Conditional Access authentication strength is now Generally Available!

Greetings! I’m thrilled to announce that Conditional Access authentication strength is now generally available. This powerful feature allows organizations to choose the right authentication method requirements for specific scenarios, making it easier than ever for organizations to move towards more secure, modern, and strong authentication.
With Conditional Access authentication strength, administrators can define a minimum level of authentication strength required for access, based on factors such as the user's sign-in risk level or the sensitivity of the resource being accessed. This can be especially useful for organizations that operate in highly regulated industries or have strict compliance requirements. For example, US Government agencies who need to comply with the US federal government's Office of Management and Budget (OMB) memorandum 22-09. Authentication strength helps government customers to enforce phishing-resistant MFA for their employees and vendors.
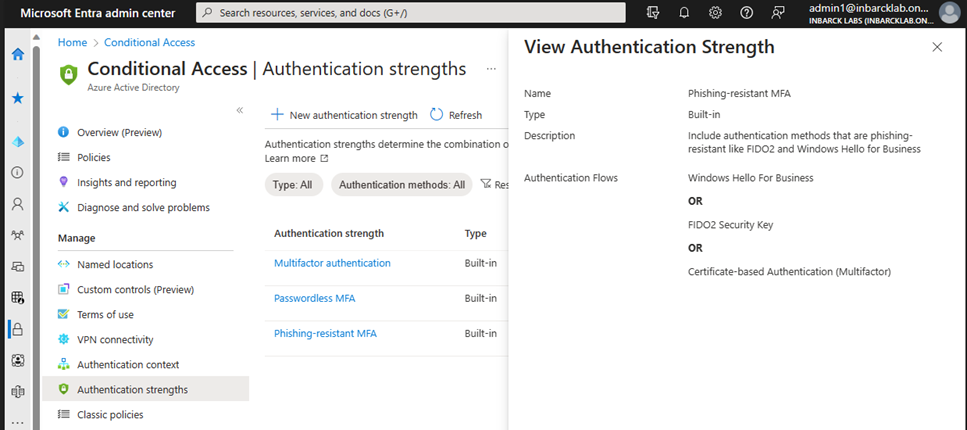
Organizations can choose from predefined authentication strength policies or define their own custom authentication strength policies, based on their specific needs and risk profiles. These policies can be applied to members in the tenant and for external users from any Microsoft cloud. It enables organizations to raise the bar for authentication requirements for their vendors and partners.
We've seen many organizations already using Conditional Access authentication strength in various ways. For example:
- A government agency that uses authentication strength to enforce Certificate-Based Authentication (CBA) for authenticating to any resource protected by Azure Active Directory (Azure AD), while allowing other authentication methods for password reset, which is used in support of legacy on-premises applications.
- A professional services company that uses authentication strength to enforce their privileged users to use FIDO2 and to gradually move away from telecom-based methods for their wide user base.
- A software company that uses authentication strength to enforce standardization of authentication methods across multiple tenants they own.
Learn more about Conditional Access authentication strength: https://aka.ms/authstrengthdocs
We encourage you to explore this powerful feature and let us know what you think!
Regards,
Alex Weinert (twitter: @Alex_t_weinert)
VP Director of Identity Security, Microsoft
Learn more about Microsoft identity:
- Related Articles:
- Get to know Microsoft Entra – a comprehensive identity and access product family
- Return to the Microsoft Entra (Azure AD) blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Entra (Azure AD) forum
Published on:
Learn more