Announcing Trusted Launch as default in Azure Portal
Malware attacks continue to adversely impact organizations across all industry verticals (2021: 5.4 billion, 2022: ~5.6 billion). Malware is a continuously evolving threat that requires organizations to take proper measures to keep IT infrastructure safe. Securing IT infrastructure is a top priority for organizations to prevent disruption to their business. Industry security best practices call for layered defense-in-depth techniques to thwart malware. Protecting IT infrastructure across the stack requires a collection of holistic security strategies that vary in operational complexity.
Azure recommends that organizations adopt ‘Secure-by-default’ mindset to ensure that their cloud infrastructure has a strong security posture before operationalization. To support this mindset, Azure is committed to providing industry-leading security solutions. One of the solutions Azure offers is Trusted Launch Virtual Machines (VMs). Trusted Launch protects VMs through Secure boot, measured boot, vTPM and integrity monitoring capabilities. It provides foundational security for your Azure VM to enable your workloads to run on a hardened VM. Trusted Launch security features allow administrators to deploy virtual machines with verified & signed bootloaders, and OS (operating systems) kernels. Integration with Microsoft Defender for Cloud provides continuous insights into VM configuration & health state. security capabilities are available to you at no extra cost. These VMs have been generally available since Nov 2021.
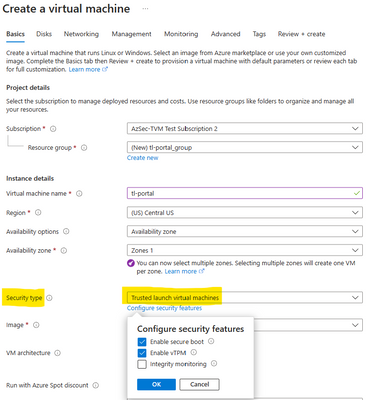
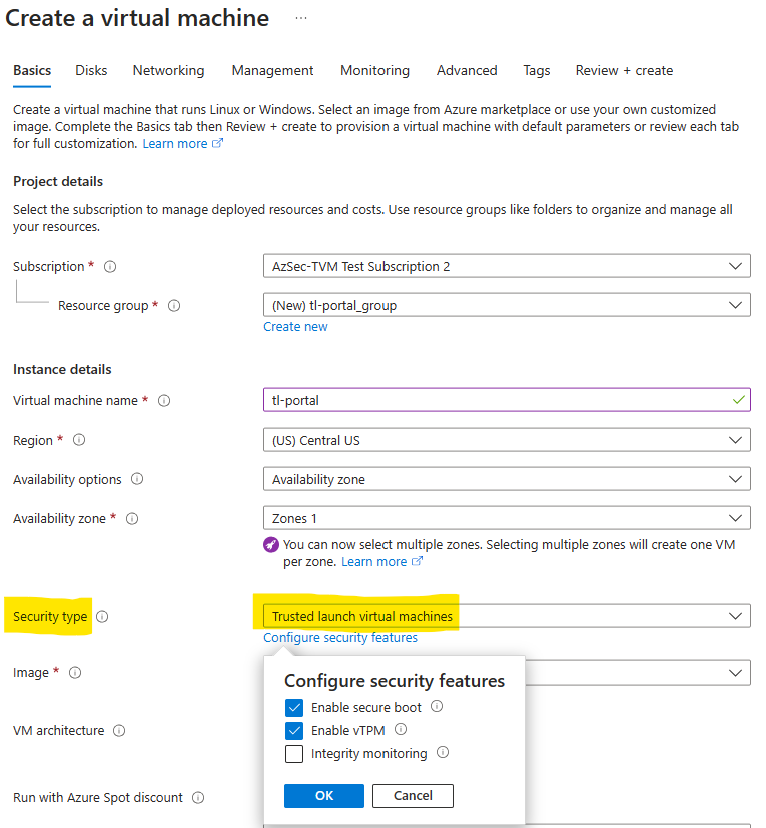
In the spirit of ‘Secure-by-default’, today, we are announcing Trusted Launch virtual machines as default in Azure Portal. With Trusted Launch as default, the security settings in Portal are pre-set for you and no special attention is required. Any new VM created on Azure Portal will have Trusted Launch capabilities turned on by default.
How to create a Trusted Launch Virtual Machine
To create a Trusted Launch VM, login to and navigate to ‘Virtual Machines’ under Azure services. In the Create a virtual machine’ page, Trusted Launch and associated properties (secure boot, vTPM, integrity monitoring) are already by default to ensure Virtual Machines always have the foundational security posture Trusted Launch VM enables.
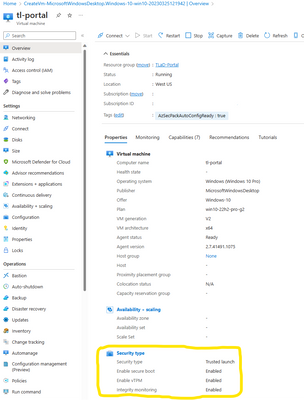
Once the VM is created, you can verify Trusted Launch properties on the VM overview page. This ensures the VM is a Trusted Launch VM and protects against rootkits and bootkits.

“Trusted Launch is essential for us to provide Windows 11 VMs and to be able to migrate existing Windows 10 machines to Windows 11. The additional benefit is a more enhanced security by providing Secure Boot and vTPM, which protects keys, certificates, and secrets. This leads to an improved trust of the Trusted Launch enabled VM”
- Thorsten Lambrecht, Architect Virtual Workplace Services, Deutsche Bahn AG
With Trusted Launch-as-default, Azure Portal organizations can now:
- Improve foundational security of virtual machines by booting to a defined and trusted state.
- Protect against persistent malware such as boot kits and rootkits that are so sophisticated that they can run with the same kernel-mode privileges as the operating system they infect.
- Enable Credential guard (isolate & protect secrets, such as user passwords, and prevent compromise of the user’s credentials. Also protects derived domain credentials) backed by secure boot, and Virtualization based security and vTPM, pre-requisites for domain controllers.
- Gain continuous insights into your virtual machines for health state and boot chain integrity, plus remediate attestation (Microsoft Azure Attestation) failures via Microsoft Defender for Cloud.
- Ensure that your Windows 11 virtual machines meet Windows 11 pre-requisites by enabling UEFI (Unified Extensible Firmware Interface), vTPM and including secure boot to prevent lower layer malware.
For details on region presence, compatible OS images, VM sizes, and feature parity, refer to Trusted Launch documentation.
Further Reading
Published on:
Learn moreRelated posts
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...
General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB
Title: General Availability for Data API in vCore-based Azure Cosmos DB for MongoDB We’re excited to announce the general availability of the ...
Microsoft Power Pages: The authentication key for your portal will expire
I saw the below Notification today, while I was working on the Portal requirements. Notification:The authentication key for your portal will e...