Part 2 - Managing Azure Firewall Network Rules with Illumination
Written in collaboration between @andrewmathu and @gusmodena
Introduction
The second tutorial in this 2-part blog series about Illumio for Microsoft Azure Firewall is going to explore how to use Illumination to visualize and manage the network traffic and security policies of your environment. Illumination provides a unique new way to reveal the traffic flows in your network and to help you configure policies to secure your applications.
Before you deep dive into this blog post, we recommend you read part 1 of the blog series: Part 1 - Managing Network Rules by using Azure Tags with Illumio for Microsoft Azure Firewall - Microsoft Community Hub
What is Illumination?
Illumination is a graphical tool that maps the connections and flows between your workloads, helping you to understand the traffic patterns and dependencies of your applications, and to design and test security policies that control the access between your workloads. Illumination uses a color-coded system to indicate whether the traffic is allowed or blocked by your policy, and whether the policy is active or in draft.
Illumination has different levels of detail - you can zoom in and out to see the traffic at the location, environment, application and role levels, or present a view based on specific tags associated with your Azure resources. You can also filter the traffic by labels, policy state, services, or time range. With Illumination, you can discover and group your workloads, write, and test rules for them, and enforce them with confidence.
Getting Started
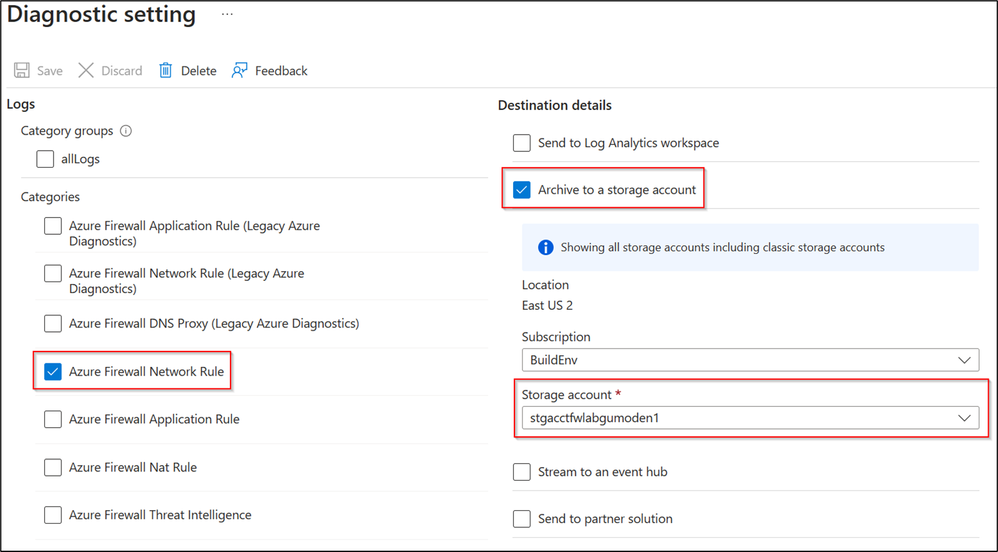
Illumination relies on the new Azure Firewall Network logs category (Azure Firewall Network Rule) stored in a storage account to identify the network traffic and create the mappings. Check the pre-requisites below to configure the Diagnostic setting.
Pre-requisites
- Storage Account
- AZFW Diagnostic Setting
- Category: Azure Firewall Network Rule
- Destination Detail: Archive to a storage account
Also, as discussed in Part 1 of the blog series, you will need to ensure that the App Registration created for Illumio has the following permissions:
- Reader
- Storage Blob Data Reader
- Illumio Firewall Administrator-“SubId”
Exploring Illumination
Once you have gone through all the configurations discussed previously, you will be able to start using Illumination. You can use Illumination to visualize allowed traffic flows between NSGs, VMs and Firewalls in your Azure subscription. The Illumination map visualizes current VMs and traffic flowing through a selected Illumio-managed Azure Firewall along with the connections your rules allow or deny. VMs are represented by the Illumio labels that you assigned in the Label Mapping step. Notice how the labels make it easy to understand what is occurring in your subscription so that you can write effective rules. In a typical iterative approach, you would:
- Analyze current flows and connections.
- Understand the impact your rules will have when enforced.
- Discover details you may have missed or did not know about.
- Iterate as necessary by adding, removing, or tuning rules in the Rule Writing tab and then returning to Illumination.
Below you will find an example describing how to use Illumination to visualize the impact these rules have on the network.
- In Illumio for Microsoft Azure Firewall, click the Illumination tab.
- You can use the filters “Source”, “Destination” or “Service” to narrow the view to specific workloads.
- Notice that Map is the default view, as shown in the image below. You can also use Table and Mash views if desired.
- Click “Run”
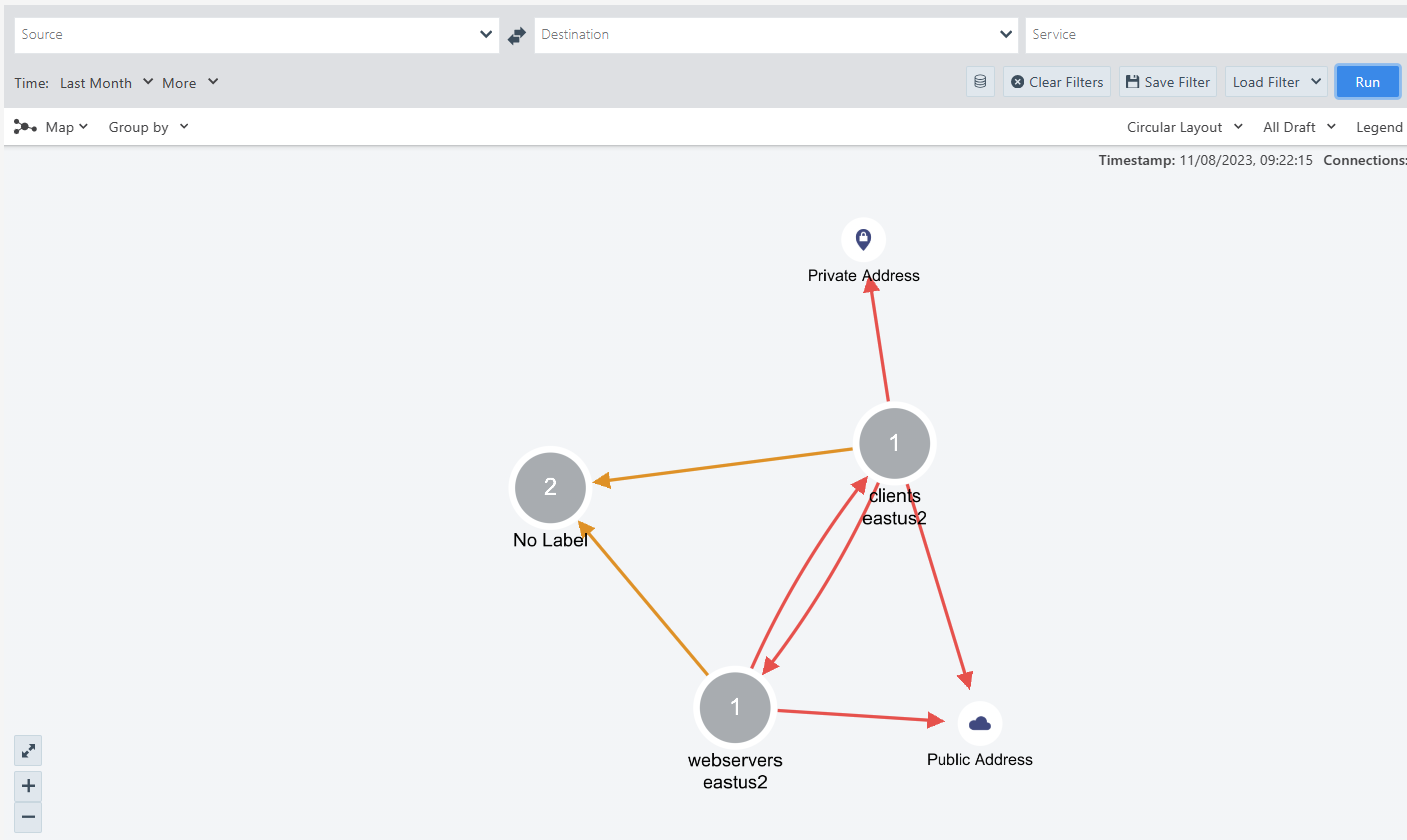
- Notice that while you are in Map view, traffic links are presented as colored arrows.
- Green arrows show the traffic that is either currently allowed or would be allowed if your rules were enforced.
- Red arrows show the traffic that is either currently blocked or would be blocked if your rules were enforced.
- Orange arrows show the traffic that is simulated blocked due to no rule.
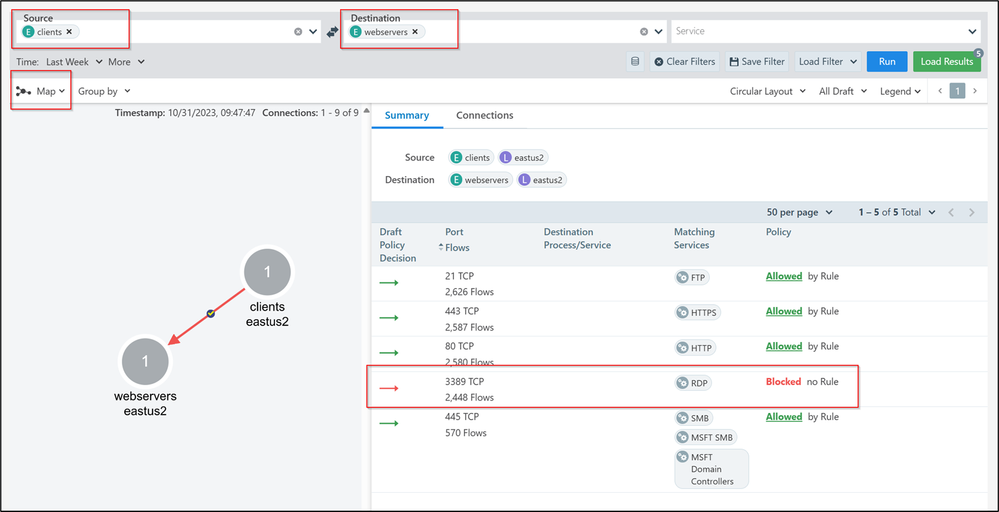
In the screenshot above we are filtering the traffic from “clients” to “webservers”, over the last week. When we click run, Illumination checks the Azure Firewall logs stored in the storage account to identify the flows and build the map. Once the map is displayed, you will see all the resources included in the Azure Tag environment with the value “clients” and “webservers”. In our example we only have 1 VM in each group.
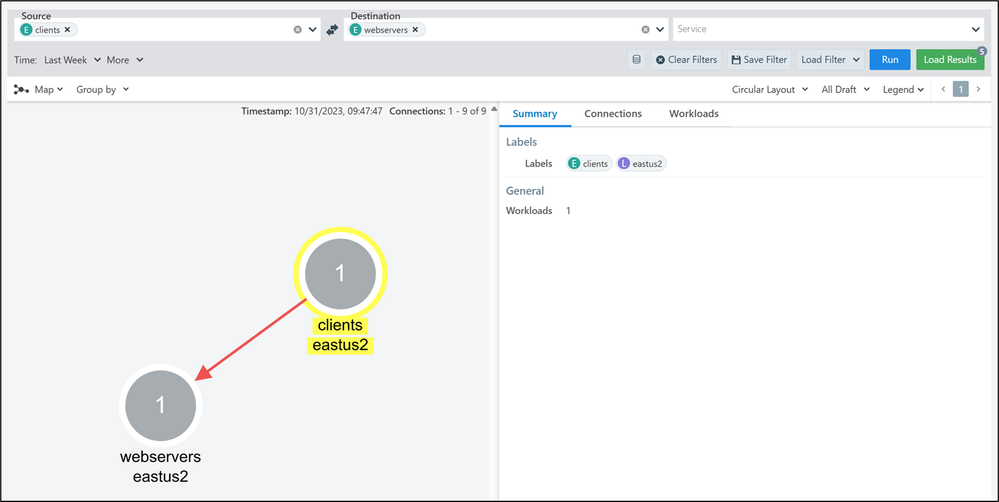
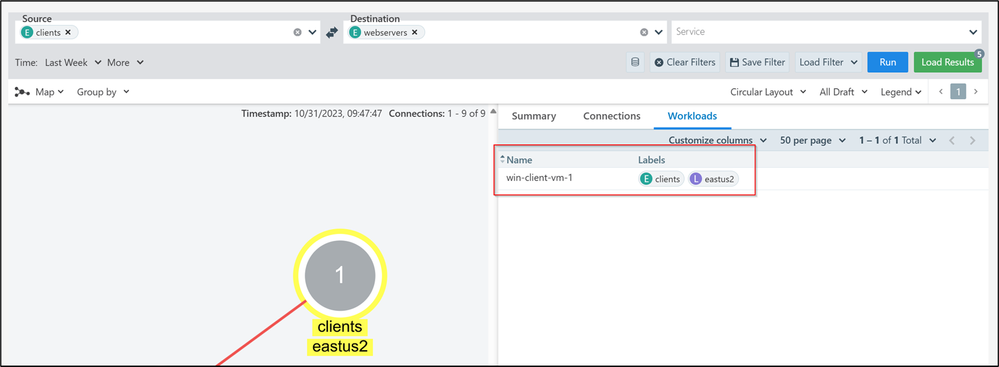
Clicking on the group clients, a new tab will open on the right side of the screen with three tabs (Summary, Connections and Workloads). In Summary you will find the labels and the total number of workloads within the group.
In the Connections tab you will find an aggregate view of all the flows identified from the logs. In the example below you can see that we have Allowed and Blocked traffic flows.
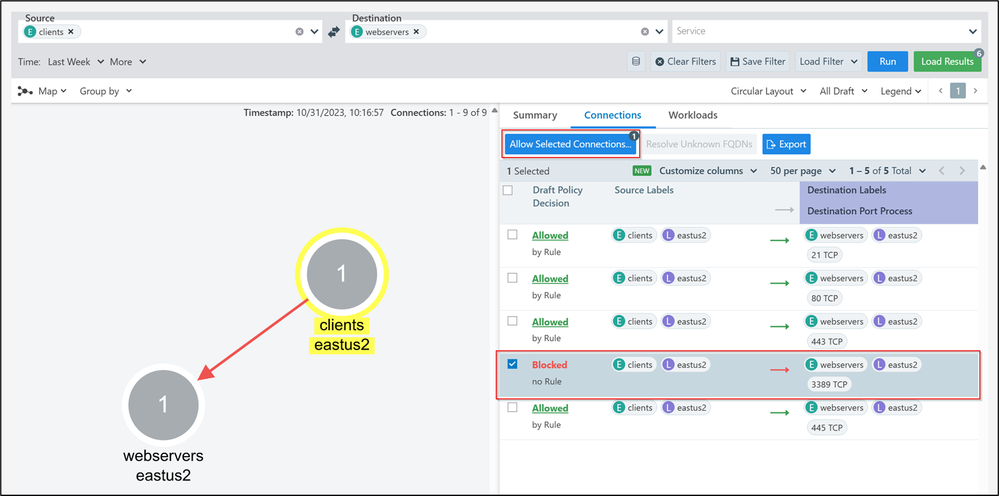
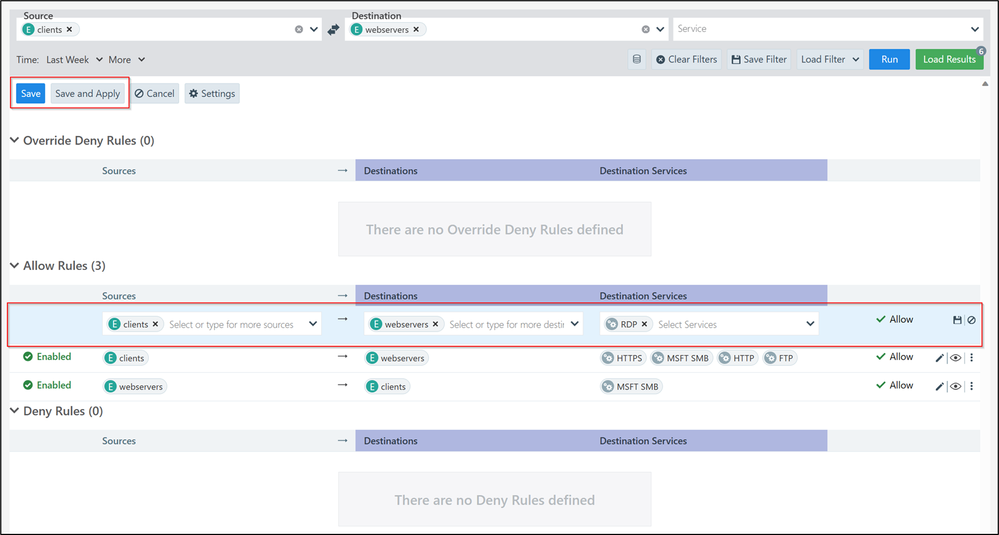
In case you want to allow the traffic from clients to webservers on port 3389, you will select the checkbox of the Blocked flow and then click on “Allow Selected Connections”. Then you will have the option to make some changes to the rules before saving and applying.
Once you click Save and Apply it will be added to your rule writing and then deployed to your Azure Firewall Policy after a few minutes.
If you want to know the resources identified within the clients group, you can move to the Workloads tab to find the name of the virtual machines labeled as clients.
With Illumination, you obtain a powerful tool that lets you see and understand the traffic flows and dependencies across your Azure resources and applications. You can also apply Zero Trust principles by creating granular and dynamic policies that segment and isolate your workloads. Moreover, you can simplify the configuration and maintenance of your Azure Firewall with Illumio’s intuitive interface.
Conclusion
The adoption of Illumio for Microsoft Azure Firewall signifies a pivotal moment in the ongoing battle to secure our digital environments. As the threat landscape continues to evolve, it is crucial to stay ahead of the curve, and these innovations offer a compelling path forward. By simplifying rule management, enhancing visibility, and providing scalability, Illumio for Microsoft Azure Firewall empowers organizations to navigate the complex world of IT infrastructure security with confidence and agility. It is time to embrace the future of firewall rule management, and the future is bright with solutions like this at our disposal.
Learn More
- Part 1 – Managing Network Rules by using Azure Tags with Illumio for Microsoft Azure Firewall: Part 1 - Managing Network Rules by using Azure Tags with Illumio for Microsoft Azure Firewall - Microsoft Community Hub
- What is Azure Firewall: What is Azure Firewall? | Microsoft Learn
- Azure Firewall Policy Overview: Azure Firewall Manager policy overview | Microsoft Learn
- IP Groups in Azure Firewall: IP Groups in Azure Firewall | Microsoft Learn
- Azure Tags: Tag resources, resource groups, and subscriptions for logical organization - Azure Resource Manager ...
- Illumio for Microsoft Azure Firewall: Illumio for Microsoft Azure Firewall | Illumio
- How Microsoft and Illumio are reinventing firewall security for the cloud era: How Microsoft and Illumio are reinventing firewall security for the cloud era | VentureBeat
Published on:
Learn moreRelated posts
Extending Regular Expressions (Regex) Support on Azure SQL Managed Instance (MI)
We are happy to announce the Private Preview of Regular Expressions (Regex) support on Azure SQL Managed Instance (MI). This new feature bring...
Shield your Copilot with Azure AI
Azure Confidential Clean Rooms demonstration
Final Days for the MSOnline and AzureAD PowerShell Modules
After many twists and turns since August 2021, the MSOnline module retirement will happen in April 2025. The AzureAD module will then retire i...
Join the Conversation: Call for Proposals for Azure Cosmos DB Conf 2025!
Are you passionate about Azure Cosmos DB? Do you have insights, experiences, or innovations that the developer community would love to hear? N...
High Performance Computing in Azure - with Mark Russinovich
See the latest innovations in silicon design from AMD with new system-on-a-chip high bandwidth memory breakthroughs with up to 7 terabytes of ...