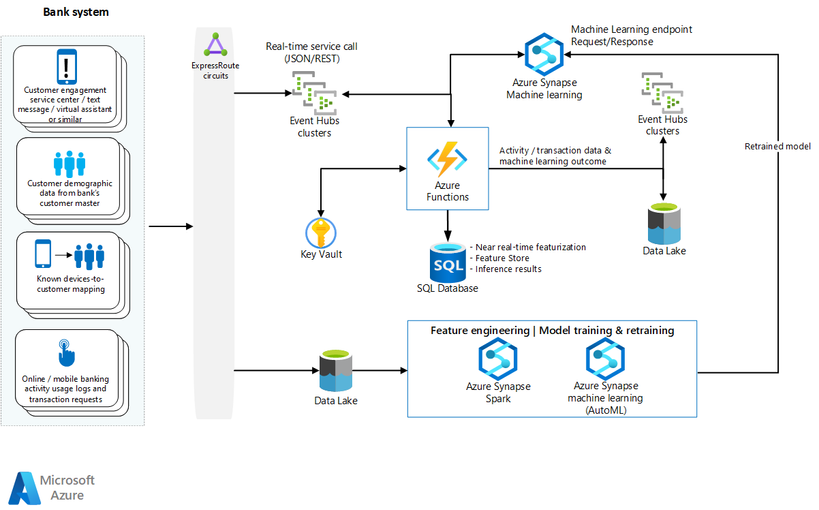
New Azure Architecture - Detect mobile bank fraud

In a typical case of online fraud, the thief makes multiple transactions, leading to a loss of thousands of dollars. That's why fraud detection must happen in near real-time.
This article presents a solution that uses Azure technology to predict a fraudulent mobile bank transaction within two seconds. We've built it with customers.
Read the article here:
Let's dig into the architecture:
An event-driven pipeline ingests and processes log data, creates and maintains behavioral account profiles, incorporates a fraud classification model, and produces a predictive score. Most steps in this pipeline start with an Azure function. A model training workstream combines on-premises historical fraud data and ingested log data. Azure Data Factory orchestrates the processing steps. We use Azure Logic Apps to connect and synchronize to an on-premises system to create a fraud management case, suspend account access, and to generate a phone contact.
In the article you'll find:
- Information about the top challenges: Rare instances of fraud and rigid rules.
- Operational context: The key questions we asked and how fraud is committed in the operational environment.
- Compromise matrix: See the methods used, data taken, and patterns for several types of fraud, including Credential, Device, Financial, and Non-Transactional compromises.
- A detailed dataflow of the above architecture.
- Data pipeline and automation: What happens in the two seconds, in order to catch the compromise.
- Event processing: Architecture and dataflow that explains in detail the fundamental interactions for an Azure function within this infrastructure.
- Data pre-processing and JSON transformation.
- Near real-time data processing and featurization with SQL Database.
- Event schema management.
- Feature engineering for machine learning.
- AutoML: It automates the time-consuming, iterative tasks of machine learning model development.
- Data imbalance: In a fraud dataset, there are many more non-fraudulent transactions than fraudulent transactions.
- Model training with a code sample!
- Model evaluation: The account-level metrics are described in a table.
- Model operationalization and retraining.
- Components: Direct links to all the Azure services used in this solution.
- Technical considerations: Skill sets and Hybrid operational environment.
- Security considerations: Includes a Networking Security Architecture and a security baseline recommendations matrix.
- Scalability considerations.
You can find the article here, on the Azure Architecture Center:
Special thanks to the Engineers who wrote this:
- Kate Baroni
- Michael Hlobil
- Cedric Labuschagne
- Frank Garofalo
- Shep Sheppard
And thanks also to our editor/tech writer, Mick Alberts.
Remember to keep your head in the Cloud!
Ed
Published on:
Learn moreRelated posts
What’s new with Azure Repos?
We thought it was a good time to check in and highlight some of the work happening in Azure Repos. In this post, we’ve covered several recent ...
Part 1: Building Your First Serverless HTTP API on Azure with Azure Functions & FastAPI
Introduction This post is Part 1 of the series Serverless Application Development with Azure Functions and Azure Cosmos DB, where we explore ...
Announcing GPT 5.2 Availability in Azure for U.S. Government Secret and Top Secret Clouds
Today, we are excited to announce that GPT-5.2, Azure OpenAI’s newest frontier reasoning model, is available in Microsoft Azure for U.S. Gover...