Exploring Azure Firewall's Threat Protection
In this blog post, I will discuss the various threat protection capabilities that customers are leveraging to safeguard their workload deployments in Azure using Azure Firewall. Azure Firewall is a cloud-native firewall-as-a-service solution that empowers customers to centrally govern and log all their traffic flows using a DevOps approach. This service offers both application and network-level filtering rules, and it seamlessly integrates with the Microsoft Threat Intelligence feed to filter known malicious IP addresses and domains. Moreover, Azure Firewall boasts high availability and comes equipped with built-in auto scaling.
While it may appear straightforward, the first line of defense can be effectively achieved through access restriction. Customers are adopting two simple approaches to bolster their security posture:
- Egress Traffic Blocking: This method involves blocking all egress traffic to the internet and only allowing access to specific domains that are deemed safe and necessary.
- Suspicious Site Blocking: Alternatively, customers can choose to allow all egress traffic to the internet while implementing measures to block access to suspicious sites. This approach mitigates potential risks associated with accessing untrustworthy destinations.
URL (Uniform Resource Locator) and FQDN (Fully Qualified Domain Name) filtering play a crucial role in analyzing web traffic and deciding whether to allow or block access based on the URLs accessed by applications. This control mechanism is critical for safeguarding cloud workloads and data from malicious activities such as command-and-control connections and data exfiltration. Notably, URL filtering is particularly essential for cloud deployments, especially when protecting Virtual Desktop Infrastructure (VDI) environments.
It's important to differentiate URL filtering from domain or FQDN filtering. FQDN filtering primarily focuses on the destination domain, while URL filtering takes into account the complete URL. Let's consider an example to illustrate this distinction. Suppose we examine the domain linkedIn.com. In this case, filtering based solely on FQDN would not suffice because distinguishing between different URLs within the domain (e.g., linkedIn.com/LegitUser vs. LinkedIn.com/MaliciousUser) becomes a critical detail when implementing a secure egress strategy. Consequently, filtering based on the URL becomes necessary.
URL filtering also plays a crucial role in preventing attackers from establishing connections to their command-and-control (C2) servers or exfiltrating data to sites under their control. Moreover, organizations often need to adhere to security compliance standards and guidelines, such as PCI DSS and SOC2 Type2, which require the implementation of URL filtering as an essential security measure.
TLS decryption is a prerequisite for implementing URL filtering since the URL is part of TLS-encrypted HTTPS traffic. And since the percentage of the encrypted web traffic is in constant incline, it is a mandatory requirement to enable TLS inspection in your Azure Firewall deployment.
The need for Threat Intelligence
Now that we understand the significance of URL filtering and the need for TLS inspection to implement it on encrypted traffic, how can we distinguish between safe and suspicious domains and URLs?
Threat intelligence is our second ring of defense. It refers to the information an organization utilizes to comprehend the threats that have targeted, are targeting, or will target the organization. This valuable information aids in preparation, prevention, and identification of cyber threats aiming to exploit valuable resources. Azure Firewall leverages threat intelligence from the Microsoft Threat Intelligence feed, which encompasses multiple sources, including the Microsoft Cyber Security team.
By enabling threat intelligence-based filtering on your firewall, you can receive alerts and block traffic associated with known malicious IP addresses and fully qualified domain names (FQDNs). With recent enhancements, Azure Firewall Threat Intelligence offers even more fine-grained filtering capabilities, including identification of malicious URLs within specific domains. Consequently, while customers may have access to a certain domain, any specific URL within that domain identified as malicious will be denied by Azure Firewall.
To achieve optimal granularity, customers have the option to utilize a Threat Intelligence allow list, which allows trusted FQDNs, IP addresses, ranges, and subnets to bypass threat intelligence validation.
In the case of HTTPS traffic, where URLs are encrypted, Azure Firewall Premium's TLS inspection comes into play. This feature enables URL-based threat intelligence analysis for encrypted traffic, ensuring comprehensive protection.
Over the past year, we observed a consistent upward trend in the number of web requests being blocked as a result of Threat Intelligence filtering. On an average daily basis, we are witnessing over 20 million blocked requests to suspicious sites.
Security Risks in Azure Cloud Workloads
Unlike Threat Intel and URL/FQDN filtering which are mainly egress oriented, a third ring of defense that Azure Firewall offers is intrusion detection and prevention system (IDPS) which protect against both ingress and egress threats.
IDPS is a security technology designed to detect and prevent unauthorized activities and potential threats within a computer network or system.
An IDPS is typically comprised of two main components:
- Intrusion Detection System (IDS): This component monitors network traffic, system logs, and other sources of information to identify potential security breaches or malicious activities. It analyzes network packets, system events, and behavior patterns to detect signs of intrusion or suspicious behavior.
- Intrusion Prevention System (IPS): This component goes a step further than IDS by actively taking measures to prevent identified threats. It can automatically block or mitigate malicious network traffic or activities to protect the network or system from attacks.
The main functions of IDPS include:
- Monitoring and Detection: The IDPS constantly scans network traffic, searching for known attack patterns or abnormal behavior that could indicate an intrusion or security breach.
- Alerting and Reporting: When the IDPS detects a potential threat, it generates alerts or notifications to notify security personnel. It provides detailed information about the detected event, including the type of attack and severity level.
- Response and Prevention: An IDPS takes action to mitigate or prevent attacks by blocking network traffic.
- Logging and Analysis: The system maintains logs and records of security events, which can be used for post-incident analysis, forensic investigations, and compliance requirements.
Azure Firewall IDPS plays a crucial role in enhancing the security posture of networks and systems by detecting and preventing unauthorized activities, reducing the risk of data breaches, and helping organizations respond effectively to security incidents.
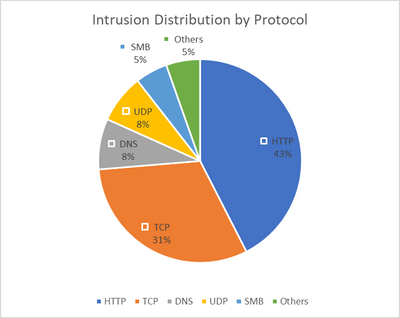
In the last year, we noticed a notable surge in network and application layer attacks. Using Azure Firewall's IDPS, we were able to handle an average of over 5 million daily threat attempts.
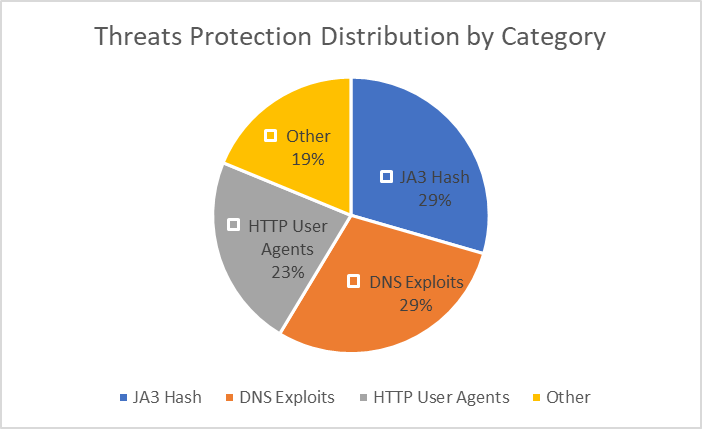
Over the past twelve months, the three main threats we've been preventing are malicious SSL certificates that use JA3 hashes, vulnerabilities in the Domain Name System (including DNS tunneling), and specific user agents associated with known malicious activity on the web.
When customizing their firewall, customers can specify which threats should be mitigated and which only require detection and alerting. We've observed that alerted threats are distributed in different way, and that most such threats are caused by policy violations within an organization, as well as information events at the audit level that can be useful for identifying interesting activity.
Although network layer attacks represent a significant portion of the pie chart, the majority of threats occur at Layer 7. Therefore, it's essential to use TLS inspection to protect against attackers who increasingly use SSL/TLS to keep their malicious activities hidden.
Conclusion
Azure Firewall offers robust threat protection capabilities for safeguarding workload deployments in Microsoft Azure. Customers can leverage its application and network-level filtering rules and its integration with Microsoft Threat Intelligence feed. URL and FQDN filtering play a crucial role in analyzing web traffic, and threat intelligence is essential for distinguishing between safe and suspicious domains and URLs. URL filtering is a vital component of a robust security strategy as it enables organizations to prevent unauthorized connections within their network and prevent data exfiltration attempts by threat actors. By leveraging TLS decryption, organizations can enhance their defenses and fortify their overall security posture.
Azure Firewall's IDPS, comprising IDS and IPS components, provides an additional layer of defense by monitoring network traffic, detecting potential breaches, and taking preventive measures. Overall, Azure Firewall offers a comprehensive set of features to enhance security and protect against various threats in Azure cloud workloads, allowing customers to improve their security posture and become better protected against future threats.
Published on:
Learn moreRelated posts
Improved Python (PyPi/uvx) support in Azure MCP Server
Azure MCP Server now offers first-class Python support via PyPI and uvx, making it easier than ever for Python developers to integrate Azure i...
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...
Azure Function to scrape Yahoo data and store it in SharePoint
A couple of weeks ago, I learned about an AI Agent from this Microsoft DevBlogs, which mainly talks about building an AI Agent on top of Copil...
Maximize Azure Cosmos DB Performance with Azure Advisor Recommendations
In the first post of this series, we introduced how Azure Advisor helps Azure Cosmos DB users uncover opportunities to optimize efficiency and...