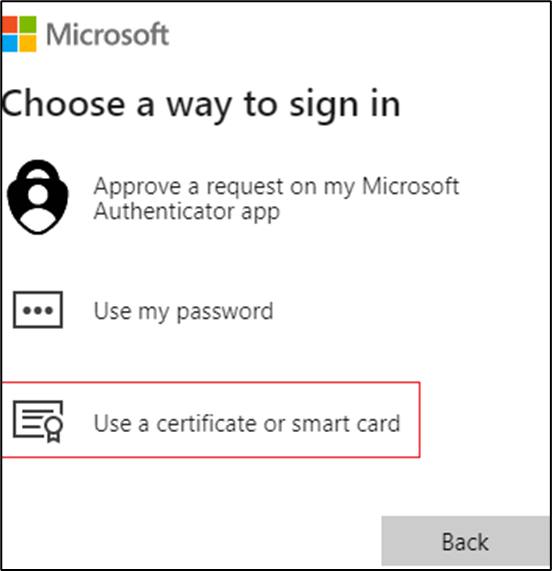
CBA as Most Recently Used (MRU) method is set once a user authenticates successfully using CBA, and the user's MRU authentication method is set to CBA. Next time, when the user enters their UPN and clicks Next, the user is taken to the CBA method directly and need not select ‘Use the certificate or smart card.’ To reset the MRU method, the user needs to cancel the certificate picker, click ‘Other ways to sign in,’ and select another method available to the user and authenticate successfully. More info at CBA as MRU.
Users on windows Hybrid and Entra-joined devices can sign into windows with their smart card and get a primary refresh token (PRT) to get Single Sign On (SSO) with Entra resources. More info at windows smartcard sign-in.
You can also learn more about Microsoft Entra CBA at http://aka.ms/aadcba and Microsoft’s commitment to Executive Order 14028.
What’s next
Keep your feedback coming at Azure Active Directory Community! We’re working diligently to bring more enhancements like the removal of limits on Certificate Revocation List (CRL), new certificate authority trust store, CBA support on the resource tenant for B2B external guest users, and iOS UX enhancements, to name some.
Learn more about Microsoft Entra:
- See recent Microsoft Entra blogs
- Dive into Microsoft Entra technical documentation
- Learn more at Azure Active Directory (Azure AD) rename to Microsoft Entra ID
- Share product suggestions on the Entra ID forum
- Join the conversation on the Microsoft Entra discussion space and Twitter
- Learn more about Microsoft Security
Published on:
Learn more