Azure WAF Post Deployment Check - Best Practices

Written in collaboration with @tobiotolorin
Introduction
Customers using Azure Web Application Firewall (WAF) are often interested in post-deployment steps to ensure they have the best security practices in place in their environment. Although deploying a WAF will protect your web applications from common attacks and improve performance by filtering out malicious traffic, it is recommended to take post-deployment actions to ensure the security and reliability of your web applications. As a post-deployment check, you can ensure the following steps are performed for your web application within your application delivery platform, Azure Application Gateway or Azure. Here are recommended measures for enhancing the security posture of the application situated at the backend of your application delivery platform through the utilization of Azure WAF.
Best Practices
Monitoring Security Events
A key and principal task after deploying a new security system like Azure WAF is to ensure proper monitoring of security events is in place. Monitoring helps you detect and prevent malicious attacks on your web application, such as SQL injections, cross-site scripting, or denial-of-service. It can also assist in identifying and fixing vulnerabilities in your web application code or configuration. Lastly, it helps you comply with security standards and regulations, such as PCI DSS, HIPAA, or GDPR, by providing evidence of your security posture and practices. Click on the GitHub link below to deploy the Azure WAF Monitor Workbook for WAF on Azure Application Gateway or Azure Front Door. This workbook visualizes security relevant WAF events across several filterable panels and provides a view into your WAF events such as top IP attackers and event triggers.
Based on the insights provided by the Azure WAF workbook, you can take an action such as block or log incoming requests that you believe are malicious.
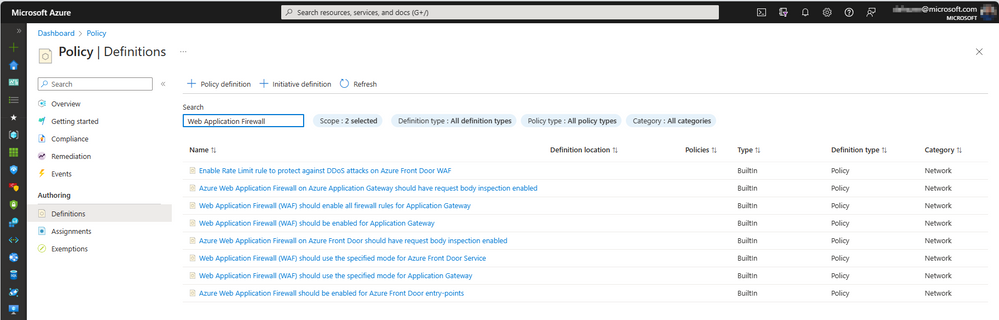
Azure Policy for Azure WAF
Azure Policy helps to enforce organizational standards and to assess compliance at-scale. Through its compliance dashboard, it provides an aggregated view to evaluate the overall state of the environment, with the ability to drill down to the per-resource, per-policy granularity. It also helps to bring your resources to compliance through bulk remediation for existing resources and automatic remediation for new resources. There are a number of Azure Policies that aid governance across your WAF resources. Azure Policy can assist in ensuring that you adhere to some of the best practices in this blog, such as enabling diagnostic logs during deployment, or remediating resources that do not have logging enabled.
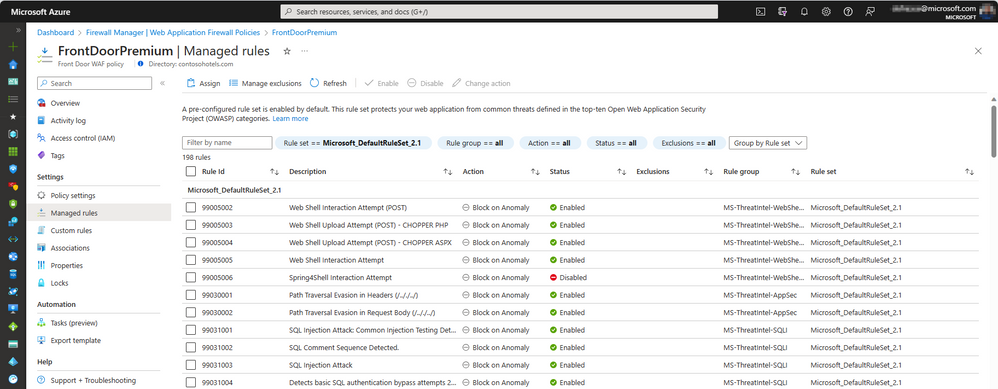
Ruleset Updates
Azure-managed rule sets provide an easy way to deploy protection against a common set of security threats. Since such rule sets are managed by Azure, the rules are updated as needed to protect against new attack signatures. Microsoft regularly updates the managed rules to take account of the current threat landscape. It is recommended that you regularly check for updates to the Azure-managed rule sets and use the latest release when available.
- Azure Application Gateway: Azure WAF on Azure Application Gateway can use either the Core Rule Set (CRS) or Default Rule Set (DRS) for the applied managed ruleset. It is recommended to use the latest stable release for Azure WAF.
- Azure Front Door: Azure WAF on Azure Front Door uses DRS for the applied managed rulesets. DRS provides the same level of protection as CRS but includes additional rules that are written in partnership with the Microsoft Threat Intelligence team. These rules provide increased coverage, patches for specific vulnerabilities, and better false positive reduction.
Rules can be enabled or disabled on a per-rule basis, or you can set specific actions by individual rule.
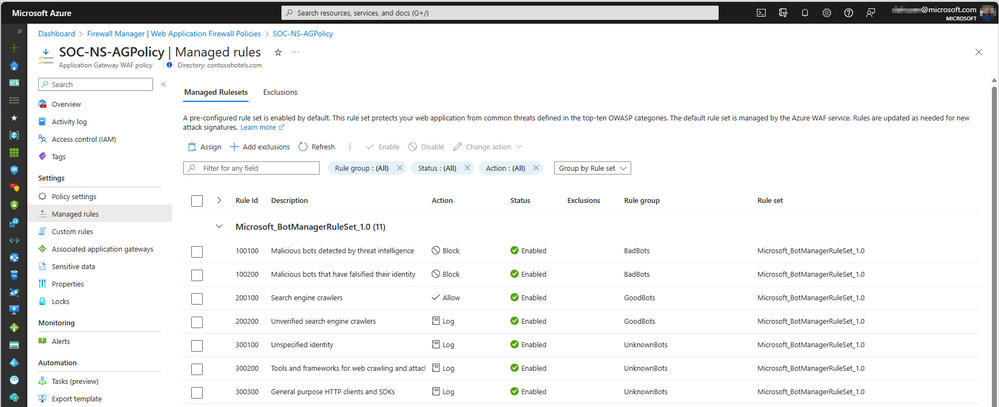
Bot Manager Rulesets
Azure WAF provides the ability to enable a managed bot protection rule set for your WAF to block or log requests from known malicious IP addresses. The IP addresses are sourced from the Microsoft Threat Intelligence feed. Intelligent Security Graph powers Microsoft threat intelligence and is used by multiple services including Microsoft Defender for Cloud.
- Azure Application Gateway: You can use the Bot Protection ruleset alongside any of the OWASP rulesets with Azure Application Gateway WAF v2 SKU.
- Azure Front Door: You can enable a managed bot protection rule set to take custom actions on requests from known bot categories with WAF on Azure Front Door.
The bot mitigation ruleset list of known bad IP addresses updates multiple times per day from the Microsoft Threat Intelligence feed to stay in sync with the bots. Your web applications are continuously protected even as the bot attack vectors change.
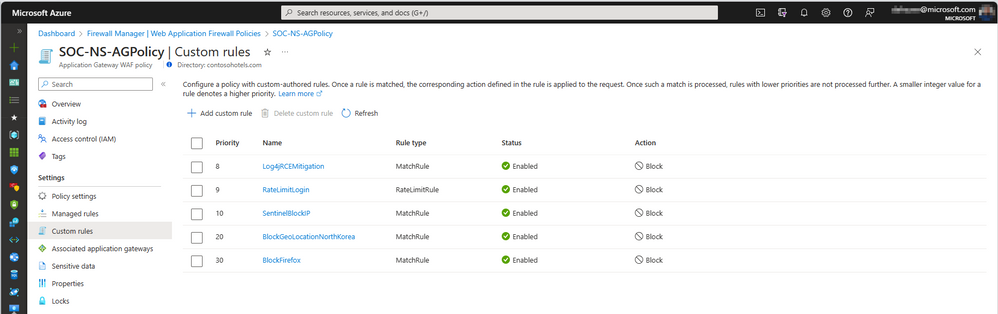
Custom Rules
Custom rules allow you to create your own rules that are evaluated for each request that passes through the WAF. These rules hold a higher priority than the rest of the rules in the managed rule sets. The custom rules contain a rule name, rule priority, and an array of matching conditions. If these conditions are met, action is taken (to allow, block, or log). If a custom rule is triggered, and an allow or block action is taken, no further custom or managed rules are evaluated. Custom rules can be enabled or disabled on demand.
- Azure Application Gateway: Read more about Custom rules with WAF on Azure Application Gateway.
- Azure Front Door: Read more about Custom rules with WAF on Azure Front Door.
There are two types of custom rules: match rules and rate limit rules. A match rule controls access based on a set of matching conditions. A rate limit rule controls access based on matching conditions and the rates of incoming requests. Configure Custom rules deny access from specific user-agents, , or redirect requests to another endpoint. You can also restrict access to known URIs and malicious strings.
- Azure Application Gateway: Learn more about rate limiting for WAF on Azure Application Gateway.
- Azure Front Door: Learn more about rate limiting for WAF on Azure Front Door.
False Positives
False positives are security alerts that are triggered by legitimate requests or traffic. They can cause performance issues, user frustration, and loss of trust in the firewall. To reduce false positives, WAFs should be configured properly, updated regularly, and tuned to the specific needs of the web application. As suggested in the documentation, new Azure WAF deployments should be enabled in detection mode for the to observe the general overview of the traffic connecting to your resources. This provides the opportunity to obtain WAF logs and update any exclusions or custom rules prior to the transition to Prevention mode. This can help reduce the occurrence of unexpected false positive.
- Azure Application Gateway: Learn how to tune your Azure WAF on Azure Application Gateway using this in-depth document to create exclusions, custom rules, and even disable rules that may be causing issues or false positives.
- Azure Front Door: Learn how to create exclusion lists for Azure WAF on Azure Front Door with this detailed document that walks us through an example SQL injection.
Find additional fine-tuning steps using attribute examples and templates in this blog post.
Restrict Access to Backend
Access to the backend application should be restricted to only allow connections from the Azure Application Gateway or the Azure Front Door. This involves setting up an IP access control list, or Network Security Group (NSG), and restricting the values of the traffic sent to the back end.
- Azure Application Gateway: For Azure Application Gateway, we can restrict the traffic to the backend mainly by utilizing an IP access control list, or NSG. In the NSG, configure the source IP address to reflect the private IP address space of the subnet that the Azure Application Gateway sits in, as well as the target port (80/443).
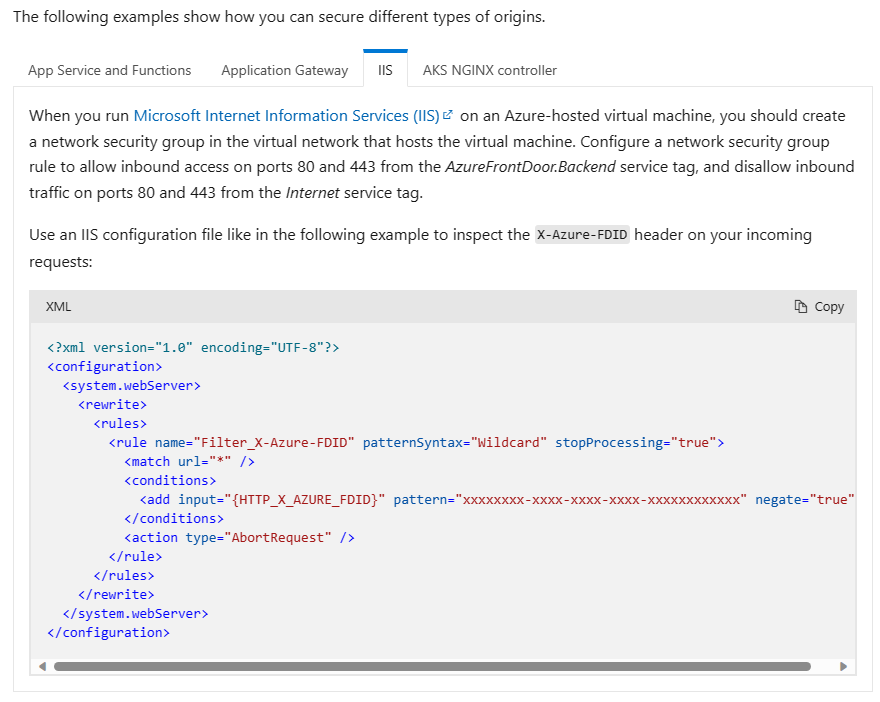
- Azure Front Door: For Azure Front Door, there are a couple of different ways to secure backend access. IP address filtering can be used with an NSG utilizing the AzureFrontDoor.Backend service tag as a source address space. It’s recommended to use the service tag instead of hard-coding IP addresses since Azure Front Door’s IP address space changes regularly. Additionally, you can configure the backend origin to only accept requests that contain the X-Azure-FDID header in the request. Azure generates a unique identifier for each Front Door profile. You can find the identifier in the Azure portal, by looking for the Front Door ID value in the Overview page of your profile.
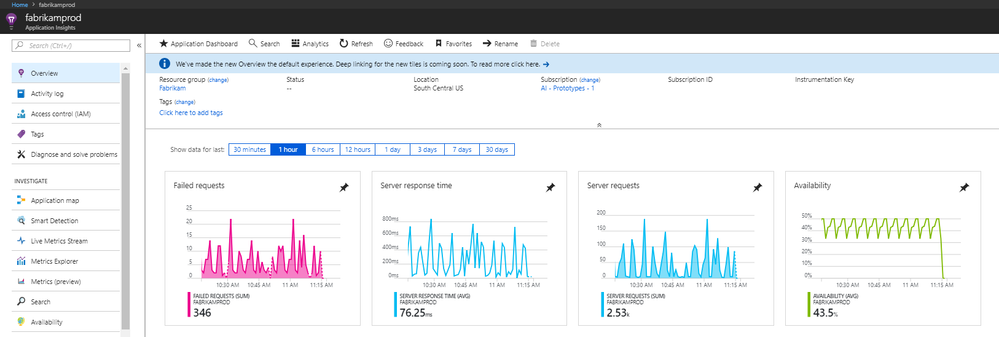
Application Insights
Application Insights is an extension of Azure Monitor and provides application performance monitoring (APM) features. APM tools are useful to monitor applications from development, through test, and into production. Application Insights provide live metrics, availability (also known as synthetic transaction monitoring), usage, smart detection, and more.
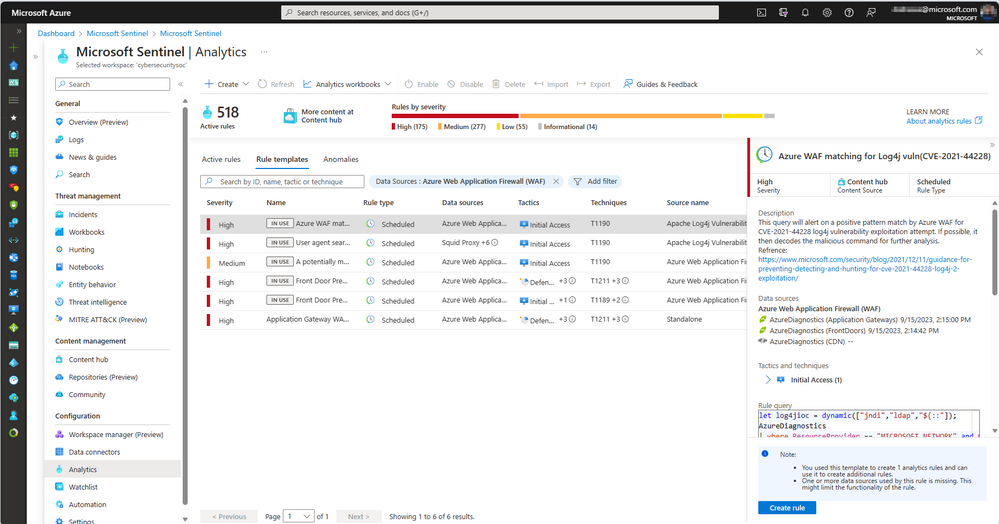
Microsoft Sentinel
Microsoft Sentinel is a scalable, cloud-native solution that provides Security information and event management (SIEM) and Security orchestration, automation, and response (SOAR) capabilities. It delivers intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response. Azure WAF combined with Microsoft Sentinel can provide security information event management for WAF resources. Microsoft Sentinel provides security analytics using Log Analytics, which allows you to easily break down and view your WAF data.
Analytic rules in Microsoft Sentinel provide centralized security management for known vulnerabilities for web applications. In place of manually updating WAF policies each time to patch a known vulnerability, Azure WAF with Microsoft Sentinel integration provides a way to automate the detection and response to threats/incidents/alerts.
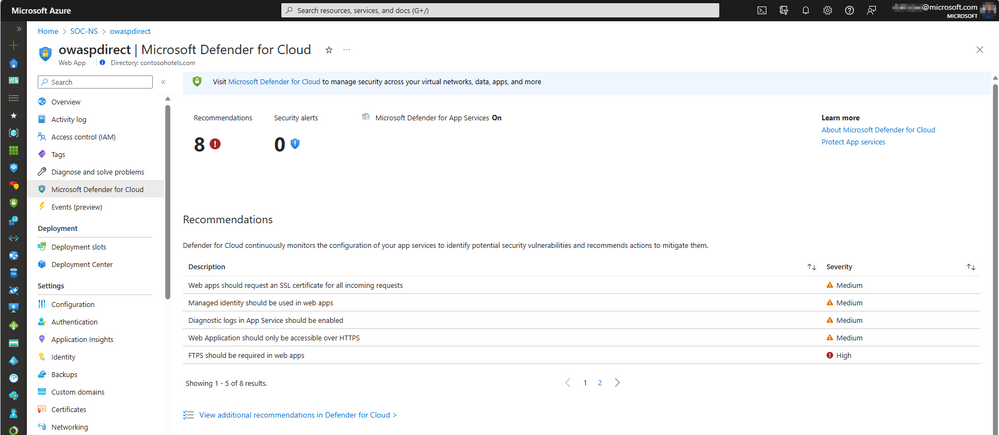
Microsoft Defender for Cloud (MDC)
Microsoft Defender for Cloud is a cloud-native application protection platform (CNAPP) with a set of security measures and practices designed to protect cloud-based applications from various cyber threats and vulnerabilities. Defender for Cloud combines the capabilities of development security operations (DevSecOps), cloud security posture management (CSPM), and cloud workload protection platform (CWPP). Defender for Cloud helps you to incorporate good security practices early during the software development process, or DevSecOps. You can protect your code management environments and your code pipelines and get insights into your development environment security posture from a single location.
Whether you’re using an Azure Web App or an Azure Virtual Machine, you can review the recommendations from MDC for your web application. Suggestions to improve your web application security include incoming client certificate options, authentication, the latest HTTP versions, and more.
Microsoft Defender for APIs
Microsoft Defender for APIs is a plan provided by Microsoft Defender for Cloud that offers full lifecycle protection, detection, and response coverage for APIs. Defender for APIs helps you to gain visibility into business-critical APIs. You can investigate and improve your API security posture, prioritize vulnerability fixes, and quickly detect active real-time threats. Leverage Microsoft Defender for API with Azure WAF for improved web application security. The Defender for APIs’ logic adapts to different API endpoints and uses machine learning algorithms, thereby providing a contextual understanding that enables precise and effective security measures against vulnerabilities.
Infrastructure as Code (IaC)
Infrastructure as code (IaC) is a method of managing and provisioning IT resources through code, rather than manual processes. Infrastructure as code provides consistency and reliability, scalability and flexibility, efficiency and speed, and auditability and compliance. IaC can help you automate and standardize the configuration and deployment of your Azure WAF. Exclusions, custom rules, associations, rule enablement and more can be managed through this method and is the recommended path for maintaining and operating your Azure WAF environments. Use tools such as Azure CLI, Azure PowerShell, Bicep, and Terraform.
Conclusion
Improved security is achieved increasingly when customers take advantage of available tools as soon as possible, to keep their environment secure. The practices outlined help to maintain the effectiveness and performance of the WAF, as well as to detect and respond to new threats and vulnerabilities. By following these best practices, web application owners can ensure that their WAFs provide optimal protection for their web applications. Ensure a security incident plan is in place to mitigate and reduce the attack surface area and follow Azure blog for security updates.
Resources
- Introduction to Azure Web Application Firewall | Microsoft Learn
- Best practices for Azure Web Application Firewall (WAF) on Azure Application Gateway | Microsoft Learn
- Best practices for Azure Web Application Firewall in Azure Front Door | Microsoft Learn
- Troubleshoot - Azure Web Application Firewall | Microsoft Learn
- Tuning Web Application Firewall (WAF) for Azure Front Door | Microsoft Learn
- Using Microsoft Sentinel with Azure Web Application Firewall | Microsoft Learn
- Azure WAF Tuning for Web Applications - Microsoft Community Hub
Published on:
Learn moreRelated posts
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...
Azure Function to scrape Yahoo data and store it in SharePoint
A couple of weeks ago, I learned about an AI Agent from this Microsoft DevBlogs, which mainly talks about building an AI Agent on top of Copil...
Maximize Azure Cosmos DB Performance with Azure Advisor Recommendations
In the first post of this series, we introduced how Azure Advisor helps Azure Cosmos DB users uncover opportunities to optimize efficiency and...
February Patches for Azure DevOps Server
We are releasing patches for our self‑hosted product, Azure DevOps Server. We strongly recommend that all customers stay on the latest, most s...
Building AI-Powered Apps with Azure Cosmos DB and the Vercel AI SDK
The Vercel AI SDK is an open-source TypeScript toolkit that provides the core building blocks for integrating AI into any JavaScript applicati...
Time Travel in Azure SQL with Temporal Tables
Applications often need to know what data looked like before. Who changed it, when it changed, and what the previous values were. Rebuilding t...